Crypto World
Why Privacy Coins Often Appear in Post-Hack Fund Flows
Key takeaways
-
Privacy coins are just a step in a broader laundering pipeline after hacks. They serve as a temporary black box to disrupt traceability.
-
Hackers typically move funds through consolidation, obfuscation and chain hopping and only then introduce privacy layers before attempting to cash out.
-
Privacy coins are most useful immediately after a hack because they reduce onchain visibility, delay blacklisting and help break attribution links.
-
Enforcement actions against mixers and other laundering tools often shift illicit flows toward alternative routes, including privacy coins.
After crypto hacks occur, scammers often move stolen funds through privacy-focused cryptocurrencies. While this has created a perception of hackers preferring privacy coins, these assets function as a specialized “black box” within a larger laundering pipeline. To understand why privacy coins show up after hacks, you need to take into account the process of crypto laundering.
This article explores how funds move post-hack and what makes privacy coins so useful for scammers. It examines emerging laundering methods, limitations of privacy coins like Monero (XMR) and Zcash (ZEC) as laundering tools, legitimate uses of privacy technologies and why regulators need to balance innovation with the need to curb laundering.
How funds flow after a hack
Following a hack, scammers don’t usually send stolen assets directly to an exchange for immediate liquidation; instead, they follow a deliberate, multi-stage process to obscure the trail and slow down the inquiry:
-
Consolidation: Funds from multiple victim addresses are transferred to a smaller number of wallets.
-
Obfuscation: Assets are shuffled through chains of intermediary crypto wallets, often with the help of crypto mixers.
-
Chain-hopping: Funds are bridged or swapped to different blockchains, breaking continuity within any single network’s tracking tools.
-
Privacy layer: A portion of funds is converted into privacy-focused assets or routed through privacy-preserving protocols.
-
Cash-out: Assets are eventually exchanged for more liquid cryptocurrencies or fiat through centralized exchanges, over-the-counter (OTC) desks or peer-to-peer (P2P) channels.
Privacy coins usually enter the stage in steps four or five, blurring the traceability of lost funds even more after earlier steps have already complicated the onchain history.

Why privacy coins are attractive for scammers right after a hack
Privacy coins offer specific advantages right at the time when scammers are most vulnerable, immediately after the theft.
Reduced onchain visibility
Unlike transparent blockchains, where the sender and receiver and transaction amounts remain fully auditable, privacy-focused systems deliberately hide these details. Once funds move into such networks, standard blockchain analytics lose much of their efficacy.
In the aftermath of the theft, scammers try to delay identification or evade automated address blacklisting by exchanges and services. The sudden drop in visibility is particularly valuable in the critical days after theft when monitoring is most intense.
Breaking attribution chains
Scammers tend not to move directly from hacked assets into privacy coins. They typically use multiple techniques, swaps, cross-chain bridges and intermediary wallets before introducing a privacy layer.
This multi-step approach makes it significantly harder to connect the final output back to the original hack. Privacy coins act more as a strategic firebreak in the attribution process than as a standalone laundering tool.
Negotiating power in OTC and P2P markets
Many laundering paths involve informal OTC brokers or P2P traders who operate outside extensively regulated exchanges.
Using privacy-enhanced assets reduces the information counterparties have about the funds’ origin. This can simplify negotiations, lower the perceived risk of mid-transaction freezes and improve the attacker’s leverage in less transparent markets.
Did you know? Several early ransomware groups originally demanded payment in Bitcoin (BTC) but later switched to privacy coins only after exchanges began cooperating more closely with law enforcement on address blacklisting.
The mixer squeeze and evolving methods of laundering
One reason privacy coins appear more frequently in specific time frames is enforcement pressure on other laundering tools. When law enforcement targets particular mixers, bridges or high-risk exchanges, illicit funds simply move to other channels. This shift results in the diversification of laundering routes across various blockchains, swapping platforms and privacy-focused networks.
When scammers perceive one laundering route as risky, alternative routes experience higher volumes. Privacy coins gain from this dynamic, as they offer inherent transaction obfuscation, independent of third-party services.
Limitations of privacy coins as a laundering tool
Privacy features notwithstanding, most large-scale hacks still involve extensive use of BTC, Ether (ETH) and stablecoins at later stages. The reason is straightforward: Liquidity and exit options are important.
Privacy coins generally exhibit:
These factors complicate the conversion of substantial amounts of crypto to fiat currency without drawing scrutiny. Therefore, scammers use privacy coins briefly before reverting to more liquid assets prior to final withdrawal.
Successful laundering involves integration of privacy-enhancing tools with high-liquidity assets, tailored to each phase of the process.
Did you know? Some darknet marketplaces now list prices in Monero by default, even if they still accept Bitcoin, because vendors prefer not to reveal their income patterns or customer volume.
Behavioral trends in asset laundering
While tactical specifics vary, blockchain analysts generally identify several high-level “red flags” in illicit fund flows:
-
Layering and consolidation: Rapid dispersal of assets across a vast network of wallets, followed by strategic reaggregation to simplify the final exit.
-
Chain hopping: Moving assets across multiple blockchains to break the deterministic link of a single ledger, often sandwiching privacy-enhancing protocols.
-
Strategic latency: Allowing funds to remain dormant for extended periods to bypass the window of heightened public and regulatory scrutiny.
-
Direct-to-fiat workarounds: Preferring OTC brokers for the final liquidation to avoid the robust monitoring systems of major exchanges.
-
Hybrid privacy: Using privacy-centric coins as a specialized tool within a broader laundering strategy, rather than as a total replacement for mainstream assets.
Contours of anonymity: Why traceability persists
Despite the hurdles created by privacy-preserving technologies, investigators continue to secure wins by targeting the edges of the ecosystem. Progress is typically made through:
-
Regulated gateways: Forcing interactions with exchanges that mandate rigorous identity verification
-
Human networks: Targeting the physical infrastructure of money-mule syndicates and OTC desks
-
Off-chain intelligence: Leveraging traditional surveillance, confidential informants and Suspicious Activity Reports (SARs)
-
Operational friction: Exploiting mistakes made by the perpetrator that link their digital footprint to a real-world identity.
Privacy coins increase the complexity and cost of an investigation, but they cannot fully insulate scammers from the combined pressure of forensic analysis and traditional law enforcement.
Did you know? Blockchain analytics firms often focus less on privacy coins themselves and more on tracing how funds enter and exit them since those boundary points offer the most reliable investigative signals.
Reality of legitimate use for privacy-enhancing technologies
It is essential to distinguish between the technology itself and its potential criminal applications. Privacy-focused financial tools, such as certain cryptocurrencies or mixers, serve valid purposes, including:
-
Safeguarding the confidentiality of commercial transactions, which includes protecting trade secrets or competitive business dealings
-
Shielding individuals from surveillance or monitoring in hostile environments
-
Reducing the risk of targeted theft by limiting public visibility of personal wealth.
Regulatory scrutiny isn’t triggered by the mere existence of privacy features, but when they are used for illicit activity, such as ransomware payments, hacking proceeds, sanctions evasion or darknet marketplaces.
This key distinction makes effective policymaking difficult. Broad prohibitions risk curtailing lawful financial privacy for ordinary users and businesses while often failing to halt criminal networks that shift to alternative methods.
Balancing act of regulators
For cryptocurrency exchanges, the recurring appearance of privacy coins in post-hack laundering flows intensifies the need to:
-
Enhance transaction monitoring and risk assessment
-
Reduce exposure to high-risk inflows
-
Strengthen compliance with cross-border Travel Rule requirements and other jurisdictional standards.
For policymakers, it underscores a persistent challenge: Criminal actors adapt more quickly than rigid regulations can evolve. Efforts to crack down on one tool often displace activity to others, turning money laundering into a dynamic, moving target rather than a problem that can be fully eradicated.
Cointelegraph maintains full editorial independence. The selection, commissioning and publication of Features and Magazine content are not influenced by advertisers, partners or commercial relationships.
Crypto World
Ethereum’s Trillion-Dollar Security Dashboard: A Six-Pillar Framework for Ecosystem Safety

TLDR:
- User experience is Ethereum’s weakest security link, with only 7 of 29 controls currently live.
- Smart contract attestations now verify deployed code, reducing reliance on one-time audits alone.
- Consensus protocol remains Ethereum’s strongest pillar, with robust anti-censorship mechanisms.
- Social governance risks like stake centralization now tracked alongside technical vulnerabilities
Ethereum Trillion Dollar Security Dashboard shows a new structured view of ecosystem safety. It is currently tracking six key areas, including UX, smart contract security, infrastructure, consensus, monitoring, and social governance.
The Ethereum Foundation launched this initiative to assess risks and progress, aiming to support large‑scale value safely.
The dashboard emphasizes transparency and measurable security for developers and institutional users.
User Experience and Smart Contract Security
The Ethereum Trillion Dollar Security Dashboard starts with user experience, the area where most losses occur. Users do not interact with the protocol directly but with wallets, dapps, browser extensions, and signing prompts.
Because Ethereum transactions are atomic and irreversible, a single mistake can lead to substantial loss. Key subdomains, including key management, blind signing, approvals, privacy, and interface fragmentation, closely align with observed exploit patterns.
Phishing attacks, malicious approvals, and fake frontends remain primary causes of user loss. Only seven out of twenty-nine controls are currently live, signaling UX as Ethereum’s most urgent frontier.
Clear signing standards and wallet safety protocols are prioritized to protect users effectively.Smart contract security has matured but continues evolving.
Audits, formal verification, bug bounties, and hardened libraries like OpenZeppelin help ensure that deployed contracts remain secure.
This highlights a shift toward verifiable on-chain attestations, solving the problem with the audited contract version.
These measures make security more transparent and reliable, improving overall ecosystem trust. Security tools now focus on making smart contract interactions legible for users.
Bytecode-to-audit linking ensures that contracts are identifiable and auditable, reducing dependency on one-off audit assurances.
The Ethereum ecosystem demonstrates consistent improvement in smart contract resilience while emphasizing usability. It helps bridge technical rigor and practical safety for participants.
Infrastructure, Consensus, and Social Governance
Infrastructure and cloud security remain essential components of Ethereum’s ecosystem defense. Reliance on centralized RPC providers, cloud-hosted nodes, and opaque Layer 2 solutions exposes the system to hidden failure points.
Outages, censorship, or data logging on these services can impact user experience even if Layer 1 remains stable. The dashboard prioritizes community-run RPCs and self-hosted nodes, emphasizing verifiability and decentralization.
Most controls are live, reflecting an understanding of evolving risks. Ethereum’s consensus protocol remains the ecosystem’s strongest pillar.
Through it, clients can diversify, stake decentralization, and actively enforce anti-censorship mechanisms.
Forced transaction inclusion ensures neutrality, and preparation for quantum-resistant cryptography, and long-term security planning. Monitoring, incident response, and mitigation strategies reduce systemic impact when failures occur.
Live monitoring, coordinated responses, and emerging insurance solutions help contain risk. Social governance, though slower to mature, is identified as a critical security surface.
Stake centralization, regulatory pressures, and organizational capture are measured, ensuring the ecosystem addresses risks beyond technical vulnerabilities.
This holistic approach reframes security from protecting the protocol to supporting a multi-trillion-dollar ecosystem.
Ethereum balances strong consensus and contract security with infrastructure vigilance and social awareness, demonstrating comprehensive security planning for both users and institutions.
Crypto World
Erebor Secures First New US Bank Charter of Trump’s Second Term


The United States has approved a newly created national bank for the first time during President Donald Trump’s second term, granting a charter to crypto-friendly startup Erebor Bank.
The Office of the Comptroller of the Currency (OCC) confirmed the approval on Friday, allowing the lender to operate nationwide, the Wall Street Journal reported, citing people familiar with the matter.
The institution launches with about $635 million in capital and aims to serve startups, venture-backed companies and high-net-worth clients, a segment left underserved after the 2023 collapse of Silicon Valley Bank.
Erebor is backed by a roster of prominent technology investors, including Andreessen Horowitz, Founders Fund, Lux Capital, 8VC and Elad Gil. The project was founded by Oculus co-creator Palmer Luckey, who will sit on the board but not manage daily operations.
Related: Nomura-backed Laser Digital seeks US bank charter amid crypto banking push: Report
Erebor targets defense tech, robotics, AI
The bank is reportedly positioning itself as a specialist lender to emerging industries such as defense technology, robotics and advanced manufacturing. Prospective clients include companies developing AI-driven factories, aerospace research and pharmaceutical production in low-gravity environments.
“You can think of us like a farmers’ bank for tech,” Luckey reportedly told the WSJ, arguing that traditional banks often lack the expertise needed to assess startups with unconventional assets.
Erebor also plans to integrate blockchain-based payment rails enabling continuous settlement, an unusual feature in the US banking system, where transactions typically follow business hours. The Federal Deposit Insurance Corp. previously approved deposit insurance for the institution.
The bank’s strategy includes extending credit backed by crypto holdings or private securities and financing purchases of high-performance artificial-intelligence chips.
Related: OCC Comptroller says WLFI charter review will remain apolitical
Erebor hits $4 billion valuation
In October, Erebor received preliminary conditional approval from the OCC. One month later, its deposit insurance application was approved by the Federal Deposit Insurance Corporation.
Erebor was valued at roughly $2 billion in a funding round last year and later reached a $4 billion valuation after raising $350 million in a funding round led by Lux Capital.
Magazine: Bitget’s Gracy Chen is looking for ‘entrepreneurs, not wantrepreneurs’
Crypto World
Banks Could Eventually Offer Crypto Products, Says Bessent

US Treasury Secretary Scott Bessent says banks and crypto may begin to offer similar products, and pledged to prevent deposit flight concerns that are stalling a key crypto bill.
US Treasury Secretary Scott Bessent has told Congress that traditional and crypto banking products and services may be more intertwined in the future.
Appearing before the Senate Banking Committee on Thursday, Bessent was asked by Republican Senator Cynthia Lummis whether there could come a time when conventional banks and crypto are offering the same types of products.
“I think that can happen over time,” Bessent said. “We’ve actually been working with small and community banks to discuss how they can be part of the digital asset revolution.”

Bessent tells those resisting regulations to move to El Salvador
Bessent said it was “impossible to proceed” without crypto having clear rules, and said the industry should back the crypto market structure legislation, dubbed the CLARITY Act, that’s before Congress.
“We have to get this CLARITY Act across the finish line, and any market participants who don’t want it should move to El Salvador.”
“We’ve got to bring safe, safe, sound, and smart practices and the oversight of the US government, but also allow for the freedom that is crypto,” Bessent said. “I think it’s a balance that is being worked out.”
Working to prevent bank deposit volatility
The crypto market structure bill has stalled in the Senate Banking Committee as bipartisan talks over inclusions in the bill are at a stalemate.
Related: Crypto firms offer ideas to break market structure gridlock: Report
Lawmakers pushed to add restrictions on stablecoin yields that some crypto companies, notably Coinbase, had resisted. Bessent said that deposit volatility is “very undesirable” because it is the stability of those deposits that allows banks to lend into their communities.
“We will continue to work to make sure that there is no deposit volatility associated with this,” he said.
Several crypto companies reportedly offered concessions this week, suggesting giving community banks a larger role in the stablecoin system to help push the bill through the Senate.
Magazine: DAT panic dumps 73,000 ETH, India’s crypto tax stays: Asia Express
Crypto World
Infinite Possibilities announces upcoming launch of Proof-of-Activity DEX and IP Membership program


- Infinite Possibilities has announced plans to launch iPDex, a multi-chain decentralized exchange aggregator.
- The project is also preparing to introduce its IP Membership NFT.
- iPDex is designed to route swaps across multiple blockchains, including Ethereum, Solana, BNB Chain, and Base.
February 6, 2026 – Infinite Possibilities has announced plans to launch iPDex, a multi-chain decentralized exchange aggregator designed around on-chain activity rather than inflationary incentives.
The project is also preparing to introduce its IP Membership NFT, which will provide early access to ecosystem features ahead of the platform’s broader rollout.
iPDex is designed to route swaps across multiple blockchains, including Ethereum, Solana, BNB Chain, and Base.
According to the team, the platform’s architecture focuses on aligning token issuance and reward distribution with verified trading activity, rather than relying on passive staking or liquidity provision models commonly used in decentralized finance.
As part of the launch, Infinite Possibilities plans to introduce IP, a utility token intended to support platform functionality and participation mechanisms across the ecosystem.
Token distribution is designed to be linked to on-chain activity recorded through iPDex, with supply growth tied to platform usage rather than predefined emissions schedules.
IP Membership program
Ahead of the public launch of iPDex, Infinite Possibilities will open access to its IP Membership NFT program.
The membership is designed to provide participants with early access to platform features, participation tracking, and ecosystem engagement mechanisms during the initial phase of development.
Membership participation involves a contribution denominated in USD equivalent, with participation levels tracked through an internal, non-transferable metric used to measure verified activity within the ecosystem.
Following the membership phase, eligible participants may receive IP tokens based on recorded participation, subject to the program’s published terms and conditions.
The company notes that the membership program is intended to support early ecosystem development and community engagement, rather than serve as a speculative investment product.
Platform development focus
Infinite Possibilities states that iPDex is being developed with an emphasis on protocol-managed liquidity, automated execution mechanisms, and cross-chain trading infrastructure.
The project aims to reduce reliance on user-supplied liquidity while enabling participation through on-chain activity and platform usage.
Additional ecosystem tools, including market data and analytics products, are planned as part of the broader Infinite Possibilities roadmap.
Looking ahead
The iPDex platform and IP Membership NFT program are expected to launch soon.
Further details regarding participation mechanics, eligibility requirements, and platform features will be released through Infinite Possibilities’ official channels.
More information is available at: IP Website | Twitter (X) | Telegram | NFT Membership Sale | BitMarketCap Website | Hacken Report
This article is authored by a third party, and CoinJournal does not endorse or take responsibility for its content, accuracy, quality, advertisements, products, or materials. Readers should independently research and exercise due diligence before making decisions related to the mentioned company.
Crypto World
Stablecoin Inflows Surge as Bitcoin Struggles Under Persistent Selling Pressure

TLDR:
- Stablecoin inflows now exceed the 90-day average despite Bitcoin struggling to regain upward momentum.
- Exchange liquidity is rising, but selling pressure continues to cap short-term price recovery attempts.
- Investor behavior reflects cautious accumulation rather than aggressive dip buying or breakout chasing.
- Market structure points to a transition phase marked by growing participation and defensive demand.
Stablecoin inflows to exchanges have surged to about $98 billion this week, nearly doubling from late December figures as Bitcoin’s price drops below key support.
Data shows capital moving back onto trading venues while sell-side pressure persists and price remains under strain.
The rising liquidity pattern comes as the market experiences heavy selling and subdued short-term demand.
Liquidity Expansion Without Price Confirmation
Stablecoin inflows have doubled in recent weeks and moved above their 90-day average. This change shows that capital is returning to exchanges after months of muted participation and low turnover.
Bitcoin price, however, continues to weaken as rallies fail to hold. Each recovery attempt meets renewed selling, indicating that supply remains greater than current demand at these levels.
Market observers described the flow as preparation rather than aggressive buying.
The structure suggests that the market is not constrained by lack of funds. Instead, it faces a persistent overhang of available Bitcoin from holders distributing into strength.
Stablecoins typically move to exchanges when investors intend to deploy capital. Their rise signals positioning activity rather than passive storage or risk avoidance.
Yet the absence of price response shows that buyers are executing cautiously. Orders appear layered and incremental, absorbing dips instead of pushing breakouts.
This pattern keeps volatility elevated while preventing sharp upside movement. Liquidity builds under the surface, but price remains trapped by steady sell-side pressure.
The result is a market where participation grows without trend confirmation. Exchange activity increases even as the broader structure remains corrective.
Defensive Demand and Early Accumulation Signals
The current environment reflects demand that is present but restrained. Investors appear focused on controlled entries rather than rapid exposure to price swings.
This behavior aligns with early accumulation phases observed during past deep corrections. Ownership changes gradually while price trades sideways or lower.
Another analyst tweet emphasized that stablecoins move before sentiment improves. The message framed the flows as strategic positioning instead of speculative chasing.
Such activity suggests that capital is preparing for longer-term opportunities rather than short-term rebounds. The market shows signs of patience rather than urgency.
Supply continues to dominate short-term price action. Long-term holders, miners, and treasury accounts remain active sellers during relief rallies.
As a result, price fails to convert higher inflows into sustained momentum. Demand absorbs pressure but does not overwhelm it.
This structure often leads to extended basing periods. Price can remain range-bound while liquidity and participation rebuild beneath the surface.
Historical patterns show that either consolidation or a volatility flush can follow this phase. Both outcomes depend on how supply responds to rising demand.
For now, stablecoin inflows signal that investors are no longer absent from the market. Capital is present, but conviction remains measured.
The market continues to adjust through balance rather than reversal. Liquidity growth and selling pressure coexist, shaping a cautious and transitional trading environment.
Crypto World
Aave Umbrella Launches to Automate Bad Debt Coverage and Boost Protocol Security

TLDR:
- Aave Umbrella automates bad debt coverage, reducing reliance on governance intervention.
- Users earn rewards by staking aTokens and GHO while actively securing the protocol.
- Deficit offset mechanisms limit slashing risk, safeguarding stakers during lending stress events.
- Transition from Safety Module ensures seamless integration for existing Aave stakers.
Aave Umbrella arrives as the Aave Protocol leads DeFi with over $50 billion in deposits, weathering recent market volatility. This includes $450 million in collateral liquidations across multiple networks in the past week.
Umbrella automates bad debt coverage and rewards staking participation, enhancing risk management precision and reducing governance delays in one of the largest decentralized lending ecosystems today.
Aave Umbrella Activation and Staking Mechanisms
Aave Umbrella is a modular system designed to manage bad debt in Aave v3 pools. It replaces the legacy Safety Module with automated coverage, relying on on-chain deficit data rather than governance intervention.
Activation begins with Ethereum, focusing on high-borrow-demand assets such as USDC, USDT, WETH, and GHO. Each deployment protects only the asset and network where it is staked, ensuring precise risk isolation.
Staking is central to Umbrella’s design. Users can stake aTokens, including aUSDC, aUSDT, and aWETH, or GHO, Aave’s native stablecoin. aToken stakers continue earning underlying yield while receiving additional Safety Incentives for participating in risk management.
GHO staking provides only Safety Incentives since it does not generate underlying yield. These rewards are claimable on-chain and vary depending on governance configuration.
The system uses a mathematically modeled Emission Curve to balance rewards. Maximum incentives are provided when total staking matches the target liquidity, with higher rewards below target to encourage participation and slightly reduced rewards above target to prevent over-staking.
This ensures predictable APY behavior, avoids extreme fluctuations, and incentivizes optimal engagement from the community.
Risk Management and Deficit Protection
Umbrella integrates slashing risk for stakers, limited to the specific asset and network they support. For example, staking aUSDC only covers USDC deficits.
The system includes first-loss offset mechanisms to protect participants. USDT staking, for instance, has a 100,000 USDT buffer, covering minor deficits before affecting staker assets.
These mechanisms drastically reduce the probability of slashing in typical scenarios. The protocol’s automated liquidation network complements Umbrella by actively managing distressed positions.
When liquidations cannot fully cover bad debt, staked assets in Umbrella are burned to offset deficits. This process eliminates manual intervention and governance delays, enhancing responsiveness and security.
During the first month of Aave v3.3, only $400 of deficits arose against nearly $9.5 billion in borrows, demonstrating Umbrella’s efficiency.
Umbrella allows broader participation in protocol security. Suppliers who are not borrowing can stake assets, actively contribute to risk management, and earn rewards.
Transition mechanisms from the legacy Safety Module ensure that stkAAVE, stkABPT, and stkGHO positions can migrate without immediate slashing risk. This creates an inclusive system where stakers align incentives with protocol health, ensuring long-term resiliency.
Crypto World
China formalizes sweeping ban on crypto trading and RWA tokenization


China has moved to lock down virtually all crypto and real‑world asset (RWA) tokenization activity, issuing a new notice that declares such operations illegal financial activity and extends liability across the entire service stack.
Summary
- A joint PBoC notice declares Bitcoin, Ether, Tether and similar tokens lack legal tender status and brands all virtual‑currency business activity as illegal finance to be “resolutely banned”.
- RWA tokenization is swept into the same risk bucket, with onshore issuance and trading prohibited absent explicit approval and offshore entities barred from serving mainland users.
Core of the new notice
The joint circular from the People’s Bank of China (PBoC) and seven other ministries states bluntly that “virtual currency does not have the same legal status as legal tender” and that tokens such as “Bitcoin, Ether, Tether…do not have legal compensation and shall not and cannot be used as currency in the market.” All “virtual currency‑related business activities” — including fiat–crypto exchange, crypto–crypto trading, market‑making, information intermediation, token issuance and crypto‑linked financial products — “are illegal financial activities” and are to be “strictly prohibited” and “resolutely banned.”
Real‑world asset tokenization is folded into the same risk bucket. Authorities define RWA tokenization as converting ownership or income rights into tokens for issuance and trading, and warn that such activities in China “shall be prohibited” unless explicitly approved on designated financial infrastructure. Offshore entities are also barred from “illegally providing…RWA tokenization‑related services” to onshore users.
Enforcement, mining and offshore routes
The notice hardens the multi‑agency framework first laid out in 2021’s Yinfa No. 237, which labeled key crypto activities as illegal and banned offshore exchanges from serving mainland clients. Financial institutions and payment firms are now forbidden from opening accounts, transferring funds, settling, custoding, or insuring any virtual‑asset‑linked product. Internet platforms may not provide “online business venues, commercial displays, marketing, traffic‑buying or paid promotion” for crypto or RWA services and must help shut down relevant websites, apps and public accounts.
Beijing also renews its campaign against mining, ordering provinces to “comprehensively identify and shut down existing virtual currency ‘mining’ projects” and “strictly prohibit” any new capacity. On offshore structuring, regulators apply a “same business, same risk, same rules” principle: domestic entities and the overseas vehicles they control may not issue virtual currencies or conduct RWA‑style securitizations based on onshore assets without prior approval, filing or registration.
Market context and price action
The clampdown lands in a market where global traders continue to treat digital assets as high‑beta macro risk. Bitcoin (BTC) trades near $66,005, down roughly 7.9% over the last 24 hours. Ethereum (ETH) changes hands around $1,890, lower by about 11.6% on the day. Solana (SOL) sits near $77.8, off approximately 15.4% in 24‑hour terms.
The notice takes immediate effect and simultaneously repeals the landmark 2021 circular on virtual‑currency speculation, signaling that China’s stance has shifted from episodic crackdowns to a durable, high‑pressure regime designed to “maintain economic and financial order and social stability” and leave no grey zone for crypto or RWA experimentation.
Crypto World
ARK Invest Sells Coinbase And Buys Bullish Shares
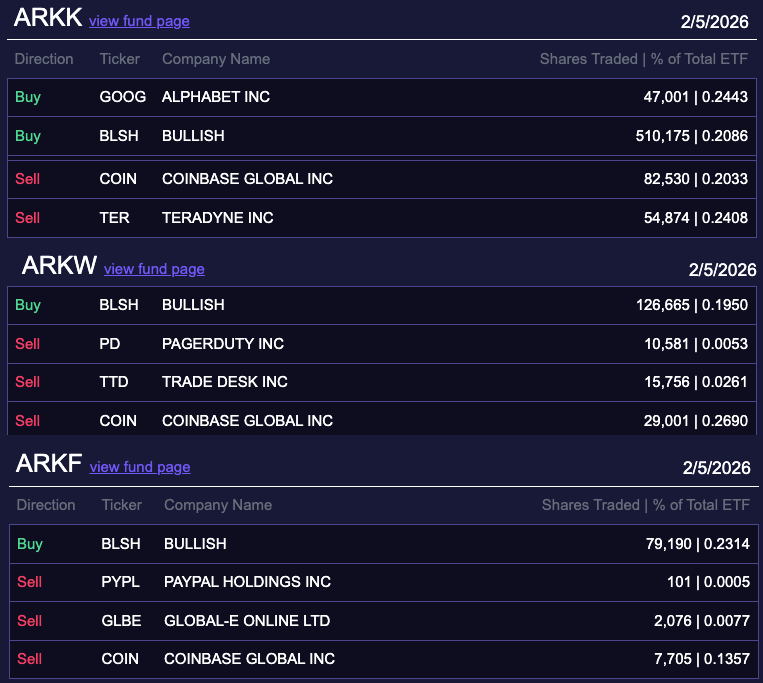
ARK Invest, the asset manager led by prominent Bitcoin bull Cathie Wood, has shifted from buying to selling Coinbase stock, as the shares dipped 13% and hit multi-month lows.
On Thursday, ARK offloaded 119,236 Coinbase (COIN) shares, valued at roughly $17.4 million, according to a trade filing seen by Cointelegraph.
The sale comes just a day after a modest 3,510-share ($630,000) purchase on Tuesday, following a series of buys at higher prices earlier in 2026.
This marks ARK’s first Coinbase sale of 2026 and its first since August 2025, signaling a shift in trading strategy. The cryptocurrency exchange’s stock is down around 37% year-to-date, according to Nasdaq data.
ARK sold Coinbase and bought Bullish
ARK spent almost the same amount it dumped in Coinbase shares to acquire 716,030 shares ($17.8 million) in Bullish (BLSH), an institution-focused digital asset platform that listed on the New York Stock Exchange in August 2025.
Since the trading launch, Bullish shares had slumped more than 60% to $24.9 on Thursday’s close, according to NYSE data.

Related: BlackRock’s IBIT hits daily volume record of $10B amid Bitcoin crash
ARK was one of the largest buyers of Bullish’s IPO, alongside investment giant BlackRock.
ARK holds $312 million in Coinbase stock
ARK’s latest Coinbase sale comes amid a sharp crypto market pullback, with Bitcoin (BTC) dipping below $70,000 on Thursday to briefly touch $60,000 on Friday.
For ARK, a major backer of Coinbase during tough market conditions, the move marks a notable reversal.

To date, ARK still holds $312 million in Coinbase shares across its three funds — the ARK Innovation ETF (ARKK), ARK Next Generation Internet ETF (ARKW) and ARK Fintech Innovation ETF (ARKF), with COIN representing 3.7%, 3.4%, and 4.95% of each fund, respectively.
Since its April 2021 trading debut, Coinbase stock has fallen about 60%, from an opening price of $381, according to Nasdaq data.
Magazine: Bitcoin’s ‘miner exodus,’ UK bans some Coinbase crypto ads: Hodler’s Digest, Jan. 25 – 31
Crypto World
Bitcoin Traders Say $58K is Key as Dip-Buyers Help BTC Rebound 11%
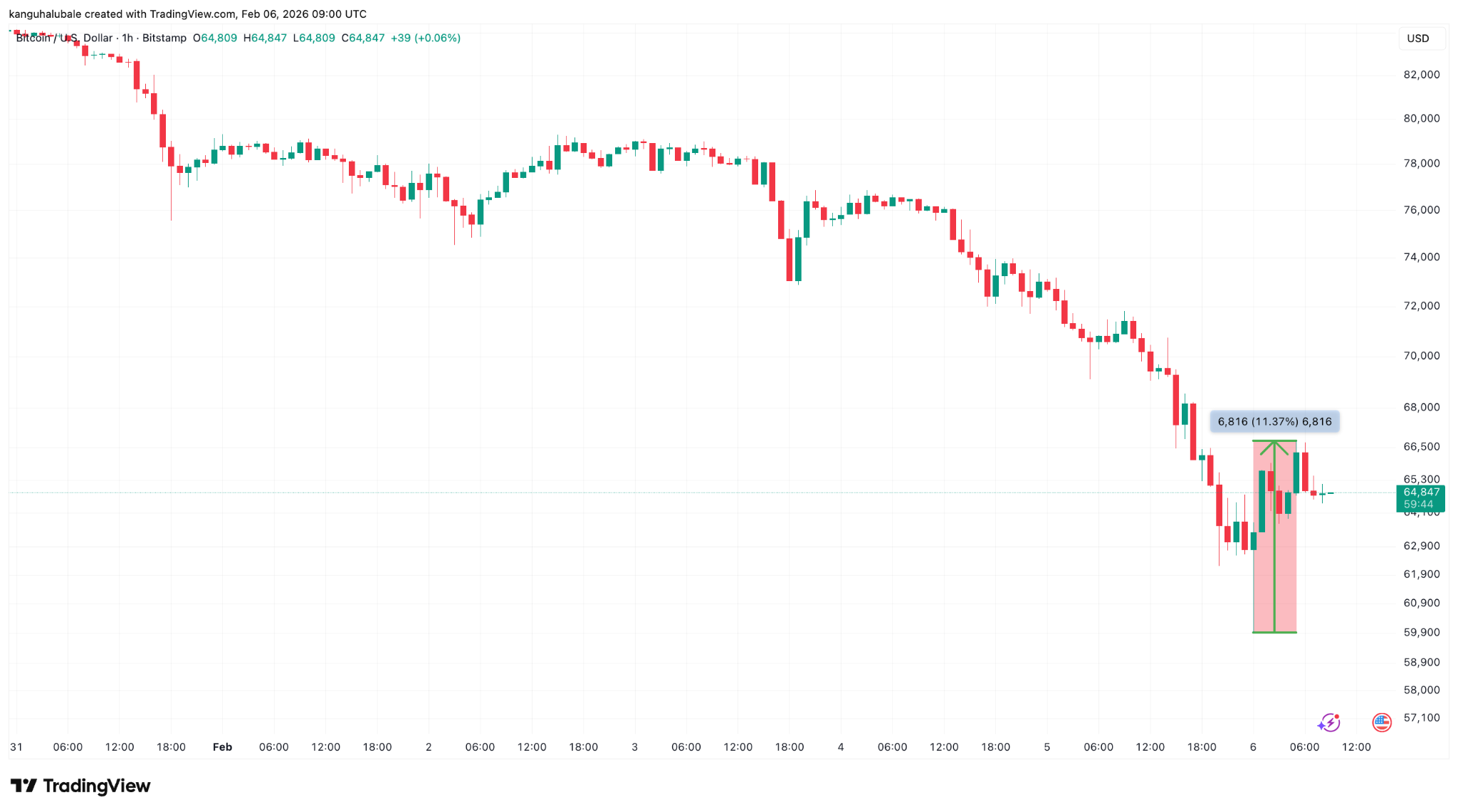
Bitcoin (BTC) rebounded above $65,000 on Friday, up 11% from 15-month lows below $60,000, as focus shifted to institutional dip buyers.
Key takeaways:
-
Bitcoin finally sees investors who are willing to “buy the dip” as prices dropped to sub-$60,000 levels.
-
Traders have shifted their focus to $58,000 as the last line of defense for Bitcoin.

Bitcoin wipes out $1.1 billion longs on drop to $59,000
Bitcoin price fell as low as $60,000 on Thursday, erasing 15 months of bullish gains as investors accumulated more at lower levels.
This extended the drop from its all-time high of $126,000 reached on Oct. 6, 2025, to 50% and was accompanied by massive liquidations across the derivatives market.
Related: Big questions: Should you sell your Bitcoin for nickels for a 43% profit?
Data from monitoring resource CoinGlass showed crypto liquidations over 24 hours nearing $2.6 billion, with longs accounting for $2.15 billion. Bitcoin accounted for $1.1 billion in long liquidations.

Bitcoin dip-buyers finally emerge
Binance’s Secure Asset Fund for Users (SAFU), an insurance fund established by Binance in July 2018 to protect users’ assets, bought another 3,600 BTC worth $250 million at about $65,000 per BTC.

Last week, Binance announced its intention to convert $1 billion SAFU reserves into Bitcoin over the next 30 days.
The first batch of 1,315 BTC, worth about $100 million was bought earlier this week, leaving $565 million more to be converted.
Crypto hedge funds have also been buying the dip, data from Bitwise shows.
The aggregate market beta across all global crypto hedge funds hit its “highest level in 2 years” as Bitcoin weakened, European head of research at Bitwise André Dragosch said in a Friday post on X, adding:
“This signals increasing $BTC market exposure by global crypto hedge funds.”

Dragosch also said that record ETF volumes amid moderate net outflows on Thursday suggested that there “were lots of dip buying” by US-based spot Bitcoin ETFs as well.

200-week MA: Bitcoin’s last line of defense?
BTC touched lows below $60,000, leaving traders to question where Bitcoin was likely to find a bottom.
“$BTC is testing the previous cycle highs, and bouncing slightly so far,” said trader Jelle in a Friday post on X.
According to Jelle, Bitcoin was required to hold a key area of interest between $58,000 and $62,000 to avoid a deeper correction.
“Time to see if we start basing here, or if we just roll over again.”

The $58,000 level coincides with the 200-day SMA, a key support level for BTC price, according to MN Capital founder Michael van de Poppe.
Given that Thursday’s $10,000 drop was the largest volume candle on record, the “assumption can be made that we hit the low there, for now,” van de Poppe said, adding:
“If prices can rally up slightly, we’re going to see a large wick. Like we always see with capitulation events.”

As Cointelegraph reported, Bitcoin’s demand zone now sits above $58,000, supported by historic transaction volume and the 200-week moving average.
This article does not contain investment advice or recommendations. Every investment and trading move involves risk, and readers should conduct their own research when making a decision. While we strive to provide accurate and timely information, Cointelegraph does not guarantee the accuracy, completeness, or reliability of any information in this article. This article may contain forward-looking statements that are subject to risks and uncertainties. Cointelegraph will not be liable for any loss or damage arising from your reliance on this information.
Crypto World
Google Search Volume For ‘Bitcoin’ Surges Amid $60K Plunge
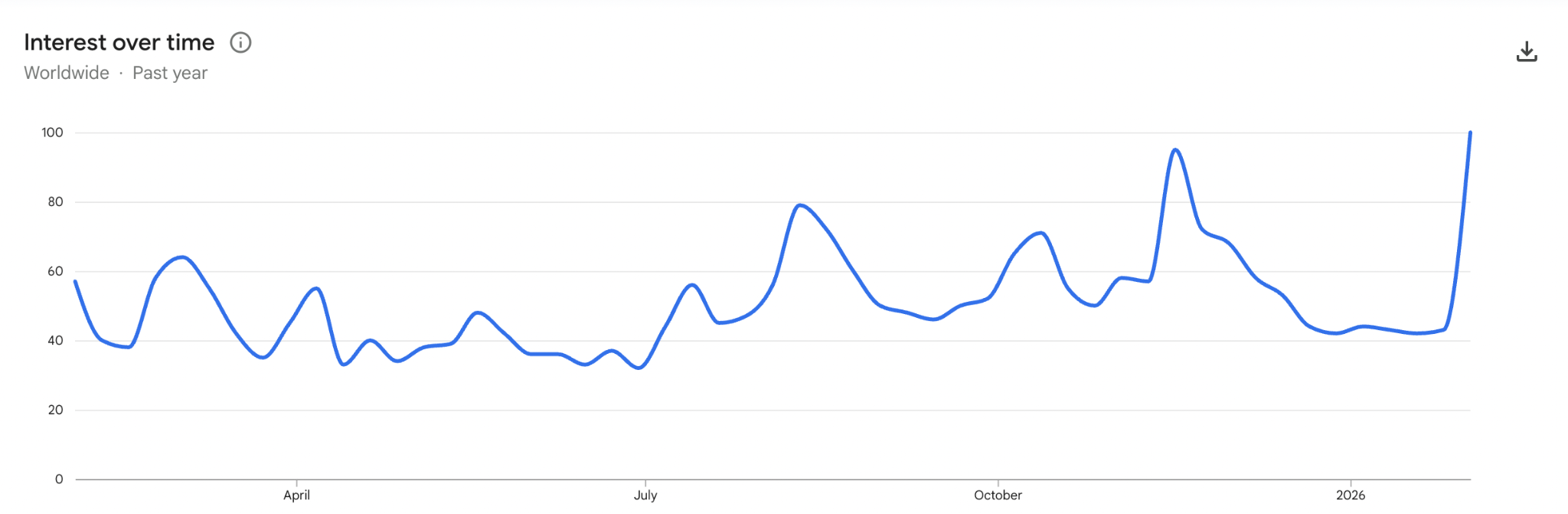
Google search volume for the term “Bitcoin” surged over the past week as the asset’s price briefly fell to the $60,000 level for the first time since October 2024.
Google Trends provisional data shows worldwide searches for “Bitcoin” reached a score of 100 for the week starting Feb. 1, the highest level in the past 12 months.
The previous peak was a score of 95 in the week of Nov. 16–23, when Bitcoin (BTC) slipped below the psychological $100,000 level for the first time in nearly six months.

Google search interest is one of several commonly used indicators among crypto analysts to gauge retail interest in Bitcoin and the broader crypto market, which typically spikes during significant price moves, particularly major rallies to new all-time highs or sudden sell-offs.
The increase comes as Bitcoin dropped from about $81,500 on Feb. 1 to roughly $60,000 within five days, before rebounding to $70,740 at the time of publication, according to CoinMarketCap.

Some market observers suggest the current price range may be drawing renewed attention from a broader retail audience. Bitwise head of Europe, André Dragosch, said in an X post on Saturday, “Retail is coming back.”
Meanwhile, CryptoQuant’s head of research, Julio Moreno, said in an X post on Saturday that US investors are buying Bitcoin after it reached $60,000. “The Coinbase premium is now positive for the first time since mid-January,” Moreno said.
Other indicators suggest that investors are still cautious about the crypto market. The Alternative.me Crypto Fear & Greed Index fell further down once again on Saturday to an “Extreme Fear” score of 6, nearing levels that haven’t been seen since June 2022.
Related: Crypto’s stress test hits balance sheets as Bitcoin, Ether collapse
The sentiment indicator’s decline to such low levels has led some market participants to suggest it could signal a buying opportunity.
Crypto analyst Ran Neuner said in an X post on Friday that, “every single metric is telling you that Bitcoin has never been more undervalued on a relative basis.”
Magazine: Bitcoin’s ‘biggest bull catalyst’ would be Saylor’s liquidation: Santiment founder
-

 Video4 days ago
Video4 days agoWhen Money Enters #motivation #mindset #selfimprovement
-

 Tech3 days ago
Tech3 days agoWikipedia volunteers spent years cataloging AI tells. Now there’s a plugin to avoid them.
-

 Politics5 days ago
Politics5 days agoSky News Presenter Criticises Lord Mandelson As Greedy And Duplicitous
-

 Crypto World7 days ago
Crypto World7 days agoU.S. government enters partial shutdown, here’s how it impacts bitcoin and ether
-

 Sports6 days ago
Sports6 days agoSinner battles Australian Open heat to enter last 16, injured Osaka pulls out
-
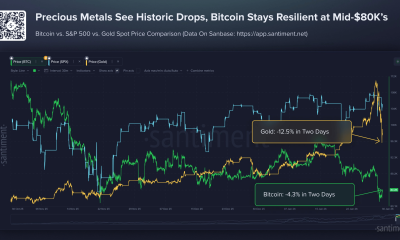
 Crypto World6 days ago
Crypto World6 days agoBitcoin Drops Below $80K, But New Buyers are Entering the Market
-

 Tech11 hours ago
Tech11 hours agoFirst multi-coronavirus vaccine enters human testing, built on UW Medicine technology
-

 Sports3 hours ago
Sports3 hours agoJD Vance booed as Team USA enters Winter Olympics opening ceremony
-
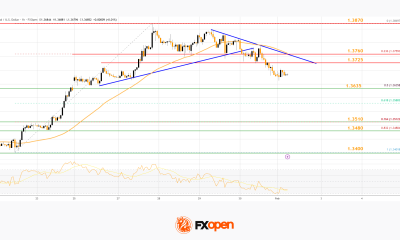
 Crypto World5 days ago
Crypto World5 days agoMarket Analysis: GBP/USD Retreats From Highs As EUR/GBP Enters Holding Pattern
-
Sports20 hours ago
New and Huge Defender Enter Vikings’ Mock Draft Orbit
-

 NewsBeat16 hours ago
NewsBeat16 hours agoSavannah Guthrie’s mother’s blood was found on porch of home, police confirm as search enters sixth day: Live
-

 Business2 days ago
Business2 days agoQuiz enters administration for third time
-

 NewsBeat4 days ago
NewsBeat4 days agoUS-brokered Russia-Ukraine talks are resuming this week
-

 Sports5 days ago
Sports5 days agoShannon Birchard enters Canadian curling history with sixth Scotties title
-

 NewsBeat5 days ago
NewsBeat5 days agoGAME to close all standalone stores in the UK after it enters administration
-

 NewsBeat2 days ago
NewsBeat2 days agoStill time to enter Bolton News’ Best Hairdresser 2026 competition
-

 NewsBeat4 hours ago
NewsBeat4 hours agoDriving instructor urges all learners to do 1 check before entering roundabout
-

 Crypto World3 days ago
Crypto World3 days agoRussia’s Largest Bitcoin Miner BitRiver Enters Bankruptcy Proceedings: Report
-

 NewsBeat4 days ago
NewsBeat4 days agoImages of Mamdani with Epstein are AI-generated. Here’s how we know
-

 Crypto World2 days ago
Crypto World2 days agoHere’s Why Bitcoin Analysts Say BTC Market Has Entered “Full Capitulation”








