A huge band of snow is set to hit the UK on Sunday morning (February 15)
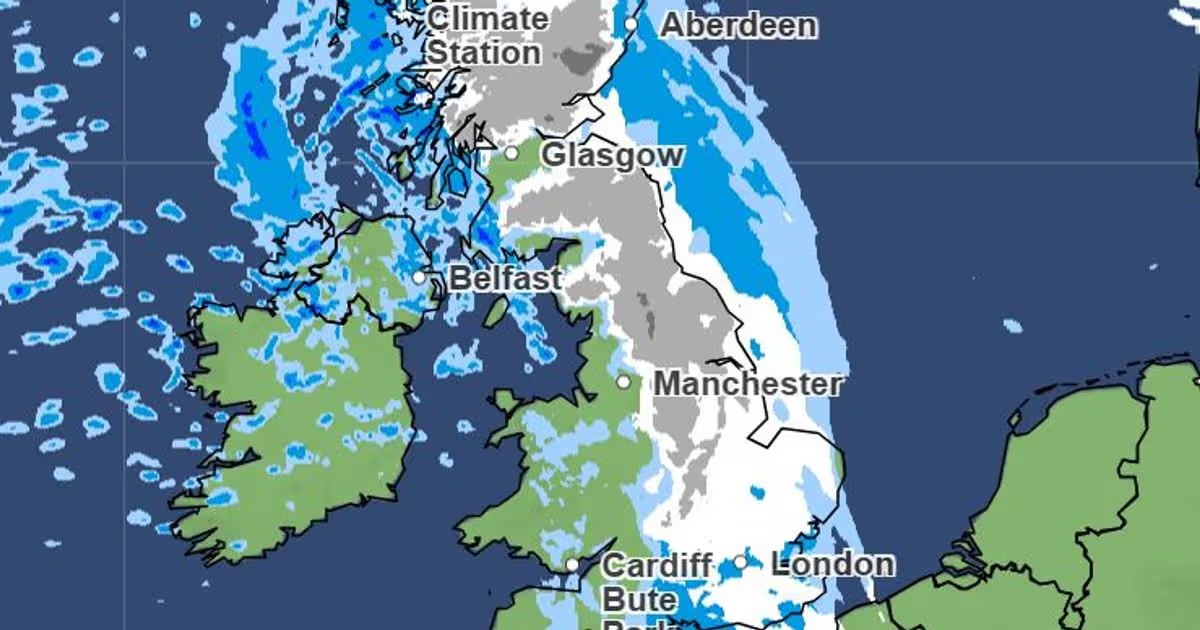
A huge 860km wall of snow is set to hit the UK this weekend, with Met Office weather maps now showing exactly what time and which areas will be affected.
It comes after the UK is seeing record-breaking levels of rain, with forecasters warning that there are ‘no signs’ of a prolonged dry spell for at least seven to 10 days.
As of Tuesday afternoon (February 10) there are 97 ‘act now’ flood warnings in force across the UK as well as 154 ‘flooding is possible’ alerts.
And now, Met Office maps show a huge band of snow heading towards the UK on Sunday (February 15), spanning a whopping 860km.
At 9am on Sunday, Met Office maps reveal a wall of snow which stretches all the way from Brighton in the south of England to the village of Durness in Scotland.
Before then though, at 6am, the band is snow is slightly smaller, stretching from the Midlands all the way up to Scotland.
By 12pm on Sunday, it looks as though most of the snow has passed over the UK, leaving rain and some dry patches in its wake.
The Met Office has not issued any severe weather warnings for the weekend, however forecasters urge people to stay up to date with the latest weather forecast in your area.
Met Office’s UK-wide forecast for Thursday to Saturday reads: “Unsettled at first with further outbreaks of rain. Turning colder from Friday with a chance of snow showers, particularly in the north. Dry, cold and sunny for many on Saturday.”
Looking at the long-range weather forecast which covers the time between February 15 and 24, the Met Office says: “Showers or longer spells of rain are expected as Atlantic low pressure systems dominate in the vicinity of the UK.
“Some heavy rain is likely in places, probably focussed on western hills, with some snow at times in the north, mainly on high ground. Strong winds are possible at times, especially around coasts.
“Temperatures will probably be near normal. Later in the period, there is a chance that drier, more settled conditions may begin to develop.”
And looking even further ahead at the period between February 25 and March 11, the Met Office forecast reads: “Low confidence in the dominant weather patterns during this period.
“There are signals for both changeable, unsettled conditions, bringing a risk of some heavy rain, and also periods of drier, more settled weather, which may mean colder conditions.”
The forecast concludes: “The latter, more settled pattern is looking slightly more probable at this stage.”