Entertainment
Which America’s Next Top Model Contestants Spoke Out About Netflix Documentary?
America’s Next Top Model’s most memorable contestants aren’t staying quiet about their experience on TV.
After more than 24 seasons, the reality show is being put under the microscope in a new Netflix docuseries titled Reality Check: Inside America’s Next Top Model.
While host Tyra Banks and judges J. Alexander, Jay Manuel and Nigel Barker are featured in the new project, many viewers are interested in the untold stories by some of the show’s breakout stars.
Since Reality Check premiered on Netflix on February 16, 2026, several contestants have shared their honest and unfiltered reviews of the project. Some are even commenting on Banks’ involvement with the show.
“When I signed on for it, Tyra wasn’t even going to be on the show, so I was kind of surprised that it was more like a judge-focused show,” cycle 10 winner Whitney Thompson said via Instagram on February 17, 2026. “I would want to hear more from the contestants.”
Keep reading to see what cast members are saying about Reality Check and if it’s an accurate representation of their experience on America’s Next Top Model:
Shandi Sullivan

Shandi Sullivan Courtesy of Netflix
America’s Next Top Model cycle 2 finalist Shandi Sullivan claimed that she was sexually assaulted during a group trip to Italy during her time on the show. Now that she’s shared more of her experience, Sullivan is grateful for the support.
“Welp the documentary is out and now you know more of my story…after all of the years the Top Model girls and what we went through were never forgotten,” Sullivan wrote via Facebook on February 16, 2026. “At the age of 43, I continue to struggle with it; always smiling. That’s why I took this opportunity. Knowing that Tyra didn’t have control over my narrative, that the director and producers here had my back…that’s why I did it. I did it for me. Because I mattered and I still do! The love I have felt today has been immense. Thank you to everyone that heard me.”
Whitney Thompson

Whitney Thompson Courtesy of Netflix
America’s Next Top Model cycle 10 winner Whitney Thompson addressed the criticism Tyra Banks was receiving from the docuseries.
“Hating Tyra is easy, right? I mean, it’s easy to blame her. But the truth is that the industry would not be what it is today if it wasn’t for her putting these things on Top Model back then,” Thompson claimed via Instagram on February 17, 2026. “We would not be gasping at the craziness that she put on TV if she hadn’t done it and shifted our entire mindset. She took queer, Black, trans, different weights, different heights and she put them into the average American’s living room where everyone was together watching these shows, rooting for someone who didn’t necessarily look like them.”
The model continued, “Because of that, it shifted the whole dynamic to where people could actually use people who weren’t identical to them in advertising. That had never happened before.”
Tiffany Richardson
America’s Next Top Model cycle 4 contestant Tiffany Richardson won’t forget the way Tyra Banks yelled at her before being eliminated.
“Hold up @tyrabanks let’s keep it cute … you know how you treated me the whole time off and on camera, YOU WAS A BULLY!!! You treated me like s*** and said the nastiest things about me and my son,” Richardson claimed in a since deleted Instagram post. “That is not how the argument went but YALL EDITED TO MAKE IT LOOK LIKE YOU CARED.”
Banks admitted in the docuseries that she “went too far” while addressing the “tough” moment.
“You know, I lost it. It was probably bigger than her. It was family, friends, society, Black girls, all the challenges that we have,” she explained. “So many people saying that we’re not good enough. I think all that was in that moment. That’s some Black girl stuff that goes real deep inside of me, but I knew I went too far.”
Adrianne Curry
Although America’s Next Top Model cycle 1 winner Adrianne Curry declined to participate in the Netflix doc, she spoke out about the project on social media.
“I was just told one of the Top Model judges admitted they’d advance girls that were not the best models…just good tv,” Curry wrote via X on February 17, 2026. “That was me. I’ve said it for years, I never was the best one. I just had the best sob story. It is nice to have it confirmed.”
Keenyah Hill

America’s Next Top Model cycle 4 contestant Keenyah Hill participated in the Netflix doc with hopes that her story would be shared accurately.
“I’m grateful for the opportunity to lend my voice about my experience on America’s Next Top Model,” Hill wrote via Instagram on February 16, 2026, before watching the finished product. “Sending SO MUCH LOVE to the ANTM Alumni ❤️. I know we all had very different experiences on the show and I feel for everyone who had to heal from the aftermath with half the world watching!! Grateful to have been a part of such a legendary show… Can’t wait to watch 🍿.”
Lisa D’Amato
America’s Next Top Model cycle 17 winner Lisa D’Amato is hopeful that E!’s upcoming project titled Dirty Rotten Scandal will be a more revealing look at the reality TV franchise she was a part of.
“#ANTM #NETFLIX mark your calendars for Dirty Rotten Scandal’s on E! March 11th,” D’Amato wrote via Instagram on February 16, 2026. “The Netflix was still very tame and sugarcoated compared to a lot of us and what happened behind the scenes to US that they kept silenced. We will have the last word. Thank you 🙏 All my love to @miss_jalexander ♥️.”
Eva Marcille
Eva Marcille, who won the third cycle of America’s Next Top Model, revealed she was “gobsmacked” after watching Reality Check: Inside America’s Next Top Model.
“I was in awe … My mouth was wide open,” she said in a February 2026 interview with CBS Mornings. “To be a part of a club, and not know what’s going on in the club is crazy.”
Marcille, who was not approached to be in the doc, added that she was horrified to hear some of the stories mentioned in the Netflix documentary.
“I’ve lived my experience. I’ve walked in my shoes. And though there is a level of relatability one would assume, someone having walked in the same shoes, I had no idea. Absolutely no idea. I have been asked about Tyra for 21 years,” she explained. “No matter what project I’m doing, what I’m involved in, somehow Top Model finds its way in my interview.”
Continue Reading
Entertainment
‘The Pitt’s Shawn Hatosy Explains How Abbot’s “Unexpected” Arrival Shakes Up This Season

Editor’s note: The below interview contains spoilers up to The Pitt Season 2 Episode 7.
With HBO’s The Pitt now returned for Season 2, the latest shift for the doctors and nurses working in the emergency department of the fictional Pittsburgh Trauma Medical Center just got even more complicated. This week’s episode, “1:00 P.M.,” reveals the real reason behind Westbridge Hospital’s “Code Black,” which has resulted in all of their patients being diverted to PTMC: hospitals are being hit with a cyberattack, and to avoid the same fate, The Pitt has to go offline.
Before that happens, however, the seventh hour of R. Scott Gemmill, John Wells, and Noah Wyle‘s medical drama finally welcomes in a familiar face in the form of Shawn Hatosy‘s Dr. Jack Abbot, who rolls in with a SWAT team seemingly just in time to help the ER buckle down for the worst. With the hospital’s CEO going above Dr. Robby (Wyle) to fill in Dr. Al-Hashimi (Sepideh Moafi) on what’s going on, will that only add to the tension that’s been brewing between them since the beginning of the shift? Ahead of The Pitt‘s return, Collider had the opportunity to speak with the show’s creators and cast alike about some of Season 2’s most pivotal moments over the first six episodes, including Hatosy and Moafi. Below, the co-stars discuss Abbot’s unexpected entrance in Season 2, why Robby and Al-Hashimi’s conflict is a joy to play, which Season 1 moment Hatosy still feels did Abbot dirty, and more.
COLLIDER: Shawn, what can you tee up for us about Abbot and what we can look forward to when he finally rolls in this season?
SHAWN HATOSY: Well, when we last left Abbot, he was up on the roof with Robby, talking him off the ledge. He says at the end of that season, “My therapist says I find comfort in the darkness.” He tries to tell Robby that maybe he should talk to a therapist, so I think as we come into Season 2, we’re definitely going to be checking in on that to make sure that the toll that this job is taking on Robby isn’t going to be too much.
That’s one of Abbot’s focuses. The other thing is he comes in in a very unexpected way. He actually moonlights on a SWAT team. They often use a doctor on SWAT teams in case something goes wrong, who is qualified to carry a gun. So something wild happens, and he has to come in, and that’s how he shows up in fatigues. That’s where he meets the great new attending physician, Dr. Al-Hashimi.
Sepideh Moafi Reveals What She Enjoys About Going Head-to-Head With Noah Wyle in ‘The Pitt’ Season 2
“You’re used to calling the shots, both of us, with our respective backgrounds.”
To tie this all into Robby, we know at the beginning of Season 2 that he is set to be taking a sabbatical. It sounds like a much-needed one. Dr. Al-Hashimi is intended to be his replacement, stepping in, but there’s been a bit of overlap. She’s there, he’s there, and we immediately see that these two have very different leadership styles. There is that initial rockiness of who should take the lead and with which med students, and who should be stepping back. Sepideh, I wanted to ask you about what you enjoyed about getting to go through those bumpy moments with Noah [Wyle] at the beginning of the season.
SEPIDEH MOAFI: Oh my gosh, those moments are so delicious where we’re talking over each other or finishing each other’s sentences, not on purpose. It’s so fun as the actor to play, and as the character, it’s a bit jarring, because you’re used to having the leadership role. You’re used to calling the shots, both of us, with our respective backgrounds. Now it’s two people in leadership positions, and one, as I think you mentioned, has a very different approach to medicine.
Dr. Al-Hashimi represents the more modern approach, the modernization of medicine, and Dr. Robby is the more traditional, sort of old-school approach. So sometimes, they clash, these two different approaches and personalities. He’s not used to having somebody else there who calls the shots and who’s in charge. She’s, as a woman in any profession, used to male counterparts being a bit cutting or condescending at times, but she takes it in stride and knows that they are both really good at their jobs. They just have different ins into medicine.
Ultimately, there is some harmony. They do harmonize together — though there is a lot of dissonance, too, throughout the season. But just for us as actors, Noah [Wyle] and I playing these scenes, it’s so much fun because it requires such radical presence and aliveness and really listening to each other and trying to hold back in certain moments and then other moments just letting loose. So, it’s been quite a journey, and I’m excited for people to experience that journey.

‘The Pitt’s Noah Wyle Reacts to That Heartbreaking Patient Death: “It’s a Funeral With a Clock”
Wyle also teases whether the tension between Robby and Langdon will eventually boil over by the end of this shift.
One quote that Dr. Al-Hashimi has in this season that really stuck out to me and felt like almost an unofficial mantra for this character and who she is is when you have the line of “Just because you know it’s broken doesn’t mean you stop trying.” [She’s] talking about a lot of the failures of the modern healthcare system and the places where maybe the hospital isn’t as well-equipped to handle certain issues. Do you feel like that is what sums her up in her approach to medicine? “I understand that the system I’m working in isn’t perfect, but that doesn’t mean I’m going to stop looking for ways to try and fix it, even if they’re small fixes here and there”?
MOAFI: Absolutely. I think if there were a few lines that were at her core, her foundation, that would be one of them. I would take it a step further and say it’s not that she thinks the system is not perfect. She knows it’s a broken system, which is why she’s finding alternative ways, different modalities of reorganizing, reshaping, and advancing medicine. At the beginning, as you saw, there was an introduction where she’s talking about using AI or using technology in order to implement some of these changes. Not for novelty’s sake, but in order to improve patient-centered care and medicine, in order to relieve some of the burden that these physicians carry every day, the emotional weight, the bandwidth. There’s always too much need in the hospitals and not enough time, and we are all human.
The whole idea with her approach to AI is that you are able to delegate some of this responsibility, able to offload some of this admin charting. I think it’s something like 28% of a physician’s time is spent at the patient’s bedside. The other 72% is spent charting or doing admin work. So, if we’re able to relieve some of that pressure, some of that workload, with the strict supervision of the physicians, of the nurses, then this could be beneficial for everyone. The idea is not to have technology take over, but to relieve some of the burden. You have to fixate on the light. You have to hold this myopic approach to healing, and where can we find little glimmers of hope that’ll keep us going? So, like you said, this is a constitutional part of who she is, this idea that just because something isn’t working or it’s broken, it doesn’t mean that you stop the fight.
For the Record, Shawn Hatosy Has Great Hand-Eye Coordination (Even if ‘The Pitt’ Season 1 Did Him Dirty)
“I just want to state for the record that I am an amazing athlete.”
Shawn, one of my favorite moments from last season is the moment where everybody circles up outside the hospital, has some beers in the park, and it’s nice to see the doctors and the nurses getting a chance to take a break from the craziness of the shift. Is there anything along those lines that we can look forward to in Season 2, potentially a little bit of downtime?
HATOSY: I think so. And I just want to say that when they throw Abbot the beer, and he doesn’t catch it, that was scripted. I’m a stellar athlete, and I just want everybody to know that there was a line when he drops it that said, “Now you know why I didn’t become a surgeon,” and they cut that line. So it just makes Abbot look clumsy and not athletic, and I just want to state for the record that I am an amazing athlete. I just want you to know that.
MOAFI: Shawn has trauma from that moment. It’s still affecting him.
HATOSY: I do think there is a moment of everybody coming together.
But just so that we have it on the record: great hand-eye coordination from Shawn Hatosy.
HATOSY: Can you please just let this be the headline of the article?
We’re going to clear some things up.
HATOSY: How are they going to leave an actor hanging like that? Cut out the line, and then just make him look clumsy. Who does that?
Entertainment
Kristin Bell’s 4-Part Cult Classic Finally Hits Netflix After Its Unexpected End

The mid-aughts were a treasure trove of heightened teen dramas, and in its day, Veronica Mars was the crème of the crop. The series was a perfect combination of film noir tropes within the heightened world of teen drama. Starring Kristen Bell as the titular teen detective, Veronica Mars was full of wit while also delving into mature topics set in a high school setting. The daughter of a former sheriff turned private investigator, Keith Mars (Enrico Colantoni), Veronica is devastated when her best friend Lilly Kane (Amanda Seyfried) is murdered. In typical film noir fashion, Keith turns into a hard-boiled detective after he ruins his career by accusing the Kane family of foul play.
Veronica’s social cachet is destroyed when she sides with her father, even though this weaponizes her friends against her. She loses her boyfriend, Duncan (Teddy Dunn), and becomes a social pariah. The worst treatment comes from Lilly’s boyfriend, Logan (Jason Dohring), who makes it his purpose in life to ruin hers after what Keith did. Veronica Mars cleverly takes the genre of film noir and adapts it for a high school setting as Veronica becomes just as clever as her father in solving crimes. As she continues to look into Lilly’s case, refusing to believe the killer has been caught, her romantic life develops as well. Bell’s chemistry with Dohring was unavoidable, and their respective characters grow closer because of it. This setup leads to an epic romance between Veronica and Logan, which spans the life of the series. This fact is ultimately what put the nail in the coffin for the series, despite all its potential.
‘Veronica Mars’ Season 4 Shocker Ruined What Was So Good About the Series
Veronica Mars’ cult status was secured long before the last season of the series premiered. After the UPN merger with The WB, the series tragically only lasted one more season. Season 3 ends in the college setting, leaving Veronica and Logan’s relationship up in the air. Much like Veronica herself, fans demanded justice and eventually got it with the 2014 fan-funded film. The Veronica Mars movie gave Veronica and Logan the ending they deserved without the characters skipping a beat.
The film gave the series the momentum it needed to return in the streaming age with another season on Hulu. This result regrettably had a less than favorable response. Because Veronica returns to Neptune, California, as an adult, the series effectively became more mature. Veronica’s relationship with Logan becomes more complex, which was not necessarily a direction that fans were interested in. The couple’s engagement and subsequent marriage end in tragedy after Logan is killed by a car bomb meant for Veronica. This tragedy turns her into a jaded version of herself who is a far cry from the character that fans fell in love with in the first place.
Logan is the MVP of ‘Veronica Mars’
Veronica Mars still maintains a 92% on Rotten Tomatoes, a fact that is soured by the destruction of one of the main selling points of the series. Jason Dohring steals the show in absolutely every scene he’s in. His snappy one-liners and fleshed-out backstory made him a fan-favorite. This is one of the reasons why he so quickly turns from a one-dimensional villain in the first season to a complex character with depth. Fans fell in love with him after seeing him as the survivor of domestic abuse at home. It redefined the character for everyone and revealed the vulnerability of the character.
His relationship with Veronica isn’t forced, but a gradual coming together of two people who have lost something. Both Logan and Veronica are filled with rage about Lilly’s death, and though they initially point it at each other, it becomes clear that they are the only two people in the world who can understand each other. Logan began the conversation of what an epic romance could look like and took fans along for the ride.
Logan’s death at the end of the season wasn’t just a move made for shock value. It also shook the foundation of why fans fell in love with the show in the first place, turning it into something that felt unrecognizable. Season 4 was left in Hulu limbo after the fact, with no clear plans to return.
Veronica Mars is now available to Netflix subscribers, with the extra season tacked on for those interested in seeing the full story, for better or worse. The ending was certainly controversial, but that doesn’t stop the beauty of the first few seasons from remaining intact. Veronica Mars became a cult classic for a reason, hammering home themes around sexual assault, domestic abuse, and class structure. It remains a perfect time capsule of the 2000s, which fans can finally enjoy on Netflix.

- Release Date
-
2004 – 2019
- Network
-
UPN, The CW, Hulu
- Directors
-
John T. Kretchmer, Nick Marck, Michael Fields, Harry Winer, Jason Bloom, Steve Gomer, Guy Norman Bee, Marcos Siega, Mark Piznarski, Sarah Pia Anderson, Scott Winant, Dan Etheridge, David Barrett, Joaquin Sedillo, Kevin Bray, Martha Mitchell, Nick Gomez, Rick Rosenthal, Tessa Blake, Tricia Brock, Amanda Marsalis
- Writers
-
John Enbom, Phil Klemmer, Dayna Lynne North, Jed Seidel, Aury Wallington
Entertainment
Brooke Hogan Toys With Foot Fetish Modeling Since She’s Got the Goods
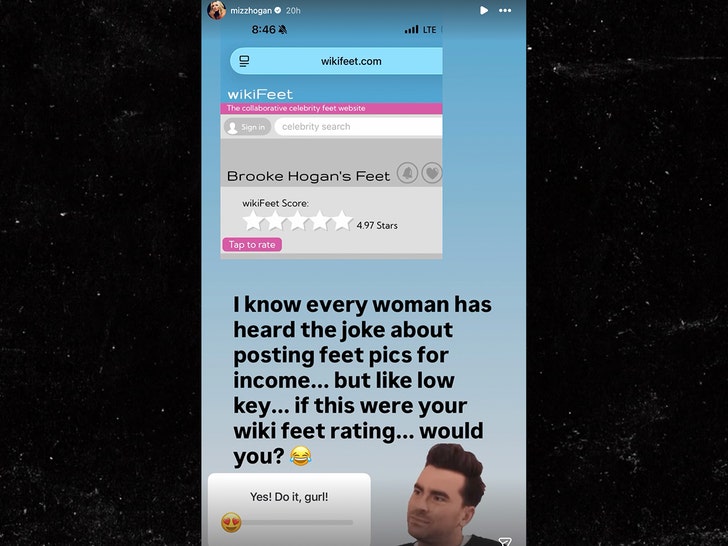
Brooke Hogan
Should I $ell Foot Pics?!?
Published
|
Updated
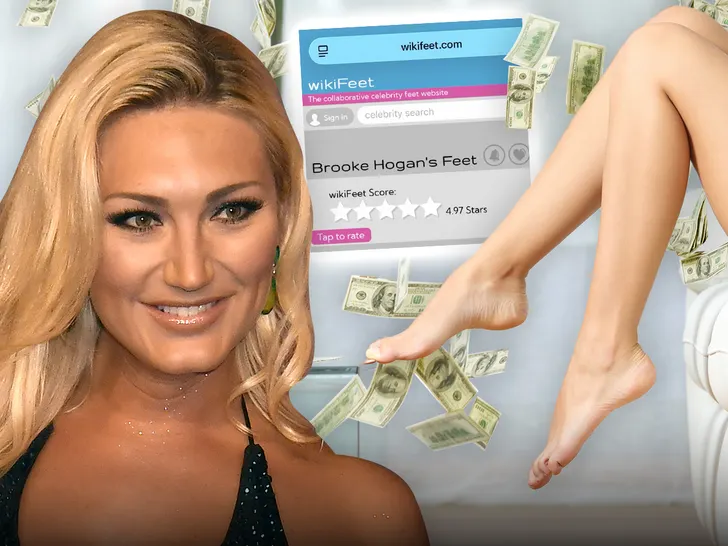
Brooke Hogan‘s got a couple aces in the whole … ’cause she sounds pretty confident she could make big bucks selling pictures of her feet to strangers.
The singer took to her Instagram Story to ask her followers if she should post feet pics for a new income stream.
On its face, it looks like Brooke is seriously considering this … because she went to wikiFEET — the fetish website rating celeb feet — and found out hers are a 4.97 out of 5.
Lots of women make money selling foot pics to strangers … so Brooke wouldn’t be the first or the last to go this route.
Money’s not a big motivator for Brooke, though … she wanted to be left out of her father Hulk Hogan‘s will to avoid family infighting over funds.

TMZ.com
But, Brooke’s definitely got the goods. Just sayin’ 🤷♂️.
Entertainment
Eva Marcille ‘Will Never Fail To Thank Tyra’ Amid ‘ANTM’ Backlash

Eva Marcille continues her long history of thanking Tyra Banks for changing her life, as the “America’s Next Top Model” host is currently under fire following the explosive documentary about the modeling reality competition show.
In a new interview, the Cycle 3 winner shared her thoughts about the supermodel, what she saw in the documentary, the world of reality television, and more.
Article continues below advertisement
Eva Marcille ‘Will Never Fail To Thank Tyra’ Amid Backlash From Explosive ‘ANTM’ Documentary

Eva Marcille is easily the most successful person to ever come from “America’s Next Top Model,” as the actress has maintained longevity in the entertainment industry since she won the show over 20 years ago, and she credits Tyra Banks as the catalyst for making it happen.
During an appearance on “CBS Mornings” on Thursday, February 19, PEOPLE reported that Marcille was naturally asked about the Netflix documentary about the show, which has been a heavy topic of conversation since its release earlier this week, and she shared her perspective.
Article continues below advertisement
“I have been asked about Tyra for 21 years,” the former “Real Housewives of Atlanta” star said. “No matter what project I’m doing, what I’m involved in, somehow ‘Top Model’ finds its way in my interview. I’ve done 154 projects since ‘Top Model.’ It’s been 21 years.”
Marcille then shared that she will always thank Banks, something she has consistently done for decades, for changing her life for the better.
“Thanks to ‘Top Model,’ though,” she said. “What I will say is I will never fail to thank Tyra. What Tyra set out to do in this business, I will always say — and especially for ‘Top Model,’ initially — she set out to change the world; to change what the modeling industry looked like, sound like, felt like and expected. And she did that for me.”
Article continues below advertisement
Marcille also pointed out that it was “very surprising” that she was not asked to participate in the documentary.
Article continues below advertisement
Marcille Addresses Banks’ Apologies In The Documentary

“I saw the show. She apologized a million times,” Marcille stated. “But an apology to the person that you wronged is only as good as they could appreciate it.”
“And so for the young girls who were sexually assaulted… for the young girls who now have eating disorders or look at themselves and never feel beautiful — that little girl in them that will always live in the woman that is them — there is no sorry, I think, that’s big enough to truly feel and heal that kind of hurt,” she added.
Article continues below advertisement
The Actress Notes That Banks Believing In Her Early On Gave Her Confidence

Marcille shared that given her height, she didn’t think her “ANTM” win would even be possible, but Banks saw something in her that made her realize her modeling dreams.
“Being that I was the shortest girl on my season, and the idea of a Black girl and this short in the modeling business, it’s unheard of. It will never happen,” the “All The Queen’s Men” star said.
“We were kids trying to find our dreams realized and actualized by a woman who believed could do it for us,” Marcille said of Banks and her support during her time on the show. “And if she could see it in us, then the world could see it in us because the world sees it in her.”
Eva Marcille Says She Was ‘Gobsmacked’ Watching The Documentary

“I watched it and after I watched it, I was gobsmacked,” Marcille admitted on “CBS Mornings.” She added, “I was in awe … my mouth was wide open. To be a part of a club, and not know what’s going on in the club is crazy.”
“That environment could not exist without producers aiding and embedding what was going on,” she said. “It’s a part of how this thing works.”
Marcille found herself in the middle of ongoing drama during her two seasons on the “Real Housewives of Atlanta,” and the Peacock spinoff, “Real Housewives: Ultimate Girls’ Trip.”
Entertainment
Guess Who These Adorable Kiddos Turned Into!

Guess Who These
Adorable Kiddos
Turned Into!
Published
Before these three terrific kiddos turned into stars, they were just posing cutesy for the cameras … Here are your clues:
1. The cool-sweater kiddo on the left turned into a musician and a swimmer!
2. On the top right is a comedian who used to dance at bar and bat mitzvahs!
3. The baby on the bottom is an ICON. “That’s Hot” is just one of her many iconic phrases!
TMZ.com

Fiending for more fun? See if you can find the words in the “Hollywood” word search below …
Entertainment
3 Best New Movies on Hulu to Watch This Weekend (February 20-22): The Astronaut and More
With Valentine’s Day in the rearview mirror, what else is there to look forward to in February?
If you have a Hulu subscription, how about new films almost every week?
Watch With Us has found three new movies worth streaming this weekend.
The British drama Urchin, the sci-fi thriller The Astronaut and the ’90s comedy Sister Act starring Whoopi Goldberg and Maggie Smith are worth a watch now or later in the year.
‘Urchin’ (2025)
Mike (Frank Dillane) is a young homeless man struggling to get by in modern-day London. After a stint in jail, he finds steady work at a high-end restaurant. But his old, destructive habits threaten to upend all the progress he’s made, especially when an old friend, Simon (Harris Dickinson), comes back into his life. With no family or friends to rely on, can Mike make a new life for himself, or will his traumatic past prevent him from moving on?
Directed by Dickinson, Urchin is a searing slice-of-life drama that doesn’t pull any punches in its depiction of a man living in poverty. As much a victim of his own addictions as he is of a broken system, Mike struggles to be better than who he currently is, but the odds seem impossibly stacked against him. While I wouldn’t describe Urchin as fun to watch, it’s always interesting, especially when it depicts Mike’s rising and falling fortunes. The movie’s climax verges on the surreal, leaving it up to you to interpret what happens to Mike. Urchin is Dickinson’s debut as a director, and it’s good enough for you to want him to make another movie sooner rather than later.
‘The Astronaut’ (2025)
Sam Walker (Kate Mara) is an astronaut who just survived a traumatic incident aboard a space station. Now back on Earth, she’s quarantined at a small cottage where she is secretly spied on by the government. After several strange incidents occur, Sam believes a strange creature is on the premises. If she’s right, what is it and does it have anything to do with what happened to her in outer space? And if not, is she slowly going insane by being isolated from her friends and family?
The Astronaut is an under-the-radar sci-fi thriller that starts with an intriguing premise and just gets stranger from there. The movie skillfully introduced several red herrings to keep you guessing where it’s going without being too cheap or manipulative. The film’s last act goes full sci-fi, with Sam uncovering a shocking secret that causes her to re-examine her entire life. What that secret is is best left for you to discover, but trust me — you won’t be disappointed.
The Astronaut is streaming on Hulu.
‘Sister Act’ (1992)
Reno lounge singer Deloris (Whoopi Goldberg) has had it with her boyfriend, Vince (Harvey Keitel). He never treated her right, but this time, he’s crossed a line — he’s killed someone! He wants to kill her, too, so she won’t rat on him, which causes Deloris to run to the police for help. They’ll protect her, but she has to disguise herself as a nun at a run-down church in San Francisco. After living a life full of sin, Deloris doesn’t know if she can fit in with God’s chosen people, but she’ll have to, or else she’ll meet the Almighty a lot sooner than she wants to.
One of 1992’s biggest hits, Sister Act is a quintessential ‘90s comedy with a never-better Goldberg and a stellar cast full of veteran character actors living it up — and telling a dirty joke or two. The movie takes a classic “fish-out-of-water” concept and breathes new life into it, with frequently hilarious results. It’s a hoot to see Deloris try to fit in with the other nuns, who aren’t as strict and boring as she first believes them to be. The movie features several terrific musical sequences, with Deloris leading her fellow sisters in singing such classic ‘60s hits as “I Will Follow Him” with a spiritual bent. The movie spawned a less satisfying sequel, Sister Act 2: Back in the Habit, and a successful Broadway musical adaptation.
Entertainment
“Jennifer Hudson Show” renewed in wake of Kelly Clarkson and Sherri Shepherd's shows ending
:max_bytes(150000):strip_icc():format(jpeg)/Jennifer-Hudson-show-021926-6bf92756b5244842b45416af7f1f2a2b.jpg)
The Oscar winner says she “could not be more honored to continue this journey.”
Entertainment
Eric Dane Dead at 53

Eric Dane
Dead at 53 After ALS Battle
Published
Eric Dane has died at the age of 53, following a battle with ALS, TMZ has learned.
The family says in a statement to TMZ … “With heavy hearts, we share that Eric Dane passed on Thursday afternoon following a courageous battle with ALS. He spent his final days surrounded by dear friends, his devoted wife, and his two beautiful daughters, Billie and Georgia, who were the center of his world. Throughout his journey with ALS, Eric became a passionate advocate for awareness and research, determined to make a difference for others facing the same fight. He will be deeply missed and lovingly remembered always. Eric adored his fans and is forever grateful for the outpouring of love and support he’s received. The family has asked for privacy as they navigate this impossible time.”
The “Grey’s Anatomy” star announced he was diagnosed with amyotrophic lateral sclerosis, commonly referred to as ALS, back in April 2025.
He explained it had been an exhausting road just to get accurate answers. He bounced from one specialist to another, test after test … until a neurologist finally dropped the bomb: ALS.
Over the months, he chronicled his battle with the progressive neurodegenerative disease … revealing how he was down to just one functioning arm and was running out of body strength.
Commonly known as Lou Gehrig’s disease, ALS is a nervous system disease that affects nerve cells in the spinal cord and brain … it gets worse over time and causes loss of muscle control, according to the Mayo Clinic. There is no known cure for ALS.
Eric persevered with work … even filming the third season of the HBO series, “Euphoria.”
TMZ.com

11/9/22
Last time we saw Eric was on his 50th birthday in 2022, where we talked about birthday cake.
He was 53.
RIP.
Entertainment
Tina Win Turns Up The Heat At New York Fashion Week!

New York Fashion Week always delivers drama, but this season, Tina Win made sure all eyes were locked on her.
The 27-year-old Romanian American singer-songwriter stepped out in head-turning looks that felt less like outfit changes and more like a statement of intent. Glittering silhouettes, sharp tailoring, bold textures. It was high glamour with a pop star pulse. And if her style was loud, her message was even louder. A new era is coming.
Article continues below advertisement
A Pop Star On The Rise

Fresh off the buzz surrounding her debut single “Try Anything,” Tina is gearing up to release her second track, “How To Be Cool.” And from what we are hearing, it is not subtle.
The upcoming dance-pop anthem blends emotional intensity with club-ready production. Think pounding beats layered with lyrics that hit where it hurts. It is confident, polished, and built for repeat plays. If “Try Anything” introduced her, “How To Be Cool” looks ready to define her.
While plenty of artists flirt with the dance floor, Tina is diving in headfirst. The track leans into glossy pop while still holding onto the raw edges that set her apart.
Article continues below advertisement
Inspired By Icons, But Playing Her Own Game

Tina has cited powerhouses like Lady Gaga and Stevie Nicks as inspirations, and you can feel that influence in her aesthetic. There is drama. There is mystique. There is a refusal to shrink.
But she is not copying anyone’s blueprint. Her sound weaves alt-rock textures into mainstream pop hooks, creating something that feels both emotional and explosive. Vulnerability meets volume.
And she is not just building songs. She is building a structure.
Article continues below advertisement
After launching Tina Win Music LLC, the singer made it clear she wants control over her creative future. This is not a quick viral moment. It is a long game. She has plans to eventually use her platform to support other artists, especially women navigating complicated industry deals. That kind of foresight feels rare in a space that often prioritizes speed over strategy.
Article continues below advertisement
Fashion Week Was Just The Tease

Her presence at New York Fashion Week was more than a red carpet cameo. It was a preview.
Behind the scenes, Tina is collaborating with producer Joey Auch on a full-length debut album set for 2026. At the same time, she is quietly mapping out ventures in fashion, beauty, and fragrance. The vision is clear. Pop star today, mogul tomorrow.
The NYFW looks were not random. They felt intentional. Polished but daring. Glamorous but strong. Exactly how she describes her evolving sound.
Article continues below advertisement
From Personal Pain To Pop Power

The glitz might grab attention, but Tina’s story runs deeper.
Adopted from Romania and shaped by early experiences of loss and adversity, she channels that history into her music. She has described songwriting as both therapy and mission. Beneath the synths and high-energy beats, there is vulnerability. Beneath the confidence, there is reflection.
That emotional core is what separates her from the crowd. The spectacle may pull you in, but the honesty keeps you there.
With “How To Be Cool” on the horizon, Tina Win is not chasing whatever trend is hot this week. She is building her own universe where fashion, sound, and self-determination collide.
And if New York Fashion Week was any indication, she is just getting started.
Entertainment
This Liquid Electrolyte Delivers a Crash-Free Energy Boost

Us Weekly has affiliate partnerships. We receive compensation when you click on a link and make a purchase. Learn more!
Waking up in the morning and feeling like you didn’t get a wink of sleep is never a good feeling. Instead of drinking multiple cups of coffee or chugging energy drinks for a pick-me-up, we found a sugar-free alternative that offers an energy boost without the jitters. Thanks to the Buoy Energy Drops, you’ll feel rejuvenated without an afternoon crash.
Say goodbye to non-stop fatigue! This energy booster is enriched with B vitamins, caffeine from green tea and pre-dissolved electrolytes that promote mental clarity, enhanced physical performance and hydration. According to the brand, this science-backed find is clinically proven to hydrate 64% more than water alone.
Get the Energy Drops Ocean Electrolytes & Minerals for just $45 at Buoy!
It doesn’t take long for this energy booster to deliver game-changing results. It has a bioavailable formula that absorbs faster than powders or tablets, offering a pick-me-up in a hurry. Even better? It’s sugar-free, with no sweeteners or added flavors, so you can add it to your favorite daily beverage without altering the taste.
Real-life shoppers compare this energy booster to other alternatives. “These [have] given me a booster I haven’t had since I gave up energy drinks and coffee,” one fan shared. “I appreciate knowing I’m building up healthy electrolytes and minerals and getting the boost!”
Another reviewer noted how helpful this booster is during lengthy work shifts: “I work in a factory, so it’s hot, dirty, dingy & soul draining,” they began. “I don’t like energy drinks or pills, but this really gives me a push to get through the night.”
Tired of always feeling . . . tired? This sugar-free liquid electrolyte is formulated to hydrate and recharge, so you’ll get an energy boost without a post-caffeine crash.
Get the Energy Drops Ocean Electrolytes & Minerals for just $45 at Buoy!
-
 Video4 days ago
Video4 days agoBitcoin: We’re Entering The Most Dangerous Phase
-

 Tech5 days ago
Tech5 days agoLuxman Enters Its Second Century with the D-100 SACD Player and L-100 Integrated Amplifier
-
 Crypto World3 days ago
Crypto World3 days agoCan XRP Price Successfully Register a 33% Breakout Past $2?
-

 Sports3 days ago
Sports3 days agoGB's semi-final hopes hang by thread after loss to Switzerland
-

 Video7 days ago
Video7 days agoThe Final Warning: XRP Is Entering The Chaos Zone
-

 Video2 hours ago
Video2 hours agoXRP News: XRP Just Entered a New Phase (Almost Nobody Noticed)
-

 Tech3 days ago
Tech3 days agoThe Music Industry Enters Its Less-Is-More Era
-

 Business2 days ago
Business2 days agoInfosys Limited (INFY) Discusses Tech Transitions and the Unique Aspects of the AI Era Transcript
-

 Entertainment2 days ago
Entertainment2 days agoKunal Nayyar’s Secret Acts Of Kindness Sparks Online Discussion
-

 Video3 days ago
Video3 days agoFinancial Statement Analysis | Complete Chapter Revision in 10 Minutes | Class 12 Board exam 2026
-

 Tech2 days ago
Tech2 days agoRetro Rover: LT6502 Laptop Packs 8-Bit Power On The Go
-
 Crypto World6 days ago
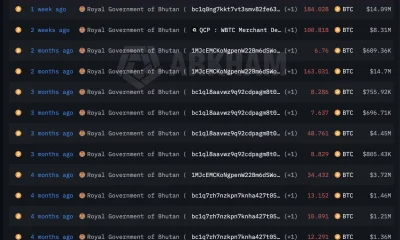
Crypto World6 days agoBhutan’s Bitcoin sales enter third straight week with $6.7M BTC offload
-

 Sports1 day ago
Sports1 day agoClearing the boundary, crossing into history: J&K end 67-year wait, enter maiden Ranji Trophy final | Cricket News
-

 Entertainment1 day ago
Entertainment1 day agoDolores Catania Blasts Rob Rausch For Turning On ‘Housewives’ On ‘Traitors’
-

 Crypto World7 days ago
Crypto World7 days agoKalshi enters $9B sports insurance market with new brokerage deal
-

 Business2 days ago
Business2 days agoTesla avoids California suspension after ending ‘autopilot’ marketing
-

 NewsBeat4 days ago
NewsBeat4 days agoThe strange Cambridgeshire cemetery that forbade church rectors from entering
-

 Crypto World1 day ago
Crypto World1 day agoWLFI Crypto Surges Toward $0.12 as Whale Buys $2.75M Before Trump-Linked Forum
-

 NewsBeat5 days ago
NewsBeat5 days agoMan dies after entering floodwater during police pursuit
-

 Crypto World7 hours ago
Crypto World7 hours ago83% of Altcoins Enter Bear Trend as Liquidity Crunch Tightens Grip on Crypto Market