Tech
Sentosa beach club Tipsy Unicorn shuts down amid legal dispute
Editor’s Note: The following article has been updated to reflect the latest statement from Sentosa Development Corporation (SDC).
Tipsy Bird is owned by local hospitality group Tipsy Collective, which has faced years of legal disputes
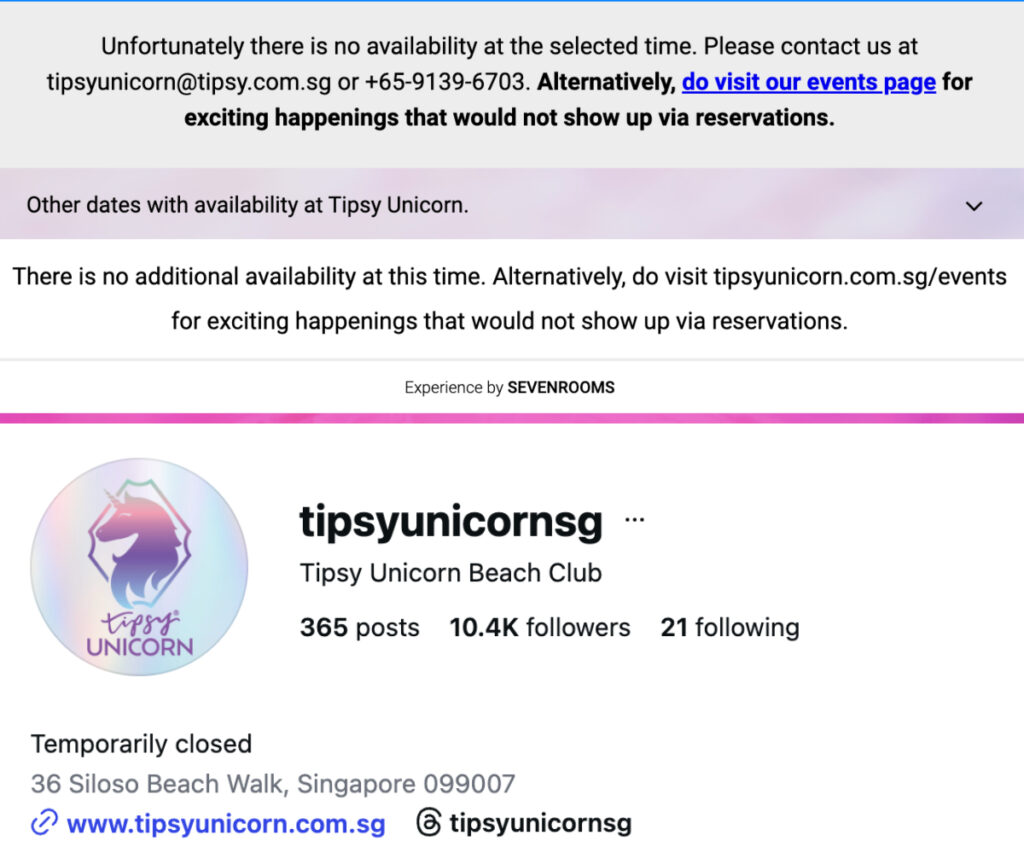
Sentosa beach club Tipsy Unicorn has ceased operations after its operator was ordered into compulsory liquidation by the Singapore High Court.
According to a report by The Straits Times, the venue’s operator, Tipsy Bird, was wound up on Jan 23 this year after United Overseas Bank (UOB) filed a winding-up application. Court documents seen by the publication showed that the bank is seeking to recover more than S$96,000 in debt and interest.
However, liquidators shared that this may not represent the company’s full liabilities. Without the firm’s Statement of Affairs, they are unable to determine the total amount owed or how many creditors are affected.
As of Feb 16, the company’s directors have yet to come forward to brief the liquidators on the firm’s financial affairs.
The liquidators also noted that Tipsy Bird operated Tipsy Unicorn Beach Club at 36 Siloso Beach Walk. Following the winding-up order, the landlord of the premises, Sentosa Development Corporation (SDC), exercised its right to repossess the property.
Responding to a Vulcan Post media enquiry, SDC confirmed that the beach club ceased operations on Jan 30, adding that they are currently in discussions with potential operators.
“Guests can continue to look forward to a vibrant beach scene on Sentosa, with new concepts and enhancements planned as part of our ongoing destination rejuvenation efforts,” said a SDC spokesperson.


When the publication visited the venue on Feb 18, the outlet was shuttered, with a notice at the entrance stating it had stopped operations from Jan 30. Its Instagram page was also marked as “temporarily closed,” and checks by Vulcan Post on Feb 20 showed that reservations were no longer available on its website.
Closure follows years of legal disputes
Corporate records show Tipsy Bird is wholly owned by local hospitality group Tipsy Collective, which remains an active entity as of Feb 19.
According to a Facebook post by the group, Tipsy Unicorn opened at Sentosa on Sept 1, 2023, and had been operating for about three years before its closure.


The closure and court order come after years of legal disputes since the passing of co-founder Derek Ong in Aug 2023.
While the other co-founder, David Gan, remained involved in the business, concerns over financial mismanagement and a lack of transparency led shareholders to clash with him, including objections to the development of the Sentosa beach club.
The budget for this project reportedly doubled from S$3 million to S$6 million. Additional concerns included debts amounting to S$5.2 million owed to suppliers, contractors and creditors. Tipsy Collective also allegedly owed about S$1 million to SDC.
Following the dispute, Gan was dismissed on Nov 6, 2024. But trouble did not stop brewing.
In Nov 2024, it was reported that more than 100 employees allegedly did not receive their Oct 2024 salaries. They were eventually paid in Jan 2025 after shareholders injected fresh funds.


Further checks by Vulcan Post showed that Tipsy Collective’s website is no longer available, though their social media pages remained active.
Vulcan Post has reached out to Tipsy Collective for comment, but did not receive a response at the time of publication.
- Read more stories we’ve written on Singaporean businesses here.
Featured Image Credit: Tipsy Unicorn
Tech
TerraClear launches autonomous farm robot to capture images for tackling rocks, weeds and more


TerraClear’s mission to help farmers map and tackle tough field problems such as rocks and weeds has evolved with the launch of a new machine: an autonomous robot called TerraScout.
The startup, based in Issaquah, Wash., and Grangeville, Idaho, says the device can collect ultra-high-resolution imagery across an entire field and convert the data into plans which can be executed by existing farm equipment, such as its rock picker or existing sprayers.
Founded in 2017 with the goal of simplifying the laborious task of removing large rocks from farmers’ fields, TerraClear has expanded into AI-powered identification and management of weeds using the same tech stack.
“TerraScout will scout entire fields in almost any condition and turn that intelligence into precise action for existing crews and equipment,” TerraClear CEO Devin Lammers said in a new release Thursday. “Today we focus that output on rock and weed management, but the future applications for this platform are vast. It is my firm belief that this technology will drive the next era of farm productivity gains.”
TerraClear says the robot can collect more than 4 billion image samples per acre and map over 1,000 acres per day at speeds of up to 15 mph. TerraScout can operate autonomously for up to six hours without refueling. Onboard technology turns massive image datasets into actionable maps in real-time.
TerraClear was founded by Brent Frei, the former CEO of Onyx Software and co-founder of Smartsheet. The initial focus was on its rock picker hardware, which can mount to a variety of machines and pick hundreds of rocks per hour, and its AI-powered mapping of fields where those rocks can cause expensive damage to machinery.
Lammers, a longtime leader in the agriculture technology industry, took over as CEO in August 2024.
The company, which employs about 50 people and has raised about $53 million to date, is not sharing revenue numbers, but is closing in on 1,000 customers.
Field trials for TerraScout began earlier this year and TerraClear said it will expand trials to existing retail partners and select farm customers this spring.
Tech
CISA orders feds to patch actively exploited Dell flaw within 3 days


The U.S. Cybersecurity and Infrastructure Security Agency (CISA) ordered government agencies to patch their systems within three days against a maximum-severity Dell vulnerability that has been under active exploitation since mid-2024.
According to security researchers from Mandiant and the Google Threat Intelligence Group (GTIG), this hardcoded-credential vulnerability (CVE-2026-22769) in Dell’s RecoverPoint (a solution used for VMware virtual machine backup and recovery) is being exploited by a suspected Chinese hacking group tracked as UNC6201.
After gaining access to a victim’s network in CVE-2026-22769 attacks, UNC6201 deploys several malware payloads, including a newly identified backdoor called Grimbolt. This malware is built using a relatively new compilation technique that makes it harder to analyze than its predecessor, the Brickstorm backdoor.
While the group swapped Brickstorm for Grimbolt in September 2025, it’s not yet clear whether this switch was part of a planned upgrade or “a reaction to incident response efforts led by Mandiant and other industry partners.”
“Analysis of incident response engagements revealed that UNC6201, a suspected PRC-nexus threat cluster, has exploited this flaw since at least mid-2024 to move laterally, maintain persistent access, and deploy malware including SLAYSTYLE, BRICKSTORM, and a novel backdoor tracked as GRIMBOLT,” they said.
The security researchers have also found overlaps between UNC6201 and the Silk Typhoon Chinese state-backed cyberespionage group (although the two are not considered identical by GTIG), also tracked as UNC5221 and known for exploiting Ivanti zero-days to target government agencies with custom Spawnant and Zipline malware.
Silk Typhoon has previously breached the systems of several U.S. government agencies, including the U.S. Treasury Department, the Office of Foreign Assets Control (OFAC), and the Committee on Foreign Investment in the United States (CFIUS).
Feds ordered to prioritize CVE-2026-22769 patches
CISA has now added the security flaw to its Known Exploited Vulnerabilities (KEV) catalog on Wednesday and ordered Federal Civilian Executive Branch (FCEB) agencies to secure their networks by the end of Saturday, February 21, as mandated by Binding Operational Directive (BOD) 22-01.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” CISA warned on Wednesday.
“Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable.”
Last week, CISA also gave U.S. federal agencies three days to secure their BeyondTrust Remote Support instances against an actively exploited remote code execution vulnerability (CVE-2026-1731).
Hacktron, which reported the vulnerability on January 31, warned in early February that around 11,000 BeyondTrust Remote Support instances were exposed online, and that around 8,500 were on-premises deployments that required manual patching.
Tech
New York’s New 3D Printing Law, As Written, Is Extremely Harmful And Annoying

from the first-do-no-harm dept
The good folks over at Adafruit are raising the alarm about a new New York State 3D printing law that could greatly imperil the public’s freedom to tinker and could generally make life way more annoying for the schools, libraries, hospitals, small businesses, hobbyists, and garages that utilize 3D printers.
New York’s 2026–2027 executive budget bill (S.9005 / A.10005) includes language requiring that all 3D printers operating in the state need to include software or firmware that scans every print file through a “firearms blueprint detection algorithm” and then locks the hardware up so it refuses to print anything it flags as a potential firearm or firearm component.
As Adafruit’s Phillip Torrone notes, the key problem here is it’s largely impossible to detect firearms from geometry alone:
“A firearms blueprint detection algorithm would need to identify every possible firearm component from raw STL/GCODE files, while not flagging pipes, tubes, blocks, brackets, gears, or any of the millions of legitimate shapes that happen to share geometric properties with gun parts. This is a classification problem with enormous false positive and false negative rates.”
NY’s new law would apply to open source firmware like Marlin, Klipper, and RepRap, which are generally maintained by volunteers without the resources for compliance. As well as office printers that never touch the internet, or CNC milling machines that can basically generate any shape you can imagine.
Torrone goes on to explain how the bill could be dramatically improved by exempting open source firmware, and focusing more concretely on the intent to create fire-arms, instead of waging an impossible enforcement war on ambiguous shapes. They’re also recommending limited liability for retailers, schools, and libraries, and the elimination of mandatory file scanning:
“But the answer to misuse isn’t surveillance built into the tool itself. We don’t require table saws to scan wood for weapon shapes. We don’t require lathes to phone home before turning metal. We prosecute people who make illegal things, not people who own tools.
The Open Source 3D printing community probably does not know about this. OSHWA and other open source advocacy orgs have ignored many of the things we really need their help with. That needs to change. This bill is in early stages — the working group hasn’t even convened yet. There’s time to work together, in the open, for amendments that make sense.”
Random aside: it’s worth reminding folks that this proposal comes on the heels of a recently passed New York State “right to repair” law (supposed to make it easier and cheaper to repair technology you own) that Governor Kathy Hochul basically lobotomized at lobbyist behest after it was passed, ensuring it doesn’t actually protect anybody’s freedom to tinker.
Filed Under: 3d printer, 3d printing, consumers, hobbyists, legislation, new york, new york state, tinker
Tech
The Search Engine for OnlyFans Models Who Look Like Your Crush
For three days in February, porn star Alix Lynx flew to Miami for her first exclusive creator gathering where she was in full grind mode: shooting Reels and talking strategy with other creators. “It was kind of like SoHo House for OnlyFans girls,” she says of the experience, which is called The Circle and drew more than a dozen sex workers, including Remy LaCroix and Forrest Smith.
Lynx, who is a former webcam model turned OnlyFans starlet, has a combined 2 million followers across Instagram, TikTok, and X. She joined OnlyFans in 2017 with “the luxury of having my own following,” she says, but those numbers haven’t always translated to subscriptions. It’s why she was in Miami.
“I don’t think people understand. I do a shitload of marketing,” Lynx says.“That’s the big misconception with OnlyFans—when creators join they think it’s going to be easy. But unless you’re a genius at marketing on social media, which is few and far between, it’s genuinely hard to get found and gain a following.”
Many of OnlyFans’ 4 million creators have said the same thing: native discovery on the platform sucks. “There’s just a frustration,” Lynx says. “In a perfect world, there would be that searchability feature because it makes it an even playing field for creators.” (According to OnlyFans, the platform limits its search feature as a safety precaution so users don’t accidentally stumble across content they didn’t intend to see.)
It’s a problem that Presearch—a free, private, decentralized search engine—wants to fix with the launch of its image-based discovery tool Doppelgänger.
Doppelgänger is the newest addition to Presearch’s Spicy Mode, a NSFW feature for searching adult content. Users can upload an image of a celebrity—or any person they think is hot—to find OnlyFans creators that resemble them. The technology matches the user with similar creators who want an audience rather than to deepfake platforms that are nonconsensual and illegal. Ever wondered who Sabrina Carpenter’s or Pedro Pascal’s porn doppelgängers were? Wonder no more.
According to the company, Doppelgänger is built with specific guardrails—no tracking what users search, explicit age-gating—and runs on Presearch’s decentralized index, “which surfaces content traditional search engines and commercial AI suppress,” says Brenden Tacon, head of product and business development at Presearch.
“We’re trying to offer a place where you might serendipitously become discovered,” Tacon tells WIRED. “You won’t on OnlyFans. If you’re hustling yourself on Instagram, Reddit, and all these places, it’s so hard to break through the noise.”
With 300,000 daily active searches on Presearch—according to the company—Doppelgänger is one of the first tools on the market pushing for ethical discovery of adult creators at scale. Unlike traditional reverse image tools that scan across the open web to locate where a photo appears or attempt to trace someone’s identity, Doppelgänger does not search the broader internet, does not surface personal information, and does not attempt to identify a person. “It simply returns visually similar public profiles based on image features, making it structurally more limited and, in many ways, more privacy-protective than a standard reverse image search,” Tacon says.
Still, the accuracy of Doppelgänger could use some improvement. In multiple tests run by WIRED, the AI seems better tailored to find matches for women than men. I had no problem finding look-alikes for Cardi B and Sydney Sweeney. But when searching for Michael B. Jordan look-alikes, it suggested female creators Chanell Heart (the number 3 match) and Chamile Symone, in addition to Uncut Jock NYC, a white-presenting Brazilian sex worker. In fact, five women were suggested among Jordan’s top 40. Curious if this was a glitch, I dragged a photo of actor Jeff Goldblum—a perennial “hottie,” according to the subreddit r/VintageLadyBoners—into the image finder, and the top search result was for Jean B, a self-described “twink content creator,” followed by 38 suggestions of large-breasted women. (A second search for Goldblum—who, for what it’s worth, is more zaddy than twink—with a different photo, did not fare any better; the lone male “look-alike” was for YCC, who is Chinese.)
Tech
Scout AI’s Fury Turns Spoken Orders into Battlefield Destruction


A low-key demonstration high in the hills of central California recently showcased some new military technology. Scout AI, a new defense startup, integrated its Fury software into a self-driving ground vehicle and two armed drones. The entire system collaborated to hunt down a truck and blow it up, all activated by a single simple instruction written in plain English.
Fury serves as the central coordinator. A commander types or speaks a goal, such as sending a vehicle to a spot and launching drones to strike a specific target, and Fury takes care of breaking it all down into individual steps, assigning tasks to the machines, monitoring what’s going on through video feeds and data, and stepping in to adjust things as needed. One drone detects the truck, Fury reroutes the others, and the strike is launched. A human is present to keep an eye on things, but the majority of the specifics are handled by machines on their own.
Sale
DJI Neo, Mini Drone with 4K UHD Camera for Adults, 135g Self Flying Drone that Follows You, Palm Takeoff…
- Due to platform compatibility issue, the DJI Fly app has been removed from Google Play. DJI Neo must be activated in the DJI Fly App, to ensure a…
- Lightweight and Regulation Friendly – At just 135g, this drone with camera for adults 4K may be even lighter than your phone and does not require FAA…
- Palm Takeoff & Landing, Go Controller-Free [1] – Neo takes off from your hand with just a push of a button. The safe and easy operation of this drone…
Fury’s approach is based on large AI models that have been taught to figure out what’s going on in a scene, devise a plan, and provide directions. The largest model, with over 100 billion parameters, functions similarly to the mission commander in that it accepts the command and begins working. It then assigns jobs to smaller models, each with approximately 10 billion parameters, which run directly on the various machines. The smaller models then handle movement, navigation, and the final explosive release. The system employs conventional cameras rather than expensive sensors, and it can connect to a variety of devices without interfering with their built-in functions. Fury just examines the technical specifications for each platform and determines the appropriate commands to deliver to their systems.

Everything in the test was real, done on actual equipment in tough terrain, with no pre-scripted situations, fake special effects, or constant human steering. The ground vehicle followed a dirt road, unleashed the drones, and set off to search. Once the truck arrived, one of the drones zeroed in and detonated its payload on impact, capping off the mission with a rapid damage assessment. The entire process went well, demonstrating how well the program can handle a variety of air and ground units from various manufacturers.

Scout AI created Fury to address a long-standing issue with unmanned systems. Older setups rely on tight, unchanging code that adheres to rigorous rules, so when things change or unanticipated challenges arise, they struggle. Fury allows the machines to think through difficulties, devise new solutions, and adjust to changing situations while remaining focused on the reward. It also simplifies communication, even when things get hectic, and scales up to larger groups working in different venues.

Colby Adcock, who co-founded the company with Collin Otis, describes the transition as follows. AI bots are already quite good at managing jobs in simulated environments, and Fury brings that same adaptable brainpower to real-world operations for American forces. The software serves as a buffer between command systems and machines, allowing units from all around to collaborate as a single team under human supervision.
[Source]
Tech
Ukrainian gets 5 years for helping North Koreans infiltrate US firms


A Ukrainian national was sentenced to five years in prison for providing North Korean IT workers with stolen identities that helped them infiltrate U.S. companies.
39-year-old Oleksandr Didenko of Kyiv, Ukraine, pleaded guilty in November 2025 to aggravated identity theft and wire fraud conspiracy after being arrested in Poland in May 2024.
This week, he was sentenced to 60 months in prison and 12 months of supervised release, and agreed to forfeit more than $1.4 million, including cash and cryptocurrency seized from Didenko and his accomplices.
“Oleksandr Didenko participated in a scheme that stole the identities of hundreds of people, to include United States citizens, which were used by North Korea to fraudulently secure lucrative IT jobs,” said James Barnacle, Assistant Director in Charge of the FBI’s New York Field Office. “This massive operation not only created an unauthorized backdoor into our country’s job market, but helped fund the regime of an adversary.”
According to court documents, Didenko stole U.S. citizens’ identities and sold them to overseas IT workers through an online platform known as UpWorkSell (which was seized by the Justice Department), who used them to fraudulently secure jobs with 40 U.S. companies in California and Pennsylvania.
Throughout this scheme, he provided the North Korean remote workers with at least 871 proxy identities and proxy accounts on three freelance IT hiring platforms. He also facilitated the operation of at least eight “laptop farms” in Virginia, Tennessee, California, Florida, Ecuador, Poland, and Ukraine that allowed the North Koreans to make it look like their devices were located in the United States.
One of these “laptop farms” was run by Christina Marie Chapman, a 50-year-old woman from Arizona, from her own home between October 2020 and October 2023. Chapman was charged in May 2024 and was sentenced to 102 months in prison after a July 2025 guilty plea.
The FBI has been warning about the danger presented by North Korean threat actors impersonating U.S.-based IT staff since at least 2023. As the law enforcement agency repeatedly noted, North Korea maintains a large and well-organized army of IT workers who use stolen identities to secure employment with hundreds of American companies.
In July 2024, U.S. authorities sanctioned, charged, or indicted 20 individuals and 8 companies across three separate enforcement waves. These actions were followed by a fourth wave of sanctions in August 2025 that targeted companies associated with North Korean IT worker schemes operated by Russian and Chinese nationals.
More recently, in December 2025, security researchers revealed that Famous Chollima (or WageMole) operatives, part of the notorious North Korean state-backed Lazarus hacking group, tricked recruiters using AI tools and stolen identities and got hired by Fortune 500 companies.
Tech
AMD Zen 6 desktop CPUs may deliver 24 cores, 7 GHz targets, and AM5 support


According to well-known leaker HXL, Zen 6 will span four single-CCD processor variants alongside three higher-end dual-CCD designs. While the exact Ryzen branding for each chip hasn’t been disclosed, the rumored Ryzen 10000 series lineup appears to back earlier whispers that AMD’s next flagship desktop CPU will push core counts…
Read Entire Article
Source link
Tech
How Niche Brands Stand Out

Niche brands stand out by building digital systems that reflect a clear point of view—and by iterating faster than generalized competitors. In 2026, the advantage comes from a purpose-built stack: composable architecture, tight data feedback loops, and trust controls that reduce friction without reducing safety.
1. Focused market design (your unfair advantage)
Niche brands win when they design for a single “job to be done,” not a broad demographic. The practical goal is to remove decision fatigue: fewer choices, clearer comparisons, and a site structure that mirrors how the niche actually shops (use cases, compatibility, constraints, and rituals).
Implementation checklist
- Build navigation around the customer’s vocabulary (problems, surfaces, ingredients, fit, size, legality), not internal product categories.
- Treat “collection pages” as decision pages: add a short buying guide, comparison hooks, and clear boundaries (“Not for X,” “Works best for Y”).
Summary: Focus beats scale because it lets you simplify choices and increase conversion without needing more traffic.
2. Technology as brand infrastructure (composable by default)
Composable commerce is no longer experimental; it’s broadly positioned as a proven strategy with a mature ecosystem of packaged components (CMS, search, PIM, OMS, CDP/engagement) that integrate into a modular architecture. Headless frontends are frequently described as “the norm,” enabling brands to optimize UX without being blocked by back-end constraints.
A practical stack map (lean, modern)
- Experience layer: headless storefront + CMS (for fast merchandising and content reuse).
- Commerce core: product/catalog, pricing, promotions, checkout.
- Discovery: search + recommendations (where niche vocabulary and intent matter most).
- Data: event collection → customer profile → segmentation (keep it minimal and consent-aware).
- Ops: OMS/3PL, returns, support tooling, email/SMS, review/UGC.
When not to go headless: if you’re pre–product-market fit, a heavy composable build can slow you down—use a simpler theme-based stack until you’ve validated merchandising, margins, and repeat demand.
Summary: Your stack is your brand’s execution engine; composable patterns let you upgrade parts without rewriting the whole business.
3. Personalization without enterprise complexity (minimum viable data)
Niche personalization works best when it’s narrow and explainable: “show the right products sooner” rather than “build a surveillance machine.” You get most of the upside with a small set of events: viewed category, viewed product attributes, add-to-cart, purchase, return reason, and support contact.
Brands like Stoned Genie leverage this approach by aligning product presentation and digital experience with a distinct cultural identity, creating resonance without relying on mass appeal. Instead of layering on complex automation, they prioritize clarity in positioning and relevance in merchandising—keeping personalization focused and defensible.
What to implement first
- Intent-based routing: “Shop by use case” quizzes or guided filters that write back a first-party preference (not 30 attributes).
- Merchandising rules that you can audit: hide out-of-stock substitutes, boost high-margin bundles, suppress high-return variants for new customers.
Pitfalls
- Personalization that changes prices or claims without transparency can destroy trust faster than it lifts conversion.
- Overfitting to short-term conversion can reduce LTV (e.g., discount addiction); treat LTV as the guardrail metric.
Summary: The best niche personalization is small, controlled, and measurable—built on signals you can defend.
4. Content as a conversion mechanism (and a search-quality moat)
For niche brands, content isn’t “blogging”—it’s the product’s proof, the buyer’s guide, and the support team, all embedded into the storefront. Google’s guidance emphasizes E‑E‑A‑T (including “experience,” such as first-hand use of a product) and original, helpful, people-first content.
High-converting content modules (put these on money pages)
- “Choose the right X” blocks on collection pages (3–5 criteria, plus who each option is for).
- Proof blocks on PDPs: test notes, materials, sourcing, safety notes, compatibility tables, and “what’s in the box.”
- Post-purchase success paths: setup guides, care instructions, refill/repurchase timing, troubleshooting.
Quality guardrails (2026 search reality)
- Avoid filler and generic intros: raters are explicitly instructed to downrate pages where the main content is copied/paraphrased/auto-generated with little added value.
- If you use AI for drafts, treat it as editing acceleration; the final page must show real expertise, real product knowledge, and unique contribution.
Summary: Content that demonstrates real experience becomes both a conversion tool and a defensible quality signal.
5. Operational efficiency through automation (without breaking the brand)
Automation should protect the brand promise: fewer errors, faster shipping, clearer support—not “more spam.” Prioritize workflows that reduce customer-facing failures: inventory sync, order routing, fraud checks, returns triage, and lifecycle messaging.
What to automate first
- Inventory and ETA truth: real-time stock, backorder rules, and proactive delay notifications.
- Support triage: route by issue type (delivery, usage, defects), auto-suggest relevant help content, escalate high-risk tickets.
Guardrails
- Don’t automate refunds/returns blindly; combine rules with human review for high-value or high-fraud patterns.
- Measure “contacts per 100 orders” and “return rate by SKU” to avoid scaling hidden problems.
Summary: Automation is a margin lever and a trust lever—if it reduces mistakes customers actually feel.
6. Trust and compliance as conversion design
In sensitive or regulated niches, trust is a feature you ship. Stripe’s secure payment system overview highlights core security components, including encryption, tokenization, multifactor authentication (MFA), fraud detection systems, and PCI DSS compliance, as part of a robust payment environment.
How to turn compliance into UX
- Make policies legible: shipping, returns, warranty, and data handling should be scannable and consistent.
- Reduce payment anxiety: recognizable payment methods, clean error states, and transparent verification steps.
Summary: Security and compliance aren’t just risk controls—they’re user-experience signals that reduce checkout hesitation.
7. Community-driven growth and iteration (your compounding advantage)
Community works when it’s embedded into the product narrative: reviews with context, UGC that demonstrates outcomes, and referral loops that reward advocacy. The compounding strategy is iteration: small reversible experiments across bundles, PDP structure, onboarding flows, and post-purchase education.
Iteration cadence (practical)
- Weekly: test one merchandising change + one content module improvement.
- Monthly: audit returns, support drivers, and cohort retention; ship fixes to the top two friction points.
- Quarterly: revisit your stack—swap components only when the bottleneck is proven.
Summary: Niche brands out-iterate because their systems are smaller, clearer, and closer to the customer.
Tech
Over $20 million stolen in surge of ATM malware attacks in 2025


The FBI warned that Americans lost more than $20 million last year amid a massive surge in ATM “jackpotting” attacks, in which criminals use malware to force cash machines to dispense money.
According to a Thursday FBI flash alert, more than 700 ATM jackpotting incidents were reported last year alone in a significant spike compared to the roughly 1,900 total incidents reported across the United States since 2020.
These attacks can be carried out in minutes and target the software layer controlling an ATM’s physical hardware, using malicious tools such as the Ploutus malware. Most often, they go undetected by financial institutions and ATM operators until the cash is already gone.
As the FBI explained, cash machines are designed to verify transactions through their bank before dispensing cash. However, Ploutus bypasses this process entirely, allowing the criminals to issue commands directly to the ATM and trigger withdrawals on demand without a bank card, a customer account, or the bank’s approval.
“Ploutus malware exploits the eXtensions for Financial Services (XFS), the layer of software that instructs an ATM what to physically do. When a legitimate transaction occurs, the ATM application sends instructions through XFS for bank authorization,” the FBI said. “If a threat actor can issue their own commands to XFS, they can bypass bank authorization entirely and instruct the ATM to dispense cash on demand.”
To install the malware, the attackers usually gain physical access to the targeted ATM using widely available generic keys. Once inside, they remove the machine’s hard drive, copy malware onto it and reinstall it, or even swap the original drive out entirely for another one preloaded with the malicious software.
To defend against these attacks, the FBI encouraged financial institutions to audit their ATM systems for signs of unauthorized removable storage use and unauthorized processes.
“When combined with gold image integrity validation, this approach enables early identification of physical intrusion and malware staging events that would otherwise evade network-based monitoring,” the law enforcement agency added.
FBI’s warning comes after a wave of arrests targeting members of the Tren de Aragua (TdA) gang, all linked to a massive ATM jackpotting scheme that used Ploutus malware to steal millions in cash from bank ATMs across the United States.
In total, the U.S. Department of Justice has charged 87 Tren de Aragua members over the past six months, who are now facing maximum prison terms ranging from 20 to 335 years each.
Tech
Holafly vs Airalo: Which eSIM Is Better in 2026?

If you’ve recently travelled abroad, you know the huge checklist of things that need to be done before getting to relax on a quiet beach. And if you’re anything like me, there’s almost something on the list that’s forgotten, which then comes back to haunt you at the wrong time. One such thing is connectivity, as no one in the history of travel has ever liked the long queues at airports to get a new SIM card. Over the past few years, though, there’s been a solution, and that’s eSIM. These non-physical SIMs are installed on your phone and help you connect to the network in any desired country. No need to spend outrageous prices at the airport anymore. Two major players in the eSIM space are Holafly and Airalo. While both provide connectivity across different countries, their approaches are super different. I tested them both on a recent trip to Vietnam, and here’s how both operators compare.
Holafly vs Airalo: Quick Comparison
| Feature | Holafly eSIM | Airalo eSIM |
| Data Plans | Mostly unlimited data plans (daily/weekly/monthly) — great for heavy users. | Fixed data plans (e.g., 1 GB, 5 GB, 20 GB) you buy as needed |
| Pricing | Generally more expensive due to unlimited data focus | Cheaper with smaller, tailored data packages |
| Coverage | ~200+ destinations globally | ~200+ destinations globally |
| Unlimited Data | Yes (main selling point) — though may throttle after heavy use. | Mostly no unlimited data (except limited specific plans) |
| Voice/SMS Support | Data-only (calls via apps like WhatsApp. | Offers some plans (Discover+) with voice/SMS in certain regions |
| Hotspot/Tethering | Yes | Yes, generally allowed with your data allowance |
| App & Activation | QR code or app install — easy setup | QR code or app install — easy setup |
| Best For | Long trips & heavy data usage (streaming, hotspot) | Short trips & light to moderate data usage |
Different Options, Different Pay
The biggest differentiator between Holafly and Airalo is the available package options. For context, Airalo offers plans without unlimited data, meaning you can configure how much you really need. Passing through France on a road trip to Spain? You can get a 1GB data plan (valid for three days) for $4 to continue using navigation, and you’re good to go. This significantly reduces the end user’s cost and provides more flexibility. However, there’s a problem. Airalo’s plans, while cheaper, start with 1GB or 3GB for the duration of the day you select. But given that the average American family uses 650-700 GB of data per month, 3GB isn’t actually a lot. You can get through that much data within just an hour of watching YouTube in Full HD. So, for any trip longer than a day, you’ll have to spend more on higher capacity plans, which can quickly add up.
On the other hand, Holafly’s approach is a whole lot different. Their plans are always unlimited, meaning you don’t have to worry about finishing up your quota and can watch movies, shows, and play games without worry. As you might expect, Holafly’s plans are more expensive, generally starting from $4 per day for unlimited data. While the exact pricing would depend on your specific country, I’m generally more on board with unlimited data, since even a short WhatsApp call can use several hundred megabytes. And you can also get 5% off using my coupon FOSSBYTES.
Global eSIM
Both Holafly and Airalo offer global eSIM plans for frequent travellers and business people who regularly travel to different countries. Like with the regular eSIM, the pricing and data strategy are very different on both. Airalo offers a 7-day 1GB global plan for $13, which goes all the way up to $34 for just 3GB for 30 days. Any additional data requirement will cost more. Holafly’s package, while expensive, at $62 for 7 days, offers unlimited data in 110+ countries. Honestly, if you plan to get a global SIM, that means you travel a lot, and in that case, Holafly’s unlimited plan is a really good deal.
Holafly also offers a global subscription plan with coverage in 160+ destinations, and you can cancel it at any time, so it’s a good option even if you are planning a trip for just 30 days. They have a Light Plan with 25GB of data for $49.90, an Unlimited Plan for $64.90 monthly, and you can also hotspot with no limits. And if you use my code FOSSBYTES, you get 10% off for 12 months on your subscription.
Length
Holafly
Airalo
7 days
Unlimited data for $62.00
1 GB for $13.00
15 days
Unlimited data for $134.00
2 GB for $24.00
30 days
Unlimited data for $224.00
3 GB for $34.00
Support & App Experience

Holafly and Airalo offer plenty of installation options for both Android and iOS users. You can either set up using the QR code, do it manually, or even through their respective apps. It’s the support infrastructure, though, where Holafly edges ahead. On Trustpilot, Holafly has a rating of 4.6, with multiple reviews highlighting the company’s 24/7 multilingual support, which has proven very helpful during times of worry. People have also mentioned Holafly’s excellent refund policy, which works for up to 6 months after purchase. Their app, however, isn’t the best. It was buggy when reporting total data usage, and I also ran into the infamous “this content isn’t available at your location” problem on Netflix a couple of times.
On the other hand, Airalo has a rating of 3.9. While it’s by no means bad, there have been some complaints about the network coverage and unhelpful support staff. That being said, the Airalo app is really stable. It was easy to use and free of bugs that could hinder the user experience, and included helpful tutorials that made the setup straightforward.
Both Holafly and Airalo have loyalty programs that grant users special discounts and cashback. Airalo’s loyalty program offers up to 10% cashback on every purchase, compared to Holafly’s 7%.
Personal Experience

As mentioned, I decided to put both services head-to-head during my recent trip to Vietnam. For some context, I set up both before my flight, and the experience was excellent on both. I bought the unlimited week plan with Holafly for $27, while the 10GB 7-day plan cost me $16. Both plans were instantly connected to service after I landed, and, being a tech reviewer, I started my usual testing, which included speed testing, downloading content, and calling my family back home.
Call quality with WhatsApp was really good with both, and my family didn’t have any problems hearing my voice. Similarly, navigation and translation between Vietnamese and English were handled very well on both. Network speeds were also comparable in both Saigon and the quiet beach town of Tuy Hoa, hovering around 50 Mbps download and 15 Mbps upload. However, the 10GB network limit didn’t last very long. After only a few days, I ran through all my data while on a train journey without Wi-Fi. This was a big worry. But fortunately, Holafly was there to the rescue with the unlimited data. Personally, I’d choose Holafly over Airalo because data can run out quickly, and you could end up stuck in an unfamiliar place.
Verdict
In the end, the choice would depend on your specific needs. If you’re like me and can’t stop worrying about finishing your data mid-trip, or if you frequently have to be on video calls, then Holafly is the best bet. The only downside is the app glitches, which can sometimes interfere with sessions. However, if you’re transiting through a country for a short time or taking a short trip, Airalo’s cost savings are the way to go. Don’t forget to use my code FOSSBYTES at Holafly if you want to get a discount on your eSIM.
-
 Video4 days ago
Video4 days agoBitcoin: We’re Entering The Most Dangerous Phase
-

 Tech5 days ago
Tech5 days agoLuxman Enters Its Second Century with the D-100 SACD Player and L-100 Integrated Amplifier
-
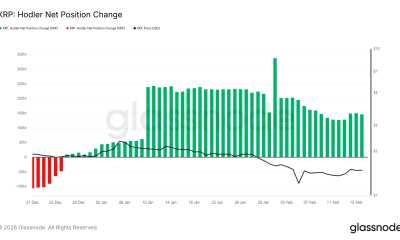
 Crypto World3 days ago
Crypto World3 days agoCan XRP Price Successfully Register a 33% Breakout Past $2?
-

 Sports3 days ago
Sports3 days agoGB's semi-final hopes hang by thread after loss to Switzerland
-

 Video9 hours ago
Video9 hours agoXRP News: XRP Just Entered a New Phase (Almost Nobody Noticed)
-

 Tech3 days ago
Tech3 days agoThe Music Industry Enters Its Less-Is-More Era
-

 Business2 days ago
Business2 days agoInfosys Limited (INFY) Discusses Tech Transitions and the Unique Aspects of the AI Era Transcript
-

 Video3 days ago
Video3 days agoFinancial Statement Analysis | Complete Chapter Revision in 10 Minutes | Class 12 Board exam 2026
-

 Entertainment2 days ago
Entertainment2 days agoKunal Nayyar’s Secret Acts Of Kindness Sparks Online Discussion
-

 Tech2 days ago
Tech2 days agoRetro Rover: LT6502 Laptop Packs 8-Bit Power On The Go
-
 Crypto World6 days ago
Crypto World6 days agoBhutan’s Bitcoin sales enter third straight week with $6.7M BTC offload
-

 Sports1 day ago
Sports1 day agoClearing the boundary, crossing into history: J&K end 67-year wait, enter maiden Ranji Trophy final | Cricket News
-

 Crypto World7 days ago
Crypto World7 days agoKalshi enters $9B sports insurance market with new brokerage deal
-

 Entertainment2 days ago
Entertainment2 days agoDolores Catania Blasts Rob Rausch For Turning On ‘Housewives’ On ‘Traitors’
-

 Business2 days ago
Business2 days agoTesla avoids California suspension after ending ‘autopilot’ marketing
-

 NewsBeat5 days ago
NewsBeat5 days agoThe strange Cambridgeshire cemetery that forbade church rectors from entering
-

 Crypto World2 days ago
Crypto World2 days agoWLFI Crypto Surges Toward $0.12 as Whale Buys $2.75M Before Trump-Linked Forum
-

 NewsBeat5 days ago
NewsBeat5 days agoMan dies after entering floodwater during police pursuit
-

 Crypto World14 hours ago
Crypto World14 hours ago83% of Altcoins Enter Bear Trend as Liquidity Crunch Tightens Grip on Crypto Market
-

 NewsBeat6 days ago
NewsBeat6 days agoUK construction company enters administration, records show










