Browsing Amazon Haul, the online shopping giant’s new $20-and-under bargain bin section, I immediately recognize not just a product, but a specific image. The photo is on a listing for “Timeless Black Dress for Both Casual and Formal Gatherings,” and it is stolen.
Technology
The delusion of Amazon Haul

The image actually belongs to a New York-based independent brand called Mirror Palais, which sold the “Daisy Dress” for $545 a few years ago. Elevated by social media algorithms and its celebrity fans, Mirror Palais’ images have traveled from the brand’s website, to tweets, to Pinterest mood boards, and finally, to the discount section of the world’s largest online retailer, where it is — obviously — not for sale. On Amazon, it’s listed for $7.49. When I add it to my cart, I realize it’s even cheaper: inexplicably and improbably, it is an additional 65 percent off.
This one image of a black mini dress does not just appear on random listings on Amazon Haul — you can find it on Walmart and AliExpress as well as smaller sites with names like Mermaid Way and VMzona — all selling dupes (short for duplicates) of the original Mirror Palais dress. I even find a separate listing on Amazon, in the typically but not unbelievably cheap section, where this same image is used to sell the LEZOOEY Womens New Lace Halter Slim Sexy Bodycon Spaghetti Strap Black Mini Dress for $19.99. The listing on normal Amazon has a bit more details about the item, including a video of close-up shots of the straps and hem. If I didn’t know about the original dress, I might assume the Haul version is a dupe of this dupe.
When Amazon announced its ultracheap Haul section in November, it made clear what shoppers already knew: Americans love junk, and the cheaper the better. Amazon Haul joins a constellation of other online retailers that offer the widest possible selection of products for the lowest possible price, exploiting shoppers’ apparently bottomless appetite to consume. But whether it’s Amazon Haul, Temu, Shein, AliExpress, or any number of other retailers, what they sell is the same — both literally and philosophically. The public’s shopping options are themselves dupes of something else.
Over the past few years, as e-commerce companies with roots in China like fast fashion brand Shein and online superstore Temu have gained popularity in the US, the tenor of how we shop shifted — instead of quick shipping, shoppers were happy to wait a couple of weeks while packages full of items made their way stateside from China. Amazon’s moniker, Haul, is indicative of this. A haul, in internet parlance, necessitates purchasing a bunch of stuff. (Recall Temu’s “Shop like a billionaire” motto.) Even if a package takes a week or two to arrive, the ability to purchase more is, for many shoppers, worth the wait.
The black imitation dress is not the only thing I purchased in my Haul haul: I threw in a salt and pepper grinder ($1.95); a protective case for AirPods ($6.99); a sweater ($19.99); a neon light that says “Love” ($6.99); a pleather handbag ($6.99); and a hat with fake distressing that, confusingly, reads “BICTH” ($7.99). With the 65 percent discount, the total came to $27.05.
Like the dress, I was able to locate many of these items for sale on other platforms. On Shein, the handbag is listed for $8.60 and uses the same product images as the listing on Amazon Haul. On AliExpress, more than a dozen listings from different storefronts use the same images, priced anywhere from 99 cents to $15. The listings and prices are arbitrary: in the past, when I’ve purchased the same item from multiple AliExpress shops, the physical product is identical. They’re just packaged and presented slightly differently, repeated until it’s unclear where the product even originated from or what the “real” price is. I’ve come to think of all of these ultracheap retailers as front doors leading to the same backend of suppliers and manufacturers, using the same set of lifted images — a Potemkin village of superstores operated across the globe, shrouded in secrecy.
In many ways, online shopping has always required the shopper to suspend their disbelief: that donated clothing actually gets redistributed, that “free” shipping is real, or that a startup is using a magic AI tool to complete your purchases. The advent of ultrafast fashion brands like Shein has pushed these delusions even further, dangling deals in front of customers and betting (often correctly) that a low, low price will be enough for them to take a chance on a product that, five years ago, would have perhaps seemed like an obvious scam. The mantra of “if it seems too good to be true, it probably is” almost feels quaint now — impossibly “good” deals are not a warning sign for consumers, but the expectation.
“Items in Amazon Haul are from vetted Amazon sellers and are backed by Amazon’s A-to-z guarantee so customers can shop with confidence that the products they’re purchasing are safe, authentic, and in the condition expected,” company spokesperson Maxine Tagay told The Verge in an email. Tagay added that Amazon has a “zero-tolerance policy” for counterfeit products and that the company is investing in measures to “protect customers from fraud and other forms of abuse.” Action taken may include removing counterfeit listings and blocking accounts. After The Verge reached out to Amazon for comment, the image of the black dress disappeared from the Haul listing, though it remains elsewhere on the site.
The thing about gimmicks that seem too good to be true is that, eventually, the fantasy fades. Sometimes reality sets in when that product an influencer promoted finally arrives and it sucks, and it eventually makes its way to a landfill. Other times, it’s because the company producing the item admits child labor is involved in its creation. And then, there is what appears to be coming down the pike: the systems that allow for cheap binge shopping come undone.
Packages valued under $800 — like my Amazon Haul order or your Shein impulse purchases — are able to enter the US import tax-free under the de minimis rule, and the White House says more than a billion parcels a year claim the exemption. In September, the Biden administration proposed overhauls of the de minimis loophole that would cut down on the number of small packages that could claim the duty-free exemption. President-elect Donald Trump has threatened to impose tariffs of 60 percent or more to products coming in from China, which would likely cause the price of goods to go up for consumers. The ultracheap product offerings of Temu, Shein, AliExpress, and Amazon Haul might start to look like not such a great deal.
My Haul package arrives about a week and a half after placing the order, traveling from China’s Guangdong Province all the way to New York. Seeing these half a dozen random products shoved in a small paper mailer, everything feels much more pathetic than the pictures online suggested. The sweater is shrink-wrapped in a lump, giving it the look of a package of frozen fish. The dress is thin and flimsy and appears to be incomplete: the ends of the straps dangle in the back instead of being secured on the inside of the bodice. Is it a design choice? Possibly. But each side is a different length. The handbag has a mysterious closure on the handle, which makes it feel like someone asked AI to design a trendy bag and the robot got confused. The hat does indeed read BICTH, which amuses me but really makes you wonder what normal person would buy this. My boss accidentally shatters the plastic battery case for the neon light with his bare hands trying to open it. If you are a shopper enticed by the promise that buying a mountain of $3 products will make you feel rich, you may be disappointed. The items themselves are not made to last — and perhaps the industry itself isn’t, either.
Technology
OpenAI’s Next Step Toward the ‘Agentic’ Future

With laptop and smartphone makers like Samsung spreading generative AI across all aspects of their devices, OpenAI is trying the same with an agentic tool announced on Jan. 23. The tool, called Operator, runs on the same basic technology as ChatGPT but resides within a proprietary web browser. This enables it to autonomously perform actions such as ordering groceries or booking tours.
OpenAI suggested in a blog post Operator could “ope[n] up new engagement opportunities for businesses,” but did not elaborate.
What is OpenAI’s Operator?
Operator is an application that includes a web browser and the generative AI model GPT-4o. It’s the result of an OpenAI project to train GPT-4o’s vision capabilities on the graphical user interfaces found on typical web pages. Its ability to make multi-step plans and correct mistakes independelty if needed set it apart from other efforts to create agentic AI, OpenAI boasted. Operator’s Computer-Using Agent (CUA) model is trained specifically on the buttons, forms, and menus likely to be found on a web page.
Operator is in beta. OpenAI said feedback from early-stage users will be used to improve it.
ChatGPT Pro subscribers can sign up for Operator starting today.
OpenAI plans to provide Operator to Plus, Team, and Enterprise soon. The tech giant also intends to integrate its capabilities into ChatGPT generally. They’ll include the CUA in their API “soon,” according to the blog post.
How does Operator work?
The company says the CUA’s reasoning technique, which they call an “inner monologue,” helps the model understand intermediate steps and adapt to unexpected input. Under the hood, CUA takes screenshots of web pages and uses a virtual mouse and keyboard to navigate.
As with ChatGPT, users can add custom instructions that Operator will remember, such as the user’s preferred airline.
SEE: Threat actors can jailbreak generative AI to automatically create phishing emails and other malicious content.
Users can prompt Operator in natural language the same way they can prompt ChatGPT. Operator is trained to balk at logging in to sites, providing payment details, or passing CAPTCHAs, so it will hand control back to the user for those steps. Operator is programmed not to accept requests — such as making banking transactions — or to weigh in on high-stakes situations, such as deciding whether to hire an employee.
If the Operator encounters an interface it can’t predict how to interact with, it will hand the task back to the user. OpenAI collaborated directly with the following companies to make sure Operator can interact with their sites:
- DoorDash.
- Instacart.
- OpenTable.
- Priceline.
- StubHub.
- Thumbtack.
- Uber.
OpenAI notes that the early iteration of Operator tends to struggle with “complex interfaces,” including creating slideshows or adding items to calendars.
Operator enters into a crowded generative AI landscape
Some of Operator’s functionality overlaps with competitor tools, such as Google Gemini or Apple Intelligence.
Operator invites comparison with Microsoft’s much-maligned Recall feature, which uses screenshots to navigate a PC. Operator also shares some capabilities with Google Lens on Chrome. However, its ability to navigate websites autonomously could be a point of differentiation. Agentic AI, in which generative AI models perform multi-step errands on the user’s account, is either the hot new thing in tech or a new way to package the still-limited products.
Technology
OpenAI’s first AI Agent is here, and Operator can make a dinner reservation and complete other tasks on the web for you

- OpenAI has officially launched it’s first AI Agent: Operator
- It’s works within a web browser to complete tasks for you, and is out now as a limited research preview
- Operator can make a dinner reservation, fill out a form, and complete other web tasks
OpenAI is always looking for the next big thing to add to ChatGPT, and after months of rumors, including a report from earlier this week that teased a launch, the technology giant’s first AI Agent is here. Operator is designed to complete web tasks for you, all with a touch of a button.
Essentially, Operator is a Computer Using Agent (CUA) that uses GPT-4o’s visual skills to browse and search the web. This means that it can understand the context of what to search for, and thanks to its multi-modality, it understands what it sees as it searches. It’s available now as a research preview for ChatGPT Pro subscribers in the United States.
Operator is described as “an agent that can use its own browser to perform tasks for you.” OpenAI released a demo showing Operator browsing the web as we (that is, we humans) do. You might ask Operator to book a dinner reservation for you, fill out an arduously long form, order groceries from a service, or even book a flight. It can use OpenTable to find and book a reservation at a restaurant, as shown in the demo. Operator will even walk you through its steps.

Operator is a ‘research preview,’ so know that it’s in its early days. OpenAI does impose some limitations. We haven’t had the chance to go hands-on yet, but it certainly looks impressive. This is OpenAI’s first entry into the world of AI agents, which will likely be the theme of the year in the realm of artificial intelligence.
OpenAI writes in a blog post announcing Operator that it “is one of our first agents, which are AIs capable of doing work for you independently—you give it a task and it will execute it.” This hints that not only are there other agents in the pipeline – Altman confirmed this during the live demo – but that they’re all based around the notion of doing things for you – a big step in the quest to make AI even more helpful, giving us some time back.
Operator is powered by the new Computer Using Agent (CUA) model, which pairs GPT4o’s vision skills with advanced reasoning. This all comes together to let Operator understand and use elements within a browser – the search bar, various buttons, and on-screen content.
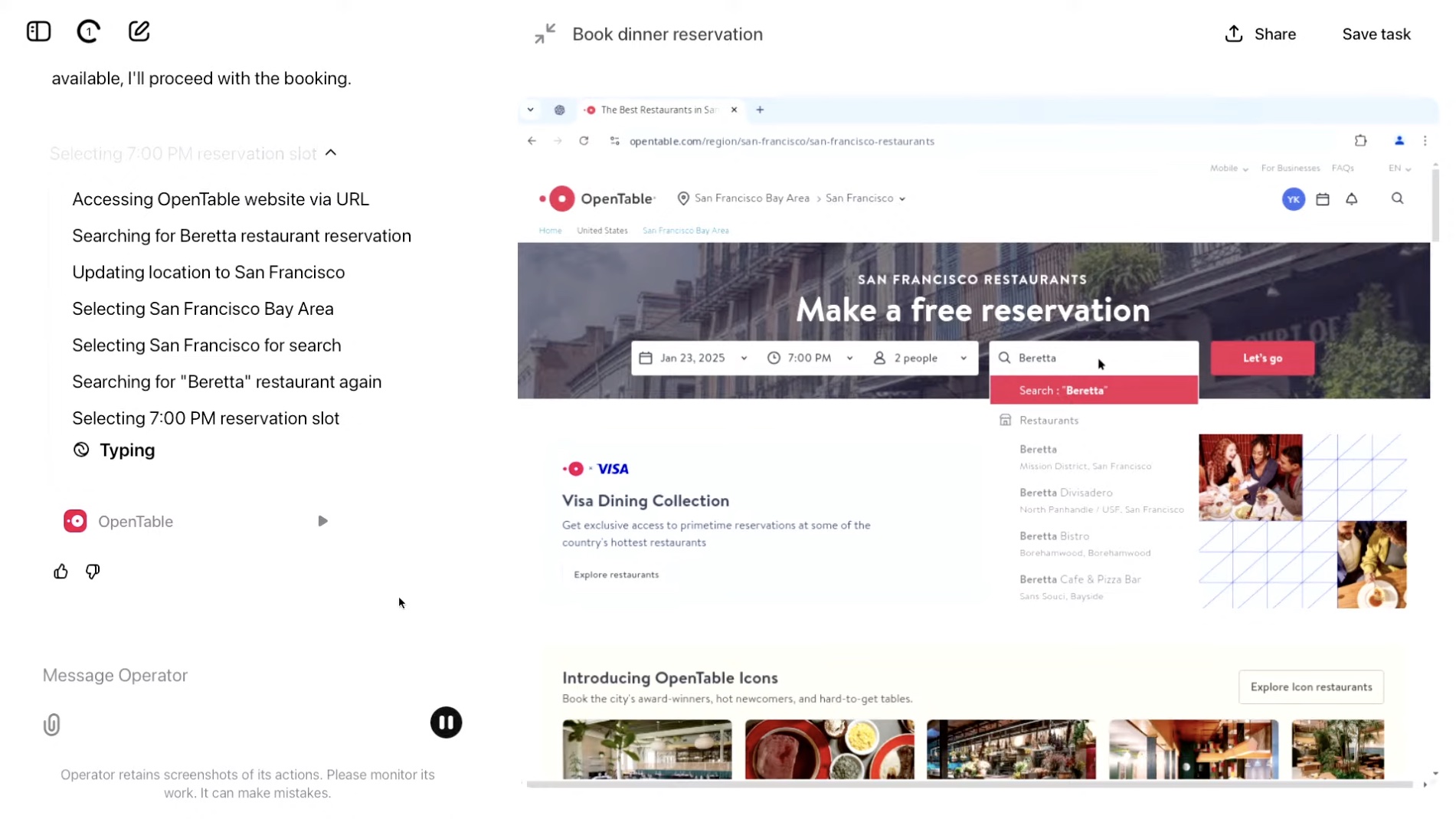
OpenAI explains that “Operator can ‘see’ (through screenshots) and ‘interact’ (using all the actions a mouse and keyboard allow) with a browser,” allowing it to functionally use a browser to complete a task. That’s pretty neat, especially if it works at a high rate of success, and according to the blog post, it can self-correct.
However, as with most new AI tools and skills, it will likely take some time for this to become truly useful in the real world. That will also require OpenAI to open it up to more folks, though as an early research preview it’s still certainly an impressive demo.
For now, if you’re in the United States and subscribed to ChatGPT Pro, you can try it out on OpenAI’s website. OpenAI CEO Sam Altman teased that it would eventually arrive in other countries and be added to the ChatGPT Plus subscription. As we remember from some of the announcements from 12 Days of OpenAI, Europe will likely take a bit longer.
You might also like
Technology
The Trump Cryptonaissance Is Here

The wheels are already beginning to turn on Donald Trump’s plan to make the US into the “crypto capital of the planet” following his return to the White House.
In an executive order signed Thursday, Trump established a “working group on digital asset markets,” which will be responsible for weighing the possibility of the US forming a “strategic national digital asset stockpile,” among other things.
The promise to establish a stockpile was one of numerous commitments made by Trump to the crypto industry before he was reelected. Though the idea stumped economists, it received a rapturous reception among bitcoiners. As rumors of an impending announcement spread Thursday, the price of bitcoin climbed to $105,000 per coin, just short of the record high.
The order also requires the working group—which will comprise the leaders of various government branches, financial regulatory bodies, and the attorney general—to come up with an appropriate set of regulations and laws governing the use of crypto.
Earlier in the week, on Trump’s second day in office, the Securities and Exchange Commission (SEC) —the US regulatory body that brought a volley of lawsuits against crypto firms under the Joe Biden administration—established a “crypto task force.” Under new leadership following the departure of former chair Gary Gensler, who was widely demonized in the cryptosphere, the SEC will develop a “comprehensive and clear regulatory framework for crypto assets,” the agency stated.
Later the same day, Trump granted clemency to Ross Ulbricht, who was serving life in prison for crimes committed while running the infamous darknet marketplace Silk Road, one of the first websites to accept bitcoin as payment. After being arrested in 2013, Ulbricht became something of a martyr in crypto circles for his part in spreading the bitcoin gospel.
These initial gestures signal Trump’s willingness to follow through on earlier campaign promises: to pass various crypto-related legislation, reform the financial regulatory apparatus in the US, and knit crypto into the US national treasury. The effects will be extensive, crypto figures believe, reverberating far beyond US shores and creating the conditions for a new golden era for the industry.
“Our technology is very powerful and transformative. We need to land it in different societies,” says Joseph Lubin, cofounder of Ethereum and chief executive at software company Consensys. “And America is a standard-setter for the rest of the world.”
Despite having previously spurned bitcoin as a “scam,” Trump now has extensive ties to the crypto industry, many high-profile members of which came out in support of his reelection campaign.
In the lead-up to the 2024 election, crypto organizations donated hundreds of millions of dollars to crypto-focused super political action committees, which spent the funds in support of crypto-friendly congressional candidates, many of them Republican.
On the campaign trail, Trump began to bill himself as the first “crypto president.” In July, in front of a rabid crowd of bitcoiners, Trump promised to turn the US into a crypto mining powerhouse and establish a national bitcoin stockpile if reelected. In the same speech, he pledged to fire Gensler, the SEC chair, prompting the most rapturous applause of the night.
Technology
Everything we saw at Xbox’s Developer Direct 2025

Though Nintendo can technically claim it had the first big gaming news event of the year, at least Xbox’s Developer Direct actually showed off some games and let us know when we can play them. The showcase was anchored by deep dives into the biggest games coming down the green pipe like Doom: The Dark Ages and Compulsion Games’ South of Midnight, with a couple of surprises to fill out the nearly one-hour-long runtime. Here are the highlights from the show.
Xbox kicked off the Direct with the surprise reveal of Ninja Gaiden 4. The game is being codeveloped by Koei Tecmo’s Team Ninja and Bayonetta studio PlatinumGames. Ninja Gaiden 4 revives the series’ bloody, fast-paced combat and high-stakes (but often frustrating) platforming with a new face, the ninja Yakumo. Yakumo will use his unique fighting styles to defeat the Divine Dragon Order that’s turned Tokyo into a dystopian, crumbling mess. Gaiden’s former protagonist, Ryu Hayabusa, will also make an appearance as a playable character and Yakumo’s rival.
Ninja Gaiden 4 will launch in the fall of this year, but if you don’t want to wait for your bloody ninja action, you don’t have to. Xbox stealth dropped Ninja Gaiden 2 Black, a remake of Ninja Gaiden II, and it’s available right now on Xbox and Game Pass.
The developers at Compulsion Games went into detail about South of Midnight’s gameplay and story. You play as Hazel who must use her powers as a Weaver, fighting monsters and traversing the haunted landscape, to rescue her mother who gets swept away in a hurricane. With this, everything I’ve seen about South of Midnight makes it seem like it’ll be one of my games of the year. It’s got a Black protagonist, features characters and tropes that harken to Southern gothic folklore, and its stop-motion art style makes it immediately stand out. I cannot wait to get my hands on this game when it releases on April 8th.
Sandfall Interactive was founded in Montpellier, France, in 2020 with a team led by former Ubisoft developers. Clair Obscur: Expedition 33 is the studio’s first game — a turn-based RPG with a compelling narrative hook. The world has been ravaged by a being known as the Paintress. Every year, she writes down a number, and everyone older than that number disappears. Expeditions are sent out to stop the Paintress, and the game will follow Expedition 33 in their attempt to save humanity. In addition to an interesting Persona 5-style take on turn-based combat, Expedition 33 features some serious voice acting talent, starring Charlie Cox, Jennifer English, Ben Starr, and Andy Serkis. Can’t wait to hear them perform when Clair Obscur: Expedition 33 launches on April 24th.
To close out the Direct, Xbox gave us another look at Doom: The Dark Ages, the prequel to id Software’s 2016 Doom reboot and Doom Eternal. It will, of course, feature all the ripping and tearing a Doom enjoyer could want, along with an interesting focus on narrative — something the series isn’t really known for. But I suspect folks are far more interested in piloting a 30-story Doomguy-shaped mech suit when the game releases on May 15th.
Technology
JetBrains launches Junie, a new AI coding agent for its IDEs

JetBrains, the company behind coding tools like the IntelliJ IDE for Java and Kotlin (and, indeed, the Kotlin language itself), on Thursday launched Junie, a new AI coding agent. This agent, the company says, will be able to handle routine development tasks for when you want to create new applications — and understand the context of existing projects you may want to extend with new features.
Using the well-regarded SWEBench Verified benchmark of 500 common developer tasks, Junie is able to solve 53.6% of them on a single run. Not too long ago, that would have been the top score, but it’s worth noting that at this point, the top-performing models score more than 60%, with Weights & Biases “Programmer O1 crosscheck5” currently leading the pack with a score of 64.6%. JetBrains itself calls Junie’s score “promising.”
But even with a lower score, JetBrains’ service may have an advantage because of its tight integration with the rest of the JetBrains IDE. The company notes that even as Junie helps developers get their work done, the human is always in control, even when delegating tasks to the agent.
“AI-generated code can be just as flawed as developer-written code,” the company writes in the announcement. “Ultimately, Junie will not just speed up development — it is poised to raise the bar for code quality, too. By combining the power of JetBrains IDEs with LLMs, Junie can generate code, run inspections, write tests, and verify they have passed. “
It may be a bit before you can try that out yourself, though. The service is only available through an early access program behind a waitlist. For now, it also only works on Linux and Mac, and in the IntelliJ IDEA Ultimate and PyCharm Professional IDEs, with WebStorm coming soon.
Technology
This devious phishing site repurposes legitimate web elements like CAPTCHA pages for malware distribution


- Phishing campaign mimics CAPTCHA to deliver hidden malware commands
- PowerShell command hidden in verification leads to Lumma Stealer attack
- Educating users on phishing tactics is key to preventing such attacks
CloudSek has uncovered a sophisticated method for distributing the Lumma Stealer malware which poses a serious threat to Windows users.
This technique relies on deceptive human verification pages that trick users into unwittingly executing harmful commands.
While the campaign primarily focuses on spreading the Lumma Stealer malware, its methodology could potentially be adapted to deliver a wide variety of other malicious software.
How the phishing campaign works
The campaign employs trusted platforms such as Amazon S3 and various Content Delivery Networks (CDNs) to host phishing sites, utilizing modular malware delivery where the initial executable downloads additional components or modules, thereby complicating detection and analysis efforts.
The infection chain in this phishing campaign begins with threat actors luring victims to phishing websites that mimic legitimate Google CAPTCHA verification pages. These pages are presented as a necessary identity verification step, tricking users into believing they are completing a standard security check.
The attack takes a more deceptive turn once the user clicks the “Verify” button. Behind the scenes, a hidden JavaScript function activates, copying a base64-encoded PowerShell command onto the user’s clipboard without their knowledge. The phishing page then instructs the user to perform an unusual series of steps, such as opening the Run dialog box (Win+R) and pasting the copied command. These instructions, once followed, cause the PowerShell command to be executed in a hidden window, which is invisible to the user, making detection by the victim almost impossible.
The hidden PowerShell command is the crux of the attack. It connects to a remote server to download additional content such as a text file (a.txt) containing instructions for retrieving and executing the Lumma Stealer malware. Once this malware is installed on the system, it establishes connections with attacker-controlled domains. This allows attackers to compromise the system, steal sensitive data, and potentially launch further malicious activities.
To guard against this phishing campaign, both users and organizations must prioritize security awareness and implement proactive defences. A critical first step is user education.
The deceptive nature of these attacks – disguised as legitimate verification processes – shows the importance of informing users about the dangers of following suspicious prompts, especially when asked to copy and paste unknown commands. Users need to be trained to recognize phishing tactics and question unexpected CAPTCHA verifications or unfamiliar instructions that involve running system commands.
In addition to education, deploying robust endpoint protection is essential for defending against PowerShell-based attacks. Since attackers in this campaign rely heavily on PowerShell to execute malicious code, organizations should ensure that their security solutions are capable of detecting and blocking these activities. Advanced endpoint protection tools with behavioural analysis and real-time monitoring can detect unusual command executions, helping to prevent the malware from being downloaded and installed.
Organizations should also take a proactive approach by monitoring network traffic for suspicious activity. Security teams need to pay close attention to connections with newly registered or uncommon domains, which are often used by attackers to distribute malware or steal sensitive data.
Finally, keeping systems updated with the latest patches is a crucial defense mechanism. Regular updates ensure that known vulnerabilities are addressed, limiting the opportunity for attackers to exploit outdated software in their efforts to distribute malware like Lumma Stealer.
“This new tactic is particularly dangerous because it plays on users’ trust in widely recognized CAPTCHA verifications, which they encounter regularly online. By disguising malicious activity behind what seems like a routine security check, attackers can easily trick users into executing harmful commands on their systems. What’s more concerning is that this technique, currently distributing the Lumma Stealer, could be adapted to spread other types of malware, making it a highly versatile and evolving threat,” said Anshuman Das, Security Researcher at CloudSEK.
You may also like
Technology
The Creators of ‘Palworld’ Are Back—This Time With a Horror Game

Pocketpair, the company behind last year’s viral game Palworld, has a new venture: publishing indie games. Its first project, scheduled for release later this year, will be an as-yet-unnamed horror game from Surgent Studios, the developer behind 2024’s Tales of Kenzera: Zau.
Palworld, jokingly referred to as “Pokémon with guns,” was a breakout success last year, drawing in more than 25 million players in its first few months. The company’s step into publishing comes at a turbulent time for video games, especially smaller studios; last year, Among Us developer Innersloth announced its own move into publishing to help push projects forward. Pocketpair’s Palworld success, it seems, is allowing them to do the same.
“As the games industry continues to grow, more and more games find themselves struggling to get funded or greenlit,” John Buckley, head of Pocketpair Publishing, said in a press release announcing the new division. “We think this is a real shame, because there are so many incredible creators and ideas out there that just need a little help to become incredible games.”
It’s no surprise, then, that Pocketpair would work with Surgent Studios, which has struggled to find funding following the release of Zau. The developer put its team on hiatus last year as it sought a partner for its next Kenzera game, currently known as Project Uso.
Surgent’s deal with Pocketpair is separate from Uso, founder Abubakar Salim tells WIRED. Unlike the Afrofuturism of Zau, it’ll be a horror title meant to introduce players to something new. “We’re taking a little detour from the Tales of Kenzera universe,” Salim says.
Salim adds that the horror genre “is a fascinating space that taps into primal emotions, immersing audiences in a reality that’s removed from their own yet strikes something deep and dark within us all.” Pocketpair and Surgent gave few details about the game in Thursday’s announcement, other than to describe it as “short and weird.”
“The world is so raw right now, and it feels natural to craft an experience that reflects and feeds off that intensity,” Salim says.
Pocketpair Publishing has not announced any other future projects. The company has been embroiled in legal drama since last year, when Nintendo filed a lawsuit in Tokyo claiming Palworld infringed on its copyright. Nintendo did not respond to a request for comment. When asked if the lawsuit was of any concern to Surgent, Salim says the studio isn’t worried. “We’re really excited to be working with their new publishing wing to bring this game to life,” he says.
Technology
Substack is spending $20 million to court TikTokers

Meta and YouTube aren’t the only platforms looking to benefit from TikTok potentially disappearing — Substack wants in on the action, too.
The company announced Thursday it’s launching a $20 million “creator accelerator fund,” promising content creators they won’t lose revenue by jumping ship to Substack. Creators in the program also get “strategic and business support” from Substack, and early access to new features.
“We established this fund because we’ve seen creators who specialize in video, audio, and text expand their audience, revenue, and influence on Substack, where the platform’s network effects amplify the quality and impact of the work they’re doing,” the company said in a blog post.
This pivot on Substack’s part has been in the works for a while — for months, the company has been marketing itself not as a newsletter delivery service but as a creator platform similar to Patreon.
“On Substack, [creators] can build their own home on the internet: one where creators, not platform executives or advertisers, own their work and their audience,” the blog post reads. The post also cites “bans, backlash, and policies that change with the political winds” as a reason creators can’t depend on traditional social media services.
That’s all fine (we at The Verge have been saying this for a while). But creators focusing on Substack are also subject to ebbs and flows depending on what the company is prioritizing: first, it was newsletters, then it was tweet-like micro blogs, followed by full-on websites and livestreaming. For some, Substack’s initial stated mission of giving more freedom to independent writers is fading. And TikTok creators looking to move to Substack will need to rebuild their following all over again — you obviously can’t export your TikTok followers.
The $20 million fund isn’t the first time Substack has offered a pool of money meant to entice creators. Under a program called Substack Pro, the company poached top media talent from traditional newsrooms with higher pay, health insurance, and other perks. That program ended in 2022, with Substack cofounder Hamish McKenzie saying the deals weren’t employment arrangements but “seed funding deals to remove the financial risk for a writer in starting their own business.” In other words, welcome to Substack. Now that you’re here, you’re on your own — which is more or less the deal other platforms offer.
Technology
Anthropic’s new Citations feature aims to reduce AI errors

In an announcement perhaps timed to divert attention away from OpenAI’s Operator, Anthropic Thursday unveiled a new feature for its developer API called Citations, which lets devs “ground” answers from its Claude family of AI in source documents such as emails.
Anthropic says Citations allows its AI models to provide detailed references to “the exact sentences and passages” from docs they use to generate responses. As of Thursday afternoon, Citations is available in both Anthropic’s API and Google’s Vertex AI platform.
As Anthropic explains in a blog post with Citations, devs can add source files to have models automatically cite claims that they inferred from those files. Citations is particularly useful in document summarization, Q&A, and customer support applications, Anthropic says, where the feature can nudge models to insert source citations.
Citations isn’t available for all of Anthropic’s models — only Claude 3.5 Sonnet and Claude 3.5 Haiku. Also, the feature isn’t free. Anthropic notes that Citations may incur charges depending on the length and number of the source documents.
Based on Anthropic’s standard API pricing, which Citations uses, a roughly-100-page source doc would cost around $0.30 with Claude 3.5 Sonnet, or $0.08 with Claude 3.5 Haiku. That may well be worth it for devs looking to cut down on hallucinations and other AI-induced errors.
Technology
New wave of sextortion scams uses personal details and images to intimidate targets while bypassing traditional security measures


- Sextortion scams evolve with personalized tactics and heightened intimidation.
- Threat actors exploit invoicing platforms to bypass email security filters.
- Robust email filters and training help counter sextortion threats effectively.
Sextortion scams are becoming more complex and personal as the scams now frequently target individuals across different sectors with greater precision creating a sense of immediate threat.
Cofense Phish Defense Center (PDC) recently observed a notable evolution in sextortion scams, which unlike earlier versions, which relied primarily on generic scare tactics, now use more sophisticated strategies, often bypassing traditional security measures.
The campaigns now personalize emails, including personal details such as the target’s home address or phone number directly in the email body, in order to capture the recipient’s attention and adds a layer of credibility to the scam.
Exploitation of fear through technical jargon
These emails generally originate from random Gmail accounts, which are harder to trace, rather than the typical impersonated addresses seen in earlier scams.
In addition to personal information, scammers have escalated their approach by including images of the target’s supposed home, workplace, neighbourhood or street in attached PDF files.
The email addresses the recipient by name and provides a specific location, followed by threats of a physical visit if the target fails to comply. This blend of personal details and digital intimidation is a shift from the simpler sextortion scams that used to rely solely on the fear of compromised online privacy.
The scam emails claim that the target’s device has been infected with spyware, often citing “Pegasus” as the malware responsible for the supposed breach. Threat actors use technical jargon to manipulate recipients with the hope that they have a limited understanding of cybersecurity. The emails claim that the attacker has been monitoring the victim for an extended period, gathering sensitive information, and even recording videos of them.
In some cases, the scammer adopts a casual tone lacing the message with slang or compliments to make it seem as if they have been closely observing the target’s life. The message typically concludes with two choices: ignore the email and face public humiliation or pay a ransom in cryptocurrency to ensure the alleged compromising material is never released.
A recurring part of these scams is the demand for payment in Bitcoin or other cryptocurrencies. Scammers often provide a Bitcoin wallet address, sometimes alongside a QR code to facilitate the payment process.
Another notable shift in sextortion campaigns is the use of invoicing services to deliver phishing emails. These services allow threat actors to send emails that bypass certain security protocols by disguising the sender’s information. Since these invoicing platforms handle the email’s delivery, their legitimate headers and content often allow the message to avoid detection.
To combat these evolving scams, individuals and organizations must stay informed and vigilant. Educating users about the nature of sextortion scams and the tactics employed by attackers can reduce the likelihood of falling victim.
You might also like
-
 Fashion8 years ago
Fashion8 years agoThese ’90s fashion trends are making a comeback in 2025
-

 Entertainment8 years ago
Entertainment8 years agoThe Season 9 ‘ Game of Thrones’ is here.
-

 Fashion8 years ago
Fashion8 years ago9 spring/summer 2025 fashion trends to know for next season
-

 Entertainment8 years ago
Entertainment8 years agoThe old and New Edition cast comes together to perform You’re Not My Kind of Girl.
-

 Sports8 years ago
Sports8 years agoEthical Hacker: “I’ll Show You Why Google Has Just Shut Down Their Quantum Chip”
-
Business8 years ago
Uber and Lyft are finally available in all of New York State
-
Entertainment8 years ago
Disney’s live-action Aladdin finally finds its stars
-
Sports8 years ago
Steph Curry finally got the contract he deserves from the Warriors
-
Entertainment8 years ago
Mod turns ‘Counter-Strike’ into a ‘Tekken’ clone with fighting chickens
-
Fashion8 years ago
Your comprehensive guide to this fall’s biggest trends




You must be logged in to post a comment Login