Crypto World
How the Scam Works and How to Protect Your Wallet

Address poisoning is reshaping risk in crypto wallets by shifting focus from private keys to how users interact with interfaces. Rather than breaking encryption, attackers exploit human habits and design flaws to misdirect funds. In 2025, a victim lost about $50 million in Tether’s USDt after copying a poisoned address. In February 2026, a phishing campaign tied to Phantom Chat drained roughly 3.5 Wrapped Bitcoin (wBTC) worth more than $264,000. These episodes underscore how small UI cues—copy buttons, visible transaction histories, and dust transfers—can seduce users into repeating trusted patterns and handing over assets they believe they are sending to legitimate contacts.
Key takeaways
- Address poisoning operates on user behavior and UI cues, not on private key theft or code flaws.
- Two high-profile losses illustrate the scale: a $50 million hit in 2025 and a February 2026 incident involving about 3.5 Wrapped Bitcoin ($WBTC) worth over $264,000.
- Copy buttons, visible transaction histories, and unfiltered dust transfers can make poisoned addresses look legitimate within wallet UIs.
- Because blockchains are permissionless, attackers can send tokens to any address, and many wallets display all incoming activity, including spam, which can seed trust in fake entries.
- Mitigations hinge on better UX and guardrails: explicit address verification, dust-filtering, proactive warnings, and recipient-address checks during sending flows.
Tickers mentioned: $USDT, $WBTC
Sentiment: Neutral
Market context: The cases underscore ongoing UX-driven security challenges in a market where on-chain activity is highly transparent and attackers increasingly target everyday user workflows. As stablecoins and tokenized assets gain prominence, wallet design and on-chain visibility will be central to risk management, alongside traditional education and phishing countermeasures.
Why it matters
The essence of address poisoning lies in the reproducible, human-centered mistakes that occur when users manage crypto transfers. Private keys remain secure in these scenarios; the vulnerability emerges when recipients or senders rely on partial address fragments or familiar transaction patterns. The attack chain typically unfolds with attackers locating valuable wallets, crafting near-identical recipient addresses, and initiating a tiny or zero-value transfer to insert their spoofed address into the victim’s recent-history view. The attacker then waits for the user to copy the address from that history and accidentally paste it into a new transfer, thereby sending funds to the wrong destination. The absence of a cryptographic breach highlights a fundamental truth: the security model of public blockchains hinges on user judgment as much as cryptography.
UX design decisions amplify the risk. Many wallets provide one-click copy buttons adjacent to recent transactions, a convenience that can backfire when spam or dusting entries appear in the same list. Investigators have long noted that victims often “trust” their own transaction history, presuming it signals legitimacy. In cases like the 2025 loss of USDt and the 2026 wBTC incident, the cost of this cognitive shortcut becomes starkly clear. The broader lesson is that user interfaces—the way addresses are displayed, verified, and confirmed—play a pivotal role in security outcomes, sometimes more so than key management alone.
Industry voices have urged wallets to adopt stronger safeguards. Tech leaders, including Changpeng “CZ” Zhao, have publicly called for enhanced protections to curb address poisoning, signaling a potential shift in wallet governance toward more rigorous recipient verification and anti-poisoning features. The tension is real: developers must balance smooth UX with robust safety checks, ensuring users can transact efficiently without becoming victims of lookalike addresses or suspicious dust transfers. In the meantime, the onus remains on users to verify destinations beyond quick-glance cues and to adopt disciplined sending practices.
At the core, the risk is not about breaking cryptography but about breaking user habits in high-friction moments—entering long addresses, approving approvals, and acting on incomplete information. The public and permissionless nature of blockchains makes every address accessible, and the legibility of transactions often lags behind the complexity of strings that represent keys and addresses. The result is a security rhythm in which attackers rely on social and UX dynamics, not on bypassing cryptographic barriers.
What address poisoning really involves
Address poisoning scams hinge on manipulating a victim’s transaction history to misdirect funds, rather than compromising keys or exploiting software vulnerabilities. The typical playbook unfolds as follows:
- Attackers first identify high-value wallets using publicly visible on-chain data.
- They generate a lookalike address that closely resembles a recipient the victim uses regularly, matching several leading and trailing characters to maximize recognizability at a glance.
- They initiate a small or zero-value transfer from the fake address to seed legitimacy and appear in the recipient’s recent activity.
- The attacker then relies on the victim copying the address from the recent transfers list when preparing a legitimate payment to someone else.
- The final step is when the victim pastes the attacker’s address and authorizes the transfer, unwittingly sending funds to the malicious destination.
The victim’s wallet and private keys remain untouched—the crypto-cryptographic layer is intact. The scam thrives on human error, habitual behavior, and trust built from familiar patterns. In some instances, the exploit is reinforced by dusting operations, where tiny transfers flood a user’s activity feed, nudging them toward interacting with suspicious entries without suspicion.
Did you know? Address poisoning scams have gained visibility in parallel with the expansion of Ethereum layer-2 networks, where reduced fees enable mass small transfers that populate users’ histories with fodder for identity-based deception.
How attackers craft deceptive addresses
Crypto addresses are long hexadecimal strings, often 42 characters on Ethereum-compatible chains. Wallets typically truncate the display to a short fragment, such as “0x85c…4b7,” which attackers exploit by constructing lookalikes with identical prefixes and suffixes while altering the middle portion. A legitimate example might read 0x742d35Cc6634C0532925a3b844Bc454e4438f44e, while an almost identical poisoned variant could appear as 0x742d35Cc6634C0532925a3b844Bc454e4438f4Ae. The strategy hinges on human visual heuristics: people rarely verify the entire string and often rely on the start and end characters to judge authenticity.
Some attackers even use vanity-address generation tools to produce thousands of near-identical strings. The social engineering angle is reinforced by dusting, where small funds accompany the malicious address to create a sense of legitimacy in a user’s transaction history. In practice, this is less about AI or cryptography and more about UX trust and careful scrutiny during each sending action.
Security researchers emphasize a key distinction: the breach lies in behavior and interface design, not in the encryption or signing process. Private keys are still the powerhouse that authorizes transactions, but they cannot verify whether the destination address is correct. The result is a paradox: the strongest security on the planet (cryptography) is undermined not by a technical flaw but by a failure to verify addresses thoroughly at the moment of sending.
Practical ways to stay safer
Because address poisoning exploits human tendencies rather than technical vulnerabilities, small but deliberate changes in how you interact with crypto wallets can markedly reduce risk. Here are practical steps for users and developers alike.
For users
- Build and maintain a verified address book or whitelist for frequent recipients, then reference it instead of retyping or copying from history.
- Always verify the full address before sending. If possible, use a character-by-character comparison or an address-checking tool.
- Avoid copying addresses from recent transaction history. If you need to, double-check the source in the list, or re-enter addresses from trusted bookmarks.
- Be wary of unsolicited small transfers that appear in your history; treat them as potential poisoning attempts and isolate them from normal activity.
For wallet developers
Design choices can dramatically reduce risk by making it harder for poisoned addresses to slip through in everyday flows. Suggested safeguards include:
- Filtering or dimming or automatically isolating very low-value (dust) transactions from typical recipient lists.
- Implementing recipient-address similarity checks that flag near-identical addresses during sending.
- Providing pre-signing simulations and risk warnings when the destination looks suspicious or matches a poisoned-pattern entry.
- Integrating on-chain checks or shared blacklists to identify and block known poisoned addresses before a user confirms a transfer.
Sources & verification
- Phantom Chat address poisoning and related bitcoin phishing details: https://cointelegraph.com/news/phantom-chat-address-poisoning-bitcoin-phishing
- General phishing attack overview in crypto: https://cointelegraph.com/learn/articles/what-is-a-phishing-attack-in-crypto-and-how-to-prevent-it
- Tether price index reference: https://cointelegraph.com/tether-price-index
- Critical observations from ZachXBT on poisoning cases: https://x.com/zachxbt/status/2021022756460966139
- Industry commentary on wallet safeguards and address poisoning: https://www.binance.com/en/square/post/34142027296314
Crypto World
Important Coinbase Announcement Concerning XRP, ADA, and Other Altcoin Investors
“Borrowing up to $100K in USDC against your tokens, instantly, without selling,” the announcement reads.
The US-based exchange Coinbase expanded its crypto-backed loan offerings to include additional tokens, such as Ripple’s XRP and Cardano’s ADA.
For the moment, the new service is available across the USA, except for residents of New York State.
Further Support for These Assets
The company rolled out its lending product, called Coinbase Borrow, in 2021. Two years later, it discontinued the service, only to bring it back at the start of 2025.
Coinbase Borrow lets users take a loan using their cryptocurrency possessions as collateral instead of selling them. Until recently, clients were able to borrow up to $5 million in USDC against their Bitcoin (BTC) holdings and as much as $1 million in the stablecoin against Ethereum (ETH). The exchange, though, decided to expand the service by adding Ripple (XRP), Cardano (ADA), Dogecoin (DOGE), and Litecoin (LTC).
“Now you can unlock the value of your portfolio without giving up your position. Borrowing up to $100K in USDC against your tokens, instantly, without selling. Available now in the US (ex. NY),” the official announcement reads.
Backing from a major exchange like Coinbase can positively influence the prices of the involved cryptocurrencies by boosting their reputation and accessibility. In this case, however, XRP, ADA, DOGE, and LTC continued trading lower, reflecting the broader market’s bearish conditions.
It is important to note that the strongest price pumps typically occur right after Coinbase lists a token or reveals its intentions to do so. Last summer, for instance, the company added SPX6900 (SPX), AWE Network (AWE), Dolomite (DOLO), Flock (FLOCK), and Solayer (LAYER) to its roadmap. Some of the involved assets headed north by double digits following the disclosure.
It’s a completely different story when Coinbase terminates services with certain coins. Towards the end of last year, Muse Dao (MUSE), League of Kingdoms Arena (LOKA), and Wrapped Centrifuge (WCFG) tumbled substantially after they were removed from the trading venue.
You may also like:
What Else is New on Coinbase?
The exchange has been quite active lately, enabling additional trading options for its clients. Earlier this month, it announced that users can buy, sell, convert, send, receive, or store RaveDAO (RAVE), Walrus (WAL), AZTEC (AZTEC), and Espresso (ESP). All assets are live on Coinbase’s official website and application.
WAL, AZTEC, and ESP experienced an initial price upswing after the news but then headed south. RAVE, on the other hand, has kept pumping and currently trades around $0.44 (per CoinGecko), representing a 25% weekly increase.
SECRET PARTNERSHIP BONUS for CryptoPotato readers: Use this link to register and unlock $1,500 in exclusive BingX Exchange rewards (limited time offer).
Crypto World
LayerZero CEO Clarifies ZRO Will Capture All Zero Network Fees

TLDR:
- ZRO becomes the only gas, staking, and fee asset across Zero, LayerZero, and Stargate infrastructure layers.
- Protocol revenue from priority fees, MEV tips, markets, and payments will all route directly into ZRO.
- Institutional buyouts removed 19.77 percent of total ZRO supply from future unlock circulation schedules.
- Public dashboards currently overstate ZRO unlock pressure by nearly twofold due to outdated supply data.
LayerZero has clarified how its ZRO token will function inside the upcoming Zero network after days of market speculation.
The update outlines a single-asset economic design that ties protocol activity directly to ZRO. It also revises assumptions about future supply pressure from token unlocks. The disclosure arrives ahead of Zero’s planned mainnet launch later this year.
ZRO Tokenomics Anchors Zero Network Fee Structure
Bryan Pellegrino published the clarification in a post on X, addressing questions around Zero’s economic design. He stated that the project will not issue a new token for the network. ZRO will serve as the only asset across all Zero functions.
ZRO will act as both the staking and gas token inside Zero. Every transaction and message will rely on the same asset for settlement. This approach removes the need for parallel fee tokens across zones.
According to the statement, all excess fees generated from priority fees linked to state contention will route to ZRO. Tips and MEV-related revenue will also accrue to the token. The design connects congestion and execution demand directly to token value flows.
Trading fees from the markets zone and payment fees from the payments zone will follow the same model.
Once LayerZero activates its fee switch, every protocol message will include a ZRO-denominated charge. This makes ZRO the financial endpoint for Zero, LayerZero, and Stargate activity.
Institutional Buybacks Cut ZRO Unlock Pressure in Half
Pellegrino also disclosed updated figures on institutional participation and internal buybacks.
He said institutional purchases and early investor buyouts now represent 19.77 percent of the total ZRO supply. Most of this came from absorbing future unlock allocations.
The update challenges assumptions shown on public token dashboards. Pellegrino noted that many trackers still treat those tokens as pending unlocks. That misclassification, he said, nearly doubles the projected supply pressure.
Community members amplified the data point after the post circulated. X user Zuuu highlighted the reduction in effective unlock risk as a key takeaway. The comment gained traction as traders reassessed ZRO’s circulating supply outlook.
LayerZero confirmed that the buyouts focused mainly on early investors and upcoming vesting schedules. The move shifts a portion of expected emissions into long-term holdings. It also reshapes how market participants model future dilution.
Zero aims to launch with permissionless infrastructure for payments, markets, and messaging. By assigning all economic flows to ZRO, the protocol links network usage with a single asset. The team said mainnet remains scheduled for this fall.
Crypto World
Ripple CEO Confirms White House Meeting between Crypto, Banking Reps
Update (Feb. 19 at 7:21 pm UTC): This article has been updated to include a statement from the Crypto Council for Innovation.
The White House has held another meeting between representatives from the cryptocurrency and banking industries on a market structure bill under consideration in the US Senate, seeking to iron-out differences on stablecoin yield provisions, among other issues.
In a Thursday Fox News interview, Ripple CEO Brad Garlinghouse said that the company’s chief legal officer, Stuart Alderoty, attended the meeting with White House officials earlier in the day. The CEO’s comments came after unconfirmed reports that the Trump administration would follow its Feb. 10 meeting on the CLARITY Act, a bill to establish digital asset market structure. That meeting did not result in a deal on stablecoins.
Passed by the US House of Representatives in July, the CLARITY Act has seen several delays while moving through the Senate and its relevant committees. These included two government shutdowns — the longest one in the country’s history spanned 43 days in 2025 — concerns from Democratic lawmakers on conflicts of interest, and groups pushing for provisions on decentralized finance, tokenized equities and stablecoin yield.
The meeting occurred a day after policymakers, including CFTC Chair Michael Selig and two US senators, and representatives from the crypto industry met at US President Donald Trump’s private Mar-a-Lago club to attend a forum hosted by World Liberty Financial, the company founded by the president’s sons and others. Ohio Senator Bernie Moreno said at the event that he expected the CLARITY Act to make it through Congress and be ready to be signed into law “by April.”
Related: US CLARITY Act to pass ‘hopefully by April’: Senator Bernie Moreno
Cointelegraph reached out to Ripple for comment on Alderoty’s presence at the meeting, but had not received a response at the time of publication. White House crypto advisers Patrick Witt and David Sacks had not publicly commented on the event at the time of publication.
In a statement shared with Cointelegraph, Crypto Council for Innovation CEO Ji Hun Kim said the Thursday discussion “built upon previous meetings to establish a framework that serves American consumers while reinforcing US competitiveness,” describing it as “constructive.”
Market structure bill awaits markup by Senate Banking panel
Although the Senate Agriculture Committee voted to advance its version of a digital asset market structure bill in January, another committee crucial to the legislation’s passage has stalled following stated opposition from Coinbase CEO Brian Armstrong.
Armstrong has objected to provisions that would restrict rewards paid on stablecoin holdings and warned the bill could weaken the CFTC’s role in favor of broader SEC authority.
The Senate Banking Committee had been scheduled to mark up its market structure bill in January, but delayed the event indefinitely after Armstrong said the exchange could not support the legislation as written, citing concerns about tokenized equities. As of Thursday, the committee had not rescheduled the markup.
Magazine: Is China hoarding gold so yuan becomes global reserve instead of USD?
Crypto World
Ripple CEO Confirms White House Meeting With Crypto and Banking Reps

Washington’s ongoing push to align crypto policy with traditional finance took another step as White House officials hosted a second meeting with industry representatives and banking executives to refine a proposed market-structure bill in the U.S. Senate. The talks, aimed at narrowing gaps on stablecoin yields and other guardrails, arrive amid broader efforts to reconcile consumer protections with U.S. competitiveness in crypto innovation. In a Thursday Fox News appearance, Ripple (the company) CEO Brad Garlinghouse said his company’s chief legal officer, Stuart Alderoty, joined White House officials at the discussions earlier in the day. The remarks followed unconfirmed reports that the administration would push ahead with the CLARITY Act, a framework designed to establish a market structure for digital assets, though no deal was announced at the time of reporting. The evolving dialogue underscores the delicate balance lawmakers seek between enabling financial innovation and safeguarding taxpayers and markets.
Key takeaways
- White House discussions with crypto and banking representatives continue as lawmakers weigh stablecoin yield provisions and market-structure safeguards.
- Ripple’s leadership participated in the talks, signaling high-level interest from the sector in shaping policy deliberations.
- The CLARITY Act remains a focal point in Congress, having passed the House earlier in the year but facing delays in the Senate and ongoing committee scrutiny.
- Coinbase (EXCHANGE: COIN) CEO Brian Armstrong has publicly challenged certain provisions, arguing they could curb the regulatory role of the CFTC in favor of the SEC and raise concerns about tokenized equities.
- Crypto policy advocates described the White House meeting as constructive and aimed at a framework that preserves American competitiveness while protecting consumers.
Tickers mentioned: $COIN
Sentiment: Neutral
Market context: The discussions sit within a broader regulatory backdrop as lawmakers and agencies navigate the overlap between traditional securities rules and crypto tokens, with market participants watching for signals on how a potential framework may affect liquidity and risk appetite.
Why it matters
The conversations in Washington reflect a policy environment where the United States is attempting to define a national standard for digital assets without stifling innovation. While lawmakers have advanced parts of their market-structure agenda in some committees, others have pressed pause or demanded clarifications. A central tension is how to treat stablecoins and yield mechanisms—areas that could influence capital flows and the attractiveness of the U.S. as a hub for crypto and blockchain experimentation. The involvement of high-profile industry voices, including Ripple’s Alderoty and Coinbase’s Armstrong, signals that the stakeholder community is intent on shaping the legislative design rather than merely reacting to it.
The CLARITY Act has been a cornerstone in this debate. Passed by the House but hampered by delays in the Senate and internal concerns about conflicts of interest and the scope of regulation, the bill’s path forward hinges on finding consensus around DeFi rules, tokenized equities, and stablecoin governance. The ongoing discourse also highlights the role of regulators—specifically the CFTC and the SEC—in delineating authority over different asset classes. As policy debates intensify, market participants are weighing how any forthcoming framework could alter trading venues, custody standards, and the treatment of tokenized assets within investor portfolios.
From a market perspective, the immediate impact of policy discussions tends to be less about dramatic price shifts and more about positioning and expectations. Traders monitor committee schedules, public statements by key figures, and any formal markup dates that could signal a near-term stance or a shift in trajectory. The meetings also underscore a broader operational reality: policy clarity is often valued more than policy speed, as clearer rules can reduce regulatory risk and encourage longer-horizon project development in the crypto economy.
What to watch next
- Rescheduling and outcome of the Senate Banking Committee markup on digital asset market structure legislation.
- Public commentary from White House crypto advisers and other senior policymakers on the CLARITY Act and related regulations.
- Further statements from the private sector, including the participation of major exchanges and industry groups, on provisions affecting stablecoins and tokenized equities.
- Any new revelations from meetings hosted at high-profile venues (e.g., discussions linked to industry events or forums) about governance and enforcement expectations.
- New official documents or filings that detail how the proposed rules might interact with existing CFTC and SEC authorities.
Sources & verification
- Congress.gov — Text of the CLARITY Act and details on its legislative timeline.
- YouTube — Brad Garlinghouse Fox News interview referencing Alderoty’s attendance at the White House meeting.
- Crypto Council for Innovation — Public statements describing the discussions and their constructive tone.
- Cointelegraph coverage — Reporting on the Mar-a-Lago forum and related policy discussions, including sentiment from lawmakers.
Market reaction and key details
The White House’s latest round of talks with cryptocurrency and banking representatives illustrates a persistent drive to harmonize digital-asset policy with traditional financial oversight. The aim is to craft a framework that resists regulatory fragmentation while ensuring robust protections for consumers and market integrity. In a Thursday appearance on Fox News, Ripple (the company) CEO Brad Garlinghouse reiterated that Alderoty attended the White House discussions earlier in the day, signaling the depth of the policy engagement from the industry side. The remarks followed media speculation about how the administration would approach the CLARITY Act—the House-approved package designed to regulate digital assets and present a coherent market structure—now navigating Senate committees and potential amendments.
The CLARITY Act’s journey through Congress has been irregular. After passing the House in July, the bill faced a series of delays in the Senate, with lawmakers weighing provisions that would influence conflicts of interest and extend governance for decentralized finance, tokenized equities, and stablecoins. The evolving legislative signal is that the administration seeks to balance innovation with safeguards rather than rushing to a verdict. In this context, the meeting with White House officials, as described by Crypto Council for Innovation chief Ji Hun Kim, was noted as constructive and aimed at building a framework that preserves American consumer welfare while maintaining competitive edge in global crypto markets.
Meanwhile, the broader legislative calendar remains complex. The Senate Agriculture Committee earlier advanced its own version of a digital-asset market-structure bill in January, a development that underscores the multi-committee path such legislation often travels before markup and potential floor votes. Yet opposition from some industry players has complicated the process. Coinbase (EXCHANGE: COIN) CEO Brian Armstrong publicly challenged certain provisions that would cap rewards on stablecoin holdings and warned that the bill risks weakening the CFTC’s role in favor of the SEC. These concerns illustrate a familiar tension in U.S. policy debates: how to allocate regulatory authority without constraining innovation or market functionality.
As policymakers navigate these issues, the policy discourse has also touched on high-profile gatherings. A private forum at Mar-a-Lago, attended by policymakers and industry representatives, added another layer to the conversation around the CLARITY Act’s prospects. Senator Bernie Moreno, present at the event, suggested that the act could reach a point where it could be signed into law by spring, though the legislative reality remains uncertain given the ongoing committee reviews and potential revisions. The episodic nature of such appearances reflects the evolving, often negotiation-heavy, path that digital-asset policy typically follows in Washington.
Overall, the latest round of meetings and public statements suggests a cautious but forward-looking stance from both policymakers and industry participants. The objective appears to be a framework that discourages harmful practices, clarifies regulatory jurisdiction, and supports responsible innovation in crypto markets—without stifling the capital flows that underpin a growing ecosystem. For investors and builders, the near-term takeaway is to monitor committee calendars, regulatory updates, and official statements from the White House and key agencies for hints about the direction of risk management, disclosure requirements, and the scope of oversight that a forthcoming bill could impose.
Interim guidance and verbatim quotes from executive statements will likely continue to influence sentiment, particularly as the Senate Banking Committee and other panels recalibrate their approach to market structure, stablecoins, and tokenized assets. In the interim, the market context remains one of guarded optimism, with careful attention paid to regulatory clarity as much as to any immediate policy actions. The interplay between public policy, industry feedback, and the practical realities of operating in a highly dynamic crypto landscape will continue to shape liquidity conditions and risk sentiment in the months ahead.
Notes from the coverage and the primary sources referenced above should be verified for any updates to committee schedules, official statements, or new voting outcomes as the legislative process evolves.
Crypto World
Ethereum price holds 0.618 fibonacci support as bullish volume signals reversal
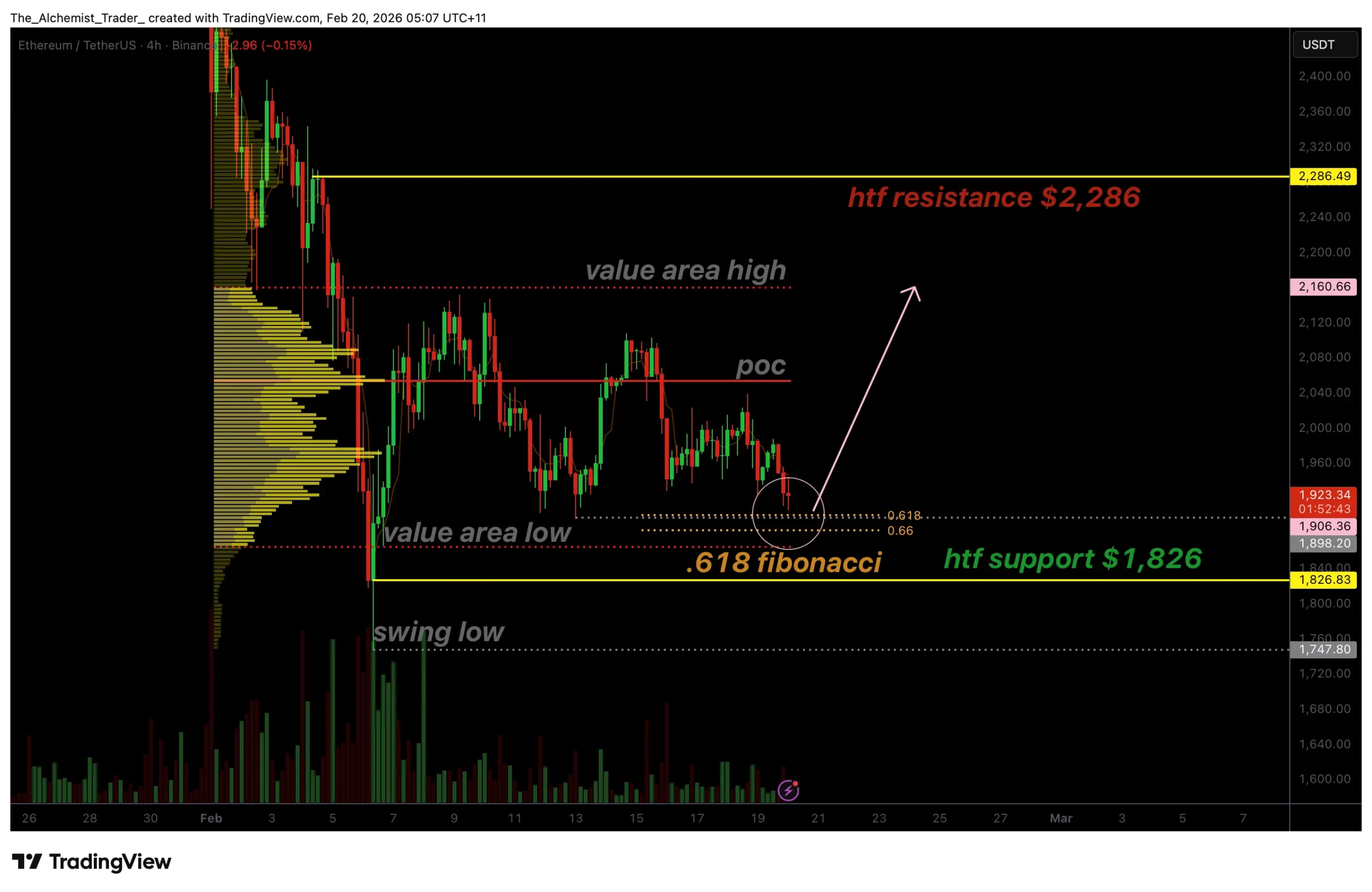
Ethereum price is testing a critical confluence support zone around the 0.618 Fibonacci level, where improving bullish volume suggests a potential reversal may be developing.
Summary
- 0.618 Fibonacci and value area low form key support zone
- Bullish volume emerging, signaling possible accumulation
- $2,286 resistance becomes upside target, if reversal confirms
Ethereum (ETH) price action has entered a decisive technical region after an extended corrective phase pushed the asset toward high-timeframe support. Following sustained selling pressure, ETH is now trading within a major confluence zone that historically attracts demand and often acts as a pivot for market reversals.
Rather than showing continued acceleration lower, recent behavior indicates stabilization near support. This shift is drawing attention from traders watching for early signs of accumulation. When price approaches major Fibonacci retracement levels alongside strong structural support, the probability of a rotational move higher begins to increase, provided buyers continue to defend the area.
Ethereum price key technical points
- 0.618 Fibonacci retracement aligns with major support, creating reversal potential
- Value area low and $1,826 high-timeframe support converge, strengthening demand zone
- Bullish volume response emerging, suggesting early accumulation behavior
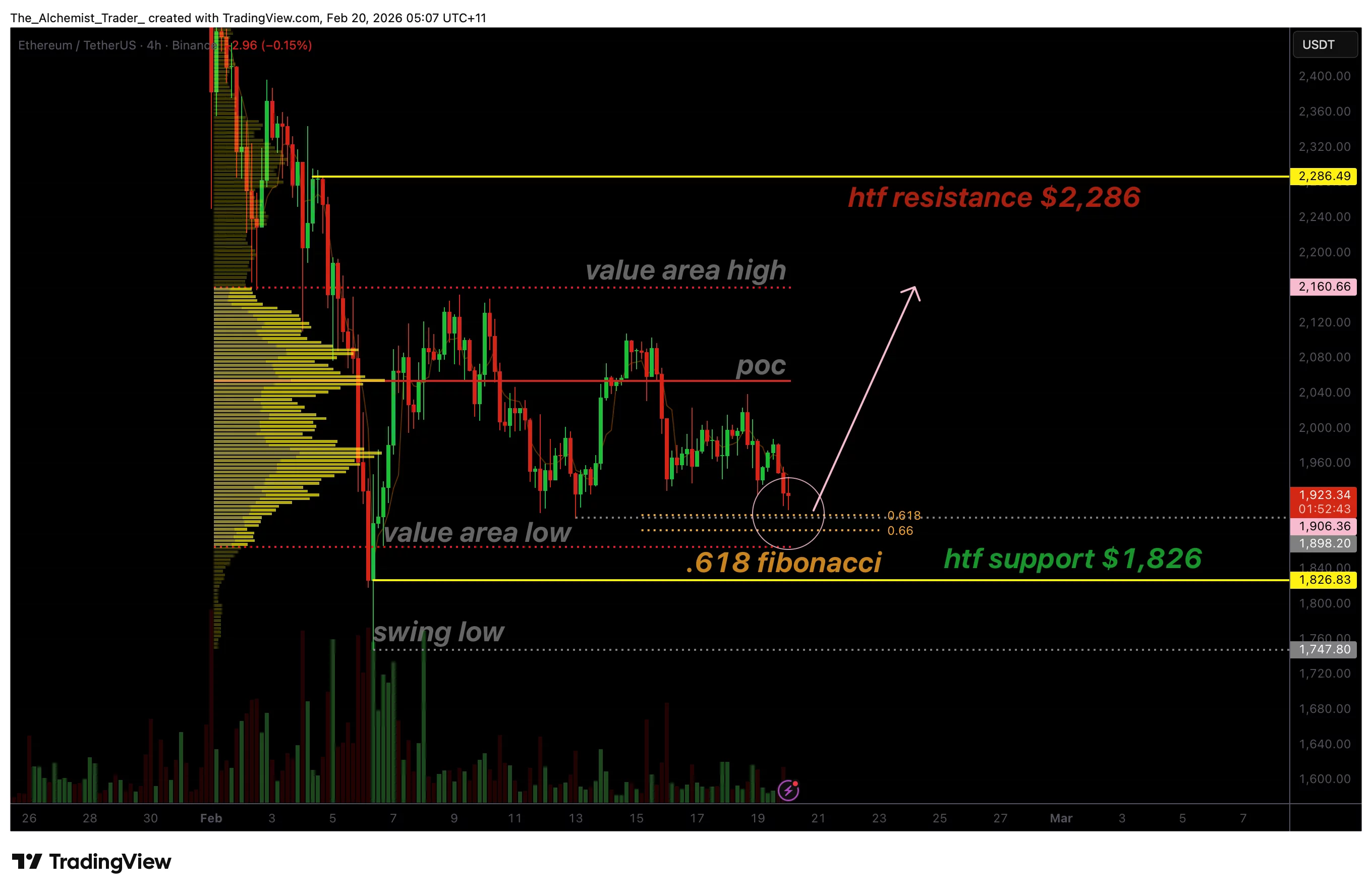
Ethereum is currently trading near $1,826, a level reinforced by multiple technical factors. The 0.618 Fibonacci retracement, often referred to as the “golden ratio” in technical analysis, sits directly within this region. Historically, this level frequently acts as a turning point during corrective moves within broader trends.
The significance of this area is amplified by its overlap with the value area low, which represents the lower boundary of fair value within the previous trading range. When price revisits such zones, markets often attempt to rebalance as buyers and sellers reassess value.
This confluence transforms the region into a high-probability reaction zone rather than an arbitrary support level.
Liquidity sweep could trigger reversal
An important dynamic unfolding around this support is the presence of resting liquidity below recent lows. Markets commonly sweep liquidity beneath key support before reversing direction. Such moves allow larger participants to accumulate positions while forcing weaker hands out of the market.
If Ethereum briefly trades below support and quickly reclaims it, the move could resemble a swing failure pattern (SFP), a classic reversal setup. This type of price action often signals that selling pressure has been absorbed and that demand is beginning to outweigh supply.
The emergence of bullish volume during these tests is particularly important, as it indicates buyers actively stepping into the market rather than passive stabilization.
Bullish volume suggests accumulation
One of the more constructive developments is the gradual increase in bullish volume near support. Rising buy-side participation at key technical levels often precedes rotational moves higher.
Volume behavior frequently acts as confirmation of intent. When buyers appear at high-timeframe support while momentum indicators begin stabilizing, markets transition from distribution into accumulation phases. Ethereum’s current setup reflects early signs of this transition.
However, confirmation remains essential. Sustained buying interest must continue to defend the support region to validate the reversal thesis.
Upside rotation targets higher resistance
If Ethereum successfully holds the $1,826 support cluster, attention shifts toward higher resistance zones. The first major objective lies near the value area high, where price previously faced rejection.
Beyond that, high-timeframe resistance around $2,286 becomes the next technical target. A rotational move toward these levels would represent a recovery within the broader trading structure rather than an immediate trend reversal.
Such moves often unfold gradually, beginning with stabilization, followed by higher lows and expanding bullish momentum.
Market structure at a turning point
From a market structure perspective, Ethereum remains at an inflection point. The broader correction has not yet invalidated long-term structure, but continued defense of support is necessary to prevent deeper downside continuation.
The combination of Fibonacci confluence, liquidity dynamics, and improving volume creates conditions favorable for a reversal attempt. Still, failure to hold this region would reopen risks toward lower support levels.
What to expect in the coming price action
From a technical, price action, and market structure standpoint, Ethereum is positioned at a potential turning point. Holding above the 0.618 Fibonacci support near $1,826 significantly increases the probability of a rotational move higher.
In the immediate short term, traders should monitor volume expansion and price acceptance above support. A confirmed swing failure or strong bullish reaction could initiate a move toward higher resistance zones, beginning with the value area high and extending toward $2,286.
Until proven otherwise, Ethereum appears to be transitioning from corrective weakness toward stabilization. If demand continues to build at current levels, the market may be preparing for a relief rally following its recent decline.
Crypto World
Ether.fi Moves Crypto Card Product to OP Mainnet From Scroll
Ether.fi is migrating its payments rail, Ether.fi Cash, to OP Mainnet, moving roughly 70,000 active cards and 300,000 accounts away from the Scroll Layer 2 network, according to a recent blog post.
The transition, announced Wednesday, involves shifting millions in Total Value Locked (TVL) over the coming months to integrate with Optimism’s broader Superchain ecosystem.
This strategic pivot underscores the fierce competition among Layer 2 solutions for high-volume consumer applications, with Ether.fi citing access to a larger DeFi ecosystem as a primary driver.
Key Takeaways
- Mass Migration: Approximately 70,000 active cards and 300,000 accounts are moving to Optimism.
- Volume Impact: Ether.fi Cash processes roughly $2 million in daily spend volume.
- Incentives: Gas fees for card transactions will be fully absorbed by Ether.fi during and after the transition.
Why Is Network Choice Critical?
Ether.fi initially built its reputation on asset restaking but successfully pivoted to consumer payments with Ether.fi Cash in 2024.
The product allows users to spend stablecoins or borrow against staked assets like eETH to fund real-world Visa purchases.
According to Paymentscan, these cards now facilitate nearly half of all crypto-native card transactions.
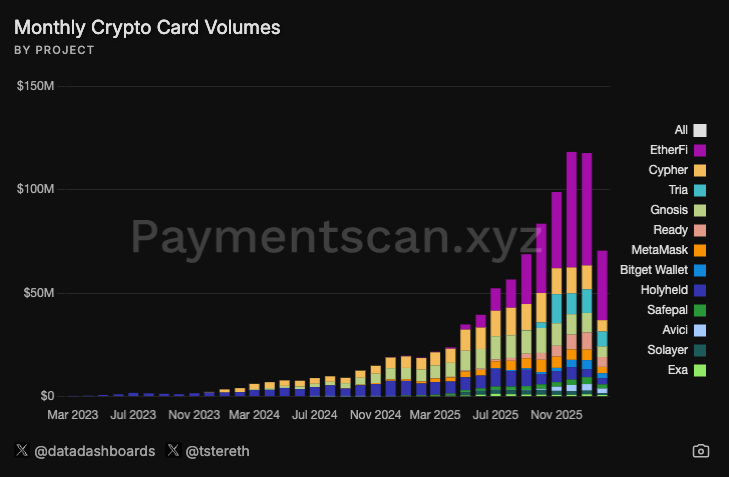
The choice of underlying network defines transaction speed and liquidity depth.
Operational stability is paramount for consumer products; just look at what happened to what happened to Moonwell this week.
Payment providers must mitigate infrastructure risks by selecting mature execution layers. Ether.fi’s move signals that liquidity depth on OP Mainnet currently outweighs the ZK-rollup advantages offered by Scroll for this specific use case.
Discover: The best crypto presales right now
Breaking Down the Migration
The migration utilizes an OP Enterprise partnership, providing Ether.fi with dedicated support and shared codebase tooling.
Transaction costs for card usage will be absorbed by the protocol, ensuring users experience no friction during the switch. This is critical as Ether.fi Cash currently processes roughly 2,000 internal swaps and 28,000 spend transactions daily, metrics that have reportedly doubled every two months.
Capital efficiency is the core technical driver here. Much like how new frameworks are introducing unified liquidity and staking solutions, Ether.fi expects deeper liquidity for swaps on OP Mainnet compared to its previous deployment.
Optimized liquidity pools mean lower slippage for users converting crypto to fiat at the point of sale.
The OP Stack itself processed a staggering 3.6 billion transactions in the second half of 2025, representing 13% of all crypto transactions in that period.
What Does This Mean for the L2 Landscape?
For Scroll, this represents a notable loss of volume. The ZK-powered chain had relied on Ether.fi as a significant driver of daily activity.
Conversely, Optimism reinforces its position as a dominant hub, securing a high-retention consumer product just as internal ecosystem dynamics shift, notably with Base signaling moves toward a bespoke chain platform.
This consolidation reflects a maturing Ethereum ecosystem where projects prioritize battle-tested liquidity over novel tech stacks.
It aligns with broader institutional positioning, similar to how funds like Founders Fund have adjusted their ETH-related exposure to align with prevailing market realities.
For the end user, the backend plumbing changes, but the card in their digital wallet simply becomes more efficient.
Discover: Diversify your crypto portfolio with these top picks
The post Ether.fi Moves Crypto Card Product to OP Mainnet From Scroll appeared first on Cryptonews.
Crypto World
Russia May Block Foreign Crypto Exchanges Under New Domestic Regulations

Breaking RBC reports suggest that Russia is manoeuvring to block foreign crypto exchange websites like Binance and OKX starting September 1 unless they comply with strict domestic regulations.
The strategic move funnels crypto customers to locally licensed and state monitored exchanges, securing control over cross-border on-chain capital flows while tightening the grip on retail speculation.
Key Takeaways
- The Move: Foreign crypto exchanges face a potential blockade by September 1 under new “experimental” legal frameworks.
- The Goal: Authorities want to centralize cross-border crypto payments to evade sanctions while monitoring domestic capital flight.
- The Impact: Traders using offshore platforms may be forced onto planned state-backed exchanges in Moscow and St. Petersburg.
Why Is This Happening Now?
Why limit access now? It comes down to control. Following the laws signed by President Putin in August 2024, crypto is no longer viewed merely as a speculative asset but as a critical tool for bypassing SWIFT bans. However, the Kremlin demands oversight.
Data from Chainalysis indicates Russia has pivoted toward “legislated sanctions evasion.” By forcing activity onto domestic platforms, authorities can monitor flows that were previously opaque.
This broadly mirrors concerns across the continent in Brussels, where leaders like Christine Lagarde warn of regulatory gaps in digital finance. Moscow wants those gaps closed.
The government is essentially bifurcating the market. One lane is for state-sanctioned entities like exporters using crypto for international settlement.
The other lane (retail) is being subjected to extreme friction to prevent capital flight.
Discover: The best meme coins on Solana
How Will the Ban Work?
The proposed mechanism targets foreign platforms offering unlicensed access. While major players like Coinbase, which Cathie Wood recently doubled down on, rely on global accessibility, Russian user bases are substantial.
Under the new regime, only exchanges operating within specific “experimental legal regimes” (EPR) might survive.
Reports suggest plans for state-backed exchanges in St. Petersburg and Moscow are accelerating.
These venues would facilitate cross-border trade for approved exporters while retail traders get squeezed out of foreign venues. Compliance is the bottleneck.
As noted in Crystal Intelligence’s regulatory roadmap, strict KYC and capital requirements have been on the table for Russian regulators since 2022. Now, they are becoming entry barriers.
Finance Minister Anton Siluanov has previously admitted that Moscow finding a regulatory solution is complex but vital.
Yet, the urgency to mitigate sanctions is overriding technical hesitations. This aligns with global trends where developer liability and platform compliance are central to legislative debates.
If foreign entities do not register locally, a move many will refuse due to Western sanctions, they face a hard block.
What Happens Next for Traders?
If the crackdown goes live in September, expect a liquidity fracture. Russian retail volume, estimated over a hundred billion annually, will likely flood into underground P2P networks or the few sanctioned domestic entities like Garantex.
As industry lobbying groups work to define clearer frameworks globally, Russia’s isolating move offers a stark counter-narrative: nationalization over decentralization.
In that light, the ruble pairing spreads may reveal the first signs of this shift.
The post Russia May Block Foreign Crypto Exchanges Under New Domestic Regulations appeared first on Cryptonews.
Crypto World
Solana Price Shows Signs of Revival: Breakout From $90?
Solana has remained range-bound after nearly two weeks of consolidation below $90. The lack of direction reflects persistent uncertainty across the crypto market.
On-chain indicators hint at a gradual recovery. However, losses endured by investors continue to shape sentiment. While technical signals show improvement, the broader structure suggests that risks remain present.
Solana Metrics’ Mixed Signals
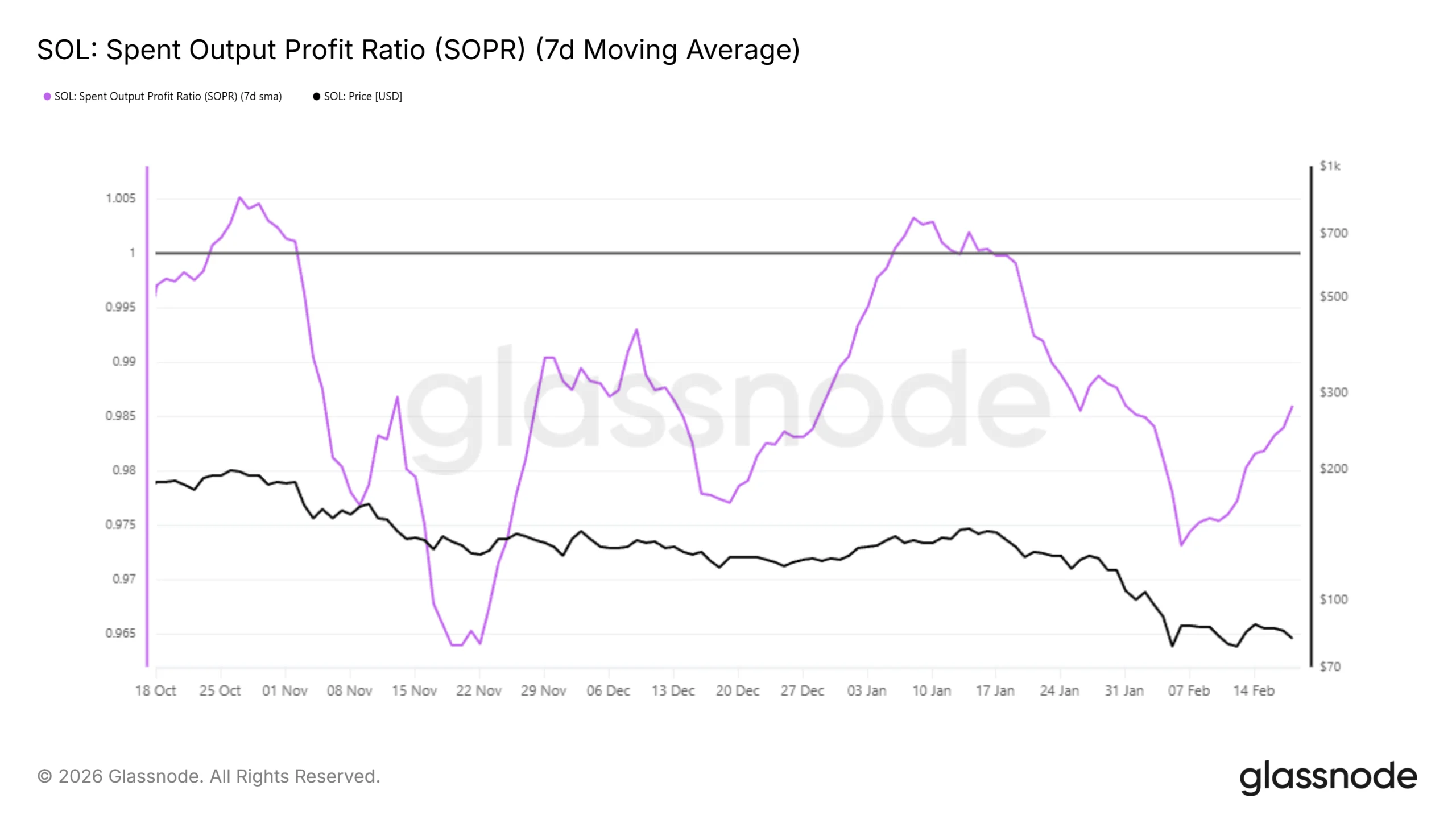
The Spent Output Profit Ratio, or SOPR, has recently ticked higher from the negative zone. A reading below 1 indicates that investors are selling at a loss. The recent uptick signals that realized losses are beginning to dissipate.
Historically, a move above 1 during extended bearish periods marks the first wave of profit-taking. Such transitions often lead to renewed volatility. When profitability briefly returns, some Solana investors sell to exit positions, triggering short-term pullbacks.
Want more token insights like this? Sign up for Editor Harsh Notariya’s Daily Crypto Newsletter here.
This pattern has appeared twice in the past three months. Each instance was followed by renewed selling pressure. If SOPR climbs above 1 again, a similar reaction could unfold. That dynamic may limit immediate recovery despite improving on-chain sentiment.
Technical indicators offer mixed signals. The Chaikin Money Flow is rising but remains in negative territory. This incline suggests that outflows are declining, yet capital has not returned decisively.
A move above the zero line would confirm sustained inflows. Until that shift occurs, Solana remains vulnerable to further weakness. Gradual improvement does not guarantee reversal, especially in an environment of cautious investor positioning.
Institutions Like Solana
Institutional flows provide a contrasting signal. For the week ending February 13, Solana recorded $31 million in inflows. Among major tokens, only XRP saw comparable institutional support.
These inflows reflect continued interest from large wallets. Despite broader bearish conditions, institutions appear to view Solana as strategically valuable. Such support can cushion downside moves during periods of market stress.

Institutional accumulation has likely prevented deeper declines. Strong backing from larger players reinforces confidence in the network’s long-term prospects. This underlying demand remains a stabilizing factor even as retail sentiment fluctuates.
SOL Price Continues Moving Sideways
Solana price is trading at $81 at the time of writing. The token remains range-bound between $78 support and $87 resistance. This consolidation has persisted for over two weeks, signaling indecision among market participants.
Without clear recovery catalysts, sideways movement may continue. If bearish pressure intensifies, SOL could slip below $78. A breakdown may expose the next support near $73, extending short-term downside risk.
Conversely, a bounce from $78 could shift momentum. A decisive move above $87 would signal breakout potential. Sustained buying pressure could then push Solana toward $100. If SOL clears that psychological barrier, price may advance toward $110, invalidating the prevailing bearish outlook.
Crypto World
Exclusive: Eric Trump Calls Maldives Hotel First of Many Real Estate Tokenization Projects


The new project highlights World Liberty Financial’s broader push to bring traditional assets on-chain.
World Liberty Financial’s plan to tokenize loan revenue interests tied to the Trump International Hotel & Resort in the Maldives is just the start of a larger plan, World Liberty Financial co-founder Eric Trump said in an exclusive interview with The Defiant.
The project, announced Wednesday, Feb. 18, is being developed with real estate firm DarGlobal and Securitize, a platform known for tokenizing real-world assets (RWAs), including funds like BlackRock’s BUIDL.
Trump told Camila Russo, founder of The Defiant, that tokenization will change real estate finance by making deals simpler and allowing more people to invest who couldn’t before.
“Do we have more plans for this? Yes, certainly, World Liberty has plans to be in the tokenization space of many different asset types, and they’re sprinting toward that,” Trump said. “I believe [DarGlobal CEO Ziad El Chaar] and I will do many more projects, tokenize many more projects, and I think history will look back and say, you know, these were the guys that popped the cork of the champagne bottle.”
The first token sale is designed to give accredited investors a fixed return, a share of income from loans tied to the resort, and the potential for profits upon any future sale. The tokens are expected to be issued on public blockchains and could later be used as collateral on World Liberty Financial’s platform, according to a press release viewed by The Defiant.
“We believe that scalable on-chain real estate products issued with compliance, governance, and market structure in mind will be globally sought after. That’s exactly what this partnership with WLFI is designed to deliver,” said Carlos Domingo, co-founder and CEO of Securitize.
The deal highlights a broader trend in crypto of more institutions and firms focusing on tokenization – one of the fastest-growing sectors in the space. As of Thursday, Feb. 19, the distributed asset value of tokenized RWAs has climbed to $24.8 billion, up 11% in the past month, while the number of holders rose more than 30% in the same time frame, according to RWAxyz.
“Everything’s gonna be tokenized,” Trump emphasized. “Commodities are gonna be tokenized, Hollywood can be tokenized, artists are gonna be tokenized, brands, I mean, you can tokenize just about anything.”
The Maldives resort is a flagship hospitality development scheduled to open in 2030. It is expected to include 100 beach and overwater villas, according to the press release.
World Liberty Financial’s native token WLFI is currently trading at around $0.12, down 3.8% over the past 24 hours, according to CoinGecko. The move follows Wednesday’s rally of 30%, which occurred just ahead of the World Liberty Financial forum held at President Donald Trump’s Mar-a-Lago resort.
Meanwhile, World Liberty Financial’s USD1 stablecoin recently surpassed $5.1 billion in circulation, up from roughly $3 billion just weeks ago. It’s now the fifth-largest stablecoin by market capitalization, according to DeFiLlama.
Crypto World
Etherfi, Scroll’s Top Fee-Generator, Leaves for Optimism
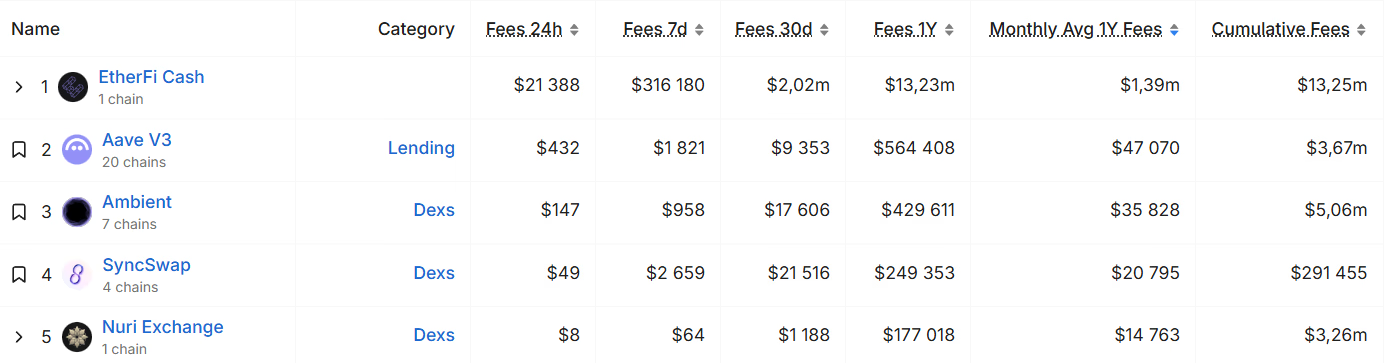
Both etherfi and Optimism described the transition as a long-term partnership.
Decentralized neobank and crypto card issuer etherfi is leaving Scroll for Optimism, taking with it millions of dollars in total value locked and monthly fees generated on Scroll, data shows.
In an X post on Wednesday, Feb. 18, etherfi said it plans to move its Cash accounts and card program from Scroll to Optimism’s OP Mainnet, migrating more than 70,000 active cards, roughly 300,000 user accounts, and nearly $160 million in TVL in the coming months.
With etherfi, Scroll’s own TVL is only around $188 million as of today, Feb. 19, per data from DefiLlama.

The decision marks a clear break from Scroll, an Ethereum ZK rollup, where etherfi was the dominant consumer-facing app. According to data from DefiLlama, as of today, EtherFi Cash, the company’s crypto card and digital account product, accounted for roughly $13.2 million in annualized fees, and over $23,000 in the past 24 hours.

For comparison, Aave V3, the second-largest protocol on Scroll by annual fees, boasts only around $564,000 over the past year, meaning EtherFi Cash produced nearly 23 times more in fees.

Since launching its Cash product in September 2024, the company says it has processed more than $265 million in card spend, positioning the service as one of the largest non-custodial crypto card programs currently in operation, the firm noted in its X post announcing the migration.
‘Long-Term Partnership’
Per its post, etherfi is framing the transition as a “long-term partnership,” pointing to deeper liquidity, broader DeFi integrations and native stablecoin support on Optimism.
In commentary for The Defiant, etherfi co-founder Rok Kopp explained that Optimism “has been one of the pioneers of the L2 space and Ethereum scaling solutions more broadly, and the Superchain has powered many of the most widely used blockchain products in the world.”
Kopp added:
“We are excited to build on battle tested, cost efficient infrastructure we know we can scale effectively on. Working with the OP Labs team has been our pleasure, and we believe our collaboration can help propel the DeFi neobanking space to new heights”
Optimism, for its part, also described the migration in a Feb. 18 blog post as a “long-term OP Enterprise partnership” aimed at scaling on-chain payments.
With its leading fee-generating dApp departing, Scroll now faces losing a big chunk of its revenue.
The Defiant reached out to etherfi and Scroll for comments on the move, but hasn’t heard back by press time.
-
 Video3 days ago
Video3 days agoBitcoin: We’re Entering The Most Dangerous Phase
-

 Tech5 days ago
Tech5 days agoLuxman Enters Its Second Century with the D-100 SACD Player and L-100 Integrated Amplifier
-
 Crypto World2 days ago
Crypto World2 days agoCan XRP Price Successfully Register a 33% Breakout Past $2?
-

 Sports3 days ago
Sports3 days agoGB's semi-final hopes hang by thread after loss to Switzerland
-

 Video6 days ago
Video6 days agoThe Final Warning: XRP Is Entering The Chaos Zone
-

 Tech3 days ago
Tech3 days agoThe Music Industry Enters Its Less-Is-More Era
-

 Business2 days ago
Business2 days agoInfosys Limited (INFY) Discusses Tech Transitions and the Unique Aspects of the AI Era Transcript
-

 Entertainment1 day ago
Entertainment1 day agoKunal Nayyar’s Secret Acts Of Kindness Sparks Online Discussion
-

 Video2 days ago
Video2 days agoFinancial Statement Analysis | Complete Chapter Revision in 10 Minutes | Class 12 Board exam 2026
-

 Tech1 day ago
Tech1 day agoRetro Rover: LT6502 Laptop Packs 8-Bit Power On The Go
-
 Crypto World6 days ago
Crypto World6 days agoBhutan’s Bitcoin sales enter third straight week with $6.7M BTC offload
-

 Sports16 hours ago
Sports16 hours agoClearing the boundary, crossing into history: J&K end 67-year wait, enter maiden Ranji Trophy final | Cricket News
-

 Entertainment22 hours ago
Entertainment22 hours agoDolores Catania Blasts Rob Rausch For Turning On ‘Housewives’ On ‘Traitors’
-

 Crypto World6 days ago
Crypto World6 days agoKalshi enters $9B sports insurance market with new brokerage deal
-

 Business2 days ago
Business2 days agoTesla avoids California suspension after ending ‘autopilot’ marketing
-

 NewsBeat4 days ago
NewsBeat4 days agoThe strange Cambridgeshire cemetery that forbade church rectors from entering
-

 Crypto World1 day ago
Crypto World1 day agoWLFI Crypto Surges Toward $0.12 as Whale Buys $2.75M Before Trump-Linked Forum
-

 NewsBeat4 days ago
NewsBeat4 days agoMan dies after entering floodwater during police pursuit
-

 NewsBeat5 days ago
NewsBeat5 days agoUK construction company enters administration, records show
-
 Crypto World6 days ago
Crypto World6 days agoBlackRock Enters DeFi Via UniSwap, Bitcoin Stages Modest Recovery



 Russia is setting up two Cryptocurrency exchanges—one for international trade, one for Russian — alongside its own stablecoin. Wave "bye" to another aspect of sanctions.
Russia is setting up two Cryptocurrency exchanges—one for international trade, one for Russian — alongside its own stablecoin. Wave "bye" to another aspect of sanctions. 







