Crypto World
Why Address Poisoning Works Without Stealing Private Keys
Key takeaways
-
Address poisoning exploits behavior, not private keys. Attackers manipulate transaction history and rely on users mistakenly copying a malicious lookalike address.
-
Cases such as the 50-million-USDT loss in 2025 and the 3.5 wBTC drain in February 2026 demonstrate how simple interface deception can lead to massive financial damage.
-
Copy buttons, visible transaction history and unfiltered dust transfers make poisoned addresses appear trustworthy within wallet interfaces.
-
Because blockchains are permissionless, anyone can send tokens to any address. Wallets typically display all transactions, including spam, which attackers use to plant malicious entries.
Most crypto users believe that their funds stay secure as long as their private keys are protected. However, as a rising number of scams show, this is not always the case. Scammers have been using an insidious tactic, address poisoning, to steal assets without ever accessing the victim’s private key.
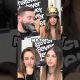
In February 2026, a phishing scheme targeted a Phantom Chat feature. Using an address poisoning tactic, attackers successfully drained roughly 3.5 Wrapped Bitcoin (wBTC), worth more than $264,000.
In 2025, a victim lost $50 million in Tether’s USDt (USDT) after copying a poisoned address. Such incidents have highlighted how poor interface design and everyday user habits can result in massive losses.

Prominent crypto figures like Binance co-founder Changpeng “CZ” Zhao have publicly urged wallets to add stronger safeguards following address poisoning incidents.
This article explains how address poisoning scams exploit user behavior rather than private key theft. It details how attackers manipulate transaction history, why the tactic succeeds on transparent blockchains and what practical steps users and wallet developers can take to reduce the risk.
What address poisoning really involves
Unlike traditional hacks that target private keys or exploit code flaws, address poisoning manipulates a user’s transaction history to deceive them into sending funds to the wrong address.
Usually, the attack proceeds in the following way:
-
Scammers identify high-value wallets via public blockchain data.
-
They create a wallet address that closely resembles one the victim often uses. For example, the attacker may match the first and last few characters.
-
They send a small or zero-value transaction to the victim’s wallet from this fake address.
-
They rely on the victim copying the attacker’s address from their recent transaction list later.
-
They collect the funds when the victim accidentally pastes and sends them to the malicious address.
The victim’s wallet and private keys remain untouched, and blockchain cryptography stays unbroken. The scam thrives purely on human error and trust in familiar patterns.
Did you know? Address poisoning scams surged alongside the rise of Ethereum layer-2 networks, where lower fees make it cheaper for attackers to mass-send dust transactions to thousands of wallets at once.
How attackers craft deceptive addresses
Crypto addresses are lengthy hexadecimal strings, often 42 characters on Ethereum-compatible chains. Wallets usually show only a truncated version, such as “0x85c…4b7,” which scammers take advantage of. Fake addresses have identical beginnings and endings, while the middle portion differs.
Legitimate address (example format):
0x742d35Cc6634C0532925a3b844Bc454e4438f44e
Poisoned lookalike address:
0x742d35Cc6634C0532925a3b844Bc454e4438f4Ae
Scammers use vanity address generators to craft these near-identical strings. The fake one appears in the victim’s transaction history thanks to the dusting transfer. To users, it looks trustworthy at a glance, especially since they rarely verify the full address string.
Did you know? Some blockchain explorers now automatically label suspicious dusting transactions, helping users spot potential poisoning attempts before interacting with their transaction history.
Why this scam succeeds so well
There are several intertwined factors that make address poisoning devastatingly effective:
-
Human limitations in handling long strings: Because addresses are not human-friendly, users rely on quick visual checks at the beginning and end. Scammers exploit this tendency.
-
Convenient but risky wallet features: Many wallets offer easy copy buttons next to recent transactions. While this feature is helpful for legitimate use, it becomes risky when spam entries sneak in. Investigators such as ZachXBT have pointed to cases where victims copied poisoned addresses directly from their wallet UI.

3. No need for technical exploits: Because blockchains are public and permissionless, anyone can send tokens to any address. Wallets usually display all incoming transactions, including spam, and users tend to trust their own history.
The vulnerability lies in behavior and UX, not in encryption or key security.
Why keys aren’t enough protection
Private keys control authorization, meaning they ensure only you can sign transactions. However, they cannot verify whether the destination address is correct. Blockchain’s core traits — permissionless access, irreversibility of transactions and trust minimization — mean malicious transactions get permanently recorded.
In these scams, the user willingly signs the transfer. The system functions exactly as designed, and the flaw lies in human judgment.
Underlying psychological and design issues involve:
-
Routine habits: People tend to repeatedly send funds to the same addresses, so they copy from their transaction history instead of reentering addresses.
-
Cognitive strain: Transactions involve multiple steps, such as addresses, fees, networks and approvals. Many users find scrutinizing every character tedious.
-
Truncated displays: Wallet UIs hide most of the address, leading to partial checks.
Did you know? In certain cases, attackers automate address lookalike generation using GPU-powered vanity tools, allowing them to produce thousands of near-identical wallet addresses within minutes.
Practical ways to stay safer
While address poisoning exploits user behavior rather than technical vulnerabilities, small changes in transaction habits can significantly reduce the risk. Understanding a few practical safety measures can help crypto users avoid costly mistakes without requiring advanced technical knowledge.
For users
Simple verification habits and transaction discipline can significantly reduce your chances of falling victim to address poisoning scams.
-
Build and use a verified address book or whitelist for frequent recipients.
-
Verify the full address. Use a checker or compare it character by character before making payments.
-
Never copy addresses from recent transaction history. Instead, reenter addresses or use bookmarks.
-
Ignore or report unsolicited small transfers as potential poisoning attempts.
For wallet developers
Thoughtful interface design and built-in safeguards can minimize user error and make address poisoning attacks far less effective.
-
Filtering or hiding low-value spam transactions
-
Similarity detection for recipient addresses
-
Pre-signing simulations and risk warnings
-
Built-in poisoned address checks via onchain queries or shared blacklists.
Cointelegraph maintains full editorial independence. The selection, commissioning and publication of Features and Magazine content are not influenced by advertisers, partners or commercial relationships.
Crypto World
Moonwell Proposes $2.68M Recovery Plan After cbETH Liquidation Incident Harms 181 Borrowers on Base

TLDR:
- Roughly 181 Moonwell borrowers on Base lost ~$2.68M due to oracle-driven cbETH liquidations from Feb 14–18, 2026.
- Moonwell will allocate ~$310,000 from its Apollo Treasury as an immediate pro-rata repayment to all affected borrowers.
- The remaining ~$2.37M will be repaid gradually through future protocol fees and OEV revenue via Sablier over 12 months.
- MFAM holders will convert their tokens into stkWELL at a 1:1.5 ratio, consolidating Apollo DAO into Moonwell’s primary governance.
Moonwell has released a recovery proposal addressing unfair liquidations of cbETH collateral between February 14 and 18, 2026.
The incident affected roughly 181 borrowers on Base, resulting in approximately $2.68M in net losses. Protocol behavior tied to MIP-X43, not user error, drove the liquidations.
The plan combines treasury funds with future revenue and includes a transition for MFAM holders into the WELL ecosystem.
cbETH Liquidation Recovery Targets 181 Affected Borrowers
The Moonwell team conducted a full onchain review of all liquidation activity during the incident window. Each borrower’s loss was calculated on a net basis, meaning only realized economic harm qualifies for remediation.
The methodology accounts for all cbETH collateral seized, minus the USD value of debt repaid at the time of liquidation.
The proposal was direct about what caused the harm. “These users trusted Moonwell with their assets and were harmed through no fault of their own,” the post stated.
Crucially, cbETH was repriced at $2,200 per token to correct erroneous oracle values that contributed to the problem. This adjustment ensures that repayments reflect actual market conditions rather than distorted price data.
To begin repayments promptly, approximately $310,000 will be drawn from the Moonwell Apollo Treasury. This amount will be distributed pro-rata to affected borrowers based on their individual calculated losses.
The proposal described this allocation as “an immediate good-faith remediation without jeopardizing protocol stability.”
The remaining balance of roughly $2.37M will be repaid over time through future protocol revenue. This includes net protocol fees and OEV revenue under the current fee split structure.
All repayments will be claimable through Sablier over a 12-month window, after which unclaimed rewards expire.
MFAM Wind-Down Consolidates Apollo DAO Into Moonwell’s Primary Governance
The proposal also addresses the full deprecation of Moonwell on Moonriver, which was completed on January 29, 2026. Chainlink’s decision to sunset oracle feeds on Moonriver forced a gradual reduction of collateral factors. With MIP-R38 passed, all Moonriver markets reached a 0% collateral factor, formally closing the deployment.
As Moonriver operations wind down, the Apollo DAO governed by MFAM will consolidate into the primary Moonwell DAO governed by WELL.
The proposal described the transition as “simplifying governance, aligning incentives, and closing out legacy infrastructure.” MFAM holders will convert their holdings into stkWELL at a 1:1.5 ratio, based on a snapshot taken at proposal submission.
The proposal noted that this conversion brings MFAM holders “direct exposure to Moonwell’s ongoing development on Base and future deployments, while eliminating fragmentation across governance tokens and treasuries.” The MFAM-to-stkWELL conversion will also be claimable for up to 12 months via Sablier.
By addressing both the cbETH incident and the MFAM wind-down together, the proposal aims to close out Moonriver “in a clean, accountable manner.”
The Moonwell DAO will vote separately on treasury allocation, the long-term repayment commitment, and execution authority.
Crypto World
US CLARITY Act To ‘Hopefully’ Pass By April: Bernie Moreno
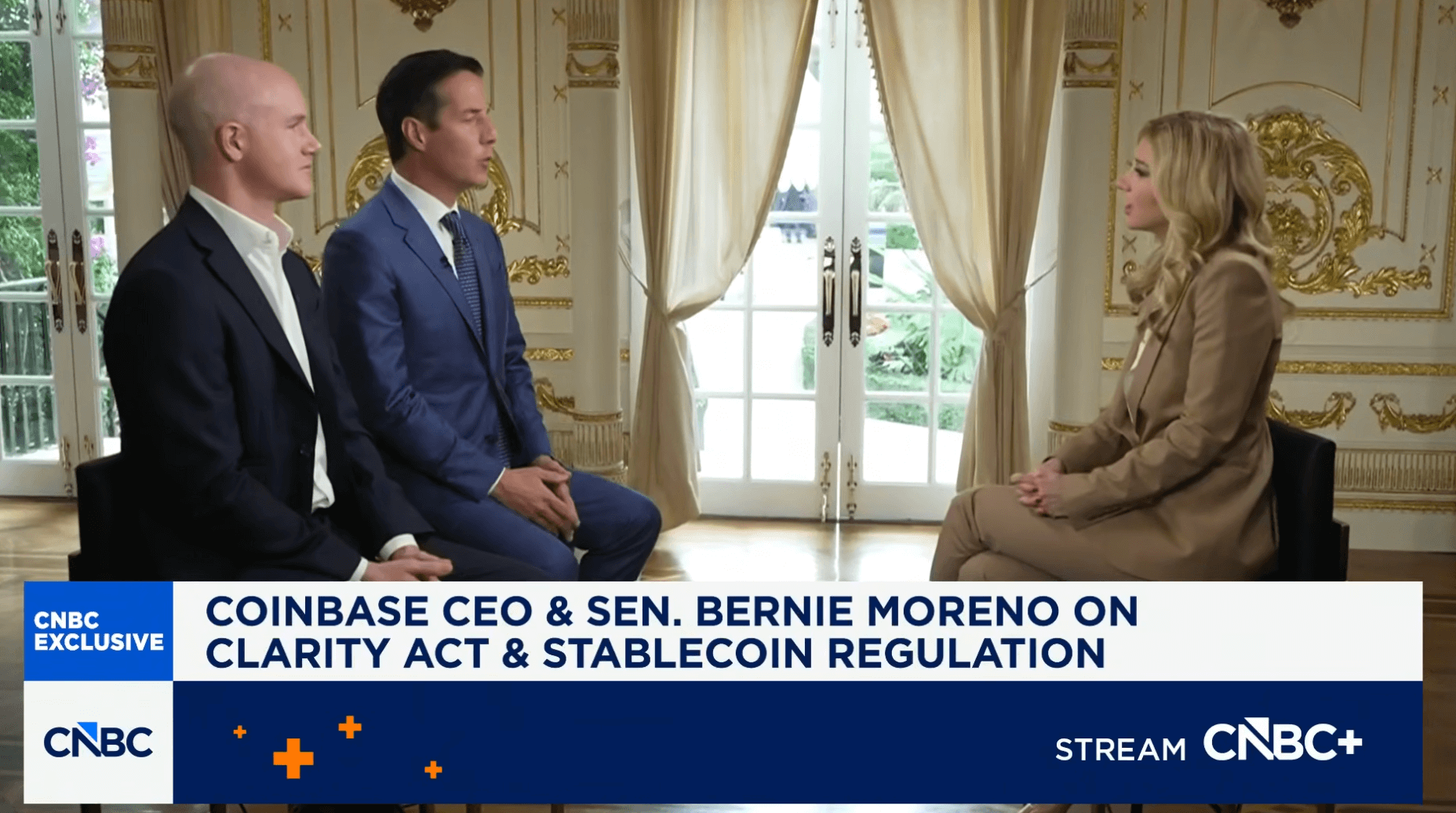
The US CLARITY Act, a highly anticipated bill aimed at providing greater clarity for the US crypto industry, could make it through Congress in just over a month, according to crypto-friendly US Senator Bernie Moreno.
“Hopefully by April,” Moreno told CNBC during an interview at US President Donald Trump’s Mar-a-Lago property in Florida on Wednesday.
Coinbase CEO Brian Armstrong joined Moreno for the interview, explaining that they were with representatives from the crypto, banking and US Congress at the World Liberty Financial (WLF) crypto forum to reach a solution on market structure.
“A path forward” is in sight, says Moreno
“One of the big issues that did come up in the past was this idea of stablecoins on rewards,” Armstrong said. The banking industry previously raised concerns that offering stablecoin yields could undermine traditional banking and shift deposits and interest away from banks.
While Armstrong had issues with the draft bill and withdrew his support for the CLARITY Act in January, he said there is “now a path forward, where we can get a win-win-win outcome here.”

“A win for the crypto industry, a win for the banks, and a win for the American consumer to get President Trump’s crypto agenda through to the finish line, so we can make America the crypto capital of the world,” Armstrong said.
Armstrong said the crypto exchange previously couldn’t support the bill because it includes provisions that ban interest-bearing stablecoins and position the US Securities and Exchange Commission as the primary regulator of the crypto industry. The White House was reportedly disappointed by Coinbase’s decision to withdraw its support, describing the move as a “unilateral” action that blindsided administration officials.
Moreno admitted that the delay stems from “getting hung up” on the stablecoin rewards, which he said “shouldn’t be part of this equation.”
Crypto prediction platform Polymarket’s odds of the US CLARITY Act passing in 2026 briefly surged to 90% on Wednesday before falling to 72% at the time of publication.
Moreno shuts down idea of a Democrat-led midterm election
Meanwhile, Moreno dismissed the idea that a Democratic takeover of Congress could threaten the bill when asked. “The House isn’t going to go Democrat, and neither is the Senate,” Moreno said.
“The American people are sick and tired of open borders; that is why we got elected. They were sick and tired of high inflation, and they were sick and tired of an out-of-control government,” he added.
Related: ECB targets 2027 digital euro pilot as provider selection begins in Q1 2026
On Dec. 19, White House crypto and AI czar David Sacks voiced strong confidence that the bill would pass early this year.
“We are closer than ever to passing the landmark crypto market structure legislation that President Trump has called for. We look forward to finishing the job in January,” Sacks said at the time.
Magazine: Bitcoin may take 7 years to upgrade to post-quantum: BIP-360 co-author
Crypto World
Ledn raises $188m with first BTC backed bond sale in asset backed market


Ledn, a crypto lending company, has completed the first asset-backed securities (ABS) deal backed by bitcoin collateral, raising $188 million for crypto credit markets.
Asset-backed securities are bonds backed by pools of underlying loans, with investors receiving payments from the cash flows generated by those loans.
Bloomberg reported that the bonds are secured by a pool of more than 5,400 consumer loans issued by the firm, each backed by borrowers’ bitcoin holdings. The loans carry a weighted average interest rate of 11.8%.
The deal includes two tranches, with the investment-grade portion priced at 335 basis points over the benchmark rate. Jefferies served as sole structuring agent and bookrunner, according to Bloomberg.
Bitcoin’s volatility has been in focus, with the largest cryptocurrency by market capitalization falling as much as 50% over the past four months to as low as $60,000.
Crypto firm Ledn sells Bitcoin-backed bonds in ABS market first
>First ever deal of its kind in asset-backed debt
>Secured by pool of 5,400 Bitcoin-collateralized loans that consumers took from Ledn at weighted avg rate of 11.8%
>Investment grade tranche priced at +335bps pic.twitter.com/Rx3944uGys— matthew sigel, recovering CFA (@matthew_sigel) February 18, 2026
The structure employs automated collateral liquidation when thresholds are breached, a feature designed to protect investors during sharp market declines.
Crypto World
Crypto, TradFi Execs Mingle At Trump Crypto Event

Trump family-owned Mar-a-Lago was home to traditional finance giants, US government officials and crypto executives in a crypto forum on Wednesday, hosted by the family’s sprawling crypto company.
Coinbase CEO Brian Armstrong and Binance co-founder Changpeng Zhao, who Donald Trump pardoned last year, were at the exclusive World Liberty Forum event alongside Goldman Sachs CEO David Solomon and the heads of the Nasdaq and New York Stock Exchange.
The event saw traditional finance executives and US regulators embrace crypto, with Solomon, a long-time crypto skeptic, saying on stage that he now owns “a little Bitcoin, very little,” according to one of the attendees.

“The great irony is this whole world has gone full circle,” Bloomberg reported Eric Trump as saying at the event.
“There’s people in this room that were probably on the opposite side of us, that were canceling bank accounts for us, that were kicking us out of their big banks for no reason other than the fact that my father was wearing a hat that said, ‘Make America Great Again.’”
Commodity Futures Trading Commission chair Mike Selig, the head of an agency that is pushing to regulate the crypto industry, was also in attendance, along with Republican senators Ashley Moody and Bernie Moreno.
World Liberty announces tokenization tie-up for Trump hotel
World Liberty announced at the event that it has partnered with tokenization firm Securitize, with plans to tokenize loan revenue interests in an upcoming Trump-branded resort in the Maldives.
The company said it was part of a “broader strategy to design, structure, and distribute [World Liberty]-branded tokenized real-world asset offerings.”
Related: Warren warns crypto bailout would enrich Trump family biz: Report
The Trump Organization said in November that it would tokenize the development of the project, which is being built by real estate developer DarGlobal. The resort is set to be completed in 2030 and feature 100 luxury villas.
World Liberty said that the offering will give investors “both a fixed yield and loan revenue streams” from the resort, giving exposure to “both potential income distributions and the potential for certain profits upon any future sale.”
It added that the offering is only available to eligible accredited investors in the US and would be accessed via “select third-party partners and wallets.”
Big Questions: Is China hoarding gold so yuan becomes global reserve instead of USD?
Crypto World
Base Chain Ditches OP Stack for Unified base/base Architecture: Here’s What Changes

TLDR:
-
- Base is moving from OP Stack to a unified base/base repository, requiring node operators to migrate to the new Base client.
- The new upgrade schedule targets six hard forks per year, doubling the current rate of three annual protocol upgrades.
- Base retains its Stage 1 Decentralized Rollup status and is adding an independent signer to its Security Council.
- All Base specifications and code remain open-source, with alternative client implementations actively encouraged by the team.
- Base is moving from OP Stack to a unified base/base repository, requiring node operators to migrate to the new Base client.
Base Chain is moving away from its multi-dependency architecture toward a single, consolidated software stack. The transition consolidates all components into one repository, base/base, built on open-sourced tools. Node operators will need to migrate to the new Base client to stay compatible with future hard forks.
A Single Stack Replaces a Web of Dependencies
Base originally launched as an OP Stack chain, relying on partners like Optimism, Flashbots, and Paradigm. Over time, this created a complex web of external dependencies. Managing these relationships added coordination overhead for the engineering team.
The Base Engineering Team stated: “Base was built on the shoulders of giants — we could not have gotten so far so quickly without the world-class technology underpinning the OP Stack.”
The new unified stack consolidates everything into base/base, removing that friction entirely. This approach makes the protocol easier to understand and maintain for individual developers.
Previously, code for Base components was spread across multiple repositories owned by different teams. That structure slowed down shipping and created communication gaps. Bringing it all under one roof changes how releases are managed going forward.
Faster Hard Fork Schedule Targets Six Upgrades Per Year
One of the clearest changes from this transition is a faster upgrade cadence. Base plans to ship six hard forks per year, up from three. Each fork will be smaller and more tightly scoped to reduce risk.
The team described the goal clearly: “We’re targeting six smaller, tightly scoped hard forks per year, doubling the current schedule.”
This replaces the current model of batching many changes into large, infrequent upgrades. Smaller updates are easier to audit and easier to roll back if needed.
The roadmap already outlines several upcoming releases. Base V1 will handle client consolidation and a proof upgrade from optimistic proofs to TEE/ZK proofs.
Base V2 and V3 will introduce new transaction types, block access lists, and alignment with Ethereum’s Glamsterdam upgrade.
Security Council and Decentralization Standards Are Preserved
Base confirmed it remains a Stage 1 Decentralized Rollup through this transition. The team made clear that no tradeoffs were made on security or technical decentralization. An additional independent signer is being added to the Base Security Council to replace Optimism’s previous role.
The engineering team noted: “The protocol spec and codebase should be understandable by a single developer.” The accelerated roadmap also includes faster withdrawals through a more robust multi-proof system. Base-specific governance structures are being developed alongside enhanced neutrality standards.
Base will continue working with Optimism as a client of OP Enterprise for mission-critical support. Bug fixes will still be upstreamed, and security disclosures will be coordinated to protect the broader Superchain ecosystem. The separation is technical, not adversarial.
Open-Source Commitments Remain Central to Base’s Direction
Despite moving away from the OP Stack, Base reaffirmed its commitment to building in public. All specifications and code will remain open-source and available for forking. Alternative client implementations are actively encouraged to strengthen network resilience.
The team was direct on this point: “Base specifications and code will always be public, open for contribution, and available for others to fork.”
Base also confirmed continued contributions to ecosystem tooling like Foundry and Wagmi. The team views this work as maintaining Base’s role as a public good within the ecosystem.
Node operators currently face no immediate action. However, over the next few months, migration to the Base client will be required to stay compatible with future hard forks.
All existing RPCs, including those in the Optimism namespace, will continue to be fully supported during the transition.
.
Crypto World
Bitcoin Range-Bound Under Pressure as Analysts Eye $55,000


The longer Bitcoin remains rangebound, the more likely it is to fall further as the bear market deepens.
Bitcoin is “range-bound under pressure,” having broken below the “True Market Mean,” slipping into a “defensive range toward the Realized Price,” of around $55,000, reported Glassnode on Wednesday. The on-chain analytics provider remained bearish, noting that demand across spot and derivative markets was weak.
“Spot flows and ETF demand remain weak, accumulation is fragile, and options positioning shows panic hedging fading, but not renewed bullish conviction.”
Glassnode noted that historically, deeper bear market phases have found their lower structural boundary around the Realized Price. This is a measure of the average acquisition cost of all circulating coins, which now stands near $54,900.
This level is almost 18% lower than current prices and would put the fall from peak to 56.4%, which is much shallower than the last two bear markets.
Market in Controlled Consolidation
The analysts also noted that the Accumulation Trend Score sits near 0.43, well short of the 1.0 level that would signal serious large-entity buying.
Spot Cumulative Volume Delta (CVD), which tracks the difference between market buy orders and market sell orders over time, has turned firmly negative across major exchanges such as Binance and Coinbase, meaning sellers are in control.
Glassnode concluded that the market is “transitioning from reactive liquidation to controlled consolidation.”
“For a durable recovery to emerge, renewed spot demand, sustained accumulation, and improving liquidity conditions will be required.”
Range-Bound Under Pressure
Bitcoin has broken below the True Market Mean, slipping into a defensive range toward the Realized Price (~$54.9k). Spot and ETF demand remain weak, and panic hedging has eased.
Read the full Week On-Chain👇 https://t.co/XAp8OQr65i pic.twitter.com/iLuDT8o50v
— glassnode (@glassnode) February 18, 2026
You may also like:
Bitcoin network activity has also collapsed, according to Santiment, which reported on Wednesday that there have been large declines in new and unique addresses as Bitcoin’s utility declined in 2025.
“A justification for crypto beginning to see a true long-term relief rally will be when metrics like active addresses and network growth begin to rise.”
“BTC is still strengthening its bear trend,” observed analyst Willy Woo, who said that volatility is a key metric to detect trends. Bitcoin entered its bear market when volatility spiked upwards quickly, he said, before adding:
“Volatility then continues to climb, meaning the bear trend is strengthening. Then volatility finds a peak in the mid to late phase bear market… that’s when the bear trend starts to weaken.”
BTC Price Outlook
Bitcoin continues to weaken, dropping below $66,000 briefly in late trading on Wednesday. It came just shy of $67,000 during the Thursday morning Asian trading session, but had not reclaimed it at the time of writing.
The asset has been trading sideways for the past two weeks, and the path of least resistance appears to be downwards.
SECRET PARTNERSHIP BONUS for CryptoPotato readers: Use this link to register and unlock $1,500 in exclusive BingX Exchange rewards (limited time offer).
Crypto World
Ethereum Foundation Outlines Main Priorities For 2026

The Ethereum Foundation has announced it is targeting faster transactions, smarter wallets, better cross-chain interoperability, and quantum-resistant security as its “protocol priorities” in 2026.
In a statement published on Wednesday, the Ethereum Foundation outlined several goals, including continuing to scale the gas limit — the maximum amount of computational work a block can handle — “toward and beyond” 100 million, a major topic of discussion among the Ethereum community in 2025.

Some members of the Ethereum community anticipate that the gas limit will increase significantly this year. In November, Ethereum educator Anthony Sassano said that the goal of significantly increasing Ethereum’s gas limit to 180 million in 2026 is a baseline, not a best-case scenario.
“Post-quantum readiness” is a focus for Ethereum
The foundation highlighted the Glamsterdam network upgrade, scheduled for the first half of 2026, as a major priority. It also emphasized “post-quantum readiness” as a priority in its trillion-dollar security initiative.
On Jan. 24, Ethereum researcher Justin Drake said in an X post that the foundation had “formed a new Post-Quantum (PQ) team.”
“Today marks an inflection in the Ethereum Foundation’s long-term quantum strategy,” Drake said.
The Ethereum Foundation said it will also focus on improving user experience in 2026, with an emphasis on enhancing smart wallets through native account abstraction and enabling smoother interactions between blockchains via interoperability.
“The goal remains seamless, trust-minimized cross-L2 interactions, and we’re getting closer day by day. Continued progress on faster L1 confirmations and shorter L2 settlement times directly supports this.”
The foundation said that 2025 was one of the “most productive years,” citing two major network upgrades, Pectra and Fusaka, and the community raising the gas limit from 30 million to 60 million between the upgrades, for the first time since 2021.
Buterin’s big plans for Ethereum and AI
Ethereum Foundation’s Mario Havel said in an X post on Wednesday that, “It took us a while to push out the announcement because we were preparing the biggest curriculum so far.”
Related: Ethereum reclaims 42% outflows from Solana — DeFi Report
It comes just days after Ethereum co-founder Vitalik Buterin shared his latest vision for Ethereum’s intersection with artificial intelligence on Feb. 10. Buterin explained that he sees the two working together to improve markets, financial safety and human agency.
Buterin said his broader vision for the future of AI is to empower humans rather than replace them, though he said the short term involves much more “ordinary” ideas.
Magazine: Is China hoarding gold so yuan becomes global reserve instead of USD?
Crypto World
Aptos Foundation proposes supply cap and reduced staking rewards in deflation push


The Aptos Foundation has proposed an overhaul of its tokenmomic and governance structure, which it says will replace the “bootstrap-era subsidy model” with a more sustainable and usage-driven economic model.
Summary
- Aptos Foundation proposed a 2.1 billion APT hard cap, lower staking rewards, and higher gas fees to curb emissions.
- The plan includes permanently staking 210 million APT and a potential buyback program.
“Aptos Foundation is proposing structural reforms that replace subsidy-based emissions with performance-driven mechanisms, establishing conditions for reduced emissions, increased burns, and potential decline in circulating supply,” it said on Wednesday.
Among the key proposals are plans to set a hard cap on total supply. Under the current structure, new tokens are continuously minted to support development, grants, and staking rewards across the ecosystem. The foundation is proposing a fixed 2.1 billion token hard cap.
“There are currently 1.196 billion APT in circulation. 1 billion APT was minted at mainnet, and 196 million APT has been distributed as staking rewards since mainnet. With a hard supply cap of 2.1 billion, this leaves 904 million APT of headroom or approximately 43% of this total cap,” the foundation said.
Over time, the additional tokens would be distributed in decreasing amounts as staking rewards and eventually phase out entirely as the network approaches the ceiling, at which point validators would be funded primarily through transaction fees rather than new token issuance.
Other policy changes include plans to reduce the annual staking rewards rate from 5.19% to 2.6% and transition to a revised staking framework that rewards “longer staking commitments.”
The foundation is also proposing increasing network gas fees by 10X, which are burned with every transaction, as another mechanism to reduce net emissions and tighten circulating supply.
“Even with a 10X increase, stablecoin transfers would still be the lowest in the world at around $0.00014, making it the ideal blockchain for stablecoins, payments, and any other similar high-volume transactions,” it said.
The team has also suggested permanently staking 210 million APT tokens, or about 18% of the current circulating supply, and supporting foundation operations using the staking rewards instead of selling treasury tokens into the market.
Meanwhile, the foundation also wants to transition to performance-based grants where tokens vest only after predefined milestones are achieved and are deferred until those targets are met.
Lastly, the foundation will explore launching a token buyback program or establishing an APT reserve funded through cash on hand or future foundation revenue to help balance supply dynamics over time.
Aptos Foundation is joining a slew of others that have proposed tokenomic overhauls and governance changes in recent months.
Last week, Aave Labs proposed redirecting all product-related revenue directly to the DAO treasury. Meanwhile, in late January, the Injective community approved a proposal to further reduce the INJ token’s long-term supply by cutting issuance and reinforcing existing burn mechanisms.
In December, Uniswap burned 100 million UNI tokens as part of the UNIfication proposal, which received overwhelming support from the community.
Crypto World
Fed Minutes Signal Hawkish Tone, Markets React
Bitcoin has emerged as the biggest underperformer since the release of the FOMC minutes for the January 28 meeting, while the US dollar index and bonds rally.
The January FOMC meeting, which saw two dovish dissents, reflected a deeply divided Federal Reserve (Fed).
Sponsored
Sponsored
Fed Minutes Reveal Hawkish Divide as Bitcoin Struggles
Almost all policymakers supported maintaining the federal funds rate at 3.50–3.75%, though a couple preferred a 25-basis-point cut, citing restrictive policy and labor market risks.
Several officials indicated that further rate cuts could be warranted if inflation declines as expected. Meanwhile, others cautioned that easing too early amid elevated inflation could compromise the Fed’s 2% target.
Some advocated for “two-sided” guidance, highlighting that rates might need to rise if inflation remains above target.
Recent macroeconomic data have reinforced Fed Chair Jerome Powell’s cautiously optimistic outlook.
Sponsored
Sponsored
Growth has surprised to the upside, inflation appears to be drifting lower, and the job market shows signs of steadying.
These developments have pushed 2026 rate-cut expectations higher, though a move in March is effectively off the table following last week’s stronger-than-expected payroll report.
Market vulnerabilities were also a focal point, with multiple participants noting risks in private credit and the broader financial system.
Analysts suggest that these concerns, combined with the Fed’s hawkish undertones, have contributed to safe-haven buying in bonds and the dollar, while Bitcoin continues to face downward pressure.

Equities showed modest gains, with the Dow Jones Industrial Average up 0.24%, the S&P 500 up 0.59%, and the NASDAQ up 1.00%, reflecting cautious optimism in markets amid signals from the Fed.
“The minutes show a Fed still divided but attentive to both inflation risks and growth momentum,” said a senior market strategist. “Bitcoin’s underperformance is partly a reflection of risk-off sentiment and the dollar’s continued strength.”
Investors will now watch for any further commentary from Fed officials as markets digest these minutes, weighing the balance between hawkish vigilance and dovish optimism in shaping 2026’s monetary policy trajectory.
Crypto World
Cardano Price Flashes 35% Rally Hope Despite This Weak Metric
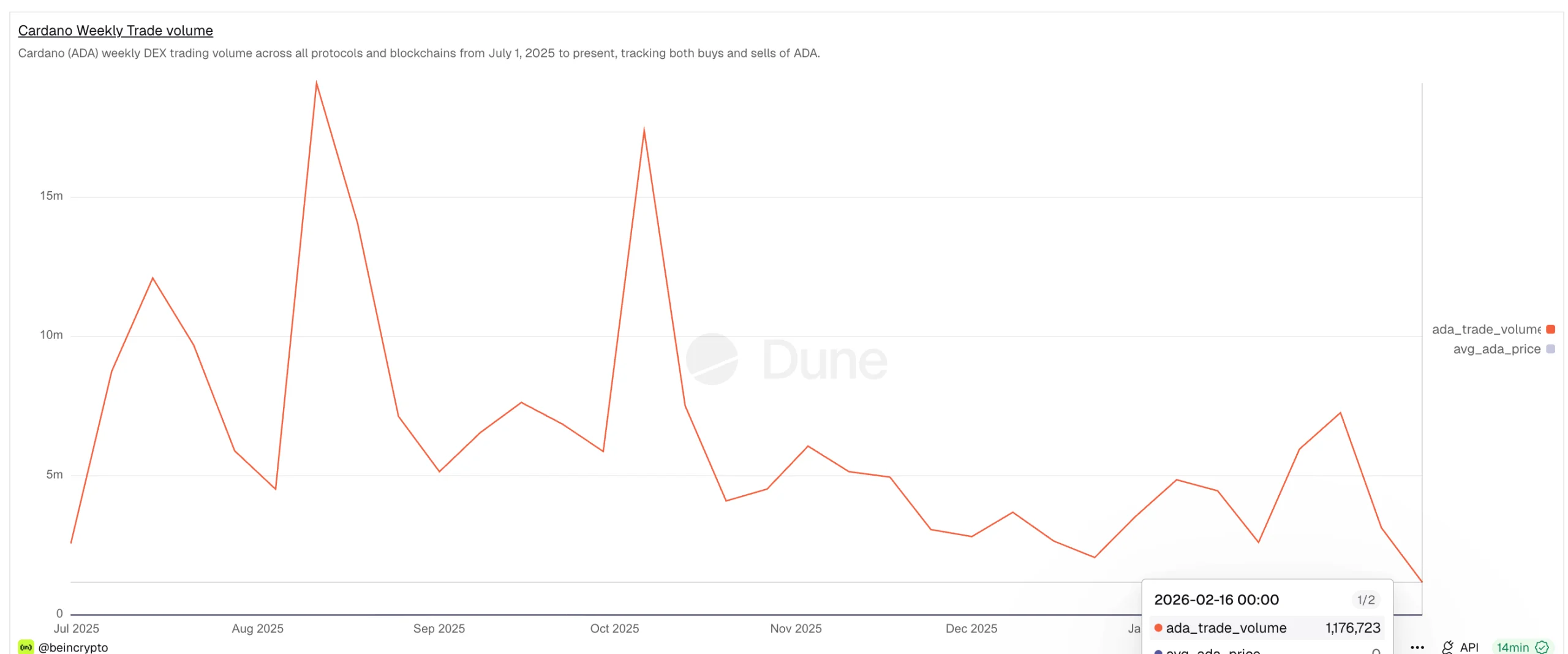
The Cardano price has declined sharply in recent months, reflecting weakening investor participation. This decline did not happen alone. Cardano’s on-chain trading activity has also collapsed during the same period. Decentralized exchange trading volume has dropped by over 94% since August, hitting a six-month low.
Yet despite this collapse in participation, technical charts now show early signs of a possible reversal. This creates a conflict between weakening network activity and improving price structure.
Sponsored
On-Chain Trading Activity Collapse Confirms Weak Trend
Cardano’s weekly decentralized exchange trading volume has dropped dramatically over the past six months. In August 2025, weekly volume peaked at 19,103,979 ADA. By February 16, 2026, this figure had fallen to just 1,176,723 ADA, highlighted exclusively by BeInCrypto’s Dune Dashboard.
This represents a 94% collapse in on-chain trading. This is also indicative of the low on-chain participation, as aggressively traded coins are often associated with sharp price moves.
Want more token insights like this? Sign up for Editor Harsh Notariya’s Daily Crypto Newsletter here.
On-chain trading volume measures real buying and selling happening directly on the blockchain. It reflects user participation and demand. When volume falls this sharply, it shows fewer investors are actively trading the asset.
Cardano’s price has mirrored this weakness. ADA has dropped roughly 68% over the same six-month period. This confirms the downtrend was supported by declining participation and demand. However, price structure now shows early signs that this trend may be changing.
Sponsored
Bullish Price Pattern Emerges, But Profit-Taking Risk Remains
Cardano is currently forming an inverse head-and-shoulders pattern on the daily chart. This is a bullish reversal pattern that appears when selling pressure weakens, and buyers begin slowly regaining control.
The left shoulder formed in January. The head formed in early February. The right shoulder has now formed near similar levels, validating the structure. However, to confirm the breakout, the daily Cardano price candle must close above $0.30.
Momentum indicator, in the form of RSI, supports this formation. The Relative Strength Index, or RSI, has formed a bullish divergence. Between December 31 and February 18, Cardano’s price made a lower low. But during the same period, RSI made a higher low. This shows selling pressure is weakening even as the price tests new lows. It confirms buyers are slowly returning.
Sponsored
However, another on-chain metric introduces risk. The percentage of Cardano supply in profit dropped sharply from 27% to just 6% during the recent decline, from late January to mid-February. It has now started rising again and currently sits near 10%.
This increase shows more investors are returning to profit. While this can support recovery, it also creates selling risk. When holders return to profit, many choose to sell and secure gains. For example, on February 15, profitable supply rose near 11%. Cardano’s price dropped from $0.29 to $0.27 soon after. This was a 7% decline in a single trading session.
This shows rising profitability can trigger selling pressure even during recovery attempts, making support and resistance levels all the more important.
Sponsored
Cardano Price Faces Critical Breakout Level at $0.30
Cardano now sits near its most important resistance level. The neckline of the inverse head and shoulders pattern is located at $0.30. This level will decide the next major move.
If Cardano breaks above $0.30 and closes above it, the bullish pattern would be confirmed. Based on the structure, this could push ADA toward $0.40 and $0.41. This would represent a potential 35% to 38% rally from the neckline.

However, failure to break this level would weaken the recovery attempt. If Cardano falls below $0.27 (led by possible profit booking), the bullish structure would begin weakening. A further drop below $0.22 would completely invalidate the pattern and confirm continued downside.
For now, Cardano sits at a critical decision point. On-chain trading confirms participation has collapsed. But technical indicators suggest a possible reversal. The next move above $0.30 or below $0.27 will determine whether Cardano begins a true recovery or resumes its longer-term decline.
-
 Video3 days ago
Video3 days agoBitcoin: We’re Entering The Most Dangerous Phase
-

 Tech4 days ago
Tech4 days agoLuxman Enters Its Second Century with the D-100 SACD Player and L-100 Integrated Amplifier
-
 Crypto World2 days ago
Crypto World2 days agoCan XRP Price Successfully Register a 33% Breakout Past $2?
-

 Sports2 days ago
Sports2 days agoGB's semi-final hopes hang by thread after loss to Switzerland
-

 Video6 days ago
Video6 days agoThe Final Warning: XRP Is Entering The Chaos Zone
-

 Tech2 days ago
Tech2 days agoThe Music Industry Enters Its Less-Is-More Era
-

 Business1 day ago
Business1 day agoInfosys Limited (INFY) Discusses Tech Transitions and the Unique Aspects of the AI Era Transcript
-

 Entertainment19 hours ago
Entertainment19 hours agoKunal Nayyar’s Secret Acts Of Kindness Sparks Online Discussion
-

 Video2 days ago
Video2 days agoFinancial Statement Analysis | Complete Chapter Revision in 10 Minutes | Class 12 Board exam 2026
-
 Crypto World5 days ago
Crypto World5 days agoBhutan’s Bitcoin sales enter third straight week with $6.7M BTC offload
-

 Tech23 hours ago
Tech23 hours agoRetro Rover: LT6502 Laptop Packs 8-Bit Power On The Go
-

 Sports4 hours ago
Sports4 hours agoClearing the boundary, crossing into history: J&K end 67-year wait, enter maiden Ranji Trophy final | Cricket News
-

 Entertainment10 hours ago
Entertainment10 hours agoDolores Catania Blasts Rob Rausch For Turning On ‘Housewives’ On ‘Traitors’
-

 NewsBeat4 days ago
NewsBeat4 days agoThe strange Cambridgeshire cemetery that forbade church rectors from entering
-

 Business7 days ago
Business7 days agoBarbeques Galore Enters Voluntary Administration
-

 Business1 day ago
Business1 day agoTesla avoids California suspension after ending ‘autopilot’ marketing
-

 Crypto World6 days ago
Crypto World6 days agoKalshi enters $9B sports insurance market with new brokerage deal
-

 Crypto World13 hours ago
Crypto World13 hours agoWLFI Crypto Surges Toward $0.12 as Whale Buys $2.75M Before Trump-Linked Forum
-
 Crypto World7 days ago
Crypto World7 days agoEthereum Price Struggles Below $2,000 Despite Entering Buy Zone
-

 NewsBeat4 days ago
NewsBeat4 days agoMan dies after entering floodwater during police pursuit