CryptoCurrency
Your Crypto Could Vanish: SlowMist Reveals Critical Flaw in AI Coding Tools

Blockchain security firm SlowMist has issued an urgent warning about a critical vulnerability in AI-powered coding tools that could compromise developer systems instantly through simple project operations.
The flaw affects mainstream integrated development environments (IDEs) and poses particular risks to crypto developers whose systems often store valuable digital assets and sensitive credentials.
Users of AI coding assistants face immediate danger when opening untrusted project directories, with several developers already compromised according to SlowMist’s threat intelligence team.
The vulnerability triggers automatically when developers perform routine actions, like “Open Folder,” on malicious projects, executing system commands on both Windows and macOS without requiring additional user interaction.
AI Coding Tools Become Attack Vector for Crypto Theft
Cursor users face particularly severe exposure to the vulnerability, which cybersecurity firm HiddenLayer first documented in September in its research into the “CopyPasta License Attack.”
The exploit manipulates how AI assistants interpret common developer files, including LICENSE.txt and README.md, by embedding harmful instructions in markdown comments that remain hidden from rendered views but guide AI tools to propagate malware across entire codebases.
Attackers can stage backdoors, exfiltrate sensitive data, or manipulate critical systems while malicious code remains buried deep inside files, according to HiddenLayer’s analysis.
The firm demonstrated the attack using Cursor alongside other vulnerable tools, including Windsurf, Kiro, and Aider, showing how minimal user interaction enables organization-wide code compromise.
The disclosure follows Coinbase CEO Brian Armstrong’s aggressive push to have AI-generated code account for 40% of the company’s output, with plans to reach 50% by October, despite firing engineers who failed to adopt AI tools within one week of his mandate.
Security experts and developers criticized the policy as a “giant red flag for any security-sensitive business,” according to Dango founder Larry Lyu, while Carnegie Mellon professor Jonathan Aldrich called it “insane” and said he would not trust Coinbase with his funds.
Nation-State Hackers Weaponize Blockchain for Malware Distribution
Developers continue to face persistent organized attacks. North Korean threat actors have escalated attacks by embedding malware directly into blockchain smart contracts, marking the first documented nation-state use of “EtherHiding” techniques.
Famous Chollima operatives deployed malicious JavaScript modules that combined the BeaverTail and OtterCookie malware through fake job interviews targeting crypto developers, distributing the code via an NPM package disguised as a chess application.
Google documented a North Korean group, UNC5342, embedding JADESNOW malware and INVISIBLEFERRET backdoors within smart contracts on the BNB Smart Chain and Ethereum since February, creating a decentralized command-and-control infrastructure that law enforcement cannot easily dismantle.
The technique stores payloads on public blockchains through read-only function calls that avoid transaction fees and leave no visible history.
Still targeting developers, back in April, the attackers established legitimate US companies using stolen identities, with Silent Push researchers discovering Blocknovas registered to a vacant South Carolina lot and Softglide traced to a Buffalo tax office.
It was discovered that both were serving as fronts for the “Contagious Interview” campaign that distributes malware through technical assessments.
These security threats keep growing even as crypto-related losses from hacks and cybersecurity exploits fell 60% in December to $76 million, according to blockchain security firm PeckShield, down from November’s $194.2 million.
AI Systems Discover Zero-Day Exploits Worth Millions
The paradox of the ethical and unethical use of AI is becoming increasingly concerning.
Last month, Anthropic research showed that AI agents successfully exploited 50% of smart contracts in its SCONE-bench testing framework, generating simulated attacks worth $550.1 million across 405 historically compromised contracts.
Claude Opus 4.5 and GPT-5 discovered working exploits on 19 contracts deployed after their knowledge cutoff dates, representing $4.6 million in value, while both models found two zero-day vulnerabilities in live Binance Smart Chain contracts worth $3,694 at an API cost of $3,476.
The study found potential exploit revenue roughly doubled every 1.3 months while token costs for generating working attacks fell sharply, meaning attackers obtain more successful exploits for identical compute budgets as models improve.
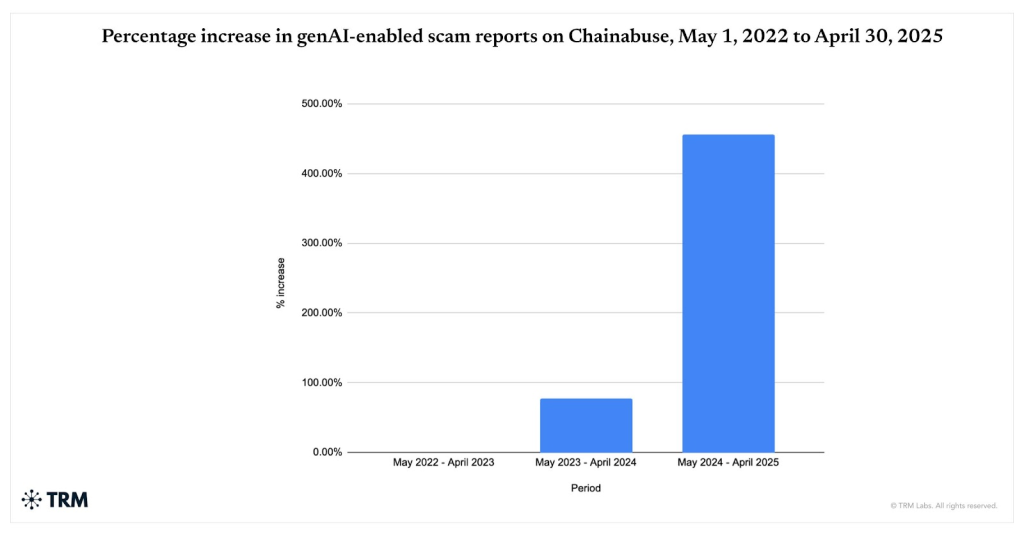
Meanwhile, AI-powered crypto scams increased 456% between May 2024 and April 2025, according to Chainabuse data, with 60% of deposits into scam wallets now stemming from AI-driven schemes using deepfakes, voice cloning, and automated bots that create fake identities and realistic conversations at scale.
The post Your Crypto Could Vanish: SlowMist Reveals Critical Flaw in AI Coding Tools appeared first on Cryptonews.

 SlowMist TI Alert
SlowMist TI Alert Cursor users: especially at…
Cursor users: especially at…  Coinbase CEO
Coinbase CEO  Crypto-related losses from hacks and cybersecurity exploits fell sharply in December, dropping 60% month-on-month to about $76 million.
Crypto-related losses from hacks and cybersecurity exploits fell sharply in December, dropping 60% month-on-month to about $76 million.