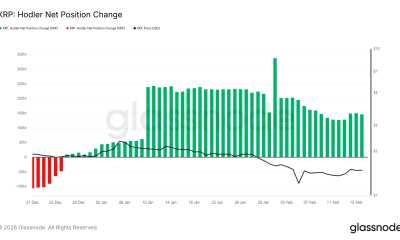
This week, things were a little quieter as we await the reveals of Samsung Unpacked next week, but that’s not to say it was boring.
YouTube went down, Apple teased its next product event, and Discord rivals crashed under the weight of new users fleeing to their platforms.
7. The Discord exodus started

Discord has inadvertently spoiled its reputation over the last week, with an announcement that it will be introducing its strict age verification plans to its users globally, after the UK’s updated Online Safety Act. It unsurprisingly sparked outrage among Discord users, who fled to multiple alternative social platforms, so much so that it gave one in particular, Stoat, server capacity issues.
It comes after a plethora of users took to unsubscribing from the platform’s Nitro service, with many looking to force Discord to rethink its strategy. Unfortunately, Discord is yet to make any adjustments to its verification plans set for March, and has only issued an update to its initial press release, providing extra ‘clarification’ for those plans.
6. We tested the weirdest e-bike so far

AI really is finding its way into everything, as this week we tried Acer’s ebii 20 — an e-bike with AI features aimed to enhance the rider’s experience.
There is something to be said for the security protection and AI pedal assistance, but the hub motor lacks the power most would expect from an e-bike in this price bracket.
It also has poor weight distribution, and made some annoying ticking and white noise sounds while we were testing it — likely because we didn’t outfit the bike with a SIM card — which led to frustrations that meant we could only award it three-and-a-half stars in our review.
5. Movie studios fought back against AI clones

Netflix and Paramount might be battling over which of them will buy Warner Bros., but for now, the trio, and some other Hollywood studios like Disney, are allies in pushing back on Seedance 2.0 — a new AI video generator from ByteDance (the TikTok owner).
That is because they all claim the platform is using their characters and IP without permission.
Several Seedance videos have gone viral recently, including one starring Brad Pitt and Tom Cruise in a fight scene, with dialogue that sees Pitt accuse Cruise of killing Jeffrey Epstein — with the Screen Actors Guild of America (SAG-AFTRA) calling the video “unacceptable”.
The Chinese company has since said it will take steps “to prevent the unauthorized use of intellectual property and likeness by users.”
4. We dissected the new Game of Thrones trailer

Thankfully, this week we didn’t need AI to get excited about one major entertainment property, as the trailer for House of the Dragon season 3 dropped.
With last season’s finale suggesting that the Targaryen Civil War will finally take center stage this season, its first teaser, which you can watch above, is a thoroughly explosive one.
Unfortunately, the one thing we’re still missing is an official release date. It’s coming sometime in June, but precisely when is still a mystery for now.
3. Ring defended its leaked plan to “zero out crime”

Privacy has been a huge theme this week – and Discord (see above) wasn’t the only company that shot itself in the foot. Ring also had to defend itself from accusations that it’s planning to create an opt-out system that borders on mass surveillance.
A leaked email from Ring founder Jamie Siminoff poured gasoline on a controversy that was sparked by the company’s Super Bowl ad for its ‘Search Party’ feature. That feature is designed to help lost dogs, but the email said it could lead to a “future where we are able to zero out crime in neighborhoods”.
That understandably didn’t go down too well with privacy advocates – but Ring told us that it’s standing firm, despite the backlash.
2. YouTube went down in a very rare outage

We’re getting pretty used to outages on X, which went down twice this week – but seeing YouTube go offline is a more panic-inducing rarity. Well, that unfortunate incident happened on Tuesday night when YouTube gave millions of people a taste of what life was like before 2006.
The 90-minute outage hit every part of YouTube – from the website and app to YouTube Music and TV – and was caused by an innocent “issue with our recommendations system”, according to Google. The experience made many realize how dependent they’ve become on the video-sharing site, which is so culturally significant it’s now an exhibit at London’s V&A museum.
1. Apple announced a big March event

We might currently be gearing up for Samsung’s upcoming Unpacked next week, but not wanting to be left out of the conversation, Apple has teased a showcase for March 4 — and it could be a doozy.
As ever, the company is keeping tight-lipped about what product launches we might see at the event, with nothing specific mentioned in the press invite itself; however, there are suggestions from leaks and speculation that it’ll have a wide range of products to announce.
This could include new MacBook Pros, the iPhone 17e, a new iPad Air, and possibly a new Mac Studio. We’ll have to wait and see what gets announced, but if you’re an Apple fan looking to upgrade your tech, you might want to wait a week or so to see what Apple has up its sleeves.