Once upon a time, the cathode ray tube was pretty much the only type of display you’d find in a consumer television. As the analog broadcast world shifted to digital, we saw the rise of plasma displays and LCDs, which offered greater resolution and much slimmer packaging. Then there was the so-called LED TV, confusingly named—for it was merely an LCD display with an LED backlight. The LEDs were merely lamps, with the liquid crystal doing all the work of displaying an image.
Today, however, we are seeing the rise of true LED displays. Sadly, decades of confusing marketing messages have polluted the terminology, making it a confusing space for the modern television enthusiast. Today, we’ll explore how these displays work and disambiguate what they’re being called in the marketplace.
The Rise Of Emissive Displays
When it comes to our computer monitors and televisions, most of us have got used to the concept of backlit LCD displays. These use a bright white backlight to actually emit light, which is then filtered by the liquid crystal array into all the different colored pixels that make up the image. It’s an effective way to build a display, with a serious limitation on contrast ratio because the LCD is only so good at blocking out light coming from behind. Over time, these displays have become more sophisticated, with manufacturers ditching cold-cathode tube backlights for LEDs, before then innovating with technologies that would vary the brightness of parts of the LED backlight to improve contrast somewhat. Some companies even started using arrays of colored LEDs in their backlights for further control, with the technology often referred to as “RGB mini LED” or “micro RGB.” This still involves an LCD panel in front of the backlight, limiting contrast ratios and response times.
The holy grail, though, would be to ditch the liquid crystal entirely, and just have a display fully made of individually addressable LEDs making up the red, green, and blue subpixels. That is finally coming to pass, with manufacturers launching new television lines under the “Micro LED” name. These are true “emissive” displays, where the individual red, blue, and green subpixels are themselves emitting light, not just filtering it from a backlight source behind them.
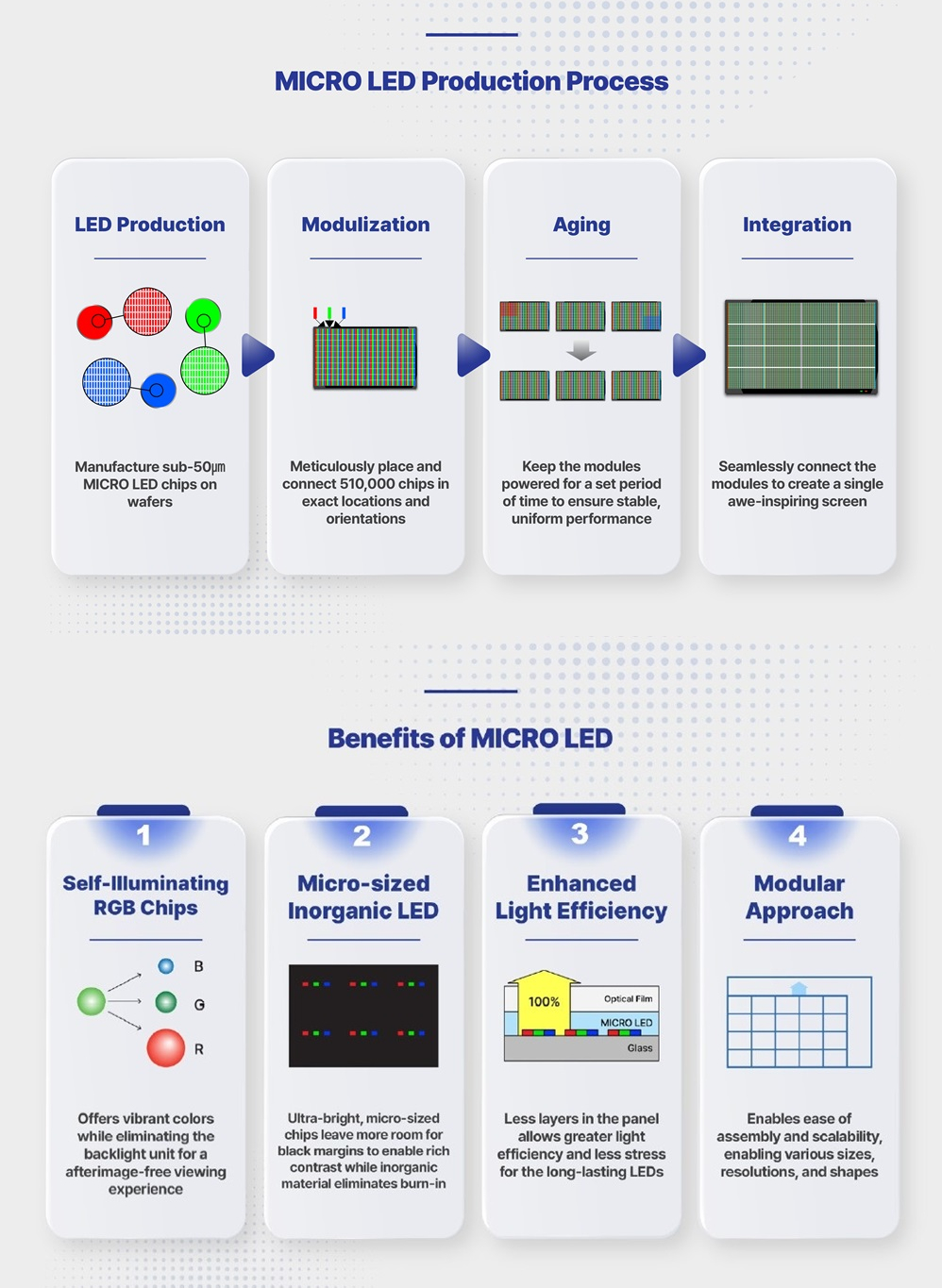
These displays promise greater contrast than backlit LCDs, because individual pixels can be turned completely off to create blacker blacks. Response times are also fast because LEDs switch on and off much more quickly than liquid crystals can react. They’re also relatively power efficient, as there’s no need to supply electrons to pixels that are off. Contrast this to LCDs, which are always spending power on turning some pixels black in front of a glowing backlight which is also drawing power. Viewing angles of emissive displays are also top-notch. Inorganic LEDs also have long lifetimes, which makes them far more desirable than OLED displays (discussed further below). Their high brightness also makes them ideal for us in bright conditions, particularly where sunlight is concerned.
Given the many boons of this technology, you might question why it’s taken true LED displays this long to hit the market. The ultimate answer comes down to cost and manufacturability. If you’ve ever built your own LED array, you’ve probably noted the engineering challenges in reducing pixel size and increasing resolution. When it comes to producing a 4K display, you’re talking about laying down 8,294,400 individual RGB LEDs, all of which need to work flawlessly and be small enough to not show up as individually visible pixels from typical viewing ranges. Other technologies like LCDs and OLEDs have the benefit that they can be easily produced with lithographic techniques in great sizes, but the technology to produce pure LED displays on this scale is only just coming into fruition.
You can purchase an all-LED TV today, if you so desire. Just note that you’ll pay through the nose for it. Few models are on the market, but Best Buy will sell you a 114″ Micro LED set from Samsung for the charming price of $149,999.99. If that’s a bit big for your house, condo, or apartment, you might consider the 89″ model for a more acceptable $109,999.99. Meanwhile, LG has demonstrated a 136″ model of a micro LED TV, but there have been no concrete plans to bring it to market. Expect it to land somewhere firmly in the six-figure range, too.
If you’re not feeling so flush, you can get a lesser “Micro RGB” TV if you like, which combines a fancy RGB matrix backlight with LCD technology as discussed above. Even then, a Samsung R95 television with Micro RGB technology will set you back $29,999.99 at Best Buy, or you can purchase it on a payment plan for $1,250 a month. In fact, with the launch of these comparatively affordable TVs, Samsung has gone somewhat quiet on its Micro LED line since initially crowing about it in 2024. Still, whichever way you go, these fancy TVs don’t come cheap.
But What About OLED?

It’s true that emissive LED displays have existed in the market for some time, but not using traditional light-emitting diodes. These are the popular “OLED” displays, with the acronym standing for “organic light emitting diode.” Unlike standard LEDs, which use inorganic semiconductor crystals to emit light, OLEDs instead use special organic compounds in a substrate between electrodes, which emit light when electricity is applied. They can readily be fabricated in large arrays to create displays, which are used in everything from tiny smartwatches to full-sized televisions.
You might question why the advent of “proper” LED displays is noteworthy given that OLED technology has been around for some time. The problem is that OLEDs are somewhat limited in their performance versus traditional inorganic LEDs. The main area in which they suffer is longevity, as the organic compounds are susceptible to degradation over time. The brightness of individual pixels in an OLED display tends to drop off very quickly compared to inorganic LEDs. A display can diminish to half of its original brightness in just a few years of moderate to heavy use. In particular, blue OLED subpixels tend to degrade faster than red or green subpixels, forcing manufacturers to take measures to account for this over the lifetime of a display. Peak brightness is also somewhat limited, which can make OLED displays less attractive for use in bright rooms with lots of natural light. Dark spots and burn in are also possible, at rates greater than those seen in contemporary LCD displays.
The limitations of OLED displays have not stopped them gaining a strong position in the TV marketplace. However, the technology will be unlikely to beat true LED displays in terms of outright image quality, brightness, and performance. Cost will still be a factor, and OLEDs (and LCDs) will still be relevant for a long time to come. However, for now at least, the pure LED display promises to become the prime choice for those looking for a premium viewing experience at any cost.
Featured image: “Micro LED” displays. Credit: Samsung