Tech
Seattle startup Griptape acquired by creative software firm Foundry


Griptape, a Seattle-based startup founded in 2023 by former Amazon Web Services executives, has been acquired by Foundry, a London-based company whose software is used in visual effects and animation across Hollywood. Terms of the deal were not disclosed.
Griptape built a platform that helps companies securely manage and coordinate multiple AI models and agents. Foundry said the deal will boost its push into AI-powered production tools.
“By bringing Griptape into Foundry, we can provide the tools our customers want to realize their creative vision more efficiently, while retaining control,” Foundry CEO Jody Madden said in a press release.
Griptape initially pitched itself as an enterprise-grade alternative to frameworks such as LangChain. The startup, which works with several production studios, raised a $12.5 million round in 2023. Investors include Seattle-area firm Fuse, as well as Acequia Capital, Crosslink Capital, Range Ventures, and Peterson Ventures. The company has 22 employees, according to LinkedIn.
Roche spent more than eight years at AWS. He previously founded 2lemetry, an IoT startup that Amazon acquired in 2015.
Vasily Vasinov, the company’s co-founder and former CTO, left Griptape in 2025.
Tech
Why District Leaders Are Rethinking Education Research and Policy
Today, district leaders are being asked to make irreversible budget decisions with fewer dollars and less margin for error than ever before. Yet many districts are making those decisions with limited evidence of what actually works in their classrooms — not because leaders lack interest in data, but because few systems are designed to support real-time learning at the district level.
For school and district leaders, quality data is key. Without strong research, data and connections, district leaders can find themselves working in silos, testing similar ideas in parallel without a shared way to learn what works, what does not and why.
“Right now, education research and development (R&D) isn’t about experimentation; it’s about making smarter bets with limited resources,” shared Jillian Doggett, director of the League of Innovative Schools at Digital Promise.
“R&D has to be embedded in a district’s DNA so that we are not making decisions based on assumptions of what we think works, or on what worked five or 10 years ago,” said Doggett.
That shift requires moving past a traditional approach in which programs are adopted districtwide before leaders have meaningful local evidence of fit or impact.
Dr. Robert Hill, superintendent and chief executive officer of the Springfield City School District in Ohio, argues that meeting students’ needs requires stepping beyond familiar models. To him, research and development is a way to test new approaches, learn quickly and build evidence before scaling.
“Through R&D, we can think outside the box, build evidence through continuous improvement and then advance policy, with funding attached, that actually supports kids,” Hill said.
How Districts Are Prioritizing Research and Development
Hill’s belief in the connection between R&D and student outcomes led him to join a national advisory group of district leaders focused on making education research more responsive to real-time needs.
Prioritizing research and development has already led to measurable progress for Hill’s district. As part of a chronic absenteeism cohort, Hill and his team worked with peer districts to test strategies, analyze real-time attendance data and refine approaches based on what was actually driving shifts in student engagement. Rather than relying on a single program or past assumptions, the district used an inclusive innovation model to identify which interventions were effective.
“Research and development has helped us better engage our students,” Hill shared. “By aligning student interests to career pathways and connecting that with labor market data, we are actually seeing forward progress on our academic outcomes.”
For Dr. Audra Pittman, superintendent of Calistoga Joint Unified School District in rural California, engaging in education research and development helps ensure her district operates through an equity lens. Her approach to innovation is grounded in the belief that if current practices are not working for all students, districts have an obligation to keep trying new approaches.
Through a structured research partnership, Pittman’s district is examining how families and staff can partner more effectively through a cohesive, district-wide engagement and support approach centered on a co-design framework. This work asks not only whether something works, but also for whom, under what conditions and why.
The partnership allows Pittman’s team to pilot ideas thoughtfully, balancing innovation with the realities of limited time and capacity.

Why Collaboration Is Essential to Scaling What Works
Alongside education research and development, Pittman attributes strong connections with peers across the country to turning local insights into broader change.
“There’s a lot of good work that’s occurring across our nation,” said Pittman. Through participation in a national learning network, leaders like Hill and Pittman test, share and refine practices through issue-focused cohorts, innovative partnerships and regular in-person touchpoints.
As a busy superintendent, Pittman knows how difficult it can be to identify new methods she can trust. Engaging with peers who are testing emerging approaches and sharing evidence of impact has supported more efficient, informed decision-making.
Doggett has seen districts benefit from this hands-on approach to research and development, including access to research partnerships, shared tools and opportunities to learn across systems.
“That connective tissue allows district-led R&D to move quickly, learn in real time and extend beyond individual districts.”
From Policy to Action
The collaborative efforts of district leaders matter not only for research and development but also for policy.
“It’s necessary to have conversations with [policymakers] to express the challenges we are facing, the flexibility that’s necessary to advance an R&D model, and the funding that’s associated with that,” Hill shared.
Traditional funding structures often require districts to commit to specific programs upfront, leaving little room for the iterative testing that defines effective research and development. As a result, districts are often forced to choose certainty over learning — even when that certainty is more assumed than proven.
Late last year, Hill, Pittman and other district leaders convened in Washington, D.C., to make the case for a reimagined approach to funding that better supports effective education R&D.
During those meetings, leaders shared how collaborative research and development efforts have supported improvements in teaching and learning and discussed ways to scale effective practices. They called for sustained investment, greater flexibility to reduce barriers to innovation and more transparent sharing of results to accelerate learning and advance equity nationwide.
“When you’re surrounded by districts from across the nation, you are reminded that education … is truly a bipartisan issue,” Pittman reflected. “We are somewhat divided now, and this is an opportunity to bring us back together.”
Are you interested in tapping into a national learning community through the League of Innovative Schools? Sign up to be the first to hear when the League’s next application cycle is live.
Tech
Telegram channels expose rapid weaponization of SmarterMail flaws


Flare researchers monitoring underground Telegram channels and cybercrime forums have observed threat actors rapidly sharing proof-of-concept exploits, offensive tools, and stolen administrator credentials related to recently disclosed SmarterMail vulnerabilities, providing insight into how quickly attackers weaponize new security flaws.
The activity occurred within days of the vulnerabilities being disclosed, with threat actors sharing and selling exploit code and compromised access tied to CVE-2026-24423 and CVE-2026-23760, critical flaws that enable remote code execution and authentication bypass on exposed email servers.
These vulnerabilities have since been confirmed in real-world attacks, including ransomware campaigns, highlighting how attackers increasingly target email infrastructure as an initial access point into corporate networks, allowing them to move laterally and establish persistent footholds.
CVE-2026-24423 and CVE-2026-23760: Critical RCE and Auth Bypass Flaws
Multiple recently disclosed SmarterMail vulnerabilities created a perfect storm that made the platform highly attractive to attackers. Among them, CVE-2026-24423 stands out as a critical unauthenticated remote code execution flaw affecting versions prior to Build 9511.
With a CVSS score of 9.3 and no user interaction required, the flaw is particularly suited for automation, large-scale scanning, and mass exploitation campaigns.
In parallel, additional vulnerabilities CVE-2026-23760 (CVSS 9.3) include authentication bypass and password reset logic flaws. It allows attackers to reset administrator credentials or gain privileged access to the platform. Research also shows that attackers were quickly reverse-engineering patches to identify and weaponize these weaknesses within days of release.
When combined, these issues enabled full server takeover scenarios, where attackers could move from application-level access to operating system control and potentially domain-level compromise in connected environments.
From an attacker’s perspective, this combination is ideal: SmarterMail is a network-exposed service, often holds a high trust position inside enterprise environments, and in many cases is monitored less aggressively than endpoint systems protected by EDR.
Once proof-of-concept exploit code becomes available, exploitation can be rapidly operationalized – meaning the timeline from vulnerability disclosure to ransomware deployment can shrink to days.
SmarterTools Breached by Own Product Flaw, Ransomware Groups Follow
Recent incidents demonstrate exactly how this pipeline plays out.
According to a SmarterTools report, SmarterTools was breached in January 2026 after attackers exploited an unpatched SmarterMail server running on an internal VM that was exposed inside their network.
The compromised environment included office and lab networks and a data-center segment connected through Active Directory, where attackers moved laterally and impacted around a dozen Windows servers.
The company shut down the affected infrastructure, restored systems from backup, rotated credentials, and removed some Windows/AD dependencies. Having said that, it was reported that core customer services and data were unaffected. Attackers gained an internal network foothold and attempted typical ransomware-style post-exploitation actions; it wasn’t successful, thanks to network segmentation.
In another investigation published by Bleeping Computer, ransomware operators gained initial access through SmarterMail vulnerabilities and waited before triggering encryption payloads, a classic affiliate behavior pattern.
This pattern is important:
- Initial access via email server vulnerability
- Credential harvesting or token extraction
- Lateral movement via Active Directory
- Persistence via scheduled tasks or DFIR tool abuse
- Ransomware deployment after staging period
Some campaigns have been linked to the Warlock ransomware group, with overlaps observed with nation-state-aligned activity clusters.
Flare monitors underground forums and Telegram channels where threat actors share PoCs, exploits, and compromised credentials within hours of disclosure.
Get early warning when your infrastructure is discussed or targeted by ransomware operators.
Email Servers: Identity Infrastructure Attackers Target First
Email servers sit at a unique intersection of trust and visibility.
They often provide:
- Domain authentication tokens
- Password reset capabilities
- External communication channels
- Access to internal contact graphs
- Integration with identity and directory services
Attackers understand that email ecosystems rely on multi-component authentication chains where a single weak link can break overall trust. Compromise the email infrastructure and you effectively compromise identity.
1,200+ Vulnerable Servers Identified on Shodan
We found ~34,000 servers on Shodan with indications of running SmarterMail. Out of the 34,000, there were 17,754 unique servers.
A further inspection of these servers shows that 1,185 are vulnerable to authentication bypass or RCE flaws. Other publications talk about ~6,000 vulnerable servers.
A geo-location analysis of these 1,185 servers shows US dominance:
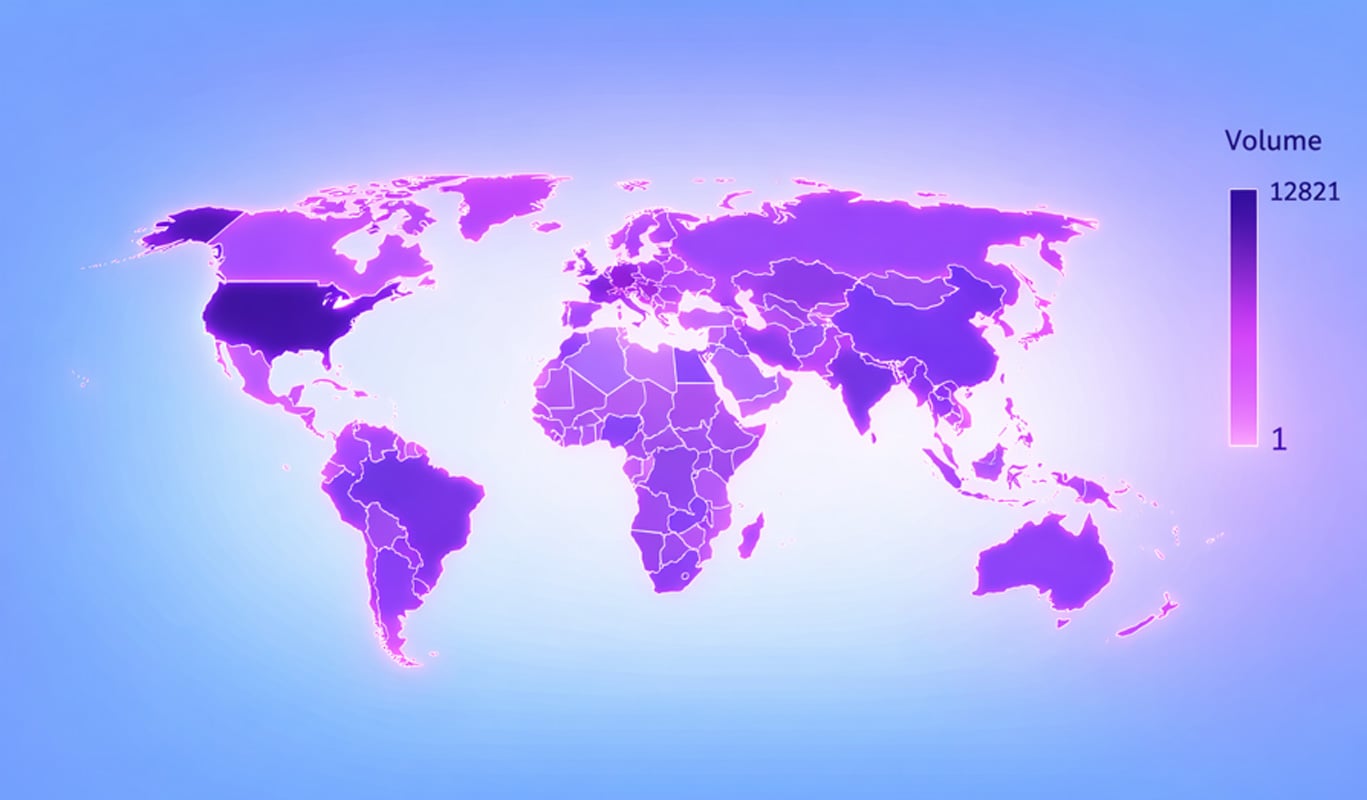
A further analysis of the ISPs and Organizations shows a very diverse distribution of open SmarterMail servers, many self-hosted admin panels, shared hosting, VPS providers, and general-purpose cloud networks, typical of deployment by individuals rather than organizations.
This may indicate that after the strong security hype over the past weeks, organizations were quick to react and block this attack surface.
Underground Forums Share Exploits Within Days of Disclosure
The underground ecosystems are fast to react to such publications. The CVEs were published around the beginning of January, and on the same day, there were mentions and references to these vulnerabilities. To date, we’ve seen dozens of publications and references to these vulnerabilities.
This is normal underground behavior when it comes to critical vulnerabilities.
We have also seen some more malicious references. A few days after the first publication, there were references to Proof of Concept or exploit of the vulnerabilities. For instance, an Arabic-speaking Telegram channel shows PoC.
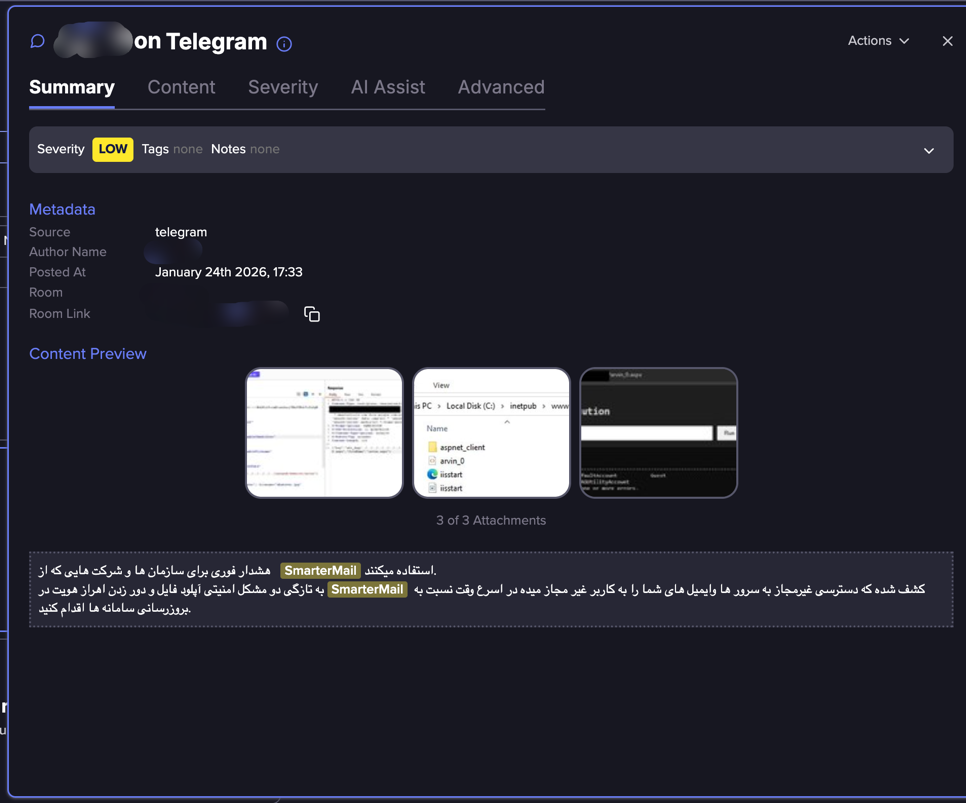
You can also see how the threat actor is showing proof of concept:
And another threat actor is showing a proof of concept to this vulnerability:
In a Spanish-speaking Telegram group, we saw references to an Offensive Security Tool:
On another Telegram group, we saw a data dump of admin credentials highlighted as it comes from a compromised SmarterMail server:
When accessing one of the links, you can indeed see a long list of admin credentials and the domains (or login) to which they belong.
CISA Confirms Active Exploitation in Ransomware Campaigns
These vulnerabilities were published in the beginning of 2026, CISA added CVE-2026-24423 to the Known Exploited Vulnerabilities catalog in the beginning of February 2026, after confirming active ransomware exploitation.
This confirms that attackers are quick to exploit newly discovered critical RCE- related vulnerabilities:
- Vulnerability disclosure
- PoC written and released
- Mass scanning operation
- Weaponization: Data exfiltration, Ransomware etc.
Timeline shrinking from months/weeks to days.
How to Protect Email Infrastructure From Ransomware Access
Many organizations still treat email servers as “ONLY application infrastructure”. Well, they are not!
They are identity infrastructures that enable many follow-up attack vectors, as well as containing secrets and business logic. Defensive priorities should include:
- Patch Urgency: Critical email server vulnerabilities should be treated like domain controller vulnerabilities.
- Identity Telemetry: Organizations should monitor these environments for:
- Admin password resets
- API calls to external hosts
- Unexpected outbound HTTP from mail servers
- Network Segmentation: Email infrastructure should never have unrestricted access to internal networks.
- Threat Hunting Practice:
- API abuse patterns
- Scheduled task persistence
- Unexpected tooling like DFIR frameworks or remote admin tools
Email Servers Are Identity Infrastructure—Secure Them Accordingly
The SmarterMail cases show once again how modern cybercrime operations are quick to add newly discovered initial access to their ongoing operation.
It also re-emphasizes the critical role email servers take in the modern organization:
- Identity brokers
- Trust anchors
- Business logic
- Invaluable reconnaissance data for follow-up cybercrime
Organizations that continue treating them as just “messaging systems” will remain vulnerable to this new generation of intrusion pipelines.
Learn more by signing up for our free trial.
Sponsored and written by Flare.
Tech
Andrew Yang Warns AI Will Displace Millions of White-Collar Workers Within 18 Months

Andrew Yang, the former presidential candidate and longtime Universal Basic Income advocate, published a blog post this week warning that AI is about to displace millions of white-collar workers in the U.S. over the next 12 to 18 months, a wave he has taken to calling “the Fuckening.”
Yang cited a conversation with the CEO of a publicly traded tech company who said the firm is cutting 15% of its workforce now and plans another 20% cut in two years, followed by yet another 20% two years after that. The U.S. currently has about 70 million white-collar workers, and Yang expects that number to fall by 20 to 50% over the next several years.
Underemployment among recent college graduates has already hit 52%, and only 30% of graduating seniors have landed a job in their field. Yang’s proposed remedy remains the same one he ran on in 2020: Universal Basic Income.
Tech
Google Pixel 10A vs. Pixel 10, 10 Pro, 10 Pro XL: How the Cheaper Pixel Matches Up
The Pixel 10A is now here, bringing a lower-cost option to Google’s Pixel 10 lineup. Starting at just $500, the Pixel 10A is more affordable than the $800 Pixel 10, and it’s significantly cheaper than the $1,000 Pixel 10 Pro and the $1,200 10 Pro XL.
Watch this: Google’s $499 Pixel 10A Launches with AirDrop Support and Faster Charging
Yet, despite a number of tradeoffs to hit its lower price, the 10A is not too shabby. These trade-offs include using the Tensor G4 processor instead of the newer Tensor G5, and the fact that PixelSnap magnetic accessories won’t attach directly to the phone. Still, if you can live without those upgrades, you’re getting a full-featured phone at a relatively low price.
Here’s how the Pixel 10A compares with the rest of Google’s Pixel 10 lineup.
Display
When it comes to display quality, the Pixel 10A compares very well to the rest of the Pixel 10 lineup. It has almost the same exact specs as the Pixel 10, with a 6.3-inch pOLED (the Pixel 10 has a 6.3-inch OLED instead), 2,424 x 1,080 pixel resolution and a 60 to 120 Hertz variable refresh rate.
Of course, the 10 Pro and 10 Pro XL are more premium. The 10 Pro has a 6.3-inch LTPO OLED, 2,856 x 1,280 pixel resolution and a 1 to 120 Hertz variable refresh rate, while the 10 Pro XL has a 6.8-inch LTPO OLED, 2,992 x 1,344 pixel resolution and the same refresh rate.
The Pixel 10A has two rear cameras: a 48-megapixel wide-angle camera and a 13-megapixel ultrawide camera.
Cameras
While most of the Pixel 10 series has at least three rear cameras, the 10A has just two. The 10A has a 48-megapixel wide and a 13-megapixel ultrawide camera, while the 10 has a 48-megapixel wide, a 13-megapixel ultrawide and a 10.8-megapixel 5x telephoto. Both the 10 Pro and the 10 Pro XL have a 50-megapixel wide, a 48-megapixel ultrawide and a 48-megapixel 5x telephoto. Both the 10A and the 10 have 4K video capture, while the 10 Pro and 10 Pro XL have 8K video capture.
The 10A does have a fairly decent front-facing camera with a 13-megapixel selfie cam, while the 10 only has a 10.5-megapixel front-facing camera. The 10 Pro and 10 Pro XL have 42-megapixel front-facing cameras.
Like the rest of the Pixel 10 line, the Pixel 10A can use Quick Share to AirDrop photos and files to an iPhone.
Battery and Performance
Surprisingly, the Pixel 10A actually has a bigger battery than some of its more expensive brethren. The 10A has a 5,100-mAh battery, which is more than the Pixel 10’s 4,970-mAh battery as well as the 10 Pro’s 4,870-mAh battery. The 10 Pro XL, however, does have a slightly larger 5,200-mAh battery, befitting its more premium features.
The Pixel 10A has 30W wired fast charging when using a 45W charging adapter, which matches the 30W wired fast charging on the Pixel 10 and the 10 Pro. As for wireless charging, the 10A supports up to 10W (Qi-certified), which isn’t quite as good as the Qi2 15W speed on the Pixel 10 and the 10 Pro, and the Qi2.2 25W speed on the Pixel 10 Pro XL.
Processor-wise, the Pixel 10A has the same Google Tensor G4 as its predecessor, while the pricier 10, 10 Pro and 10 Pro XL all have the upgraded Google Tensor G5. The Pixel 10A also only has 8GB of RAM, which is considered the bare minimum these days. By contrast, the 10 has 12GB of RAM while the 10 Pro and 10 Pro XL both have 16GB of RAM.
Check out the chart to see more ways the Pixel 10A compares to the rest of the Pixel 10 line.
Google’s Pixel 10A Looks Stylish for a Low-Cost Flagship Phone
Google Pixel 10A vs. Pixel 10, Pixel 10 Pro, Pixel 10 Pro XL
| Google Pixel 10A | Google Pixel 10 | Google Pixel 10 Pro | Google Pixel 10 Pro XL | |
|---|---|---|---|---|
| Display size, tech, resolution, refresh rate | 6.3-inch pOLED, 2,424×1,080 pixels, 60-120 Hz variable refresh rate | 6.3-inch OLED; 2,424×1,080 pixels; 60 to 120 Hz variable refresh rate | 6.3-inch LTPO OLED; 2,856×1,280 pixels; 1 to 120 Hz variable refresh rate | 6.8-inch LTPO OLED; 2,992×1,344 pixels; 1 to 120 Hz variable refresh rate |
| Pixel density | 422 ppi | 422 ppi | 495 ppi | 486 ppi |
| Dimensions (inches) | 6.1×2.9×0.4 in | 6×2.8×0.3 in | 6×2.8×0.3 in | 6.4x3x0.3 in |
| Dimensions (millimeters) | 154.7×73.3×8.9 mm | 152.8x72x8.5 mm | 152.8x72x8.5 mm | 162.8×76.6×8.5 mm |
| Weight (grams, ounces) | 183g (6.5oz) | 204g (7.2oz) | 207g (7.3oz) | 232g (8.2oz) |
| Mobile software | Android 16 | Android 16 | Android 16 | Android 16 |
| Camera | 48-megapixel (wide), 13-megapixel (ultrawide) | 48-megapixel (wide), 13-megapixel (ultrawide), 10.8-megapixel (5x telephoto) | 50-megapixel (wide), 48-megapixel (ultrawide), 48-megapixel (5x telephoto) | 50-megapixel (wide), 48-megapixel (ultrawide), 48-megapixel (5x telephoto) |
| Front-facing camera | 13-megapixel | 10.5-megapixel | 42-megapixel | 42-megapixel |
| Video capture | 4K | 4K | 8K | 8K |
| Processor | Google Tensor G4 | Google Tensor G5 | Google Tensor G5 | Google Tensor G5 |
| RAM + storage | 8GB + 128GB, 256GB | 12GB RAM + 128GB, 256GB | 16GB RAM + 128GB, 256GB, 512GB, 1TB | 16GB RAM + 256GB, 512GB, 1TB |
| Expandable storage | None | None | None | None |
| Battery | 5,100 mAh | 4,970 mAh | 4,870 mAh | 5,200 mAh |
| Fingerprint sensor | Under display | Under display | Under display | Under display |
| Connector | USB-C | USB-C | USB-C | USB-C |
| Headphone jack | None | None | None | None |
| Special features | 7 years of OS, security and Pixel feature drops; Gorilla Glass 3 cover glass; IP68 dust and water resistance; 3,000-nit peak brightness; 2,000,000:1 contrast ratio; 45W fast charging (charger not included); 10W wireless charging Qi certified; Satellite SOS; Wi-Fi 6E; NFC; Bluetooth 6; dual-SIM (nano SIM + eSIM); Camera Coach, Add Me; Best Take; Magic Eraser; Magic Editor; Photo Unblur; Super Res Zoom; Circle to Search. Colors: Lavender, berry, fog, obsidian (black) | Gorilla Glass 2 Victus cover glass; 3,000 nits peak brightness; Satellite SOS; dual-eSIM; Wi-Fi 6E; NFC; Bluetooth 6; 30W fast charging (wall charger not included); Qi2 15W wireless charging; support for PixelSnap magnetic accessories; Google VPN; Super Res Zoom up to 20x; Camera Coach; Add Me; Macro mode; Face Unblur; Auto Best Take; IP68 rating for dust and water resistance; 7 years of OS, security and Pixel Drop updates; Corning Gorilla Glass Victus 2 polished back with satin finish aluminum frame | Gorilla Glass 2 Victus cover glass; 3,300 nits peak brightness; Satellite SOS; Dual-eSIM; Wi-Fi 7; NFC; Bluetooth 6; 30W fast charging (wall charger not included); Qi2 15W wireless charging; support for PixelSnap magnetic accessories; Google VPN; Pro Res zoom up to 100x; Camera Coach; Add Me; Macro mode; Face Unblur; Auto Best Take; High-Res Portrait mode; IP68 rating for dust and water resistance; 7 years of OS, security and Pixel Drop updates; Corning Gorilla GlassVictus 2 silky matte back with polished finish aluminum frame; ultrawideband chip | Gorilla Glass 2 Victus cover glass; 3,300 nits peak brightness; Satellite SOS; Dual-eSIM; Wi-Fi 7; NFC; Bluetooth 6; 45W fast charging (wall charger not included); Qi2.2 25W wireless charging; support for PixelSnap magnetic accessories; Google VPN; Pro Res zoom up to 100x; Camera Coach; Add Me; Macro mode; Face Unblur; Auto Best Take; High-Res Portrait mode; IP68 rating for dust and water resistance; 7 years of OS, security, and Pixel Drop updates; Corning Gorilla GlassVictus 2 silky matte back with polished finish aluminum frame; ultrawideband chip |
| US price starts at | $500 (128GB) | $800 (128GB) | $1,000 (128GB) | $1,200 (256GB) |
Tech
Ingestible Electronics Are Turning Pills Into Devices

One day soon, a doctor might prescribe a pill that doesn’t just deliver medicine but also reports back on what it finds inside you—and then takes actions based on its findings.
Instead of scheduling an endoscopy or CT scan, you’d swallow an electronic capsule smaller than a multivitamin. As it travels through your digestive system, it could check tissue health, look for cancerous changes, and send data to your doctor. It could even release drugs exactly where they’re needed or snip a tiny biopsy sample before passing harmlessly out of your body.
This dream of a do-it-all pill is driving a surge of research into ingestible electronics: smart capsules designed to monitor and even treat disease from inside the gastrointestinal (GI) tract. The stakes are high. GI diseases affect tens of millions of people worldwide, including such ailments as inflammatory bowel disease, celiac disease, and small intestinal bacterial overgrowth. Diagnosis often involves a frustrating maze of blood tests, imaging, and invasive endoscopy. Treatments, meanwhile, can bring serious side effects because drugs affect the whole body, not just the troubled gut.
If capsules could handle much of that work—streamlining diagnosis, delivering targeted therapies, and sparing patients repeated invasive procedures—they could transform care. Over the past 20 years, researchers have built a growing tool kit of ingestible devices, some already in clinical use. These capsule-shaped devices typically contain sensors, circuitry, a power source, and sometimes a communication module, all enclosed in a biocompatible shell. But the next leap forward is still in development: autonomous capsules that can both sense and act, releasing a drug or taking a tissue sample.
That’s the challenge that our lab—the MEMS Sensors and Actuators Laboratory (MSAL) at the University of Maryland, College Park—is tackling. Drawing on decades of advances in microelectromechanical systems (MEMS), we’re building swallowable devices that integrate sensors, actuators, and wireless links in packages that are small and safe enough for patients. The hurdles are considerable: power, miniaturization, biocompatibility, and reliability, to name a few. But the potential payoff will be a new era of personalized and minimally invasive medicine, delivered by something as simple as a pill you can swallow at home.
The Origin of Ingestible Devices
The idea of a smart capsule has been around since the late 1950s, when researchers first experimented with swallowable devices to record temperature, gastric pH, or pressure inside the digestive tract. At the time, it seemed closer to science fiction than clinical reality, bolstered by pop-culture visions like the 1966 film Fantastic Voyage, where miniaturized doctors travel inside the human body to treat a blood clot.
 One of the authors (Ghodssi) holds a miniaturized drug-delivery capsule that’s designed to release medication at specific sites in the gastrointestinal tract.Maximilian Franz/Engineering at Maryland Magazine
One of the authors (Ghodssi) holds a miniaturized drug-delivery capsule that’s designed to release medication at specific sites in the gastrointestinal tract.Maximilian Franz/Engineering at Maryland Magazine
For decades, though, the mainstay of GI diagnostics was endoscopy: a camera on a flexible tube, threaded down the throat or up through the colon. These procedures are quite invasive and require patients to be sedated, which increases both the risk of complications and procedural costs. What’s more, it’s difficult for endoscopes to safely traverse the circuitous pathway of the small intestine. The situation changed in the early 2000s, when video-capsule endoscopy arrived. The best-known product, PillCam, looks like a large vitamin but contains a camera, LEDs, and a transmitter. As it passes through the gut, it beams images and videos to a wearable device.
Today, capsule endoscopy is a routine tool in gastroenterology; ingestible devices can measure acidity, temperature, or gas concentrations. And researchers are pushing further, with experimental prototypes that deliver drugs or analyze the microbiome. For example, teams from Tufts University, in Massachusetts, and Purdue University, in Indiana, are working on devices with dissolvable coatings and mechanisms to collect samples of liquid for studies of the intestinal microbiome.
Still, all those devices are passive. They activate on a timer or by exposure to the neutral pH of the intestines, but they don’t adapt to conditions in real time. The next step requires capsules that can sense biomarkers, make decisions, and trigger specific actions—moving from clever hardware to truly autonomous “smart pills.” That’s where our work comes in.
Building on MEMS technology
Since 2017, MSAL has been pushing ingestible devices forward with the goal of making an immediate impact in health care. The group built on the MEMS community’s legacy in microfabrication, sensors, and system integration, while taking advantage of new tools like 3D printing and materials like biocompatible polymers. Those advances have made it possible to prototype faster and shrink devices smaller, sparking a wave of innovation in wearables, implants, and now ingestibles. Today, MSAL is collaborating with engineers, physicians, and data scientists to move these capsules from lab benches to pharmaceutical trials.
As a first step, back in 2017, we set out to design sensor-carrying capsules that could reliably reach the small intestine and indicate when they reached it. Another challenge was that sensors that work well on the benchtop can falter inside the gut, where shifting pH, moisture, digestive enzymes, and low-oxygen conditions can degrade typical sensing components.
Our earliest prototype adapted MEMS sensing technology to detect abnormal enzyme levels in the duodenum that are linked to pancreatic function. The sensor and its associated electronics were enclosed in a biocompatible, 3D-printed shell coated with polymers that dissolved only at certain pH levels. This strategy could one day be used to detect biomarkers in secretions from the pancreas to detect early-stage cancer.
 A high-speed video shows how a capsule deploys microneedles to deliver drugs into intestinal tissue.University of Maryland/Elsevier
A high-speed video shows how a capsule deploys microneedles to deliver drugs into intestinal tissue.University of Maryland/Elsevier
That first effort with a passive device taught us the fundamentals of capsule design and opened the door to new applications. Since then, we’ve developed sensors that can track biomarkers such as the gas hydrogen sulfide, neurotransmitters such as serotonin and dopamine, and bioimpedance—a measure of how easily ions pass through intestinal tissue—to shed light on the gut microbiome, inflammation, and disease progression. In parallel, we’ve worked on more-active devices: capsule-based tools for controlled drug release and tissue biopsy, using low-power actuators to trigger precise mechanical movements inside the gut.
Like all new medical devices and treatments, ingestible electronics face many hurdles before they reach patients—from earning physician trust and insurance approval to demonstrating clear benefits, safety, and reliability. Packaging is a particular focus, as the capsules must be easy to swallow yet durable enough to survive stomach acid. The field is steadily proving safety and reliability, progressing from proof of concept in tissue, through the different stages of animal studies, and eventually to human trials. Every stage provides evidence that reassures doctors and patients—for example, showing that ingesting a properly packaged tiny battery is safe, and that a capsule’s wireless signals, far weaker than those of a cellphone, pose no health risk as they pass through the gut.
Engineering a Pill-Size Diagnostic Lab
The gastrointestinal tract is packed with clues about health and disease, but much of it remains out of reach of standard diagnostic tools. Ingestible capsules offer a way in, providing direct access to the small intestine and colon. Yet in many cases, the concentrations of chemical biomarkers can be too low to detect reliably in early stages of a disease, which makes the engineering challenge formidable. What’s more, the gut’s corrosive, enzyme-rich environment can foul sensors in multiple ways, interfering with measurements and adding noise to the data.


 Microneedle designs for drug-delivery capsules have evolved over the years. An early prototype [top] used microneedle anchors to hold a capsule in place. Later designs adopted molded microneedle arrays [center] for more uniform fabrication. The most recent version [bottom] integrates hollow microinjector needles, allowing more precise and controllable drug delivery.From top: University of Maryland/Wiley;University of Maryland/Elsevier;University of Maryland/ACS
Microneedle designs for drug-delivery capsules have evolved over the years. An early prototype [top] used microneedle anchors to hold a capsule in place. Later designs adopted molded microneedle arrays [center] for more uniform fabrication. The most recent version [bottom] integrates hollow microinjector needles, allowing more precise and controllable drug delivery.From top: University of Maryland/Wiley;University of Maryland/Elsevier;University of Maryland/ACS
Take, for example, inflammatory bowel disease, for which there is no standard clinical test. Rather than searching for a scarce biomarker molecule, our team focused on a physical change: the permeability of the gut lining, which is a key factor in the disease. We designed capsules that measure the intestinal tissue’s bioimpedance by sending tiny currents across electrodes and recording how the tissue resists or conducts those currents at different frequencies (a technique called impedance spectroscopy). To make the electrodes suitable for in vivo use, we coated them with a thin, conductive, biocompatible polymer that reduces electrical noise and keeps stable contact with the gut wall. The capsule finishes its job by transmitting its data wirelessly to our computers.
In our lab tests, the capsule performed impressively, delivering clean impedance readouts from excised pig tissue even when the sample was in motion. In our animal studies, it detected shifts in permeability triggered by calcium chelators, compounds that pry open the tight junctions between intestinal cells. These results suggest that ingestible bioimpedance capsules could one day give clinicians a direct, minimally invasive window into gut-barrier function and inflammation. We believe that ingestible diagnostics can serve as powerful tools—catching disease earlier, confirming whether treatments are working, and establishing a baseline for gut health.
Drug Delivery at the Right Place, Right Time
Targeted drug delivery is one of the most compelling applications for ingestible capsules. Many drugs for GI conditions—such as biologics for inflammatory bowel disease—can cause serious side effects that limit both dosage and duration of treatment. A promising alternative is delivering a drug directly to the diseased tissue. This localized approach boosts the drug’s concentration at the target site while reducing its spread throughout the body, which improves effectiveness and minimizes side effects. The challenge is engineering a device that can both recognize diseased tissue and deliver medication quickly and precisely.
With other labs making great progress on the sensing side, we’ve devoted our energy to designing devices that can deliver the medicine. We’ve developed miniature actuators—tiny moving parts—that meet strict criteria for use inside the body: low power, small size, biocompatibility, and long shelf life.
Some of our designs use soft and flexible polymer “cantilevers” with attached microneedle systems that pop out from the capsule with enough force to release a drug, but without harming the intestinal tissue. While hollow microneedles can directly inject drugs into the intestinal lining, we’ve also demonstrated prototypes that use the microneedles for anchoring drug payloads, allowing the capsule to release a larger dose of medication that dissolves at an exact location over time.
In other experimental designs, we had the microneedles themselves dissolve after injecting a drug. In still others, we used microscale 3D printing to tailor the structure of the microneedles and control how quickly a drug is released—providing either a slow and sustained dose or a fast delivery. With this 3D printing, we created rigid microneedles that penetrate the mucosal lining and gradually diffuse the drug into the tissue, and soft microneedles that compress when the cantilever pushes them against the tissue, forcing the drug out all at once.
Tissue Biopsy via Capsule
Tissue sampling remains the gold standard diagnostic tool in gastroenterology, offering insights far beyond what doctors can glean from visual inspection or blood tests. Capsules hold unique promise here: They can travel the full length of the GI tract, potentially enabling more frequent and affordable biopsies than traditional procedures. But the engineering hurdles are substantial. To collect a sample, a device must generate significant mechanical force to cut through the tough, elastic muscle of the intestines—while staying small enough to swallow.
Different strategies have been explored to solve this problem. Torsion springs can store large amounts of energy but are difficult to fit inside a tiny capsule. Electrically driven mechanisms may demand more power than current capsule batteries can provide. Magnetic actuation is another option, but it requires bulky external equipment and precise tracking of the capsule inside the body.
Our group has developed a low-power biopsy system that builds on the torsion-spring approach. We compress a spring and use adhesive to “latch” it closed within the capsule, then attach a microheater to the latch. When we wirelessly send current to the device, the microheater melts the adhesive on the latch, triggering the spring. We’ve experimented with tissue-collection tools, integrating a bladed scraper or a biopsy punch (a cylindrical cutting tool) with our spring-activated mechanisms; either of those tools can cut and collect tissue from the intestinal lining. With advanced 3D printing methods like direct laser writing, we can put fine, microscale edges on these miniature cutting tools that make it easier for them to penetrate the intestinal lining.
Storing and protecting the sample until the capsule naturally passes through the body is a major challenge, requiring both preservation of the sample and resealing the capsule to prevent contamination. In one of our designs, residual tension in the spring keeps the bladed scraper rotating, pulling the sample into the capsule and effectively closing a hatch that seals it inside.
The Road to Clinical Use for Ingestibles
Looking ahead, we expect to see the first clinical applications emerge in early-stage screening. Capsules that can detect electrochemical, bioimpedance, or visual signals could help doctors make sense of symptoms like vague abdominal pain by revealing inflammation, gut permeability, tumors, or bacterial overgrowth. They could also be adapted to screen for GI cancers. This need is pressing: The American Cancer Society reports that as of 2021, 41 percent of eligible U.S. adults were not up to date on colorectal cancer screening. What’s more, effective screening tools don’t yet exist for some diseases, such as small bowel adenocarcinoma. Capsule technology could make screening less invasive and more accessible.
Of course, ingestible capsules carry risks. The standard hazards of endoscopy still apply, such as the possibility of bleeding and perforation, and capsules introduce new complications. For example, if a capsule gets stuck in its passage through the GI tract, it could cause bowel obstruction and require endoscopic retrieval or even surgery. And concerns that are specific to ingestibles, including the biocompatibility of materials, reliable encapsulation of electronics, and safe battery operation, all demand rigorous testing before clinical use.
 A microbe-powered biobattery designed for ingestible devices dissolves in water within an hour. Seokheun Choi/Binghamton University
A microbe-powered biobattery designed for ingestible devices dissolves in water within an hour. Seokheun Choi/Binghamton University
Powering these capsules is a key challenge that must be solved on the path to the clinic. Most capsule endoscopes today rely on coin-cell batteries, typically silver oxide, which offer a safe and energy-dense source but often occupy 30 to 50 percent of the capsule’s volume. So researchers have investigated alternatives, from wireless power transfer to energy-harvesting systems. At the State University of New York at Binghamton, one team is exploring microbial fuel cells that generate electricity from probiotic bacteria interacting with nutrients in the gut. At MIT, researchers used the gastric fluids of a pig’s stomach to power a simple battery. In our own lab, we are exploring piezoelectric and electrochemical approaches to harvesting energy throughout the GI tract.
The next steps for our team are pragmatic ones: working with gastroenterologists and animal-science experts to put capsule prototypes through rigorous in vivo studies, then refining them for real-world use. That means shrinking the electronics, cutting power consumption, and integrating multiple functions into a single multimodal device that can sense, sample, and deliver treatments in one pass. Ultimately, any candidate capsule will require regulatory approval for clinical use, which in turn demands rigorous proof of safety and clinical effectiveness for a specific medical application.
The broader vision is transformative. Swallowable capsules could bring diagnostics and treatment out of the hospital and into patients’ homes. Whereas procedures with endoscopes require anesthesia, patients could take ingestible electronics easily and routinely. Consider, for example, patients with inflammatory bowel disease who live with an elevated risk of cancer; a smart capsule could perform yearly cancer checks, while also delivering medication directly wherever necessary.
Over time, we expect these systems to evolve into semiautonomous tools: identifying lesions, performing targeted biopsies, and perhaps even analyzing samples and applying treatment in place. Achieving that vision will require advances at the very edge of microelectronics, materials science, and biomedical engineering, bringing together capabilities that once seemed impossible to combine in something the size of a pill. These devices hint at a future in which the boundary between biology and technology dissolves, and where miniature machines travel inside the body to heal us from within.
From Your Site Articles
Related Articles Around the Web
Tech
Vermont EV Buses Prove Unreliable For Transportation This Winter

An anonymous reader writes:
Electric buses are proving unreliable this winter for Vermont’s Green Mountain Transit, as it needs to be over 41 degrees for the buses to charge, but due to a battery recall the buses are a fire hazard and can’t be charged in a garage.
Spokesman for energy workers advocacy group Power the Future Larry Behrens told the Center Square: “Taxpayers were sold an $8 million ‘solution’ that can’t operate in cold weather when the home for these buses is in New England.”
“We’re beyond the point where this looks like incompetence and starts to smell like fraud,” Behrens said.
“When government rushes money out the door to satisfy green mandates, basic questions about performance, safety, and value for taxpayers are always pushed aside,” Behrens said. “Americans deserve to know who approved this purchase and why the red flags were ignored.”
General manager at Green Mountain Transit (GMT) Clayton Clark told The Center Square that “the federal government provides public transit agencies with new buses through a competitive grant application process, and success is not a given.”
Tech
When accurate AI is still dangerously incomplete

Typically, when building, training and deploying AI, enterprises prioritize accuracy. And that, no doubt, is important; but in highly complex, nuanced industries like law, accuracy alone isn’t enough. Higher stakes mean higher standards: Models outputs must be assessed for relevancy, authority, citation accuracy and hallucination rates.
To tackle this immense task, LexisNexis has evolved beyond standard retrieval-augmented generation (RAG) to graph RAG and agentic graphs; it has also built out “planner” and “reflection” AI agents that parse requests and criticize their own outputs.
“There’s no such [thing] as ‘perfect AI’ because you never get 100% accuracy or 100% relevancy, especially in complex, high stake domains like legal,” Min Chen, LexisNexis’ SVP and chief AI officer, acknowledges in a new VentureBeat Beyond the Pilot podcast.
The goal is to manage that uncertainty as much as possible and translate it into consistent customer value. “At the end of the day, what matters most for us is the quality of the AI outcome, and that is a continuous journey of experimentation, iteration and improvement,” Chen said.
Getting ‘complete’ answers to multi-faceted questions
To evaluate models and their outputs, Chen’s team has established more than a half-dozen “sub metrics” to measure “usefulness” based on several factors — authority, citation accuracy, hallucination rates — as well as “comprehensiveness.” This particular metric is designed to evaluate whether a gen AI response fully addressed all aspects of a users’ legal questions.
“So it’s not just about relevancy,” Chen said. “Completeness speaks directly to legal reliability.”
For instance, a user may ask a question that requires an answer covering five distinct legal considerations. Gen AI may provide a response that accurately addresses three of these. But, while relevant, this partial answer is incomplete and, from a user perspective, insufficient. This can be misleading and pose real-life risks.
Or, for example, some citations may be semantically relevant to a user’s question, but they may point to arguments or instances that were ultimately overruled in court. “Our lawyers will consider them not citable,” Chen said. “If they’re not citable, they’re not useful.”
Moving beyond standard RAG
LexisNexis launched its flagship gen AI product, Lexis+ AI — a legal AI tool for drafting, research and analysis — in 2023. It was built on a standard RAG framework and hybrid vector search that grounds responses in LexisNexis’ trusted, authoritative knowledge base.
The company then released its personal legal assistant, Protégé, in 2024. This agent incorporates a knowledge graph layer on top of vector search to overcome a “key limitation” of pure semantic search. Although “very good” at retrieving contextually relevant content, semantic search “doesn’t always guarantee authoritative answers,” Chen said.
Initial semantic search returns what it deems relevant content; Chen’s team then traverses those returns across a “point of law” graph to further filter the most highly authoritative documents.
Going beyond this, Chen’s team is developing agentic graphs and accelerating automation so agents can plan and execute complex multi-step tasks.
For instance, self-directed “planner agents” for research Q&A break user questions into multiple sub-questions. Human users can review and edit these to further refine and personalize final answers. Meanwhile, a “reflection agent” handles transactional document drafting. It can “automatically, dynamically” criticize its initial draft, then incorporate that feedback and refine in real time.
However, Chen said that all of this is not to cut humans out of the mix; human experts and AI agents can “learn, reason and grow together.” “I see the future [as] a deeper collaboration between humans and AI.”
Watch the podcast to hear more about:
-
How LexisNexis’ acquisition of Henchman helped ground AI models with proprietary LexisNexis data and customer data;
-
The difference between deterministic and non-deterministic evaluation;
-
Why enterprises should identify KPIs and definitions of success before rushing to experimentation;
-
The importance of focusing on a “triangle” of key components: Cost, speed and quality.
You can also listen and subscribe to Beyond the Pilot on Spotify, Apple or wherever you get your podcasts.
Tech
A Vast Trove of Exposed Social Security Numbers May Put Millions at Risk of Identity Theft

After years spent finding and investigating data breaches, Greg Pollock admits that when he comes across yet another exposed database full of passwords and Social Security numbers, “I come to it with some fatigue.” But Pollock, director of research at the cybersecurity company UpGuard, says he and his colleagues found an exposed, publicly accessible database online in January that appeared to contain a trove of Americans’ sensitive personal data so massive that his weariness lifted and they sprang to action to validate the finding.
The UpGuard researchers point out that not all of the records represent unique, valid information, but the raw totals they found in the January exposure included roughly 3 billion email addresses and passwords as well as about 2.7 billion records that included Social Security numbers. It was unclear who had set up the database, but it seemed to contain personal details that may have been cobbled together from multiple historic data breaches—including, perhaps, the trove from the 2024 breach of the background-checking service National Public Data. It is common for data brokers and cybercriminals to combine and recombine old datasets, but the scale and the potential quantity of Social Security numbers—even if only a fraction of them were real—was striking.
“Every week, there’s another finding where it looks big on paper, but it’s probably not very novel,” Pollock says. “So I was surprised when I started digging into the specific cases here to validate the data. In some cases, the identities in this data breach are at risk because they have been exposed, but they have not yet been exploited.”
The data was hosted by the German cloud provider Hetzner. Since Pollock could not identify an owner of the database to contact, he notified Hetzner on January 16. The company, in turn, said it notified its customer, which removed the data on January 21.
Hetzner did not provide WIRED with comment ahead of publication.
The researchers did not download the entire dataset for analysis due to its size and sensitivity. Instead they worked with a sample of 2.8 million records—a tiny fraction of the total trove. By analyzing trends in the data, including the popularity of certain cultural references in passwords, they concluded that much of the data likely dates to the United States in roughly 2015. For example, passwords referencing One Direction, Fall Out Boy, and Taylor Swift were very common. Meanwhile, references to Blackpink, Katseye, and Btsarmy were just barely beginning to show up.
Old data is still valuable for two reasons. First, people often reuse the same email address and password, or a variation of the password, across many different websites and services. This means that cybercriminals can keep trying the same login credentials for the same people over time. The second reason is that people’s Social Security numbers are often linked to their most sensitive and high-stakes data but almost never change during their lifetimes. As a result, valid SSNs are one of the crown jewels of identity theft for attackers.
In the sample of data the researchers reviewed, Pollock says that one in four Social Security numbers appeared to be valid and legitimate. The sample was too small to extrapolate to the entire dataset, but a quarter of all the records containing SSNs would be 675 million. A fraction of that would still represent a very significant set of Social Security numbers.
To verify the data, UpGuard researchers contacted a handful of people whose data appeared in the leaked trove. Pollock emphasizes that one of the most concerning findings from speaking to those individuals was that not all of them have had their identities stolen or suffered hacks. In other words, there was information in the database that has not been exploited by cybercriminals—and potential victims don’t necessarily know that their information has been exposed.
Tech
Daily Deal: The All-in-One Super-Sized Ethical Hacking Bundle

from the good-deals-on-cool-stuff dept
To completely understand computer security, it’s vital to step outside the fence and to think outside the box. Computer security is not just about firewalls, Intrusion Prevention Systems, or anti-viruses. It’s also about tricking people into doing whatever a hacker wishes. A secure system, network, or infrastructure is also about informed people. The All-in-One Super-Sized Ethical Hacking Bundle will help you learn to master ethical hacking techniques and methodologies over 14 courses. It’s on sale for $28 for a limited time.
Note: The Techdirt Deals Store is powered and curated by StackCommerce. A portion of all sales from Techdirt Deals helps support Techdirt. The products featured do not reflect endorsements by our editorial team.
Filed Under: daily deal
Tech
Dutch defense chief claims F-35 could be "jailbroken like an iPhone" to bypass US approval


In an interview with NR Nieuwsradio, Tuinman was asked if the F-35’s software could be altered by European forces without the United States’ consent should they lose the US as an ally – a prospect that has been repeatedly raised as tensions between the continent and President Trump continue to…
Read Entire Article
Source link
-

 Sports7 days ago
Sports7 days agoBig Tech enters cricket ecosystem as ICC partners Google ahead of T20 WC | T20 World Cup 2026
-
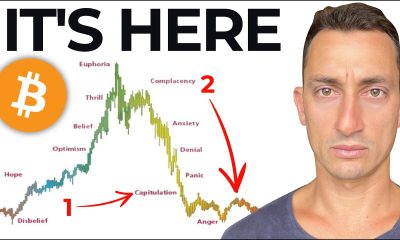
 Video2 days ago
Video2 days agoBitcoin: We’re Entering The Most Dangerous Phase
-

 Tech4 days ago
Tech4 days agoLuxman Enters Its Second Century with the D-100 SACD Player and L-100 Integrated Amplifier
-

 Video5 days ago
Video5 days agoThe Final Warning: XRP Is Entering The Chaos Zone
-

 Sports2 days ago
Sports2 days agoGB's semi-final hopes hang by thread after loss to Switzerland
-
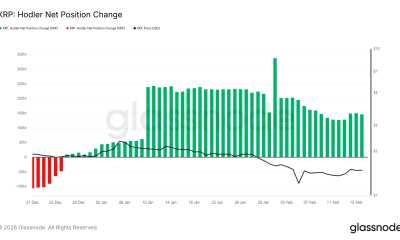
 Crypto World1 day ago
Crypto World1 day agoCan XRP Price Successfully Register a 33% Breakout Past $2?
-

 Tech2 days ago
Tech2 days agoThe Music Industry Enters Its Less-Is-More Era
-

 Business20 hours ago
Business20 hours agoInfosys Limited (INFY) Discusses Tech Transitions and the Unique Aspects of the AI Era Transcript
-

 Entertainment6 hours ago
Entertainment6 hours agoKunal Nayyar’s Secret Acts Of Kindness Sparks Online Discussion
-

 Video1 day ago
Video1 day agoFinancial Statement Analysis | Complete Chapter Revision in 10 Minutes | Class 12 Board exam 2026
-
 Crypto World7 days ago
Crypto World7 days agoPippin (PIPPIN) Enters Crypto’s Top 100 Club After Soaring 30% in a Day: More Room for Growth?
-
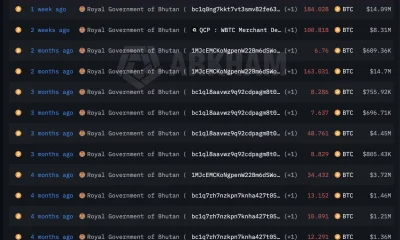
 Crypto World5 days ago
Crypto World5 days agoBhutan’s Bitcoin sales enter third straight week with $6.7M BTC offload
-

 Tech11 hours ago
Tech11 hours agoRetro Rover: LT6502 Laptop Packs 8-Bit Power On The Go
-
 Video7 days ago
Video7 days agoPrepare: We Are Entering Phase 3 Of The Investing Cycle
-

 NewsBeat3 days ago
NewsBeat3 days agoThe strange Cambridgeshire cemetery that forbade church rectors from entering
-

 Business6 days ago
Business6 days agoBarbeques Galore Enters Voluntary Administration
-

 Business12 hours ago
Business12 hours agoTesla avoids California suspension after ending ‘autopilot’ marketing
-
 Crypto World6 days ago
Crypto World6 days agoEthereum Price Struggles Below $2,000 Despite Entering Buy Zone
-

 NewsBeat3 days ago
NewsBeat3 days agoMan dies after entering floodwater during police pursuit
-

 Crypto World5 days ago
Crypto World5 days agoKalshi enters $9B sports insurance market with new brokerage deal









