Servers computers
How to enable SSH on Linux Ubuntu (Easy step by step guide)

Install OpenSSH-server on Ubuntu to enable SSH to remotely connect to your Ubuntu computer
✅ Subscribe to help us grow: https://www.youtube.com/knowledgesharingtech?sub_confirmation=1
My Amazon affiliate link:
Amazon best sellers Computers and Accessories: https://amzn.to/37v1Z7Z
Linux Commands
Ctrl+Alt+T (to Open terminal)
sudo apt update
clear (to clear the screen)
sudo apt install openssh-server
sudo systemctl status ssh
sudo ufw allow ssh
ip a
Windows commands:
ssh user@ipaddress
Follow me on:
My websites:
https://knowledgesharingtech.com/
https://tripleewebdesigns.com
Facebook: https://www.facebook.com/knowledgesharingtech
Twitter: https://twitter.com/KnowledgeShari6
Disclaimer: Use the instructions in this video at your own risk. We are not responsible for any data loss or other damages that may occur .
source
Servers computers
New Home Backup Server (Dell T640 with 18 20TB Disks)

In this video I create a new backup server from a Dell EMC PowerEdge T640 with 18x 20TB Seagate Exos refurbished drives. Also there’s some more ranting about backups in general. But idk, there are chapters so you can skip to whatever. And it’s not technically a server, in that it doesn’t serve files. It’s really more of a client that takes files from other servers and holds onto them. But I call it a backup server because hardware-wise it’s a server. Anywho, that’s the description. It’s probably not optimal for the YouTube algorithm, but hey, I’m not an influencer even though I have a TikTok account that I don’t use.
Update: https://www.youtube.com/watch?v=Secv5P01k2M&t=5195
00:00 Intro
02:08 The Drives
03:30 The Data & Other Backups
05:40 RAID & Data Loss
10:00 IcyDock ExpressCage
13:23 Fan Noise
18:30 Caddies, Trays, or Sleds.. Whatever
28:27 Booting & Array Creation
33:50 Array Build Status and Drive Stats
36:43 OS SSDs and T640 Internals
58:20 Lengthy Conclusion (Backups Rant.. again)
1:10:20 Outro .
source
Servers computers
How to Configure iDRAC9 at Initial Setup of Your Dell PowerEdge Server

For more information on the configuration of an iDRAC 9 please visit our knowledge base: http://www.dell.com/support/article/SLN306877
During the initial startup of your new Dell Server, you have to configure the iDRAC to be able to manage your Dell PowerEdge server remotely. In this video you will learn how to configure the iDRAC9 of your Server for the first time.
The iDRAC 9 is configured with a default IP which you can change during the initial setup.
You can access the iDRAC via a dedicated Network Card or the LAN on Motherboard after it is configured.
🔴 For more helpful tutorials, tips and tricks for Dell EMC Products, subscribe to our channel: http://www.youtube.com/DellEnterpriseSupport?sub_confirmation=1
Want to know more about iDRAC, check out this Playlist:
📺 Find our latest Video here:
📖 You can find our Knowledgebase filled with helpful articles here:
https://dell.to/2mgVTVj
💻 Need help? Contact our Support
Community Forums: http://www.dell.com/community
Twitter: http://www.twitter.com/DellCaresPRO
Facebook: https://www.facebook.com/DellEMCSupport/
Other Contact Options: http://www.dell.com/contact .
source
Servers computers
Now Available in Lenovo ThinkSystem SR645 Rack Servers

Lenovo is excited to deliver AMD EPYC™ processors with AMD 3D V-Cache™ technology in its ThinkSystem SR645 rack servers. These new systems feature expanded L3 cache designed for technical computing workloads—helping customers get new products to market faster than ever before.
Discover more: https://www.amd.com/en/events/epyc
*See claims information in video endnotes.
***
Subscribe: http://bit.ly/Subscribe_to_AMD
Like us on Facebook: http://bit.ly/AMD_on_Facebook
Follow us on Twitter: http://bit.ly/AMD_On_Twitter
Follow us on Twitch: http://Twitch.tv/AMD
Follow us on LinkedIn: http://bit.ly/AMD_on_Linkedin
Follow us on Instagram: http://bit.ly/AMD_on_Instagram
©2022 Advanced Micro Devices, Inc. AMD, the AMD Arrow Logo, and combinations thereof are trademarks of Advanced Micro Devices, Inc. in the United States and other jurisdictions. Other names are for informational purposes only and may be trademarks of their respective owners. .
source
Servers computers
Best Public Bedrock SMP Server to Join!
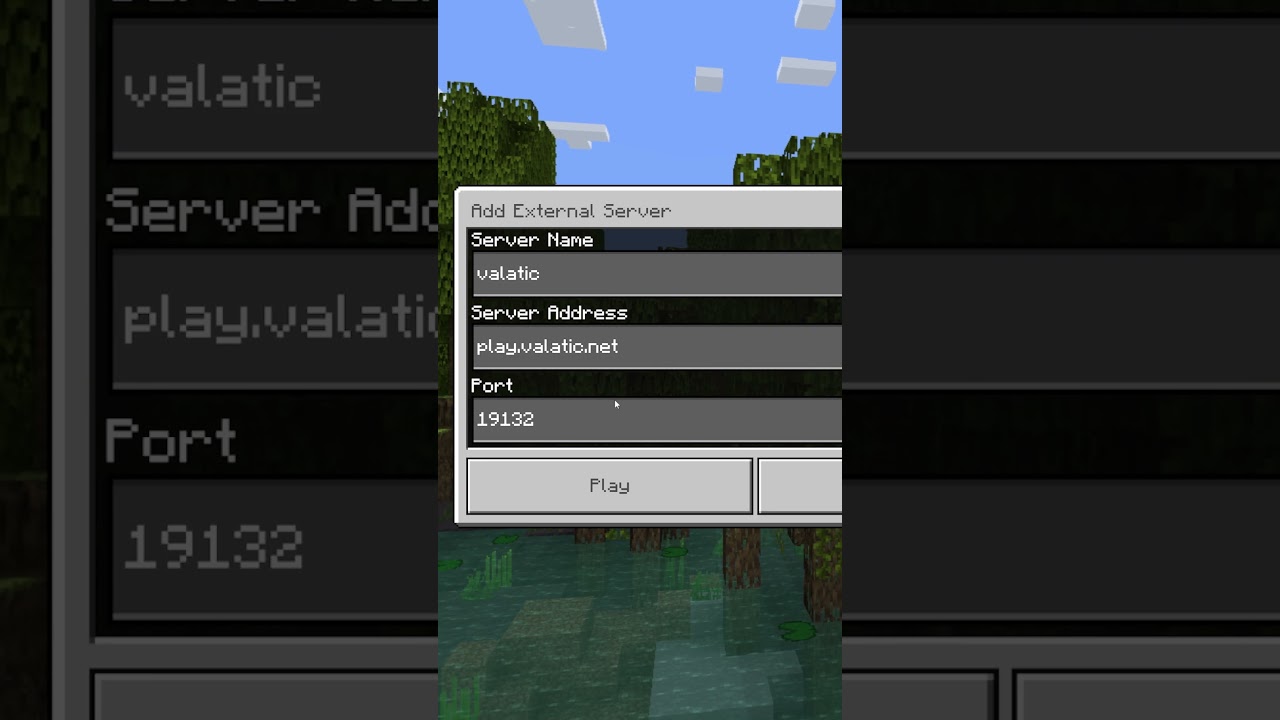
Best Public Bedrock SMP Server to Join!
Come join this Minecraft Valatic SMP on Java or Bedrock on any device! Join this active server with your friends or by yourself for completely free!
Server IP ➤ play.valatic.net
Bedrock PORT ➤ 19132
SMP Store (HUGE SALE) ➤ https://store.valatic.net
Use code BLUEJAY to save on your purchase! Purchase crate-keys, ranks, and more on the Valatic store.
SMP Discord Server ► https://discord.gg/valatic
To join the Public Minecraft Valatic SMP, watch the ENTIRE VIDEO for the server ip and port. Also, leave all your questions in the comments and I’ll do my best to answer!
The Public Minecraft Valatic SMP is just like the Dream smp and Lifesteal smp and you can join on Minecraft java, bedrock, or pocket edition. You can join anytime for completely free with your friends, or make some on the SMP! The server has an active, growing player base, exciting events, awesome server features, professional staff, and the world map is always expanding so you can explore! You can make friends with other players on the server at the spawn, or smp clubhouse too! There is even a server shop to get awesome items that support the Valatic SMP so it can keep the server running! On the Valatic SMP you can travel to many server locations, build cities, explore land, and even start governments or massive server wars! There are even different game modes on the server like Minecraft Lifesteal SMP, Earth SMP, and One Block! The possibilities on the Public Minecraft Valatic SMP are endless so join now and get started!
If you enjoyed the video then subscribe so I can make more just like it!
This server is a 1.18-1.19.2 Minecraft server and nothing else. Consider Subscribing.
#smp #join #public #java #bedrock #valatic .
source
Servers computers
Computer Security | Types of Computer Security | Cybersecurity Course | Edureka

🔵Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN
🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl
This Edureka video gives an introduction to Computer Security and the types of computer security. Also, it teaches you various ways to secure your computer devices. Topics covered in this video includes:
1. What is Computer security?
2. Goals of Computer security
3. What to secure?- Types of computer security
4. Potential losses due to cyber attacks
5. How to secure?
🔵CyberSecurity Certification Training : https://www.edureka.co/cybersecurity-certification-training
Subscribe to our channel to get video updates. Hit the subscribe button above.
————————————-
About Edureka Cyber Security Training
Cybersecurity is the combination of processes, practices, and technologies designed to protect networks, computers, programs, data and information from attack, damage or unauthorized access.
Edureka’s Cybersecurity Certification Course will help you in learning about the basic concepts of Cybersecurity along with the methodologies that must be practiced ensuring information security of an organization. Starting from the Ground level Security Essentials, this course will lead you through Cryptography, Computer Networks & Security, Application Security, Data & Endpoint Security, idAM (Identity & Access Management), Cloud Security, Cyber-Attacks and various security practices for businesses.
————————————————
Why Learn Cyber Security?
Cybersecurity is the gathering of advances that procedures and practices expected to ensure systems, PCs, projects and information from assault, harm or unapproved get to. In a processing setting, security incorporates both cybersecurity and physical security, it is imperative since cyberattackers can without much of a stretch take and obliterate the profoundly grouped data of governments, defense offices and banks for which the results are huge so it is essential to have an appropriate innovation which an avoid digital wrongdoings.
—————————————————
Objectives of Edureka Cyber Security Course
This course is designed to cover a holistic & a wide variety of foundational topics of the cybersecurity domain which will be helpful to lead freshers as well as IT professional having 1 to 2 years of experience, into the next level of choice such as ethical hacking/ audit & compliance / GRC/ Security Architecture and so on
This course focuses mainly on the basics concepts of Cyber Security
In this course, we are going to deal with Ground level security essentials cryptography, computer networks & security, application security, data & endpoint security, idAM (identity & access management), cloud security, cyber-attacks and various security practices for businesses
This course will be your first step towards learning Cyber Security
————————————–
Who Should go for this Training?
Anyone having the zeal to learn innovative technologies can take up this course. Especially, students and professionals aspiring to make a career in the Cybersecurity technology. However, Cybersecurity Certification Course is best suited for the below mentioned profiles:-
Networking Professionals
Linux Administrators
———————————————–
For more information, Please write back to us at sales@edureka.co or call us at IND: 9606058406 / US: 18338555775 (toll free).
Instagram: https://www.instagram.com/edureka_learning/
Facebook: https://www.facebook.com/edurekaIN/
Twitter: https://twitter.com/edurekain
LinkedIn: https://www.linkedin.com/company/edureka .
source
Servers computers
The Man Who Revolutionized Computer Science With Math

Leslie Lamport revolutionized how computers talk to each other. The Turing Award-winning computer scientist pioneered the field of distributed systems, where multiple components on different networks coordinate to achieve a common objective. (Internet searches, cloud computing and artificial intelligence all involve orchestrating legions of powerful computing machines to work together.) In the early 1980s, Lamport also created LaTeX, a document preparation system that provides sophisticated ways to typeset complex formulas and format scientific documents. In 1989, Lamport invented Paxos, a “consensus algorithm” that allows multiple computers to execute complex tasks; without it, modern computing could not exist. He’s also brought more attention to a handful of problems, giving them distinctive names like the bakery algorithm and the Byzantine Generals Problem. Lamport’s work since the 1990s has focused on “formal verification,” the use of mathematical proofs to verify the correctness of software and hardware systems. Notably, he created a “specification language” called TLA+ (for Temporal Logic of Actions), which employs the precise language of mathematics to prevent bugs and avoid design flaws.
Read more at Quanta Magazine: https://www.quantamagazine.org/bringing-mathematical-perfection-to-software-20220516/
– VISIT our Website: https://www.quantamagazine.org
– LIKE us on Facebook: https://www.facebook.com/QuantaNews
– FOLLOW us Twitter: https://twitter.com/QuantaMagazine
Quanta Magazine is an editorially independent publication supported by the Simons Foundation https://www.simonsfoundation.org/
#computerscience #math .
source
-
 Science & Environment4 weeks ago
Science & Environment4 weeks agoHyperelastic gel is one of the stretchiest materials known to science
-

 Technology4 weeks ago
Technology4 weeks agoWould-be reality TV contestants ‘not looking real’
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoHow to unsnarl a tangle of threads, according to physics
-

 Science & Environment4 weeks ago
Science & Environment4 weeks ago‘Running of the bulls’ festival crowds move like charged particles
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoMaxwell’s demon charges quantum batteries inside of a quantum computer
-

 Technology3 weeks ago
Technology3 weeks agoIs sharing your smartphone PIN part of a healthy relationship?
-
 Science & Environment4 weeks ago
Science & Environment4 weeks agoLiquid crystals could improve quantum communication devices
-
 Science & Environment4 weeks ago
Science & Environment4 weeks agoQuantum ‘supersolid’ matter stirred using magnets
-

 Womens Workouts3 weeks ago
Womens Workouts3 weeks ago3 Day Full Body Women’s Dumbbell Only Workout
-

 Science & Environment3 weeks ago
Science & Environment3 weeks agoX-rays reveal half-billion-year-old insect ancestor
-
 Science & Environment4 weeks ago
Science & Environment4 weeks agoWhy this is a golden age for life to thrive across the universe
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoSunlight-trapping device can generate temperatures over 1000°C
-
 Science & Environment4 weeks ago
Science & Environment4 weeks agoQuantum forces used to automatically assemble tiny device
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoITER: Is the world’s biggest fusion experiment dead after new delay to 2035?
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoNerve fibres in the brain could generate quantum entanglement
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoHow to wrap your mind around the real multiverse
-
News1 month ago
the pick of new debut fiction
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoA slight curve helps rocks make the biggest splash
-

 News4 weeks ago
News4 weeks agoOur millionaire neighbour blocks us from using public footpath & screams at us in street.. it’s like living in a WARZONE – WordupNews
-
 Science & Environment4 weeks ago
Science & Environment4 weeks agoLaser helps turn an electron into a coil of mass and charge
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoTime travel sci-fi novel is a rip-roaringly good thought experiment
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoNuclear fusion experiment overcomes two key operating hurdles
-
 Science & Environment4 weeks ago
Science & Environment4 weeks agoPhysicists are grappling with their own reproducibility crisis
-

 News1 month ago
News1 month ago▶️ Hamas in the West Bank: Rising Support and Deadly Attacks You Might Not Know About
-

 News4 weeks ago
News4 weeks ago▶️ Media Bias: How They Spin Attack on Hezbollah and Ignore the Reality
-
 News4 weeks ago
News4 weeks agoYou’re a Hypocrite, And So Am I
-
Business3 weeks ago
Eurosceptic Andrej Babiš eyes return to power in Czech Republic
-

 Sport4 weeks ago
Sport4 weeks agoJoshua vs Dubois: Chris Eubank Jr says ‘AJ’ could beat Tyson Fury and any other heavyweight in the world
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoA new kind of experiment at the Large Hadron Collider could unravel quantum reality
-

 Technology3 weeks ago
Technology3 weeks agoWhy Machines Learn: A clever primer makes sense of what makes AI possible
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoCaroline Ellison aims to duck prison sentence for role in FTX collapse
-

 News1 month ago
News1 month agoNew investigation ordered into ‘doorstep murder’ of Alistair Wilson
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoRethinking space and time could let us do away with dark matter
-

 Technology3 weeks ago
Technology3 weeks agoQuantum computers may work better when they ignore causality
-

 Sport3 weeks ago
Sport3 weeks agoWatch UFC star deliver ‘one of the most brutal knockouts ever’ that left opponent laid spark out on the canvas
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoA tale of two mysteries: ghostly neutrinos and the proton decay puzzle
-
News4 weeks ago
The Project Censored Newsletter – May 2024
-
 Technology3 weeks ago
Technology3 weeks agoRobo-tuna reveals how foldable fins help the speedy fish manoeuvre
-
Business3 weeks ago
Should London’s tax exiles head for Spain, Italy . . . or Wales?
-

 MMA3 weeks ago
MMA3 weeks agoConor McGregor challenges ‘woeful’ Belal Muhammad, tells Ilia Topuria it’s ‘on sight’
-

 Football3 weeks ago
Football3 weeks agoFootball Focus: Martin Keown on Liverpool’s Alisson Becker
-

 Technology2 weeks ago
Technology2 weeks agoMicrophone made of atom-thick graphene could be used in smartphones
-

 Business2 weeks ago
Business2 weeks agoWhen to tip and when not to tip
-

 Sport2 weeks ago
Sport2 weeks agoWales fall to second loss of WXV against Italy
-

 Health & fitness4 weeks ago
Health & fitness4 weeks agoThe secret to a six pack – and how to keep your washboard abs in 2022
-
 Technology3 weeks ago
Technology3 weeks ago‘From a toaster to a server’: UK startup promises 5x ‘speed up without changing a line of code’ as it plans to take on Nvidia, AMD in the generative AI battlefield
-

 Technology3 weeks ago
Technology3 weeks agoUniversity examiners fail to spot ChatGPT answers in real-world test
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoPhysicists have worked out how to melt any material
-

 News4 weeks ago
News4 weeks agoIsrael strikes Lebanese targets as Hizbollah chief warns of ‘red lines’ crossed
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoFuture of fusion: How the UK’s JET reactor paved the way for ITER
-

 Technology2 weeks ago
Technology2 weeks agoThis AI video generator can melt, crush, blow up, or turn anything into cake
-
Business2 weeks ago
Ukraine faces its darkest hour
-
Politics3 weeks ago
Robert Jenrick vows to cut aid to countries that do not take back refused asylum seekers | Robert Jenrick
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoBeing in two places at once could make a quantum battery charge faster
-

 Technology4 weeks ago
Technology4 weeks agoThe ‘superfood’ taking over fields in northern India
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoUK spurns European invitation to join ITER nuclear fusion project
-

 CryptoCurrency4 weeks ago
CryptoCurrency4 weeks agoCardano founder to meet Argentina president Javier Milei
-
Politics4 weeks ago
UK consumer confidence falls sharply amid fears of ‘painful’ budget | Economics
-

 TV3 weeks ago
TV3 weeks agoCNN TÜRK – 🔴 Canlı Yayın ᴴᴰ – Canlı TV izle
-

 News3 weeks ago
News3 weeks agoWhy Is Everyone Excited About These Smart Insoles?
-

 Womens Workouts3 weeks ago
Womens Workouts3 weeks ago3 Day Full Body Toning Workout for Women
-

 Technology3 weeks ago
Technology3 weeks agoGet ready for Meta Connect
-

 Sport4 weeks ago
Sport4 weeks agoUFC Edmonton fight card revealed, including Brandon Moreno vs. Amir Albazi headliner
-

 News1 month ago
News1 month agoHow FedEx CEO Raj Subramaniam Is Adapting to a Post-Pandemic Economy
-

 Science & Environment4 weeks ago
Science & Environment4 weeks agoWhy we need to invoke philosophy to judge bizarre concepts in science
-
Business4 weeks ago
Thames Water seeks extension on debt terms to avoid renationalisation
-
Politics4 weeks ago
‘Appalling’ rows over Sue Gray must stop, senior ministers say | Sue Gray
-

 Science & Environment3 weeks ago
Science & Environment3 weeks agoMeet the world's first female male model | 7.30
-

 Health & fitness3 weeks ago
Health & fitness3 weeks agoThe 7 lifestyle habits you can stop now for a slimmer face by next week
-
Business2 weeks ago
DoJ accuses Donald Trump of ‘private criminal effort’ to overturn 2020 election
-

 Entertainment1 week ago
Entertainment1 week agoChristopher Ciccone, artist and Madonna’s younger brother, dies at 63
-

 Technology2 weeks ago
Technology2 weeks agoUkraine is using AI to manage the removal of Russian landmines
-
Business2 weeks ago
Bank of England warns of ‘future stress’ from hedge fund bets against US Treasuries
-

 TV2 weeks ago
TV2 weeks agoPhillip Schofield accidentally sets his camp on FIRE after using emergency radio to Channel 5 crew
-

 Technology2 weeks ago
Technology2 weeks agoAmazon’s Ring just doubled the price of its alarm monitoring service for grandfathered customers
-

 News2 weeks ago
News2 weeks agoHeartbreaking end to search as body of influencer, 27, found after yacht party shipwreck on ‘Devil’s Throat’ coastline
-

 Politics4 weeks ago
Politics4 weeks agoTrump says he will meet with Indian Prime Minister Narendra Modi next week
-

 CryptoCurrency4 weeks ago
CryptoCurrency4 weeks agoEthereum is a 'contrarian bet' into 2025, says Bitwise exec
-
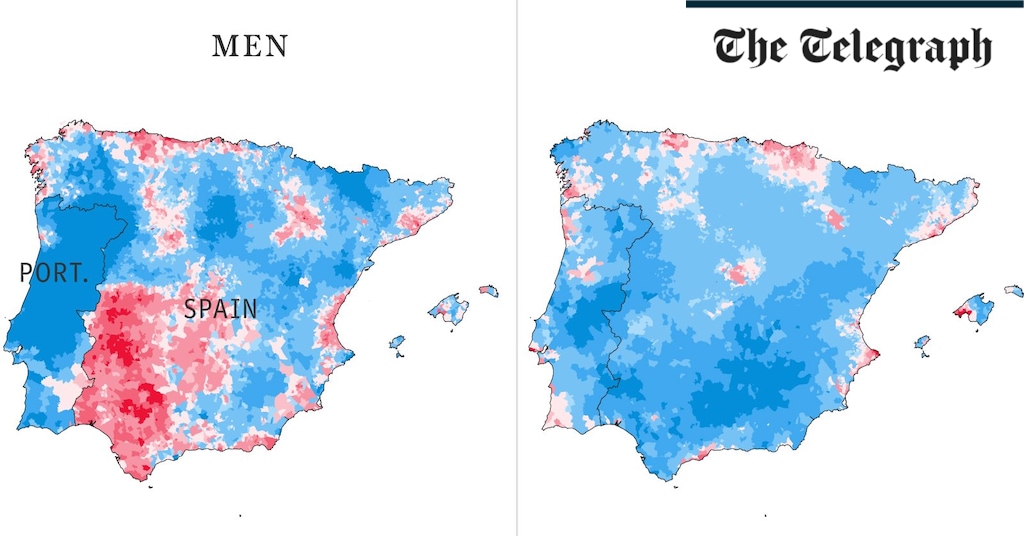
 Health & fitness4 weeks ago
Health & fitness4 weeks agoThe maps that could hold the secret to curing cancer
-
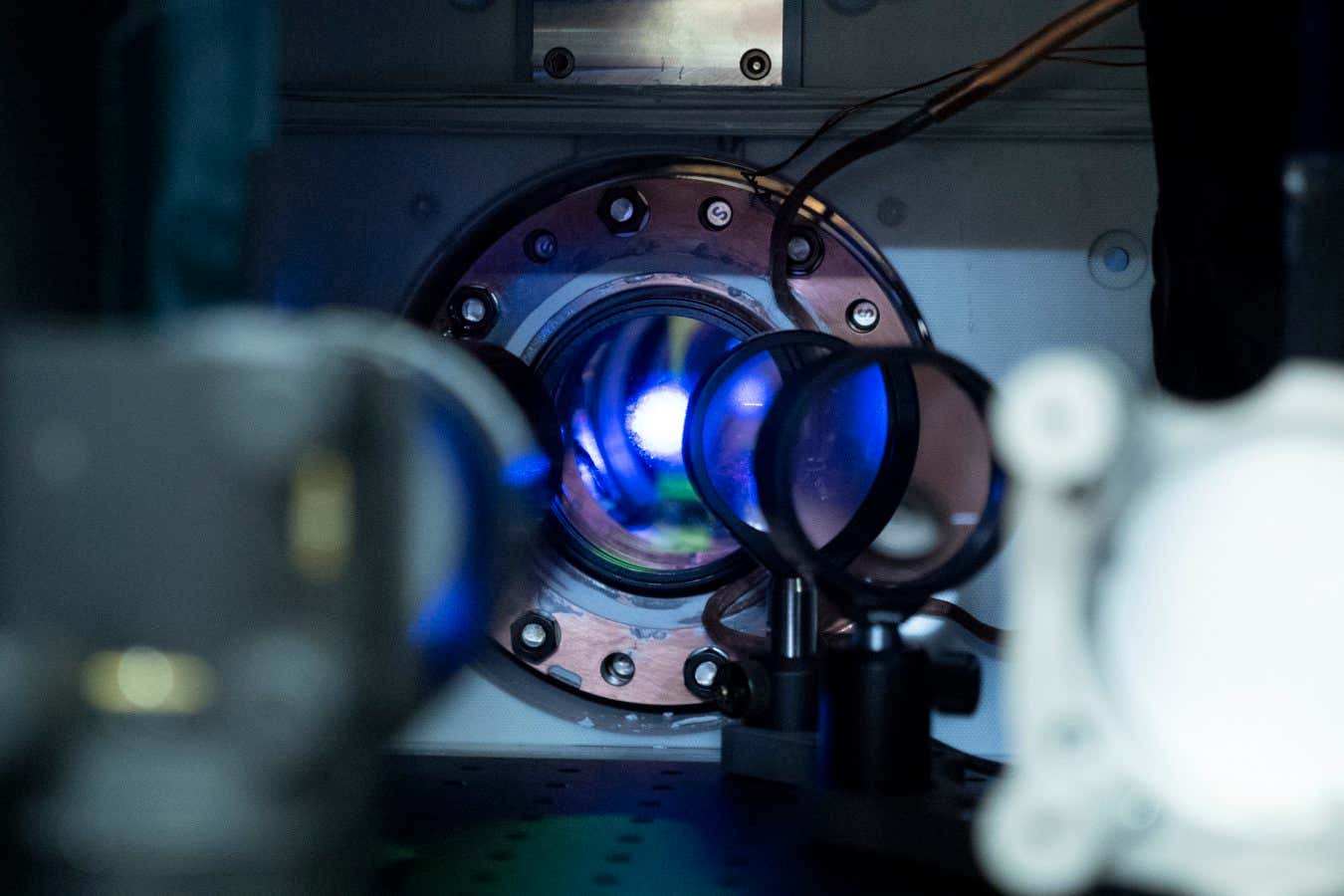
 Science & Environment4 weeks ago
Science & Environment4 weeks agoMost accurate clock ever can tick for 40 billion years without error
-

 CryptoCurrency4 weeks ago
CryptoCurrency4 weeks agoDecentraland X account hacked, phishing scam targets MANA airdrop
-

 CryptoCurrency4 weeks ago
CryptoCurrency4 weeks agoBitcoin miners steamrolled after electricity thefts, exchange ‘closure’ scam: Asia Express
-

 CryptoCurrency4 weeks ago
CryptoCurrency4 weeks agoDZ Bank partners with Boerse Stuttgart for crypto trading
-

 CryptoCurrency4 weeks ago
CryptoCurrency4 weeks agoLow users, sex predators kill Korean metaverses, 3AC sues Terra: Asia Express
-

 CryptoCurrency4 weeks ago
CryptoCurrency4 weeks agoBlockdaemon mulls 2026 IPO: Report
-

 MMA4 weeks ago
MMA4 weeks agoRankings Show: Is Umar Nurmagomedov a lock to become UFC champion?
-

 Womens Workouts4 weeks ago
Womens Workouts4 weeks agoBest Exercises if You Want to Build a Great Physique
-

 Womens Workouts4 weeks ago
Womens Workouts4 weeks agoEverything a Beginner Needs to Know About Squatting
-

 News3 weeks ago
News3 weeks agoFour dead & 18 injured in horror mass shooting with victims ‘caught in crossfire’ as cops hunt multiple gunmen
-

 Servers computers3 weeks ago
Servers computers3 weeks agoWhat are the benefits of Blade servers compared to rack servers?
-

 News4 weeks ago
News4 weeks agoChurch same-sex split affecting bishop appointments
-

 Technology4 weeks ago
Technology4 weeks agoiPhone 15 Pro Max Camera Review: Depth and Reach
-

 News4 weeks ago
News4 weeks agoBrian Tyree Henry on voicing young Megatron, his love for villain roles
-
Business4 weeks ago
JPMorgan in talks to take over Apple credit card from Goldman Sachs
-
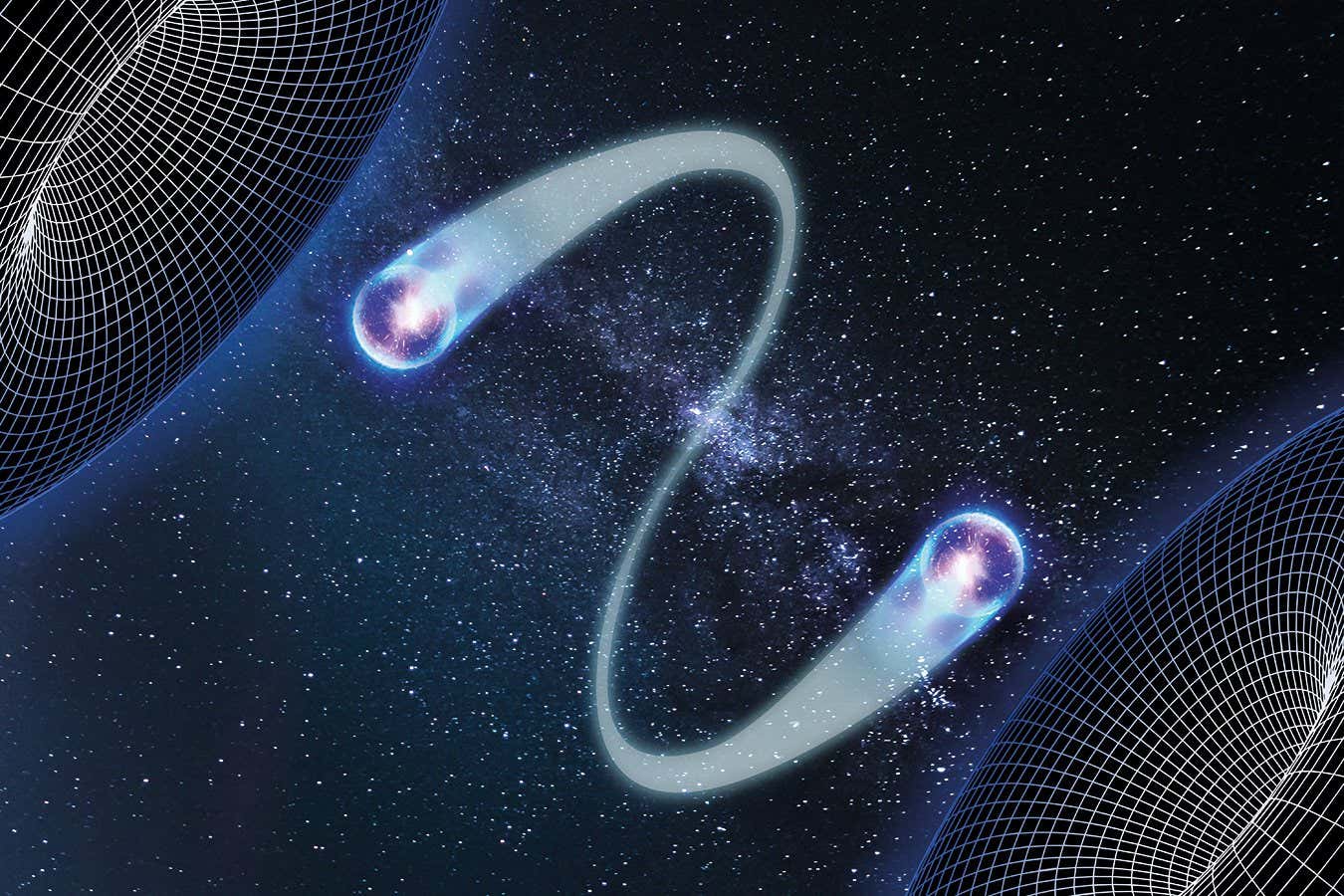
 Science & Environment4 weeks ago
Science & Environment4 weeks agoQuantum time travel: The experiment to ‘send a particle into the past’
-
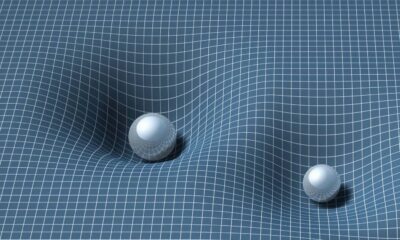
 Science & Environment4 weeks ago
Science & Environment4 weeks agoTiny magnet could help measure gravity on the quantum scale
-
 Science & Environment4 weeks ago
Science & Environment4 weeks agoHow do you recycle a nuclear fusion reactor? We’re about to find out
-
 CryptoCurrency4 weeks ago
CryptoCurrency4 weeks agoDorsey’s ‘marketplace of algorithms’ could fix social media… so why hasn’t it?
-

 CryptoCurrency4 weeks ago
CryptoCurrency4 weeks agoBitcoin bulls target $64K BTC price hurdle as US stocks eye new record
-

 News4 weeks ago
News4 weeks agoBrian Tyree Henry on voicing young Megatron, his love for villain roles







@SHAILESHYADAV-gv6hu
October 13, 2024 at 9:23 am
Very good 👍
@ddubz6356
October 13, 2024 at 9:23 am
does not work
@mincoarmin1260
October 13, 2024 at 9:23 am
You Sir are a life saver
Thanks to you I can work on my mariadb server on my main pc
Thank you
@manideepkumar959
October 13, 2024 at 9:23 am
when both windows and ubuntu are installed on my machine it is working, i am able to connect from my windows machine to my ubuntu machine (where ssh server is installed) , but the same url -when i am trying to connect from diff computer to my ubuntu machine it is saying connection timedout
@peterrchimaa
October 13, 2024 at 9:23 am
You have no idea the miracle you just did…this problem slowed me down when i was learning Ansible…i tried everything..UFW PORT ENABLING just unlocked everything
@3mre_1233
October 13, 2024 at 9:23 am
Good Video, thanks <3
@TylerrTheMasterBaiter
October 13, 2024 at 9:23 am
Where did the command prompt came from ?
@ibrarali4592
October 13, 2024 at 9:23 am
thank you for sharing
Knowledge
@DAYSHIVANSH
October 13, 2024 at 9:23 am
It is saying port 22 connect timed out
@johnali4117
October 13, 2024 at 9:23 am
Does this technique work in NAT? I've noticed that NAT uses different IP address (inet 10.0.2.15/24) while Bridge Adaptor uses 192.168.x.x ip. Also the Ubuntu must be configured to use static IP address. Please comment if this is correct or am I just imagining?
@microsoftskill8191
October 13, 2024 at 9:23 am
❤ thanks i done with your video
@santoshgujar5237
October 13, 2024 at 9:23 am
Thank you, Sir, 🙏🌺😇
@rajankumar_37
October 13, 2024 at 9:23 am
Best guide, pretty straight forward! quality content. thanks
@EpicVideoTime4You
October 13, 2024 at 9:23 am
THANK YOU! Straight to the point <3
@YanaLukomskaya
October 13, 2024 at 9:23 am
It was fast and wonderful! Thank you
@YoungSecurity
October 13, 2024 at 9:23 am
At 00:46, it says, "All commands are in the description." The video description does not contain any commands.
@shaykren7362
October 13, 2024 at 9:23 am
SMAAAAAAAAAAAAAAAAAAAAAAAAAAAASH
@bretthl1
October 13, 2024 at 9:23 am
That was perfect.
@NathanielMujesia
October 13, 2024 at 9:23 am
thanks
@aerobrain2001
October 13, 2024 at 9:23 am
As an enthusiastic but not overly technical dabbler in Linux, I’d always assumed SSH was way beyond me. But thank you for making it look so simple, simple things but put a smile on my face when I logged into my Ubuntu machine from my UnRAID terminal 🙂
Thank you!
@kicksiva5845
October 13, 2024 at 9:23 am
thank you for your guidance. i tried with redhat but its not working for me but ubuntu its working.
@faustoricardo8875
October 13, 2024 at 9:23 am
thanks mate you are the best great video!
@user_hinth
October 13, 2024 at 9:23 am
Thanks a lot for your tutorial. Praise to the Almighty Allah,It's working properly.
@legendshettygaming6113
October 13, 2024 at 9:23 am
What is the password for IP address
@dogbyte7875
October 13, 2024 at 9:23 am
Hey Eloy, thanks for the video, it served as a great refresher. I am not as young as I would like to be, and my memory does not seem to function as it used to. I gave you a like and subscribed. Will join next month, as my finances are limited and fixed (social security). Again, much thanks 😉
@pravin3870
October 13, 2024 at 9:23 am
which password to put after putting our othrr pc IP is that Laptops password or which???
plz help
@nmarks
October 13, 2024 at 9:23 am
Clear, unfussy instructions which worked first time. Thank you very much. Subscribed. 👍
@pablocarballeira4443
October 13, 2024 at 9:23 am
Thank you for the tutorial,but I have a problem, when trying the connection it says "permission denied(publickey)"
I am using latest ubuntu server for arm in a Pi4
@omartusson
October 13, 2024 at 9:23 am
Thank you.
@advocate7643
October 13, 2024 at 9:23 am
Hi, do I have to run these two commands after every time I turn on my server?
@Rahyss
October 13, 2024 at 9:23 am
Thank you 👍🏿
@Mateo-pu7xg
October 13, 2024 at 9:23 am
Thank you
@harsh8135
October 13, 2024 at 9:23 am
and how to do the same for windows
@JustinEckert-fn4nu
October 13, 2024 at 9:23 am
you need to run "sudo systemctl start ssh, then sudo systemctl enable ssh if the status came back as dead (inactive)
@tobios89p13
October 13, 2024 at 9:23 am
What do i do when its inactive(dead)?
@4evrOk4U
October 13, 2024 at 9:23 am
thank,s Done
@blither592
October 13, 2024 at 9:23 am
Hello eloy, half of this video helped me so much with the commands when it comes to ssh for both linux and windows, but I am having some trouble here. So what is the password that we have to put for our ip address? I'm a bit confused
@impliese9983
October 13, 2024 at 9:23 am
thank you
@Okeh189
October 13, 2024 at 9:23 am
not working in mac machine
@pranavvats9439
October 13, 2024 at 9:23 am
thankyou so very much sir
this was sooooo sooo sooooooo helpful
@Chris-nq3ri
October 13, 2024 at 9:23 am
nice dude thx!!
@Valksforge
October 13, 2024 at 9:23 am
So this can be done the other way around “Connect FROM my personal computer Ubuntu terminal TO datacenter SSH Dedicated Server terminal” A full control from my house to the datacenter em I right? Sorry I’m new to this and wanted to learn more 🙏.
@Valksforge
October 13, 2024 at 9:23 am
So this can be done the other way around “Connect FROM my personal computer Ubuntu terminal TO datacenter SSH Dedicated Server terminal” A full control from my house to the datacenter em I right? Sorry I’m new to this and wanted to learn more 🙏.
@luciano5026
October 13, 2024 at 9:23 am
Thank you
@KnowledgeSharingTech
October 13, 2024 at 9:23 am
For more tutorials, subscribe to my channel, it really makes a difference 💗: https://www.youtube.com/knowledgesharingtech?sub_confirmation=1