Technology
Why MFA alone won’t protect you in the age of adversarial AI

Join our daily and weekly newsletters for the latest updates and exclusive content on industry-leading AI coverage. Learn More
For a long time, multi-factor authentication (MFA) — in the way of push notifications, authenticator apps or other secondary steps — was thought to be the answer to the mounting cybersecurity problem.
But hackers are cunning and crafty and come up with new ways all the time to break through the fortress of MFA.
Today’s enterprises need even stronger defenses — while experts say MFA is still critical, it should be just a small piece of the authentication process.
“Traditional MFA methods, such as SMS and push notifications, have proven to be vulnerable to various attacks, making them nearly as susceptible as passwords alone,” said Frank Dickson, group VP for security and trust at IDC. “The growing prevalence of sophisticated threats requires a move towards stronger authentication methods.”
Why isn’t MFA enough?
The once tried-and-true practice of relying on passwords now seems quaint.
No matter what string of numbers, letters, special characters or numbers they comprised, they became so easy to steal as users were careless, lazy, gullible or overtrusting.
“Traditional passwords are simply shared secrets, not much more advanced than a Roman sentry asking for the secret codeword thousands of years ago (‘Halt, who goes there? What’s the passcode?),” said Lou Steinberg, founder and managing partner at CTM insights.
As Matt Caulfield, VP of product for identity security at Cisco, told VentureBeat: “As soon as those were stolen, it was game over.”
MFA became more mainstream in the mid-1990s to 2000s as more enterprises went online, and it seemed a solution to traditional passwords. But with digital transformation, the shift to the cloud, and the adoption of dozens or even hundreds of SaaS apps, enterprises are more vulnerable than ever. They no longer safely hide away behind firewalls and data centers. They lack control and transparency.
“MFA changed the game for a long time,” said Caulfield. “But what we’ve found over the past 5 years with these recent identity attacks is that MFA can easily be defeated.”
One of the greatest threats to MFA is social engineering or more personalized psychological tactics. Because people put so much of themselves online — via social media or LinkedIn — attackers have free reign to research anyone in the world.
Thanks to increasingly sophisticated AI tools, stealthy threat actors can craft campaigns “at mass scale,” said Caulfield. They will initially use phishing to access a user’s primary credential, then employ AI-based outreach to trick them into sharing a second credential or take action that allows attackers into their account.
Or, attackers will spam the secondary MFA SMS or push notification method causing “MFA fatigue,” when the user eventually gives in and pushes “allow.” Threat actors will also prime victims, making situations seem urgent, or fool them into thinking they’re getting legitimate messages from an IT help desk.
With man-in-the-middle attacks, meanwhile, an attacker can intercept a code during transmission between user and provider. Threat actors may also deploy tools that mirror login pages, tricking users into providing both their passwords and MFA codes.
Enter passwordless
The downfalls of MFA have prompted many enterprises to adopt passwordless methods such as passkeys, device fingerprinting, geolocation or biometrics.
With passkeys, users are authenticated through cryptographic security “keys” stored on their computer or device, explained Derek Hanson, VP of standards and alliances at Yubico, which manufactures the widely-used YubiKey device.
Each party must provide evidence of their identity and communicate their intention to initiate authentication. Users can sign into apps and websites with a biometric sensor (such as a fingerprint or facial recognition), PIN or pattern.
“Users are not required to recall or manually enter long sequences of characters that can be forgotten, stolen or intercepted,” said Hanson. This reduces the burden on users to make the right choices and not hand over their credentials during a phishing attempt.
“Approaches like device fingerprinting or geolocation can supplement traditional MFA,” explained Anders Aberg, director of passwordless at Bitwarden. “These methods adjust security requirements based on user behavior and context — such as location, device or network — reducing friction while maintaining high security.”
The tandem use of devices and biometrics is on the rise, Caulfield agreed. At initial sign-in and verification, the user shows their face along with physical identification such as a passport or driver’s license, and the system performs 3D mapping, which is a sort of “liveness check.” Once photo IDs are confirmed with government databases, the system will then register the device and fingerprint or other biometrics.
“You have the device, your face, your fingerprint,” said Caulfield. “The device trust piece is much more prevalent as the new silver bullet for preventing phishing and AI-based phishing attacks. I call it the second wave of MFA. The first wave was the silver bullet until it wasn’t.”
However, these methods aren’t completely foolproof, either. Hackers can get around biometrics tools by using deepfakes or by simply stealing a photo of the legitimate user.
“Biometrics are stronger than passwords, but once compromised they are impossible to change,” said Steinberg. “You can change your password if needed, but did you ever try to change your fingerprint?”
Leveraging analytics, creating a failsafe
Caulfield pointed out that organizations are incorporating analytics tools and amassing mountains of data — yet they’re not putting it to use to bolster their cybersecurity.
“These tools generate a ton of telemetry,” said Caulfield, such as who is signing in, from where and on what device. But they’re then “sending that all into a black hole.”
Advanced analytics can help with identity threat detection and analytics, even if after the fact to provide a “stopgap or failsafe” when attackers bypass MFA, he said.
Ultimately, enterprises must have a fail-safe strategy, agreed Ameesh Divatia, co-founder and CEO at data privacy company Baffle. Personally identifiable information (PII) and other confidential data must be cryptographically protected (masked, tokenized or encrypted).
“Even if you have a data breach, cryptographically protected data is useless to an attacker,” said Divatia. In fact, GDPR and other data privacy laws don’t require companies to notify affected parties if cryptographically protected data gets leaked, because the data itself is still secure, he pointed out.
“Fail safe just means that when one or more of your cybersecurity defenses fail, then your data is still secure,” said Divatia.
There’s a reason it’s called ‘multifactor’
Still, that’s not to say that MFA is completely going away.
“In the entire scheme of things, the hierarchy of authentication starts with MFA, as weak MFA is still better than not having it at all, and that shouldn’t be overlooked,” said Dickson.
As Caulfield pointed out, it’s called multi-factor authentication for a reason — “multi” can mean anything. It can ultimately be a mix of passwords, push notifications, fingerprint scans, physical possession of a device, biometrics or hardware and RSA tokens (and whatever evolves next).
“MFA is here to stay, it’s just the definition now is ‘How good is your MFA’? Is it basic, mature or optimized?,” he said. However, in the end, he emphasized: “There’s never going to be a single factor that in and of itself is completely secure.”
Source link
Servers computers
rackmount servers – windows server
Technology
NYT Mini Crossword today: puzzle answers for Saturday, October 5


The New York Times has introduced the next title coming to its Games catalog following Wordle’s continued success — and it’s all about math. Digits has players adding, subtracting, multiplying, and dividing numbers. You can play its beta for free online right now.
In Digits, players are presented with a target number that they need to match. Players are given six numbers and have the ability to add, subtract, multiply, or divide them to get as close to the target as they can. Not every number needs to be used, though, so this game should put your math skills to the test as you combine numbers and try to make the right equations to get as close to the target number as possible.
Players will get a five-star rating if they match the target number exactly, a three-star rating if they get within 10 of the target, and a one-star rating if they can get within 25 of the target number. Currently, players are also able to access five different puzzles with increasingly larger numbers as well. I solved today’s puzzle and found it to be an enjoyable number-based game that should appeal to inquisitive minds that like puzzle games such as Threes or other The New York Times titles like Wordle and Spelling Bee.
In an article unveiling Digits and detailing The New York Time Games team’s process to game development, The Times says the team will use this free beta to fix bugs and assess if it’s worth moving into a more active development phase “where the game is coded and the designs are finalized.” So play Digits while you can, as The New York Times may move on from the project if it doesn’t get the response it is hoping for.
Digits’ beta is available to play for free now on The New York Times Games’ website
Technology
How to disable Google Assistant on your Pixel Watch 3
One of the best things about Wear OS smartwatches these days is the Google Assistant integration and that goes for the Google Pixel Watch 3 as well. However, if for whatever reason you decide you don’t want to use this incredibly useful feature, just know that you can actually disable it. In fact, turning off Google Assistant on your Pixel Watch 3 is pretty simple. If you aren’t sure how to disable it and you want some help, that’s what this handy little guide is here for.
We’ll walk you through the steps to disable Google Assistant if you decide you simply don’t want it to be active. I would be remiss if I didn’t mention that in doing so, you’ll be crippling the watch a little bit. After all, smartwatches are, among other things, meant to give you a hands-free way to interact with tons of smart features. Things you maybe can’t do with your phone because your hands are full. Nevertheless, it’s understandable that not everyone will want to use Google Assistant on their watch. And if you aren’t using it, then there’s not much of a reason for it to be enabled.
It’s also worth mentioning that you can always enable it again if you change your mind. So with that said, let’s dive in.
How to disable Google Assistant on your Pixel Watch 3
![]()
Bring up the quick settings menu
You’ll want to start by bringing up the quick settings menu. The watch will walk you through how to get to this upon your first time setting it up. Just in case you forgot though, you simply need to swipe down from the top edge of the display to bring up the quick settings menu.
Tap on settings
Now tap on the settings tile. The settings tile is the button that looks like a little gear icon. Just like on your Android smartphone.
![]()
Scroll down to the Google menu
When you open the settings menu, it should put you right at the top, with “connectivity” being the first sub-menu you can open. Scroll down a bit, either by using your finger or the haptic crown, and look for the “Google” sub-menu. Tap on that.
![]()
Tap on “Assistant”
This will be the first option in the Google sub-menu. Tap on Assistant to see a handful of options you can enable or disable.
![]()
Scroll down and tap on “Turn off Assistant”
In this menu scroll all the way down to the bottom and tap on the button that says “Turn off Assistant.” This will give you a tiny disclaimer about what will happen and what you won’t be able to do if you disable this feature. Now tap on the “Turn Off” button That’s pretty much it. Now it’ll be disabled.
Alternatively, there are some other ways to lessen the Google Assistant interaction if you don’t want to turn it off completely.
Turn off the wake word
If you still want to use Google Assistant on your Pixel Watch 3, but don’t want the wake word to be active, you can turn this off to limit the interaction so that it won’t activate without you manually trying to engage the Assistant. In the same menu where you disabled the Google Assistant feature, there are three other toggles you can play with. The first one is to turn off the Hey Google wake word. If you disable this toggle, then you won’t be able to activate the Assistant when saying this.
It also means that it won’t randomly activate anytime something that sounds remotely similar is said. This doesn’t happen often, but it can happen. If you do turn this off, you’ll want to make sure that the toggle just below this is turned on. This toggle controls pressing and holding the side button to bring up Google Assistant. You can disable this as well and still use the Google Assistant feature. However, you’ll now have to access it by opening the app drawer and tapping on the Assistant app. That might be preferrable to you, but if you want ease of use, leave this toggle enabled.
Servers computers
The Dell EMC PowerEdge R540 Rack Server
Technology
Samsung’s One UI now covers all of its consumer devices, including TVs and appliances

Samsung will begin using the One UI name for all its consumer devices, now including TVs and home appliances. Executive Vice President Sally Hyesoon Jeong made the announcement at the company’s 2024 developer conference (via 9to5Google). The One UI branding was previously exclusive to its Galaxy phones, tablets and wearables.
“One UI now goes beyond mobile as the software experience for all Samsung consumer devices,” Hyesoon Jeong said onstage at the San Jose keynote. It’s part of the company’s aim for more cohesive branding across its consumer ecosystem, especially as its AI approach evolves.
Samsung also teased that its next software user experience, One UI 7, will arrive with the 2025 batch of Galaxy S phones. “One UI 7 will bring a fresh, new look to the entire interface,” Hyesoon Jeong said at the conference. She laid out three goals for the upcoming software: simple (with a purpose), impactful (leaving a “signature impression”), and emotive design that elicits a human reaction from the user.
The Samsung VP says the One UI 7 home screen grid represents the more focused design principles. “It’s sleeker and easier to use, giving you a neat home screen no matter which Galaxy device you’re using,” said Hyesoon Jeong.
Although you’ll have to wait until early next year for One UI 7, the company said a developer beta will be available to test-drive by the end of this year.
Servers computers
Compaq 9000 series 42u rack cabinet

This is the said updated video of my full 42u cabinet, allthough I still don’t have UPS unit batteries. Sorry for the video choppiness and such, it’s my Cannon Power Shot digital still camera’s video mode. only does 30FPS. I don’t use my DV cam, since I’ve had too many issues with synching the video and sound when ripping over firewire. .
source
-

 Womens Workouts2 weeks ago
Womens Workouts2 weeks ago3 Day Full Body Women’s Dumbbell Only Workout
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoHow to unsnarl a tangle of threads, according to physics
-
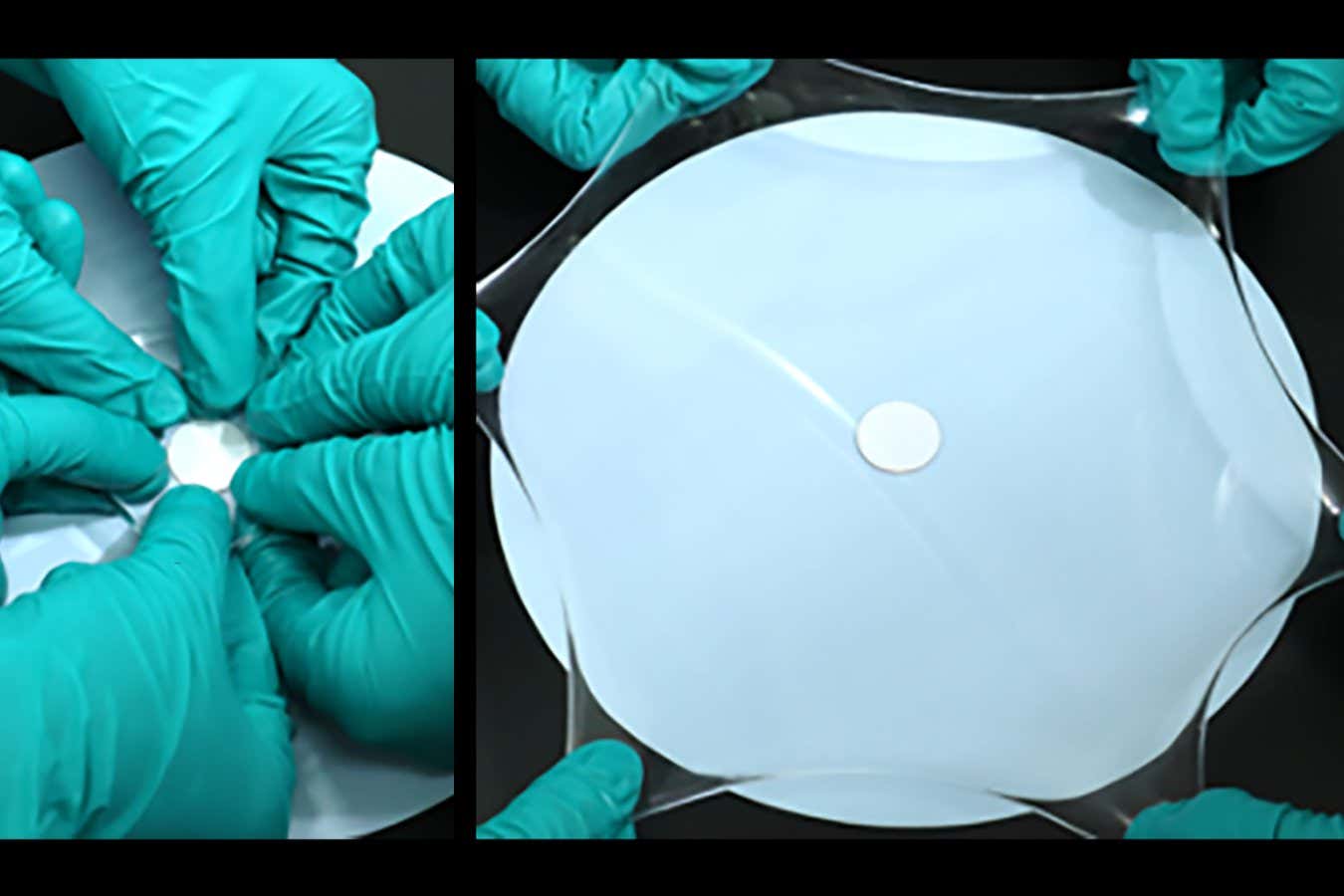
 Science & Environment2 weeks ago
Science & Environment2 weeks agoHyperelastic gel is one of the stretchiest materials known to science
-

 Technology2 weeks ago
Technology2 weeks agoWould-be reality TV contestants ‘not looking real’
-

 Science & Environment2 weeks ago
Science & Environment2 weeks ago‘Running of the bulls’ festival crowds move like charged particles
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoMaxwell’s demon charges quantum batteries inside of a quantum computer
-

 News2 weeks ago
News2 weeks agoOur millionaire neighbour blocks us from using public footpath & screams at us in street.. it’s like living in a WARZONE – WordupNews
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoHow to wrap your mind around the real multiverse
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoSunlight-trapping device can generate temperatures over 1000°C
-
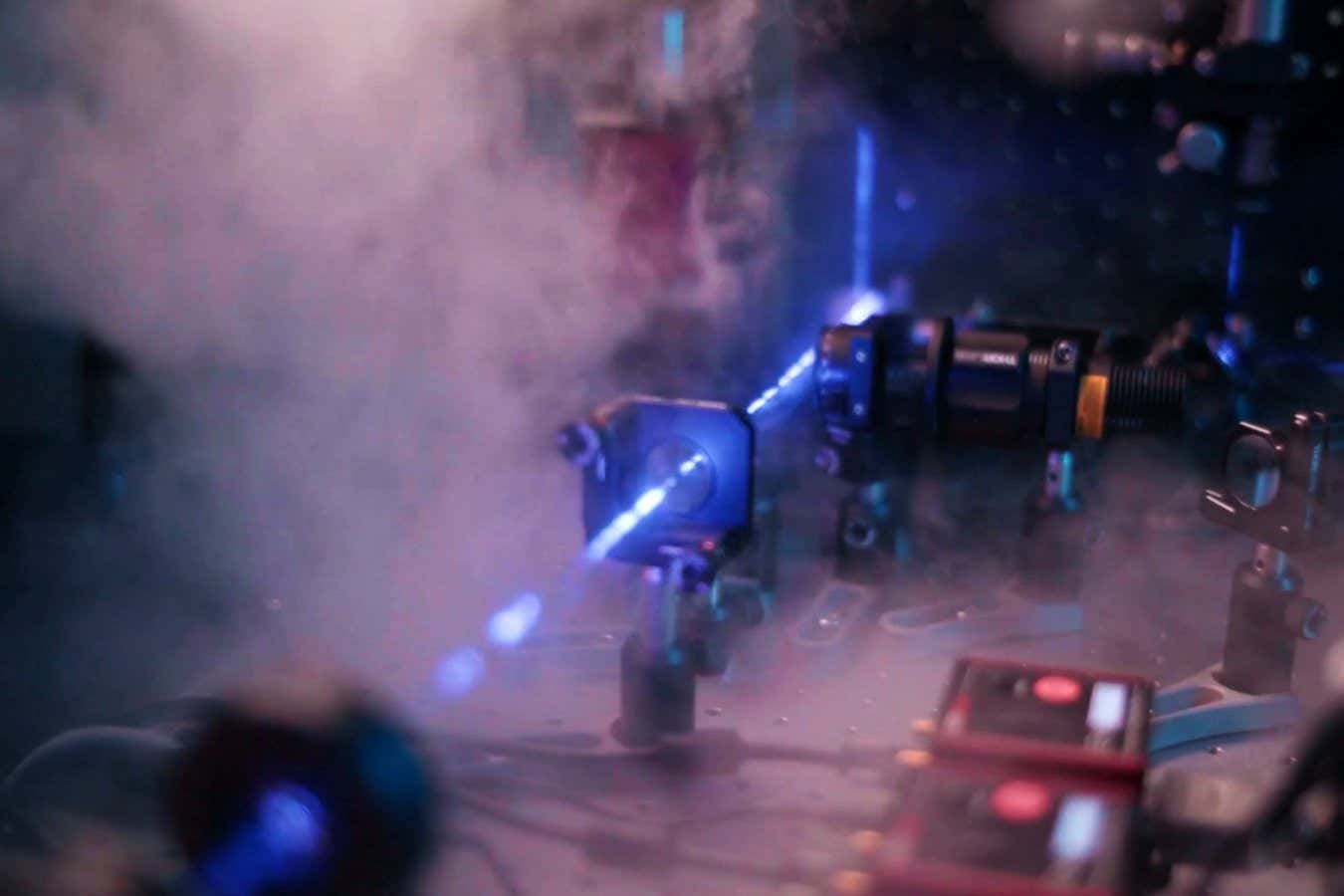
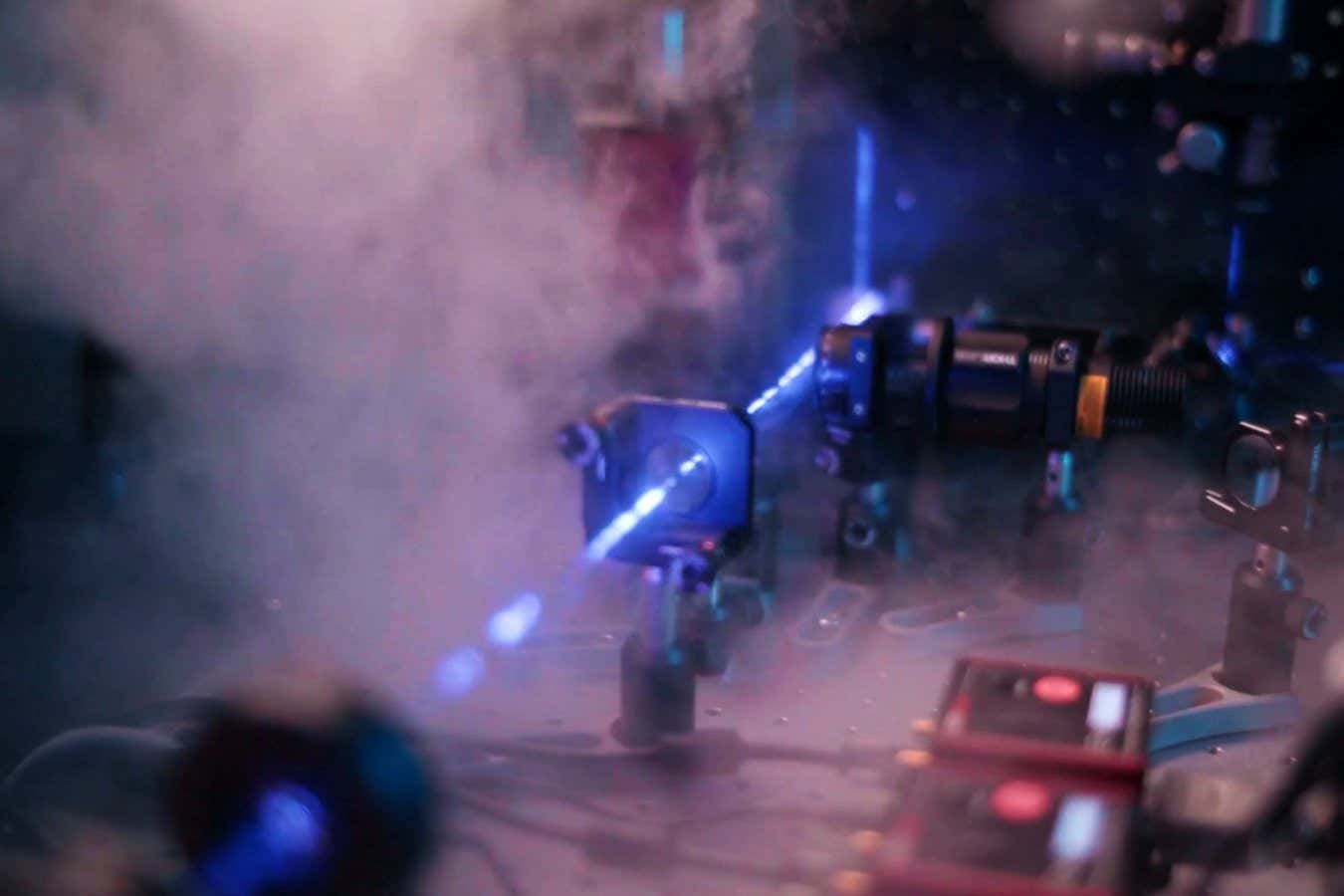 Science & Environment2 weeks ago
Science & Environment2 weeks agoLiquid crystals could improve quantum communication devices
-
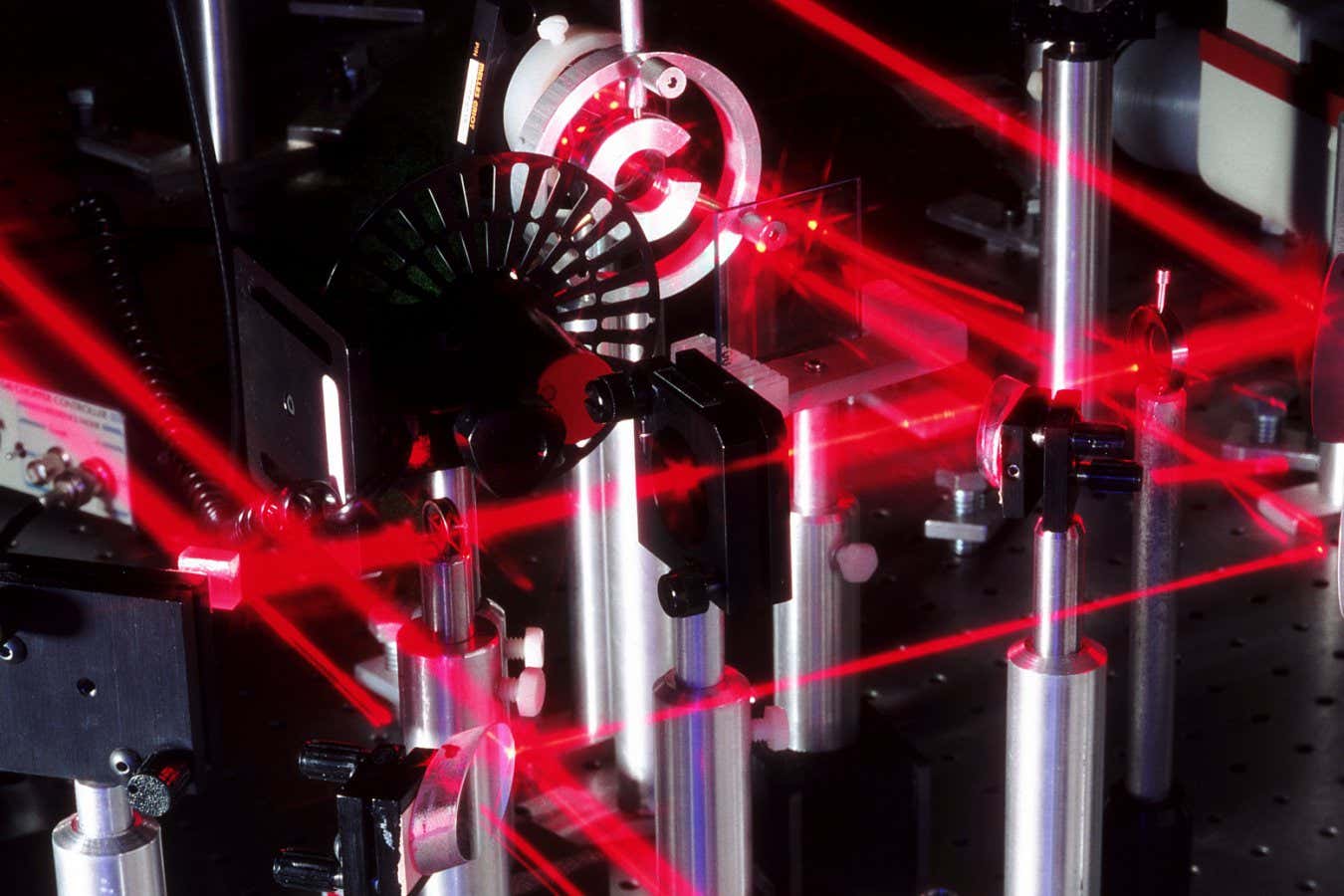
 Science & Environment2 weeks ago
Science & Environment2 weeks agoQuantum ‘supersolid’ matter stirred using magnets
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoITER: Is the world’s biggest fusion experiment dead after new delay to 2035?
-
 Science & Environment2 weeks ago
Science & Environment2 weeks agoPhysicists are grappling with their own reproducibility crisis
-
 Science & Environment2 weeks ago
Science & Environment2 weeks agoQuantum forces used to automatically assemble tiny device
-
 Science & Environment2 weeks ago
Science & Environment2 weeks agoWhy this is a golden age for life to thrive across the universe
-
 News2 weeks ago
News2 weeks agoYou’re a Hypocrite, And So Am I
-
News3 weeks ago
the pick of new debut fiction
-

 Sport2 weeks ago
Sport2 weeks agoJoshua vs Dubois: Chris Eubank Jr says ‘AJ’ could beat Tyson Fury and any other heavyweight in the world
-

 Science & Environment3 weeks ago
Science & Environment3 weeks agoCaroline Ellison aims to duck prison sentence for role in FTX collapse
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoNuclear fusion experiment overcomes two key operating hurdles
-
 Technology7 days ago
Technology7 days ago‘From a toaster to a server’: UK startup promises 5x ‘speed up without changing a line of code’ as it plans to take on Nvidia, AMD in the generative AI battlefield
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoTime travel sci-fi novel is a rip-roaringly good thought experiment
-

 MMA7 days ago
MMA7 days agoConor McGregor challenges ‘woeful’ Belal Muhammad, tells Ilia Topuria it’s ‘on sight’
-
 Science & Environment2 weeks ago
Science & Environment2 weeks agoLaser helps turn an electron into a coil of mass and charge
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoNerve fibres in the brain could generate quantum entanglement
-
Business7 days ago
Eurosceptic Andrej Babiš eyes return to power in Czech Republic
-

 Football7 days ago
Football7 days agoFootball Focus: Martin Keown on Liverpool’s Alisson Becker
-

 News2 weeks ago
News2 weeks agoIsrael strikes Lebanese targets as Hizbollah chief warns of ‘red lines’ crossed
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoUK spurns European invitation to join ITER nuclear fusion project
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoCardano founder to meet Argentina president Javier Milei
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoMeet the world's first female male model | 7.30
-

 Science & Environment1 week ago
Science & Environment1 week agoX-rays reveal half-billion-year-old insect ancestor
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoRethinking space and time could let us do away with dark matter
-

 News2 weeks ago
News2 weeks ago▶️ Media Bias: How They Spin Attack on Hezbollah and Ignore the Reality
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoA slight curve helps rocks make the biggest splash
-
Business3 weeks ago
JPMorgan in talks to take over Apple credit card from Goldman Sachs
-

 News3 weeks ago
News3 weeks ago▶️ Hamas in the West Bank: Rising Support and Deadly Attacks You Might Not Know About
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoFuture of fusion: How the UK’s JET reactor paved the way for ITER
-

 Womens Workouts2 weeks ago
Womens Workouts2 weeks agoBest Exercises if You Want to Build a Great Physique
-

 News2 weeks ago
News2 weeks agoWhy Is Everyone Excited About These Smart Insoles?
-

 News2 weeks ago
News2 weeks agoFour dead & 18 injured in horror mass shooting with victims ‘caught in crossfire’ as cops hunt multiple gunmen
-
 Technology2 weeks ago
Technology2 weeks agoRobo-tuna reveals how foldable fins help the speedy fish manoeuvre
-
Business7 days ago
Should London’s tax exiles head for Spain, Italy . . . or Wales?
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoEthereum is a 'contrarian bet' into 2025, says Bitwise exec
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoA new kind of experiment at the Large Hadron Collider could unravel quantum reality
-

 Health & fitness2 weeks ago
Health & fitness2 weeks agoThe secret to a six pack – and how to keep your washboard abs in 2022
-
 Science & Environment2 weeks ago
Science & Environment2 weeks agoQuantum time travel: The experiment to ‘send a particle into the past’
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoWhy we need to invoke philosophy to judge bizarre concepts in science
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoBitcoin miners steamrolled after electricity thefts, exchange ‘closure’ scam: Asia Express
-
 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoDorsey’s ‘marketplace of algorithms’ could fix social media… so why hasn’t it?
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoDZ Bank partners with Boerse Stuttgart for crypto trading
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoLow users, sex predators kill Korean metaverses, 3AC sues Terra: Asia Express
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoBitcoin bulls target $64K BTC price hurdle as US stocks eye new record
-

 Womens Workouts2 weeks ago
Womens Workouts2 weeks agoEverything a Beginner Needs to Know About Squatting
-

 Womens Workouts2 weeks ago
Womens Workouts2 weeks ago3 Day Full Body Toning Workout for Women
-

 Travel2 weeks ago
Travel2 weeks agoDelta signs codeshare agreement with SAS
-

 Servers computers1 week ago
Servers computers1 week agoWhat are the benefits of Blade servers compared to rack servers?
-

 Politics1 week ago
Politics1 week agoHope, finally? Keir Starmer’s first conference in power – podcast | News
-

 Technology7 days ago
Technology7 days agoThe best robot vacuum cleaners of 2024
-

 Sport2 weeks ago
Sport2 weeks agoUFC Edmonton fight card revealed, including Brandon Moreno vs. Amir Albazi headliner
-

 Technology2 weeks ago
Technology2 weeks agoiPhone 15 Pro Max Camera Review: Depth and Reach
-

 News2 weeks ago
News2 weeks agoBrian Tyree Henry on voicing young Megatron, his love for villain roles
-
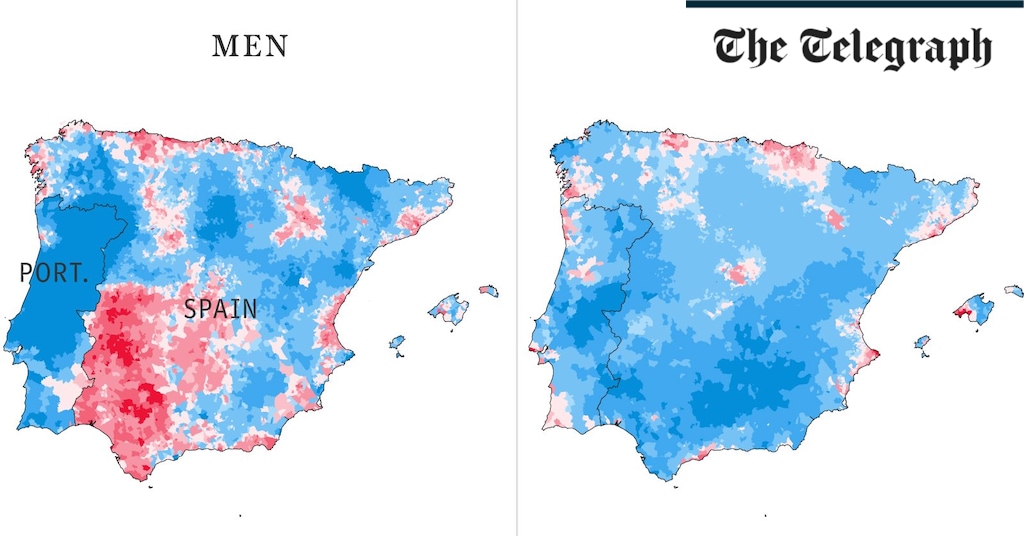
 Health & fitness2 weeks ago
Health & fitness2 weeks agoThe maps that could hold the secret to curing cancer
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoBeing in two places at once could make a quantum battery charge faster
-

 News3 weeks ago
News3 weeks agoNew investigation ordered into ‘doorstep murder’ of Alistair Wilson
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoRedStone integrates first oracle price feeds on TON blockchain
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoBlockdaemon mulls 2026 IPO: Report
-
 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoCoinbase’s cbBTC surges to third-largest wrapped BTC token in just one week
-
Politics2 weeks ago
UK consumer confidence falls sharply amid fears of ‘painful’ budget | Economics
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoCNN TÜRK – 🔴 Canlı Yayın ᴴᴰ – Canlı TV izle
-

 News1 week ago
News1 week agoUS Newspapers Diluting Democratic Discourse with Political Bias
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoHow one theory ties together everything we know about the universe
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoCrypto scammers orchestrate massive hack on X but barely made $8K
-
 Science & Environment2 weeks ago
Science & Environment2 weeks agoTiny magnet could help measure gravity on the quantum scale
-
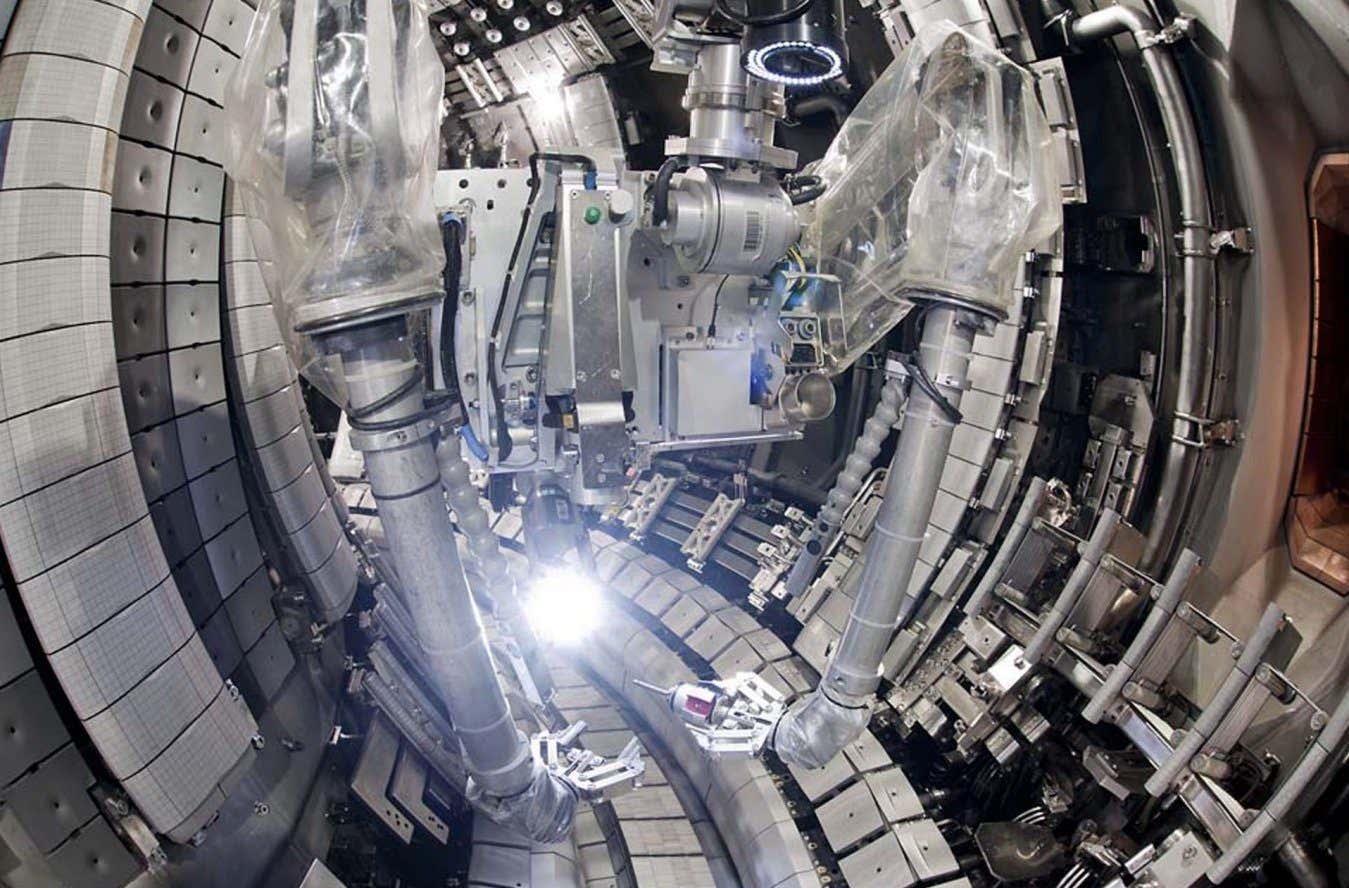
 Science & Environment2 weeks ago
Science & Environment2 weeks agoHow do you recycle a nuclear fusion reactor? We’re about to find out
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoDecentraland X account hacked, phishing scam targets MANA airdrop
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoTelegram bot Banana Gun’s users drained of over $1.9M
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoVonMises bought 60 CryptoPunks in a month before the price spiked: NFT Collector
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoSEC asks court for four months to produce documents for Coinbase
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks ago‘Silly’ to shade Ethereum, the ‘Microsoft of blockchains’ — Bitwise exec
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks ago‘No matter how bad it gets, there’s a lot going on with NFTs’: 24 Hours of Art, NFT Creator
-
Business2 weeks ago
Thames Water seeks extension on debt terms to avoid renationalisation
-
Business2 weeks ago
How Labour donor’s largesse tarnished government’s squeaky clean image
-
Politics2 weeks ago
‘Appalling’ rows over Sue Gray must stop, senior ministers say | Sue Gray
-

 News2 weeks ago
News2 weeks agoBrian Tyree Henry on voicing young Megatron, his love for villain roles
-

 Womens Workouts2 weeks ago
Womens Workouts2 weeks agoHow Heat Affects Your Body During Exercise
-

 Womens Workouts2 weeks ago
Womens Workouts2 weeks agoKeep Your Goals on Track This Season
-

 TV2 weeks ago
TV2 weeks agoCNN TÜRK – 🔴 Canlı Yayın ᴴᴰ – Canlı TV izle
-

 News2 weeks ago
News2 weeks agoChurch same-sex split affecting bishop appointments
-

 Politics2 weeks ago
Politics2 weeks agoTrump says he will meet with Indian Prime Minister Narendra Modi next week
-

 Technology2 weeks ago
Technology2 weeks agoFivetran targets data security by adding Hybrid Deployment
-
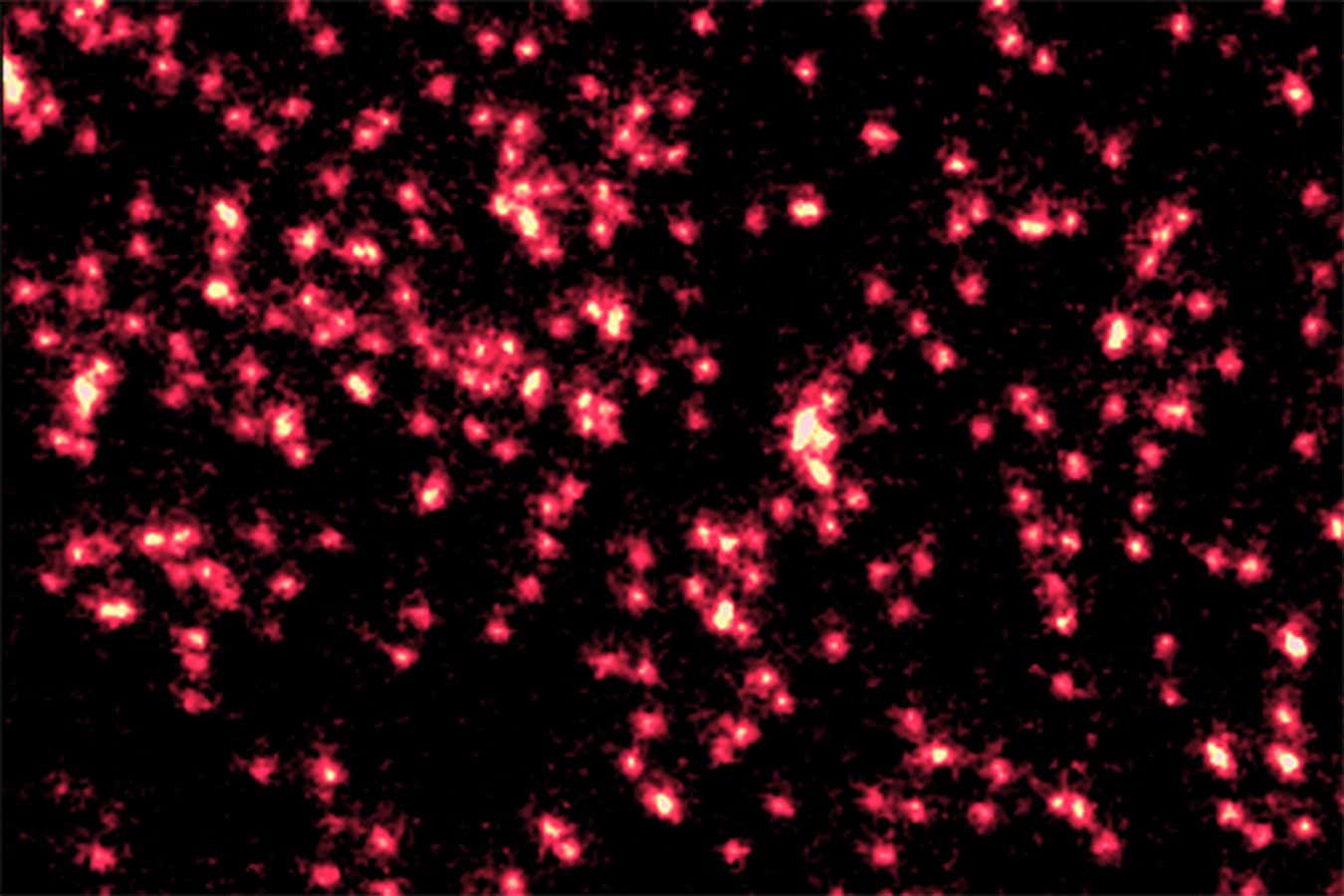
 Science & Environment2 weeks ago
Science & Environment2 weeks agoSingle atoms captured morphing into quantum waves in startling image
-

 Politics2 weeks ago
Politics2 weeks agoLabour MP urges UK government to nationalise Grangemouth refinery
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoLouisiana takes first crypto payment over Bitcoin Lightning
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks ago$12.1M fraud suspect with ‘new face’ arrested, crypto scam boiler rooms busted: Asia Express
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoA tale of two mysteries: ghostly neutrinos and the proton decay puzzle
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoBitcoin price hits $62.6K as Fed 'crisis' move sparks US stocks warning
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoCertiK Ventures discloses $45M investment plan to boost Web3
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoBeat crypto airdrop bots, Illuvium’s new features coming, PGA Tour Rise: Web3 Gamer
-

 CryptoCurrency2 weeks ago
CryptoCurrency2 weeks agoVitalik tells Ethereum L2s ‘Stage 1 or GTFO’ — Who makes the cut?


You must be logged in to post a comment Login