Technology
Why Microsoft’s Security Initiative and Apple’s Cloud Privacy Matter

Join our daily and weekly newsletters for the latest updates and exclusive content on industry-leading AI coverage. Learn More
With cyber threats growing more automated and malicious, securing enterprise data and privacy has never been more challenging. Apple and Microsoft‘s new security initiatives capitalize on their core cloud security and privacy strengths to close security gaps and reduce risk for every business.
Microsoft’s Secure Future Initiative (SFI) and Apple’s Private Cloud Compute (PCC) represent the latest enterprise-ready approaches to improving cloud security and privacy. The larger the enterprise, the more diverse its cybersecurity and privacy needs, so SFI and PCC are designed to deliver real-time responses at scale.
Microsoft first unveiled the Secure Future Initiative (SFI) in Nov. 2023 to enhance its clients’ enterprise cloud security infrastructure. SFI’s goal is to deliver step-wise improvements in security across the Microsoft ecosystem. The company recently published its Secure Future Initiative Progress Report.
Apple launched its Private Cloud Compute (PCC) platform in June 2024. The PCC is a cloud intelligence system created specifically for private AI processing. Apple’s device-level security and privacy architecture is core to PCC and extended to cloud-based AI operations. One of the PCC’s primary design goals is to keep cloud-processed user data private. This is done with custom silicon, a hardened OS and privacy-preserving methods that manage data requests without storing data.
Microsoft’s Secure Future Initiative (SFI) is a multi-layered defense for enterprise security
At its foundation, SFI is designed to embed security into every layer of Microsoft products and services as part of its secure-by-design framework and more broadly speaking, a new security philosophy.
Microsoft’s Executive Vice President Takeshi Numoto recently said, “At Microsoft, security is our top priority, and through SFI, we ensure that our products and AI systems are secure, private and safe.” Microsoft reaffirmed its commitment to TrustWorthy AI with an announcement this week emphasizing responsible development and deployment of AI technologies.
Six engineering pillars form the foundation of Microsoft’s Secure Future Initiative (SFI) strategy. These pillars are designed to protect systems, data and identities while anticipating cybersecurity threats all from a common platform.
Three core principles define SFI. These include secure by design, secure by default and secure operations. Microsoft committed to these in their latest report, saying all product teams will be using these principles and adopting the Microsoft Security Development Lifecycle (SDL) as their development methodology.

Six engineering pillars make up Microsoft SFI:
- Protect identities and secrets. Securing identities is a critical focus of SFI, especially after the rise in identity-based breaches targeting Active Directory (AD), looking to take control of all identities in a company. Microsoft looks to significantly reduce enterprise identity-related attack surfaces by introducing phishing-resistant credentials and video-based identity verification.
- Protect tenants and isolate production systems. Microsoft designed SFI to strengthen network security by isolating production environments and improving compliance tracking. Also designed in are more stringent isolation policies across virtual networks and production systems to help prevent lateral movement of threats. Microsoft also vows to provide enhanced monitoring to ensure potential threats are identified and acted on quickly.
- Protect Networks. Core to SFI is improved monitoring of virtual networks by recording all assets in a central inventory and ensuring isolation between corporate and production networks. The teams who architected SFI are placing a high priority on enforcing micro-segmentation and minimizing the attack surface. A core construct of this area of SFI is that it ensures lateral movement within the network is limited and controlled, limiting the blast radius of a potential attack.
- Protect Engineering Systems. SFI’s architects chose to rely on the Zero Trust framework to protect Microsoft’s software development environments. Central to this approach is limiting the lifespan of personal access tokens and enforcing stringent checks during code development. Microsoft’s SFI contends that these measures help prevent unauthorized access and protect critical resources during the software development lifecycle.
- Monitor and Detect Threats. Real-time threat detection is the cornerstone of SFI. Microsoft’s SFI framework aims to enable all production systems to emit standardized security logs, providing timely visibility into network activities. This centralized logging enables faster identification of threats and helps enterprises proactively monitor malicious activities.
- Accelerate Response and Remediation. SFI also reduces threat identification and action time to address vulnerabilities quickly. Microsoft publishes critical vulnerabilities (CVEs) regardless of customer action, helping the industry adopt mitigation strategies faster. This proactive approach boosts cloud ecosystem security.
Apple’s Private Cloud Compute (PCC) has privacy at the core
While Microsoft concentrates on closing the gaps it sees across the cloud and entering infrastructure, Apple’s Private Cloud Compute (PCC) capitalizes on the company’s decades of R&D experience in privacy.
Apple invested years of research and development in PCC, looking to create a stateless architecture that could ensure the privacy of customers’ data at the silicon level, making it impossible for an insider attack inside the company to breach it.
Of the many design goals that define the PCC, one of the most important is scaling Apple’s industry-leading device privacy controls into cloud-based AI services. Apple’s central goal is to set a new standard for secure cloud intelligence.
Key features of PCC include the following:
- Stateless computation and enforceable privacy: PCC employs a unique stateless architecture that ensures sensitive data is processed only for its intended purpose and never retained after a process is complete. The stateless architecture is built on hardware-backed secure enclaves and cryptographic protocols to ensure data confidentiality during processing. PCC’s memory is non-persistent, with all data cryptographically erased upon request completion.
- No privileged access: PCC implemented a zero-trust model that prevents any privileged access that could potentially bypass privacy controls. Apple achieves this by using a combination of hardware-enforced isolation, secure boot processes and code-signing algorithms. PCC is designed with such stringent privileged access that Apple’s site reliability engineers cannot access user data or bypass security measures.
- Verifiable transparency to the log level. Cryptographically signed transparency logs of all software running on PCC nodes are published to enable third-party audits. The transparency logs are also used to verify that the code matches the reviewed software. Apple also provides a Virtual Research Environment for simulating PCC environments and offers bug bounties for discoveries across the entire PCC stack.
- Custom silicon and hardened OS. PCC leverages custom Apple silicon with built-in security features like the Secure Enclave and a hardened subset of iOS and macOS. This ensures that user data is processed in isolated environments with hardware-enforced security boundaries.
- Oblivious HTTP routing: PCC requests go through an independent Oblivious HTTP relay. This hides the request origin, preventing IP address-person correlation.
Apple also designed end-to-end encryption, advanced anonymization techniques to protect data throughout its lifecycle, advanced access controls, and support for multi-factor authentication. The PCC also has real-time threat detection and supports regular security audits and penetration testing. For a thorough analysis of the PCC platform, see VentureBeat’s recent in-depth analysis.
Security and privacy comparison: Microsoft SFI vs. Apple PCC
IT and security teams are too busy to manage another platform. Microsoft and Apple are embedding security into their architectures to reduce this burden.
SFI is how Microsoft is integrating security into Azure and Microsoft 365 at every layer. Hardware-level privacy protections in Apple’s Private Cloud Compute (PCC) boost privacy. Both methods simplify critical security measures to keep teams safe without adding work.
The following comparison is a short guide to help IT and security teams gain insights into the differences between each platform:
Cloud security and threat model
- Apple PCC: Designed for secure AI cloud processing, it aims to prevent data leakage, insider threats, and targeted attacks, with robust measures to ensure privacy and security in cloud environments, according to Apple’s PCC blog post released earlier this year.
- Microsoft SFI: Focuses on reducing the attack surfaces across all Microsoft tenants and production environments, with a specific aim of preventing lateral movement between environments. SFI aligns with Zero Trust, a framework that assumes a breach has already happened and requires continuous verification of user and device identity, regardless of network location. Azure and Microsoft 365 ecosystems are protected by Zero Trust. For more information on the Zero Trust framework see the NIST standard, Special Publication 800-207, which outlines the key principles of Zero Trust Architecture (ZTA).
Cultural Integration
- Apple PCC: Prioritizes privacy through technical design rather than cultural changes. Privacy is embedded in both the hardware (Apple silicon) and software (iOS/macOS), ensuring secure-by-design architecture without needing broad cultural shifts.
- Microsoft SFI: Security is embedded into all operations, from corporate governance to employee evaluations. The Microsoft Cybersecurity Governance Council plays a key role in ensuring risk management is consistent across the company.
Scope and Focus:
- Apple PCC: Focuses on AI privacy in cloud, multi-cloud and hybrid cloud environments. It is designed specifically for businesses seeking security and privacy assurances in AI applications, offering high levels of security for AI processing and data storage.
- Microsoft SFI: Microsoft’s product and services-wide initiative to engrain security into the DNA of every product and service they offer. A comprehensive security framework that spans identity management, governance, employee training, and technical safeguards across its ecosystem, including Azure and Microsoft 365. It aims to secure all layers of its platform and user base.
Technical Implementation:
- Apple PCC: Apple secures its framework with custom server hardware and silicon. Stateless computation reduces risks by not storing data between sessions. AI data privacy is a primary design goal by having an integrated hardware and software design. With privacy protections at its core, Apple’s goal is to make PCC-based AI processing secure.
- Microsoft SFI: Microsoft’s strategy weaves security into every phase of software development through a Secure Development Lifecycle (SDL), ensuring that security measures are incorporated from the design stage to deployment. CodeQL, an automated code analysis tool, meticulously scans for vulnerabilities within the code. Moreover, robust identity protection is guaranteed via MSAL (Microsoft Authentication Library), which oversees secure authentication and token management across various applications and services.
Transparency and Governance:
- Apple PCC: Researchers can audit Apple’s systems and view its AI processing environments in cryptographically signed transparency logs. Accountability allows businesses to evaluate and trust Apple’s AI infrastructure without compromising sensitive data.
- Microsoft SFI: Microsoft’s Secure Future Initiative (SFI) seeks to improve security transparency and cybersecurity across its products and services. Advanced security features like Azure Active Directory Conditional Access and Microsoft Defender for Cloud use machine learning algorithms to detect and respond to threats in real time. The company also launched Cyber Signals to provide threat intelligence insights and a Customer Security Management Office (CSMO) to improve security incident communication. These initiatives are promising, but Microsoft’s handling of critical system flaws and data breaches shows the ongoing challenges of scaling cybersecurity.
Why Microsoft SFI and Apple PCC signal a shift in enterprise security
Realizing that IT and security teams are overstretched already, and no one needs another platform to look after, Microsoft and Apple have taken unique approaches to make security and privacy the core of their DNA.
For many IT and security leaders, these two platforms are overdue. SFI is a strong attempt to change the security of Microsoft DNA at its core. As the first generation of an entirely new era of security, SFI is comprehensive and sets the structure so security can become part of its DNA. Starting with the areas that are the most challenging for IT and security to deal with, SFI takes on the challenges of identity management, governance, and technical safeguards.
Apple’s continual investments in privacy pay dividends in PCC. Their prioritizing AI cloud privacy, and embedding privacy protections directly into silicon and operating system software make them unlike any other platform vendors offering privacy at scale.
Source link
Technology
Threads inherits Instagram’s location tagging feature
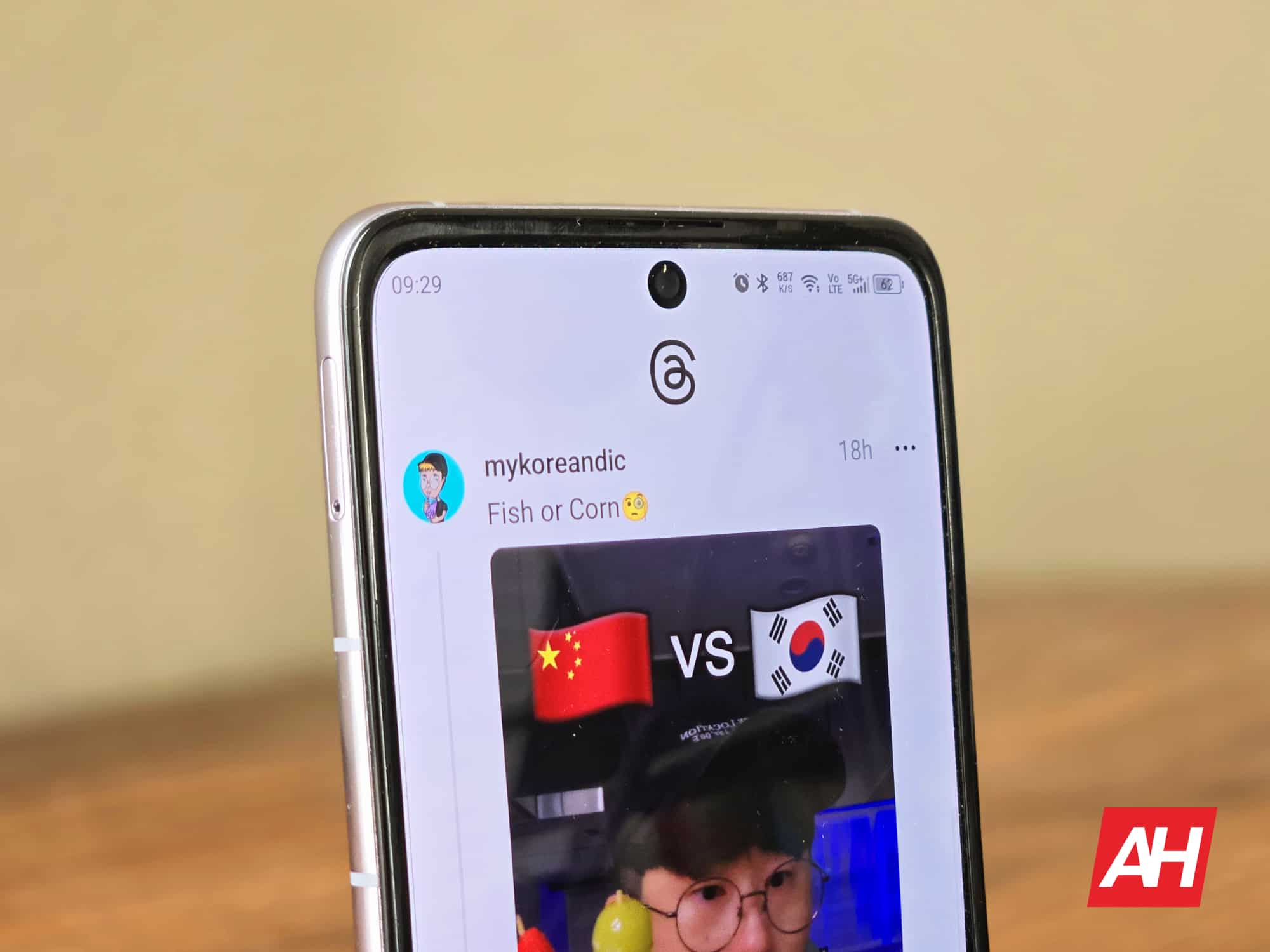
Threads was born as a direct competitor to Twitter (now X) amidst all the controversy over the latter’s management change. Meta already said that it does not intend to turn Threads into another Instagram, so certain features common to modern social networks, like DMs, are not available. However, a seemingly inherited feature from Instagram is now available on Threads: location tagging.
As its name suggests, the new feature allows you to tag the location from which you upload a post. Long-time Instagram users will find this feature quite familiar. Even Facebook (also from Meta) offers a similar option. You can find the option to tag your location from within the Threads post composer.
Meta integrates Instagram’s location tagging into Threads, but without a map
The implementation of the location tagging feature in Threads is a bit less complete than in Instagram. The latter places a “pin” on a map that you can scroll through to see other pinned posts uploaded from that location. However, in Threads, there is no scrollable map with other people’s pins.
Much like on Instagram, you can be more or less specific when tagging your location. You can tag the name of a city, a neighborhood, or even a venue (such as a restaurant). While there isn’t a scrollable map, tapping the location label under the username in a post will show you posts from other users who have tagged that particular location.
For now, the feature appears to be available only in the Threads app for iOS devices. It’s not yet accessible in either the Android app or the web version of Threads. There’s also no official word on when it will be available to everyone. Given Meta’s background regarding the rollout of new features, it’s possible that location tagging is currently available to a percentage of Threads users.
No DMs system in sight for Threads yet
As for other requested features, like DMs, it doesn’t look like they’ll be coming anytime soon. Perhaps the company considers it redundant to offer DMs on Threads and Instagram. After all, Threads originated as an “extension” of Instagram, and the two services even share usernames. So, if you want to send a DM to a Threads user, you can search for them on Instagram. However, the process is a bit cumbersome, and it would be great if the company could make it easier in some way.
Servers computers
Loading a batch of 8x 7.68TB Solidigm P5520 SSDs into a new Supermicro Sapphire Rapids 1U 1P server.
Technology
Three men charged in connection with the Trump campaign hack

The US Department of Justice charged three Iranian nationals as part of an effort to hack into the emails and computers used by President Donald Trump’s campaign staff and other political connections.
The Washington Post reported that DOJ officials filed charges against Masoud Jalili, Seyyed Ali Aghamiri and Yasar Balaghi in an indictment filed Thursday in the US District Court for the District of Columbia. The indictment alleges the three men “prepared for and engaged in a wide-ranging hacking campaign” against current and former US officials, political campaigns and the media.
According to the indictment Jalili, Aghamiri and Balaghi’s “activity is part of Iran’s continuing efforts to […] erode confidence in the US electoral process.” They also face possible charges such as providing material support to a designated foreign terrorist organization, wire fraud and aggravated identity theft.
The suspects are accused of running a targeted hacking campaign committed in Iran over a four-year period. Their victims include current and former officials with the US State Department, the Central Intelligence Agency, the US Ambassador to Israel and an Iranian human rights organization.
Then last May, the three hackers successfully gained access to accounts belonging to Trump campaign officials. (Attempts to breach Biden campaign staff were, apparently, unsuccessful.) President Joe Biden’s campaign staffers as well as news outlets like The Washington Post and Politico received unsolicited emails from an AOL account owned by “Robert” that contained materials stolen from the Trump campaign. They included some internal poll results and the vetting dossier for Trump’s running mate Senator J.D. Vance.
Because of extradition laws, it’s unlikely these hackers will be brought to justice on US soil.
Servers computers
Perakitan Rak Server Indorack: Open Rack Post 20

Halo Sobat IT!
Selamat datang di video terbaru kami yang kali ini akan mengulas proses perakitan Open Rack Post 20 dari Indorack! Dalam video ini, Sobat IT akan diajak menyaksikan tim profesional kami yang merakit Open Rack Post 20 dengan lancar dan efisien, membawa solusi penyimpanan server terdepan dari Indorack langsung ke ruang server Anda.
Open Rack Post 20 menampilkan desain inovatif yang tidak hanya canggih namun juga fungsional, menjadikannya pilihan yang ideal untuk kebutuhan para profesional IT dan bisnis. Tipe rack server ini dilengkapi dengan fitur khusus yang mempermudah pengelolaan server dengan efisiensi tinggi. Dalam video ini, kami juga akan mengulas spesifikasi teknisnya, termasuk kapasitas dan tingkat keamanan, sambil menyoroti keunggulan bahwa tipe ini bisa disesuaikan kedalamannya (adjustable depth), memberikan fleksibilitas yang optimal sesuai dengan kebutuhan spesifik ruang server Anda.
source
Technology
Cohere updates APIs to make it easier for devs to switch to it

Join our daily and weekly newsletters for the latest updates and exclusive content on industry-leading AI coverage. Learn More
Cohere has announced the release of updated versions of its application programming interfaces (APIs) for its AI models Chat, Embed, Rerank, and Classify.
Collectively, the new API updates are known as API V2, and Cohere is being transparent about the fact that the updates are meant to more closely align with AI industry standards to make it easier for developers to switch their applications over to be powered by Cohere’s models in lieu of the competition: namely, OpenAI, Anthropic, Google, Mistral, and Meta.
Earlier this month, Andreessen Horowitz (A16z) general partner Martin Casado posted on X an image of a graph showing the results of a survey from AI API platform Kong of 800 enterprise leaders revealing the large language models (LLMs) they were using.
OpenAI’s ChatGPT dominated the chart with 27% market share compared to 18% using Microsoft’s Azure AI cloud service and 17% for Google Gemini. Cohere was second-to-last with a distant 5%, showing how the Toronto-based startup — co-founded by some of the former Google researchers behind the original 2017 Transformer paper that ushered in the generative AI era — has a lot of ground to make up to win over the enterprise customers it’s courting.
Enhanced reliability with more precise settings
One of the most significant changes in the V2 API release is the requirement for developers to specify the model version in their API calls.
Previously, this field was optional, which sometimes led to unexpected behavior when new models were released and the default model changed.
By making the model version a mandatory field, Cohere ensures that developers maintain consistent application performance, particularly in scenarios involving Embed models, where using different versions can impact results.
The updated Chat API introduces several usability improvements, including the consolidation of input parameters into a single messages array, replacing the previous structure that required separate message, chat_history, and preamble parameters.
This change simplifies the input process, allowing for more complex use cases where roles such as system or assistant can be assigned to the latest message in a chat sequence.
Cohere’s new APIs also enhance tool integration capabilities. In the V2 release, tools are defined using JSON schema instead of Python types, making the process more flexible and compatible with a wider range of applications.
Additionally, each tool call now includes a unique ID, enabling the API to correctly match tool results with their corresponding calls—an improvement over the V1 API, which lacked this feature.
For streaming interactions, the V2 Chat API has switched from JSON-stream events to Server Sent Events (SSE), providing a more robust and responsive experience for users.
Support for existing APIs
Cohere has confirmed that the V1 suite of APIs will continue to be supported, ensuring that developers who are not yet ready to migrate can still rely on existing implementations.
There will be no breaking changes to the V1 API or its associated SDKs.
However, the company recommends upgrading to V2 for enhanced stability and access to the latest features, such as model version enforcement and advanced chat capabilities.
Resources for developers
To facilitate the transition to API V2, Cohere has released a new SDK and an OpenAPI specification for its updated endpoint.
These resources, along with a detailed Chat Migration Guide, are available on the Cohere platform. Developers are encouraged to provide feedback and suggestions via the company’s Discord community.
Cohere’s API V2 release represents a significant step forward in making its platform more accessible and efficient for developers. With these updates, the company aims to offer a more streamlined and predictable development experience, and ultimately, win over users from OpenAI and other popular APIs.
Source link
Technology
WordPress.org temporarily lifts its ban on WP Engine

WordPress.org has lifted its ban on hosting provider WP Engine until October 1, after putting a block on it earlier this week. The block prevented several sites from updating their plug-ins and themes and exposing them to potential security risk.
WordPress co-founder Matt Mullenweg, who has been in a tussle with WP Engine for over a week, blamed WP Engine’s private equity investor, Silver Lake.
“I’ve heard from WP Engine customers that they are frustrated that WP Engine hasn’t been able to make updates, plugin directory, theme directory, and Openverse work on their sites. It saddens me that they’ve been negatively impacted by Silver Lake‘s commercial decisions,” Mullenweg said on the WordPress.org blog.
“WP Engine was well aware that we could remove access when they chose to ignore our efforts to resolve our differences and enter into a commercial licensing agreement. Heather Brunner, Lee Wittlinger, and their Board chose to take this risk. WPE was also aware that they were placing this risk directly on WPE customers,” he added.
After Mullenweg barred WP Engine from accessing WordPress.org resources, many people in the WordPress community criticized the sudden move, which affected several websites.
In the past week, Mullenweg called WP Engine “Cancer to WordPress” and called them out on their lack of contributions to the WordPress ecosystem. WP Engine sent a cease-and-desist letter to Automattic— which owns WordPress.com and has an exclusive commercial license to the WordPress trademark — and Mullenweg to withdraw these comments. In reply, Automattic also sent its cease-and-desist letter to WP Engine, accusing them of trademark infringement.
This fight impacts a larger ecosystem as WordPress technology is open source and free, and it powers a huge chunk of the internet — around 40% of websites. Websites can host their own WordPress instance or use a provider like Automattic or WP Engine for a plug-and-play solution.
Over the last few days, Mullenweg has said that his fight is against WP Engine — and primarily about tradermarks. However, the WordPress community at large has felt uncertain about how they can use WordPress in their services and if Automattic or Mullenweg would come after them as well.
The WordPress Foundation, which owns the WordPress trademark, filed for two new trademarks, “Managed WordPress” and “Hosted WordPress,” in July. Developers and providers are worried that if these trademarks are granted, they could be used against them.
-

 Womens Workouts5 days ago
Womens Workouts5 days ago3 Day Full Body Women’s Dumbbell Only Workout
-

 News6 days ago
News6 days agoOur millionaire neighbour blocks us from using public footpath & screams at us in street.. it’s like living in a WARZONE – WordupNews
-

 Technology1 week ago
Technology1 week agoWould-be reality TV contestants ‘not looking real’
-
 News1 week ago
News1 week agoYou’re a Hypocrite, And So Am I
-
 Science & Environment1 week ago
Science & Environment1 week agoHyperelastic gel is one of the stretchiest materials known to science
-

 Science & Environment1 week ago
Science & Environment1 week ago‘Running of the bulls’ festival crowds move like charged particles
-

 Sport1 week ago
Sport1 week agoJoshua vs Dubois: Chris Eubank Jr says ‘AJ’ could beat Tyson Fury and any other heavyweight in the world
-

 Science & Environment1 week ago
Science & Environment1 week agoMaxwell’s demon charges quantum batteries inside of a quantum computer
-

 Science & Environment1 week ago
Science & Environment1 week agoHow to wrap your mind around the real multiverse
-

 Science & Environment1 week ago
Science & Environment1 week agoSunlight-trapping device can generate temperatures over 1000°C
-

 Science & Environment1 week ago
Science & Environment1 week agoITER: Is the world’s biggest fusion experiment dead after new delay to 2035?
-
 Science & Environment1 week ago
Science & Environment1 week agoLiquid crystals could improve quantum communication devices
-
 Science & Environment1 week ago
Science & Environment1 week agoPhysicists are grappling with their own reproducibility crisis
-

 Science & Environment1 week ago
Science & Environment1 week agoHow to unsnarl a tangle of threads, according to physics
-
 Science & Environment1 week ago
Science & Environment1 week agoQuantum ‘supersolid’ matter stirred using magnets
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoCardano founder to meet Argentina president Javier Milei
-

 Science & Environment2 weeks ago
Science & Environment2 weeks agoCaroline Ellison aims to duck prison sentence for role in FTX collapse
-
 Science & Environment1 week ago
Science & Environment1 week agoWhy this is a golden age for life to thrive across the universe
-

 News1 week ago
News1 week agoIsrael strikes Lebanese targets as Hizbollah chief warns of ‘red lines’ crossed
-

 Womens Workouts1 week ago
Womens Workouts1 week agoBest Exercises if You Want to Build a Great Physique
-
 Science & Environment1 week ago
Science & Environment1 week agoQuantum forces used to automatically assemble tiny device
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoDZ Bank partners with Boerse Stuttgart for crypto trading
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoEthereum is a 'contrarian bet' into 2025, says Bitwise exec
-

 Womens Workouts1 week ago
Womens Workouts1 week agoEverything a Beginner Needs to Know About Squatting
-

 Science & Environment6 days ago
Science & Environment6 days agoMeet the world's first female male model | 7.30
-

 Science & Environment1 week ago
Science & Environment1 week agoNuclear fusion experiment overcomes two key operating hurdles
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoBitcoin miners steamrolled after electricity thefts, exchange ‘closure’ scam: Asia Express
-
 CryptoCurrency1 week ago
CryptoCurrency1 week agoDorsey’s ‘marketplace of algorithms’ could fix social media… so why hasn’t it?
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoRedStone integrates first oracle price feeds on TON blockchain
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoBitcoin bulls target $64K BTC price hurdle as US stocks eye new record
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoBlockdaemon mulls 2026 IPO: Report
-

 News1 week ago
News1 week agoBrian Tyree Henry on voicing young Megatron, his love for villain roles
-
 CryptoCurrency1 week ago
CryptoCurrency1 week agoCoinbase’s cbBTC surges to third-largest wrapped BTC token in just one week
-

 News6 days ago
News6 days agoFour dead & 18 injured in horror mass shooting with victims ‘caught in crossfire’ as cops hunt multiple gunmen
-

 Womens Workouts4 days ago
Womens Workouts4 days ago3 Day Full Body Toning Workout for Women
-

 Science & Environment1 week ago
Science & Environment1 week agoNerve fibres in the brain could generate quantum entanglement
-

 Science & Environment1 week ago
Science & Environment1 week agoTime travel sci-fi novel is a rip-roaringly good thought experiment
-

 News1 week ago
News1 week ago▶️ Media Bias: How They Spin Attack on Hezbollah and Ignore the Reality
-
 Science & Environment1 week ago
Science & Environment1 week agoLaser helps turn an electron into a coil of mass and charge
-
 Science & Environment1 week ago
Science & Environment1 week agoQuantum time travel: The experiment to ‘send a particle into the past’
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoCrypto scammers orchestrate massive hack on X but barely made $8K
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoLow users, sex predators kill Korean metaverses, 3AC sues Terra: Asia Express
-

 CryptoCurrency1 week ago
CryptoCurrency1 week ago‘No matter how bad it gets, there’s a lot going on with NFTs’: 24 Hours of Art, NFT Creator
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoSEC asks court for four months to produce documents for Coinbase
-

 Sport1 week ago
Sport1 week agoUFC Edmonton fight card revealed, including Brandon Moreno vs. Amir Albazi headliner
-
Business1 week ago
How Labour donor’s largesse tarnished government’s squeaky clean image
-

 Technology1 week ago
Technology1 week agoiPhone 15 Pro Max Camera Review: Depth and Reach
-

 News1 week ago
News1 week agoBrian Tyree Henry on voicing young Megatron, his love for villain roles
-

 Womens Workouts1 week ago
Womens Workouts1 week agoKeep Your Goals on Track This Season
-

 Travel4 days ago
Travel4 days agoDelta signs codeshare agreement with SAS
-

 Science & Environment1 week ago
Science & Environment1 week agoWhy we need to invoke philosophy to judge bizarre concepts in science
-
 Science & Environment1 week ago
Science & Environment1 week agoHow do you recycle a nuclear fusion reactor? We’re about to find out
-

 News1 week ago
News1 week agoChurch same-sex split affecting bishop appointments
-
 Science & Environment1 week ago
Science & Environment1 week agoTiny magnet could help measure gravity on the quantum scale
-

 Technology1 week ago
Technology1 week agoFivetran targets data security by adding Hybrid Deployment
-

 CryptoCurrency1 week ago
CryptoCurrency1 week ago$12.1M fraud suspect with ‘new face’ arrested, crypto scam boiler rooms busted: Asia Express
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoDecentraland X account hacked, phishing scam targets MANA airdrop
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoCertiK Ventures discloses $45M investment plan to boost Web3
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoBeat crypto airdrop bots, Illuvium’s new features coming, PGA Tour Rise: Web3 Gamer
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoTelegram bot Banana Gun’s users drained of over $1.9M
-

 CryptoCurrency1 week ago
CryptoCurrency1 week ago‘Silly’ to shade Ethereum, the ‘Microsoft of blockchains’ — Bitwise exec
-
Business1 week ago
Thames Water seeks extension on debt terms to avoid renationalisation
-
Politics1 week ago
‘Appalling’ rows over Sue Gray must stop, senior ministers say | Sue Gray
-

 Womens Workouts1 week ago
Womens Workouts1 week agoHow Heat Affects Your Body During Exercise
-

 News6 days ago
News6 days agoWhy Is Everyone Excited About These Smart Insoles?
-

 Politics1 week ago
Politics1 week agoTrump says he will meet with Indian Prime Minister Narendra Modi next week
-

 Technology1 week ago
Technology1 week agoCan technology fix the ‘broken’ concert ticketing system?
-

 Health & fitness1 week ago
Health & fitness1 week agoThe secret to a six pack – and how to keep your washboard abs in 2022
-

 Science & Environment1 week ago
Science & Environment1 week agoBeing in two places at once could make a quantum battery charge faster
-

 Science & Environment1 week ago
Science & Environment1 week agoA new kind of experiment at the Large Hadron Collider could unravel quantum reality
-

 Science & Environment1 week ago
Science & Environment1 week agoHow one theory ties together everything we know about the universe
-

 Science & Environment1 week ago
Science & Environment1 week agoUK spurns European invitation to join ITER nuclear fusion project
-
 CryptoCurrency1 week ago
CryptoCurrency1 week ago2 auditors miss $27M Penpie flaw, Pythia’s ‘claim rewards’ bug: Crypto-Sec
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoLouisiana takes first crypto payment over Bitcoin Lightning
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoJourneys: Robby Yung on Animoca’s Web3 investments, TON and the Mocaverse
-

 CryptoCurrency1 week ago
CryptoCurrency1 week ago‘Everything feels like it’s going to shit’: Peter McCormack reveals new podcast
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoSEC sues ‘fake’ crypto exchanges in first action on pig butchering scams
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoBitcoin price hits $62.6K as Fed 'crisis' move sparks US stocks warning
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoVonMises bought 60 CryptoPunks in a month before the price spiked: NFT Collector
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoVitalik tells Ethereum L2s ‘Stage 1 or GTFO’ — Who makes the cut?
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoEthereum falls to new 42-month low vs. Bitcoin — Bottom or more pain ahead?
-

 News1 week ago
News1 week agoBrian Tyree Henry on his love for playing villains ahead of “Transformers One” release
-

 Womens Workouts1 week ago
Womens Workouts1 week agoWhich Squat Load Position is Right For You?
-

 News7 days ago
News7 days agoBangladesh Holds the World Accountable to Secure Climate Justice
-
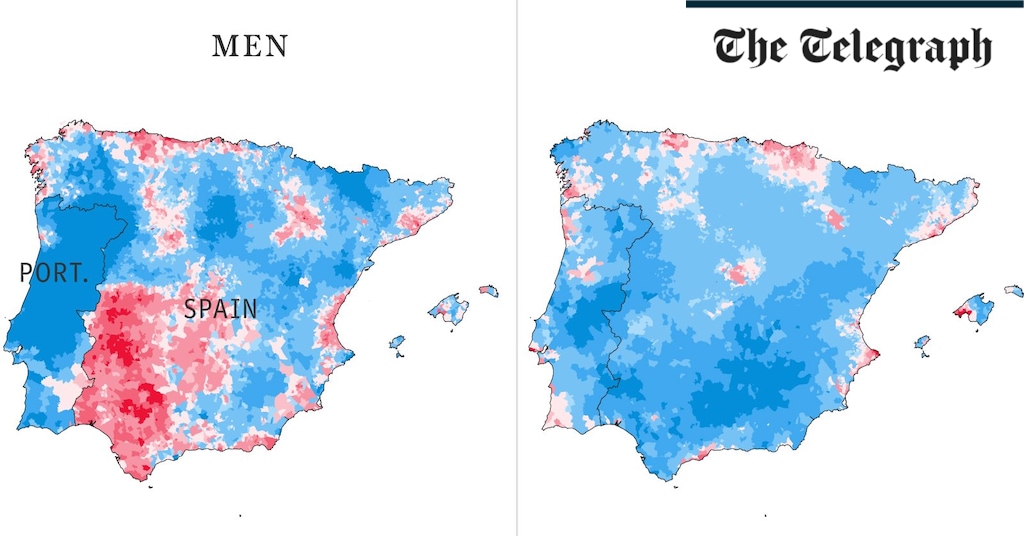
 Health & fitness1 week ago
Health & fitness1 week agoThe maps that could hold the secret to curing cancer
-
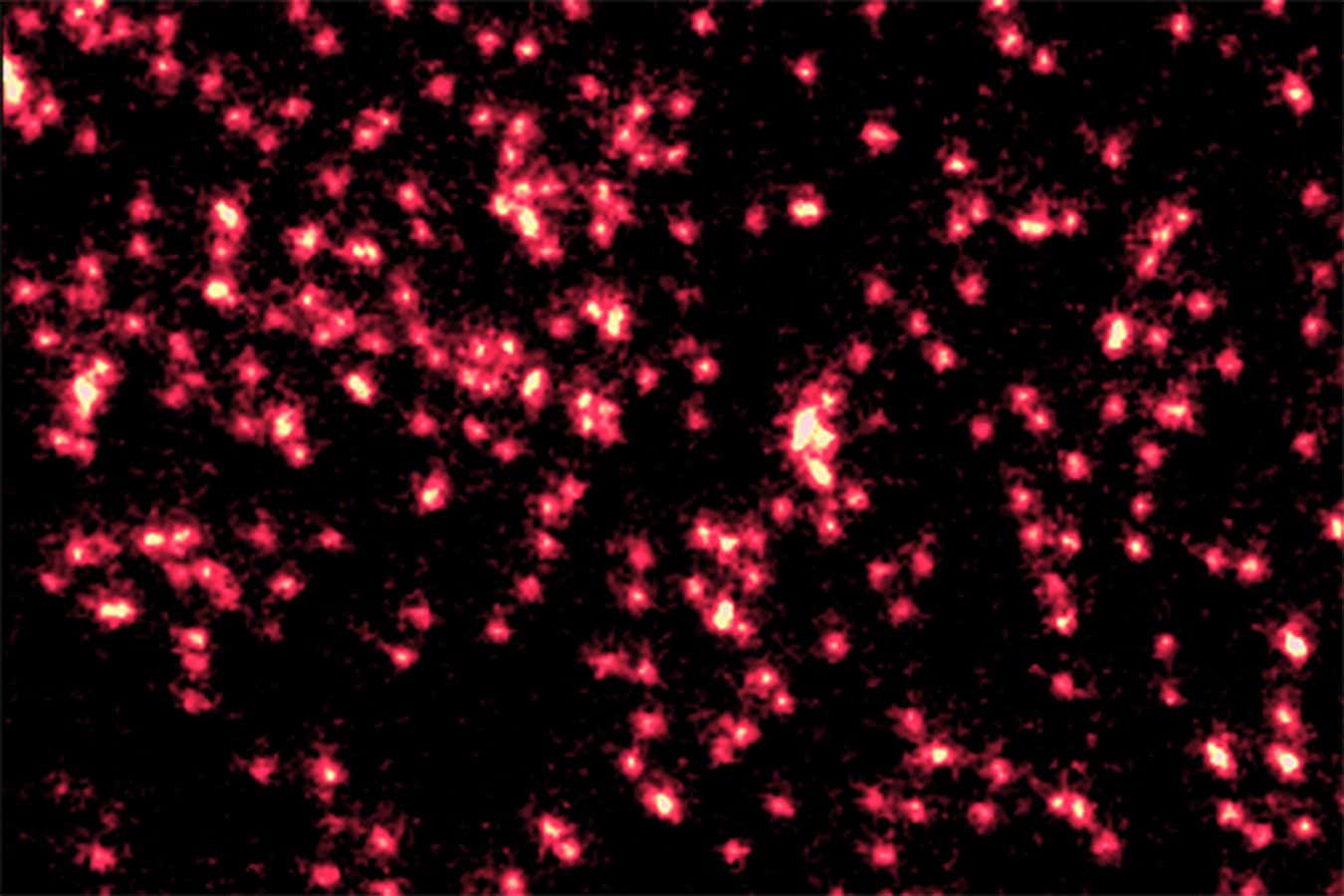
 Science & Environment1 week ago
Science & Environment1 week agoSingle atoms captured morphing into quantum waves in startling image
-
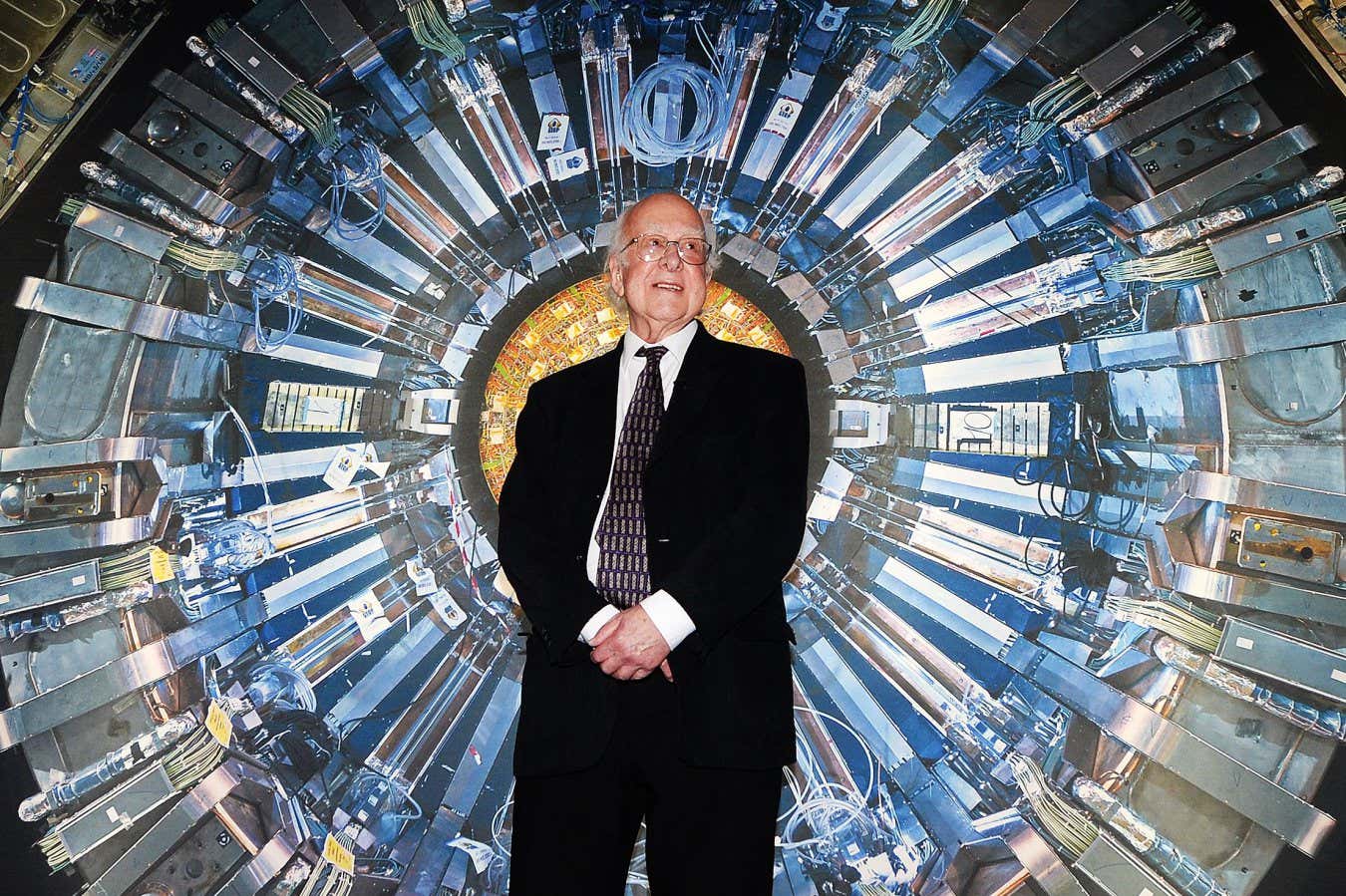
 Science & Environment1 week ago
Science & Environment1 week agoHow Peter Higgs revealed the forces that hold the universe together
-

 Science & Environment1 week ago
Science & Environment1 week agoFuture of fusion: How the UK’s JET reactor paved the way for ITER
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoHelp! My parents are addicted to Pi Network crypto tapper
-

 CryptoCurrency1 week ago
CryptoCurrency1 week agoCZ and Binance face new lawsuit, RFK Jr suspends campaign, and more: Hodler’s Digest Aug. 18 – 24
-

 Fashion Models1 week ago
Fashion Models1 week agoMixte
-

 Politics1 week ago
Politics1 week agoLabour MP urges UK government to nationalise Grangemouth refinery
-

 Money1 week ago
Money1 week agoBritain’s ultra-wealthy exit ahead of proposed non-dom tax changes
-

 Womens Workouts1 week ago
Womens Workouts1 week agoWhere is the Science Today?
-

 Womens Workouts1 week ago
Womens Workouts1 week agoSwimming into Your Fitness Routine
-

 News2 weeks ago
News2 weeks agoBrain changes during pregnancy revealed in detailed map
-

 Science & Environment1 week ago
Science & Environment1 week agoA slight curve helps rocks make the biggest splash
-

 News1 week ago
News1 week agoRoad rage suspects in custody after gunshots, drivers ramming vehicles near Boise
-

 Science & Environment1 week ago
Science & Environment1 week agoA tale of two mysteries: ghostly neutrinos and the proton decay puzzle
-

 News2 weeks ago
News2 weeks agoToolkit to help journalists overcome ‘unspoken power dynamic’ in sensitive interviews

You must be logged in to post a comment Login