Crypto World
BTC re-takes $70,000 as Michael Saylor addresses Quantum Computing threat
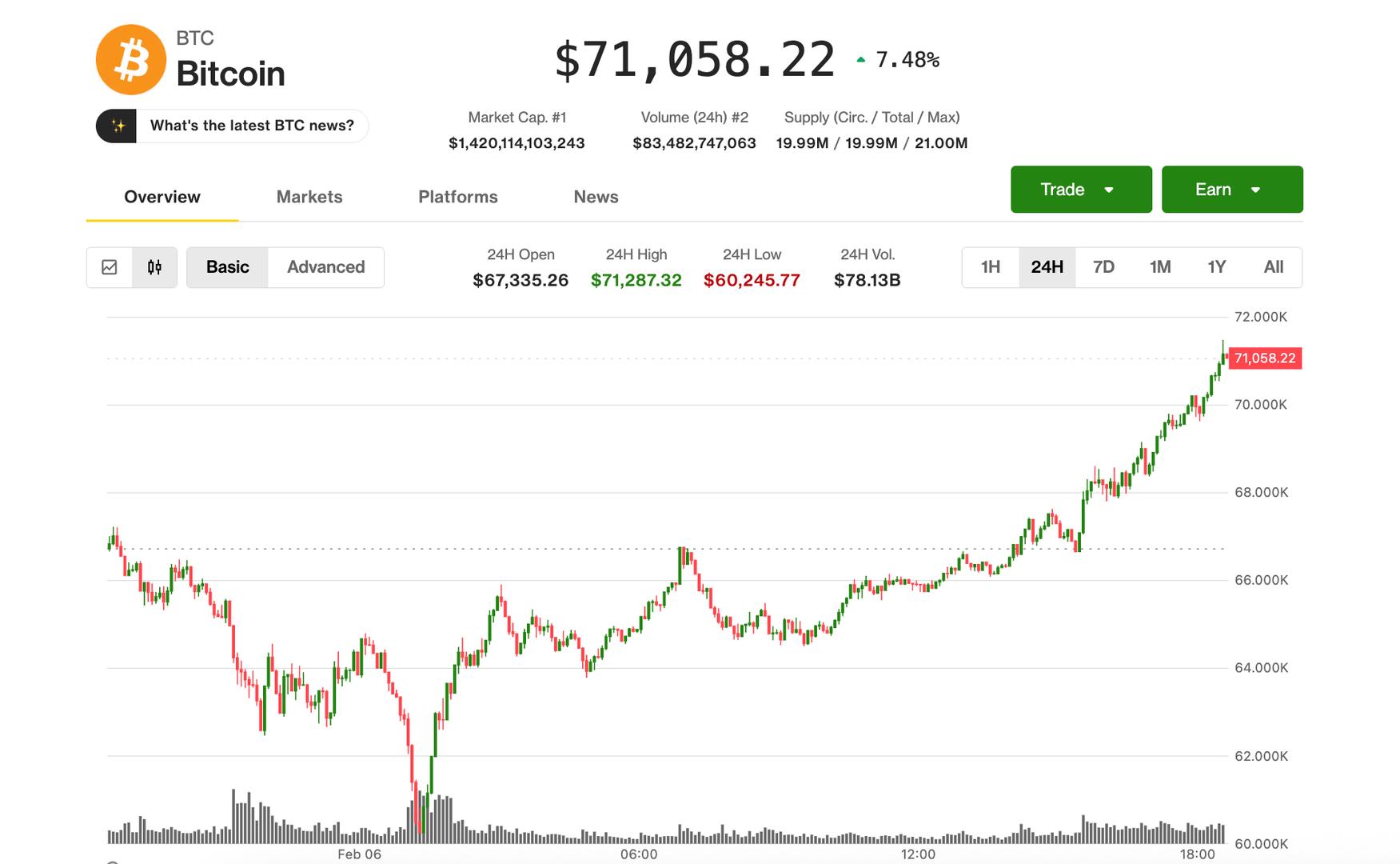
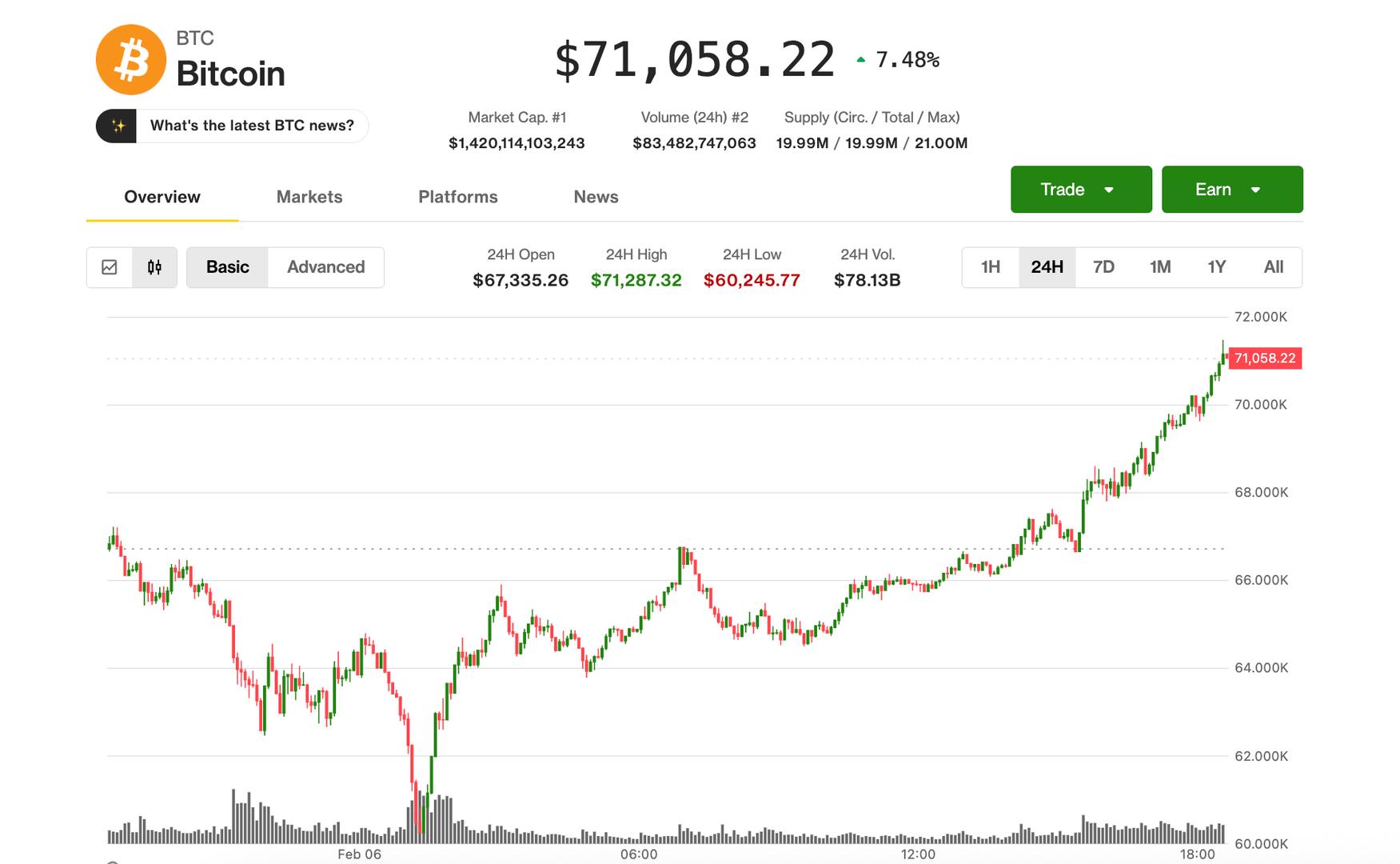
Crypto markets are adding to overnight gains in U.S. morning trade on Friday, with bitcoin climbing above $68,000, up nearly 17% since hitting $60,000 late yesterday.
Bitcoin is now higher by 2.5% over the past 24 hours. Ether is up 2.2% and solana 2%. Outperforming is XRP , which has climbed to $1.50, now higher by 17% over the last day.
Crypto-related stocks are seeing major upside moves Friday after plunging in the previous session.
Strategy (MSTR) — which reported a $14.2 billion fourth-quarter loss late Thursdy — is higher by 14%, though at $122, still lower by 22% year-to-date. Galaxy Digital (GLXY) is up 15% and bitcoin miner MARA Holdings (MARA) is up 12%.
Underperforming on Friday is bitcoin miner-turned AI infrastructure provider IREN (IREN), down 1.8% after disappointing earnings results Thursday night.
Saylor gets serious about Quantum
Those looking for bottom signals are pointing to last night’s Strategy earnings call in which Michael Saylor pledged a commitment to leading a Bitcoin security program that will address the quantum threat.
Some in crypto have argued that bitcoin’s security model faces a serious threat from quantum computing — a threat so imminent that many investors are either selling or refusing to allocate to bitcoin at all.
“Saylor’s announcement tells me prices have finally gotten the Bitcoin community to acknowledge and address quantum risk,” wrote Quinn Thompson.
Poised for technical bounce
Paul Howard, director at crypto trading firm Wincent, noted that bitcoin is now back at price levels last seen 14 months ago with key momentum indicator RSI flashing deeply oversold conditions. He added that trading volumes in BTC and ETH have surged to their highest in over two years. That technical setup that often invites at least a short-term bounce.
“It would be odd if we did not see at least some short term reversion here,” he said.
Updated (14:55 UTC): Adds price of bitocin rising past $70,000.
Crypto World
Labor Market and Housing Data Raise New Fears of a U.S. Economic Slowdown

TLDR:
- Layoffs and declining job openings show employers preparing for slower growth and tighter financial conditions
- Housing demand is weakening as sellers outnumber buyers, creating a record imbalance and reduced market liquidity
- Bond and credit markets reflect rising stress tied to debt levels and long-term growth uncertainty
- Rapid disinflation and firm monetary policy increase the risks of tightening into an already fragile economy
U.S. economic indicators are showing coordinated signs of strain across labor, housing, and credit markets. Layoffs are rising while hiring slows, reducing job security for many workers.
Housing demand is weakening as sellers outnumber buyers. Bond and credit markets also reflect growing caution. Together, these trends suggest the economy is entering a fragile late-cycle phase.
Labor and Housing Data Point to Late-Cycle Fragility
Labor and housing data are moving together in a pattern associated with late-cycle slowdowns. January layoff announcements exceeded one hundred thousand, the highest level for that month since the global financial crisis.
Weekly jobless claims have trended higher, while job openings have fallen to levels last seen in 2020. This combination reduces worker mobility and weakens income security across sectors.
Companies are not only cutting staff but also limiting recruitment, with hiring plans reaching record lows for the month. Consumer confidence surveys now reflect growing caution toward discretionary spending and long-term purchases.
Housing markets mirror this shift in behavior. Sellers outnumber buyers by a wide margin, creating the largest recorded gap between supply and demand participants.
Elevated mortgage rates continue to restrict affordability, while existing owners hesitate to reduce prices because of low-rate loans locked in earlier years. Listings remain visible, yet transactions slow as liquidity dries up.
This imbalance delays price discovery and increases carrying costs for households and developers.
Employment weakness directly affects housing demand. Fewer stable incomes mean fewer qualified buyers, placing additional pressure on inventories struggling to clear.
Together, labor deterioration and housing imbalance suggest that economic momentum is being supported by inertia rather than expanding demand, a condition that historically precedes slowdowns across consumption-driven industries.
Bond, Credit, and Inflation Signals Reinforce Economic Stress
Financial markets are reflecting stress through bond and credit indicators. The Treasury yield curve has entered bear steepening, where long-term yields rise faster than short-term rates.
Investors demand higher compensation to hold extended maturity debt, signaling concern over fiscal deficits and long-term growth expectations. Similar curve movements have preceded economic contractions in previous cycles.
Corporate credit conditions show parallel weakness. A rising share of lower-quality bonds now trades at distressed levels or faces elevated default risk.
When financing tightens, firms cut costs, postpone investment, and reduce payroll. These actions feed back into employment and consumer demand, reinforcing pressure already visible in labor data.
Business bankruptcy filings continue to trend upward, reducing liquidity within supply chains and tightening lending standards across financial institutions. Inflation readings have shifted quickly, with real-time measures pointing toward levels near one percent.
Rapid disinflation increases the risk that consumers delay spending in anticipation of lower prices, slowing transaction activity across goods and services markets.
Monetary policy remains focused on inflation control despite weakening forward indicators in labor and housing. A restrictive stance during slowing growth raises the probability of misalignment between financial conditions and economic capacity.
Combined with credit strain and yield curve signals, the environment reflects fragility rather than expansion.
Crypto World
Why Privacy Coins Often Appear in Post-Hack Fund Flows
Key takeaways
-
Privacy coins are just a step in a broader laundering pipeline after hacks. They serve as a temporary black box to disrupt traceability.
-
Hackers typically move funds through consolidation, obfuscation and chain hopping and only then introduce privacy layers before attempting to cash out.
-
Privacy coins are most useful immediately after a hack because they reduce onchain visibility, delay blacklisting and help break attribution links.
-
Enforcement actions against mixers and other laundering tools often shift illicit flows toward alternative routes, including privacy coins.
After crypto hacks occur, scammers often move stolen funds through privacy-focused cryptocurrencies. While this has created a perception of hackers preferring privacy coins, these assets function as a specialized “black box” within a larger laundering pipeline. To understand why privacy coins show up after hacks, you need to take into account the process of crypto laundering.
This article explores how funds move post-hack and what makes privacy coins so useful for scammers. It examines emerging laundering methods, limitations of privacy coins like Monero (XMR) and Zcash (ZEC) as laundering tools, legitimate uses of privacy technologies and why regulators need to balance innovation with the need to curb laundering.
How funds flow after a hack
Following a hack, scammers don’t usually send stolen assets directly to an exchange for immediate liquidation; instead, they follow a deliberate, multi-stage process to obscure the trail and slow down the inquiry:
-
Consolidation: Funds from multiple victim addresses are transferred to a smaller number of wallets.
-
Obfuscation: Assets are shuffled through chains of intermediary crypto wallets, often with the help of crypto mixers.
-
Chain-hopping: Funds are bridged or swapped to different blockchains, breaking continuity within any single network’s tracking tools.
-
Privacy layer: A portion of funds is converted into privacy-focused assets or routed through privacy-preserving protocols.
-
Cash-out: Assets are eventually exchanged for more liquid cryptocurrencies or fiat through centralized exchanges, over-the-counter (OTC) desks or peer-to-peer (P2P) channels.
Privacy coins usually enter the stage in steps four or five, blurring the traceability of lost funds even more after earlier steps have already complicated the onchain history.

Why privacy coins are attractive for scammers right after a hack
Privacy coins offer specific advantages right at the time when scammers are most vulnerable, immediately after the theft.
Reduced onchain visibility
Unlike transparent blockchains, where the sender and receiver and transaction amounts remain fully auditable, privacy-focused systems deliberately hide these details. Once funds move into such networks, standard blockchain analytics lose much of their efficacy.
In the aftermath of the theft, scammers try to delay identification or evade automated address blacklisting by exchanges and services. The sudden drop in visibility is particularly valuable in the critical days after theft when monitoring is most intense.
Breaking attribution chains
Scammers tend not to move directly from hacked assets into privacy coins. They typically use multiple techniques, swaps, cross-chain bridges and intermediary wallets before introducing a privacy layer.
This multi-step approach makes it significantly harder to connect the final output back to the original hack. Privacy coins act more as a strategic firebreak in the attribution process than as a standalone laundering tool.
Negotiating power in OTC and P2P markets
Many laundering paths involve informal OTC brokers or P2P traders who operate outside extensively regulated exchanges.
Using privacy-enhanced assets reduces the information counterparties have about the funds’ origin. This can simplify negotiations, lower the perceived risk of mid-transaction freezes and improve the attacker’s leverage in less transparent markets.
Did you know? Several early ransomware groups originally demanded payment in Bitcoin (BTC) but later switched to privacy coins only after exchanges began cooperating more closely with law enforcement on address blacklisting.
The mixer squeeze and evolving methods of laundering
One reason privacy coins appear more frequently in specific time frames is enforcement pressure on other laundering tools. When law enforcement targets particular mixers, bridges or high-risk exchanges, illicit funds simply move to other channels. This shift results in the diversification of laundering routes across various blockchains, swapping platforms and privacy-focused networks.
When scammers perceive one laundering route as risky, alternative routes experience higher volumes. Privacy coins gain from this dynamic, as they offer inherent transaction obfuscation, independent of third-party services.
Limitations of privacy coins as a laundering tool
Privacy features notwithstanding, most large-scale hacks still involve extensive use of BTC, Ether (ETH) and stablecoins at later stages. The reason is straightforward: Liquidity and exit options are important.
Privacy coins generally exhibit:
These factors complicate the conversion of substantial amounts of crypto to fiat currency without drawing scrutiny. Therefore, scammers use privacy coins briefly before reverting to more liquid assets prior to final withdrawal.
Successful laundering involves integration of privacy-enhancing tools with high-liquidity assets, tailored to each phase of the process.
Did you know? Some darknet marketplaces now list prices in Monero by default, even if they still accept Bitcoin, because vendors prefer not to reveal their income patterns or customer volume.
Behavioral trends in asset laundering
While tactical specifics vary, blockchain analysts generally identify several high-level “red flags” in illicit fund flows:
-
Layering and consolidation: Rapid dispersal of assets across a vast network of wallets, followed by strategic reaggregation to simplify the final exit.
-
Chain hopping: Moving assets across multiple blockchains to break the deterministic link of a single ledger, often sandwiching privacy-enhancing protocols.
-
Strategic latency: Allowing funds to remain dormant for extended periods to bypass the window of heightened public and regulatory scrutiny.
-
Direct-to-fiat workarounds: Preferring OTC brokers for the final liquidation to avoid the robust monitoring systems of major exchanges.
-
Hybrid privacy: Using privacy-centric coins as a specialized tool within a broader laundering strategy, rather than as a total replacement for mainstream assets.
Contours of anonymity: Why traceability persists
Despite the hurdles created by privacy-preserving technologies, investigators continue to secure wins by targeting the edges of the ecosystem. Progress is typically made through:
-
Regulated gateways: Forcing interactions with exchanges that mandate rigorous identity verification
-
Human networks: Targeting the physical infrastructure of money-mule syndicates and OTC desks
-
Off-chain intelligence: Leveraging traditional surveillance, confidential informants and Suspicious Activity Reports (SARs)
-
Operational friction: Exploiting mistakes made by the perpetrator that link their digital footprint to a real-world identity.
Privacy coins increase the complexity and cost of an investigation, but they cannot fully insulate scammers from the combined pressure of forensic analysis and traditional law enforcement.
Did you know? Blockchain analytics firms often focus less on privacy coins themselves and more on tracing how funds enter and exit them since those boundary points offer the most reliable investigative signals.
Reality of legitimate use for privacy-enhancing technologies
It is essential to distinguish between the technology itself and its potential criminal applications. Privacy-focused financial tools, such as certain cryptocurrencies or mixers, serve valid purposes, including:
-
Safeguarding the confidentiality of commercial transactions, which includes protecting trade secrets or competitive business dealings
-
Shielding individuals from surveillance or monitoring in hostile environments
-
Reducing the risk of targeted theft by limiting public visibility of personal wealth.
Regulatory scrutiny isn’t triggered by the mere existence of privacy features, but when they are used for illicit activity, such as ransomware payments, hacking proceeds, sanctions evasion or darknet marketplaces.
This key distinction makes effective policymaking difficult. Broad prohibitions risk curtailing lawful financial privacy for ordinary users and businesses while often failing to halt criminal networks that shift to alternative methods.
Balancing act of regulators
For cryptocurrency exchanges, the recurring appearance of privacy coins in post-hack laundering flows intensifies the need to:
-
Enhance transaction monitoring and risk assessment
-
Reduce exposure to high-risk inflows
-
Strengthen compliance with cross-border Travel Rule requirements and other jurisdictional standards.
For policymakers, it underscores a persistent challenge: Criminal actors adapt more quickly than rigid regulations can evolve. Efforts to crack down on one tool often displace activity to others, turning money laundering into a dynamic, moving target rather than a problem that can be fully eradicated.
Cointelegraph maintains full editorial independence. The selection, commissioning and publication of Features and Magazine content are not influenced by advertisers, partners or commercial relationships.
Crypto World
Justin Sun’s ‘ex’ claims he slid into her DMs to get articles deleted
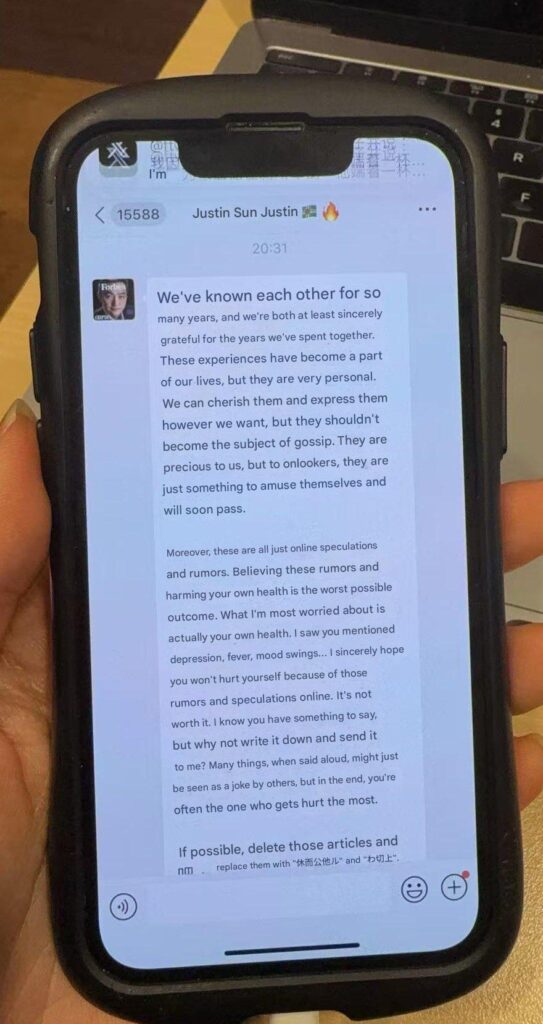
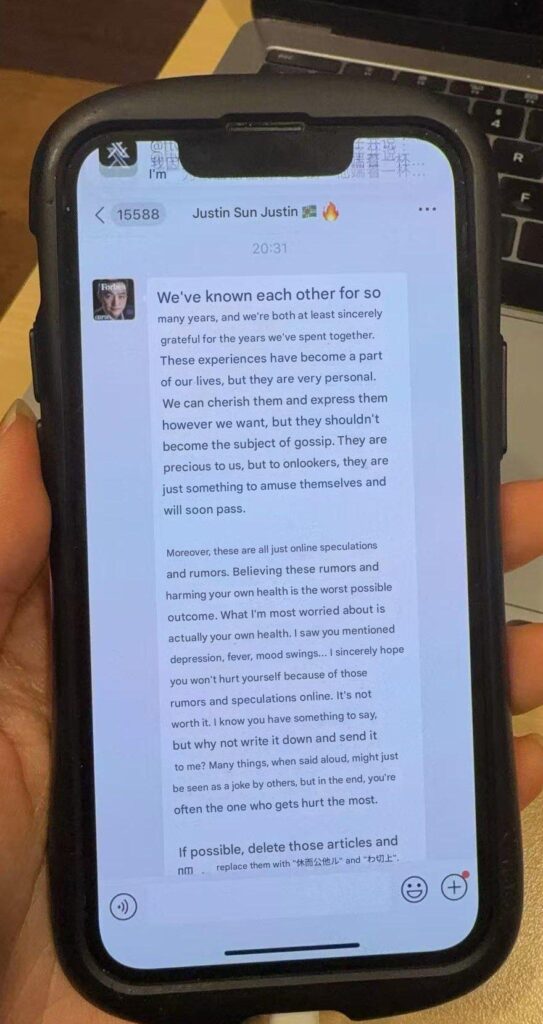
A crypto blogger claiming to be Justin Sun’s ex-girlfriend has shared what appears to be a message from the Tron founder asking her to delete numerous articles while admitting that he “cherishes” their personal time together.
Zeng Ying, otherwise known as Ten Ten, started making accusations against Sun last weekend, accusing him of manipulating the price of TRX with Binance accounts wash trading on his behalf, and also directing crypto accounts to spread misinformation about her.
Her latest post appears to reveal a message she received from Sun, in which he admits that he’s known her for many years and shared “very personal” experiences with her.
In the alleged message, translated using Google, he tells Ten Ten that the two can “cherish” and “express” these experiences, but that they “shouldn’t become the subject of gossip.”
Read more:Justin Sun’s alleged ex accuses him of market manipulation, insider trading
“They are precious to us, but to onlookers, they are just something to amuse themselves and will soon pass.”
He additionally downplays her accusations as “online speculations and rumors,” and tells her that “Believing these rumors and harming your own health is the worst possible outcome.”
“I know you have something to say, but why not write it down and send it to me?” he asks. “Many things, when said aloud, might just be seen as a joke by others, but in the end, you’re often the one who gets hurt the most.”
In the message, Sun apparently also asks Ten Ten to delete some articles and replace them with different text. However, the screenshot shared online doesn’t reveal what specific text this would be.
When sharing the message, Ten Ten said, “So you bought all those water army accounts to smear me, all to help me strengthen my body and build fitness, huh?”
Justin Sun denies all of Ten Ten’s claims
Sun claimed yesterday that “rumors regarding an ‘ex-girlfriend’ and our compliance status are unequivocally false.”
He claims that his firm “cooperates fully with global judicial and law enforcement agencies to crack down on embezzlement, fraud, hacking, other forms of cybercrime, to protect our users’ lawful assets.”
Ten Ten posted minutes later that, “Sun finally got hard for once — he never really got hard when we were together before. I’ll send the full verdict later.” This post was later deleted.
Read more: Justin Sun directed wash trading scheme from his US apartment, SEC claims
The crypto blogger claims to have started publicly attacking Sun after she says she witnessed him become “an insurmountable gate of corruption and wrongdoing.”
She also claims that he offered to marry her later in life, only for him to then announce that he was in a relationship with the skier Eileen Gu.
Protos has reached out to Ten Ten for comment on her allegations and will update this piece should we hear back.
Got a tip? Send us an email securely via Protos Leaks. For more informed news and investigations, follow us on X, Bluesky, and Google News, or subscribe to our YouTube channel.
Crypto World
Macro ‘Accomodative Policies’ May Not Be The Next Big Catalyst For Bitcoin

Bitcoin’s next major catalyst may come from the common assumption being flipped on its head that interest rates are bullish for Bitcoin only when they fall, according to a crypto analyst.
“I think we should expect that having more accommodative policies may in fact actually not be the catalyst to help us go into a bull market,” ProCap Financial chief investment officer Jeff Park said during an interview with Anthony Pompliano on Thursday.
“We have to accept that reality and possibility,” Park said. Accomodative policies, such as lowering interest rates, are employed by the US Federal Reserve to stimulate economic growth, reduce unemployment, and increase liquidity. Bitcoiners often see these conditions as more favorable for riskier assets such as Bitcoin (BTC), as traditional investments like bonds and term deposits become less attractive.

Rising interest rates are usually seen as a negative for Bitcoin, but Park said that may not be the case forever. He said Bitcoin’s next biggest upside catalyst — and potentially its “endgame” — may be its entry into what he called a “positive row Bitcoin,” where the asset’s price continues to rise even as US Federal Reserve interest rates rise.
“Perfect holy grail” for Bitcoin
“This is the mythical, elusive perfect holy grail of what Bitcoin is meant to be, which is when Bitcoin goes up as interest rates go up, which is very counterintuitive to the QE theory,” he said.
However, Park said this idea would undermine the “risk-free rate itself.”
Park emphasizes the monetary system “is broken”
“In that world, what we’re saying is actually because the risk-free rate is not the risk-free rate, because the dollar hegemony is not the dollar hegemony, and we are no longer able to price the yield curve in the ways we’ve known,” Park said.
Related: Bitcoin price rebounds 11% above $65K: Who is buying the dip?
Park explained that the monetary system is “broken” and the relationship between the Fed and the US Treasury is “not at the level it should be” to drive the direction of national securities.
Traders on the crypto prediction platform Polymarket are giving the highest probability, 27%, to three total Fed interest rate cuts in 2026.
Bitcoin is trading at $70,503 at the time of publication, down 22.53% over the past 30 days, according to CoinMarketCap.
Magazine: Bitcoin’s ‘biggest bull catalyst’ would be Saylor’s liquidation: Santiment founder
Crypto World
Ethereum Price Falls to 9-Month Low as Investors Panic Sell
Ethereum has suffered a sharp correction, with price falling nearly 29% over the past week and slipping below the $2,000 mark. ETH is now trading at levels last seen nine months ago, reflecting severe weakness across the market.
Diminishing buyer support has worsened conditions, with on-chain data confirming growing stress among Ethereum holders.
Sponsored
Sponsored
Ethereum Holders Move Back To Selling
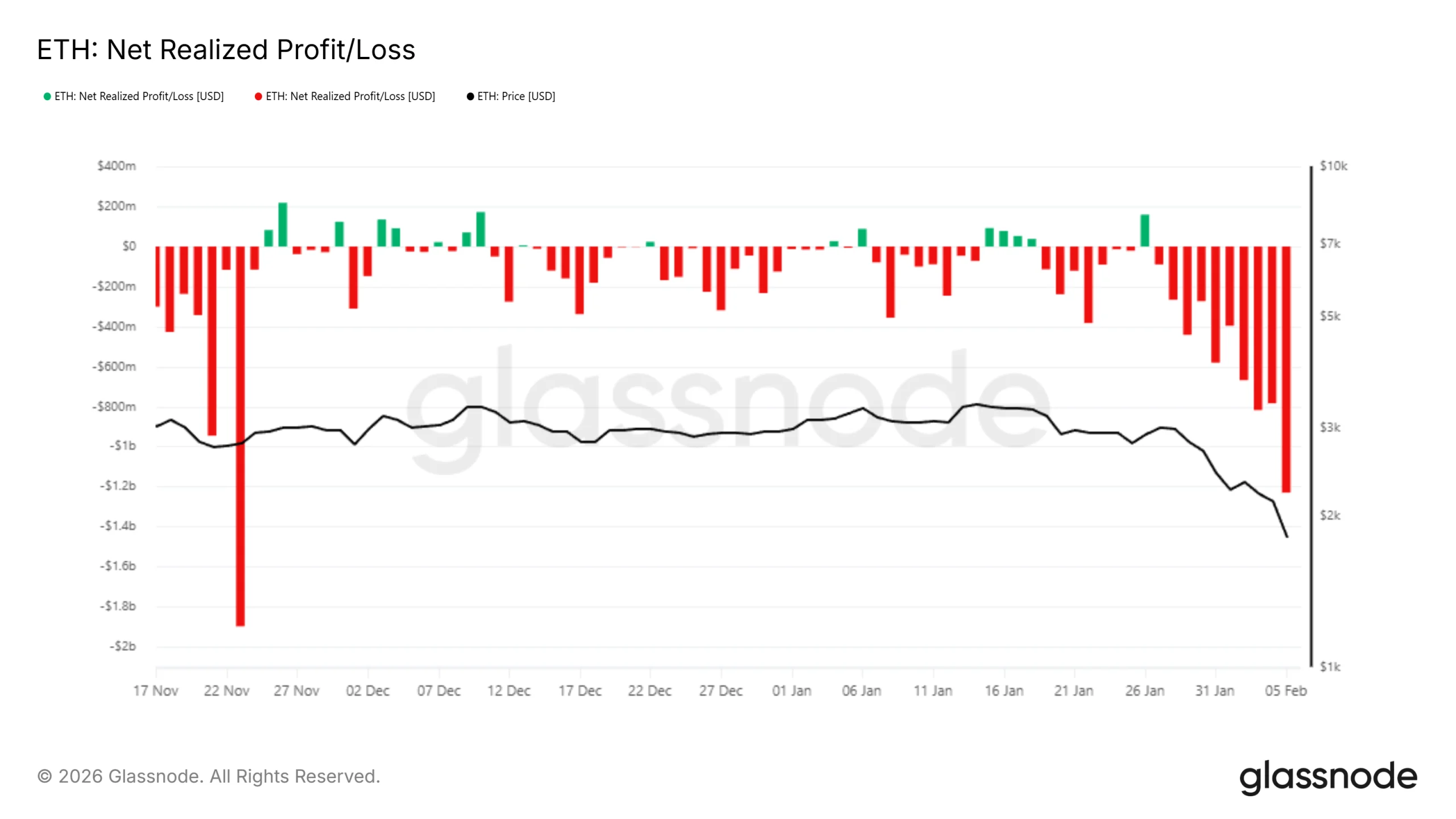
Ethereum holders have increasingly resorted to panic selling as broader market conditions deteriorated. On-chain data from the Realized Profit/Loss indicator shows investors selling despite being underwater. Realized losses surged past $1.2 billion within 24 hours, highlighting widespread capitulation as holders prioritize risk reduction over recovery.
Such elevated realized losses often extend declines by reinforcing negative momentum. As more ETH is sold at a loss, the price faces additional downward pressure. This behavior suggests confidence remains fragile, limiting the ability of Ethereum to stabilize until selling activity meaningfully subsides across the network.
Want more token insights like this? Sign up for Editor Harsh Notariya’s Daily Crypto Newsletter here.
ETH Long-Term Investors Change Stance
Long-term holder behavior reflects similar stress. The HODLer Net Position Change has declined, with bars flipping red, signaling net outflows from long-term wallets. This shift is notable because long-term holders are typically considered the backbone of Ethereum’s market structure and price stability.
Sponsored
Sponsored
When long-term holders distribute rather than accumulate, it often signals deep concern. Their decision to sell amid mounting losses indicates rising panic even among conviction-driven investors. This development adds macro-level pressure and increases the risk that Ethereum’s decline could deepen before a meaningful recovery begins.
ETH Price Could Note A Reversal
Ethereum price is trading near $1,920 at the time of writing after a 29% drop in one week. The move below $2,000 has reinforced bearish structure across multiple timeframes. Given the prevailing on-chain and sentiment indicators, ETH remains vulnerable to additional downside in the near term.
ETH is currently holding above the $1,796 support level. If this level fails, price could slide toward $1,671 or lower. Ethereum is already at a nine-month low, last seen in May 2025, increasing the risk of further liquidation-driven selling if support breaks.
A recovery scenario remains possible if selling pressure eases. Ethereum could reclaim $2,000, supported by oversold conditions. The Money Flow Index sits well below the 20.0 threshold, indicating selling pressure has likely saturated. Historically, such readings have preceded short-term relief rallies.
A similar rebound could unfold if investors refrain from further selling. Holding supply off exchanges may allow ETH to regain momentum. Under this scenario, Ethereum could push beyond $2,000 and advance toward $2,500. Securing that move would invalidate the bearish thesis and restore market confidence.
Crypto World
CryptoQuant CEO warns of cascading institutional BTC sell-off risk


CryptoQuant’s Ki Young Ju warns that absent a near-term Bitcoin rebound, forced liquidations and cascading institutional selling could hit ETFs, miners, and trust.
Summary
- CryptoQuant CEO Ki Young Ju says large BTC releases may signal forced institutional liquidations that pressure prices and ETF flows.
- He warns that if Bitcoin does not rebound within a month, structural, chain institutional selling could rise and push miners toward bankruptcy risk.
- Ju notes institutions that capitulate near market lows may struggle to re-enter, with trust in Bitcoin markets taking a long time to rebuild.
CryptoQuant CEO Ki Young Ju stated that the risk of institutional selling in cryptocurrency markets could increase significantly if Bitcoin does not experience a strong recovery in the short term, according to a statement dated February 6.
CryptoQuant analyst warns of pain in Bitcoin recovery
Ju’s comments addressed potential reasons behind sharp movements in spot Bitcoin exchange-traded funds, particularly responding to observations from DeFi Development manager Parker White regarding a notable ETF decline. White suggested one or more Hong Kong-based non-crypto hedge funds may have contributed to the drop.
The CryptoQuant executive argued that large-scale Bitcoin releases into the market could indicate a forced sell-off scenario. Ju outlined a potential domino effect in which fund liquidations could drive prices lower, creating additional selling pressure in the market and potentially pushing miners toward bankruptcy risk.
“If Bitcoin fails to achieve a significant rise from current levels in the next month, the risk of structural and chain institutional selling increases significantly,” Ju stated.
According to Ju’s analysis, institutional investors who exit positions at market lows may face difficulty returning to the market, with trust rebuilding potentially requiring extended time periods.
The statement included a disclaimer noting the information does not constitute investment advice.
Bitcoin ETFs have experienced increased volatility in recent weeks, with market participants monitoring institutional trading activity closely. The cryptocurrency sector remains sensitive to large-scale transactions from institutional holders, according to market analysts.
Crypto World
How options on the BlackRock bitcoin ETF may have worsened crypto meltdown


BlackRock’s spot bitcoin exchange-traded fund has been a massive hit since launch, pulling in billions from investors seeking exposure to the cryptocurrency without the hassle of crypto wallets or exchanges. Traders and analysts religiously track inflows into the fund to gauge how institutions are positioning in the market.
Now they might have to do the same with options tied to the ETF, as activity exploded during Thursday’s crash. According to one observer, the record activity stemmed from a hedge fund blowup, while others disagreed, citing routine market chaos as a catalyst.
What really stood out
On Friday, as the ETF tanked 13% to its lowest level since October 2024, options volume exploded to a record 2.33 million contracts, with puts narrowly outpacing calls.
The fact that puts saw more volume than calls on Thursday indicates a higher demand for downside protection, a typical occurrence during price sell-offs.
Options are derivative contracts that provide built-in insurance against swings in the price of the underlying asset, in this case, IBIT. You pay a small fee (premium) for the right, but not the obligation, to buy or sell IBIT at a set price by a deadline or expiry.
A call option lets you lock in IBIT at a set price today for a small premium. If it rallies above that level later, you buy cheap and sell for profit; if not, you only lose the premium. A put option locks in the sale of IBIT at that price. If it slides below, you sell high and pocket the difference; otherwise, you lose just the premium. Calls offer leveraged upside bets, while puts protect against downside drops.
Another standout figure was the record $900 million in premiums paid by IBIT options buyers that day—the highest single-day total ever. To put it in context, that’s equivalent to the market cap of several crypto tokens ranking beyond the top 70.
Speculative theory: record activity tied to hedge fund blowup
A post by market analyst Parker, which has gone viral on X, argues that the $900 million premium payments resulted from the blowup of a large hedge fund (one or a few) with nearly 100% of money invested in IBIT. Funds often focus on just one asset, avoiding spreading out risk exposure elsewhere.
Parker’s post alleges that this fund initially bought cheap “out of the money” call options on IBIT following the October crash, anticipating a quick recovery and bigger rally.
These OTM calls are like cheap lottery tickets at levels well above the ongoing price of the underlying asset. If the asset rallies past these levels, these calls make significant money; if it doesn’t, buyers of these calls lose the initial premium paid.
However, the fund bought these calls using borrowed money. As IBIT continued to drop, they doubled down on their bet.
On Thursday, as IBIT crashed, these calls tanked in value and brokers hit the fund with margin calls demanding cash/collateral. The fund, having bled money elsewhere, was unable to provide the same and ended up dumping large amounts of IBIT shares in the market, resulting in a record $10 billion spot volume.
The fund also desperately replaced expiring calls or closed loss-making calls, resulting in a record $900 million in total premium payments. Essentially, Parker associates the record activity with one or a few massive players scrambling, not routine trading.
Shreyas Chari, director of trading and head of derivatives at Monarq Asset Management put it best: “Systematic selling across the majors yesterday probably tied to margin calls especially in the ETF with the highest crypto exposure IBIT.”
“Rumors swirled of a short options entity that had to sell the underlying far more aggressively after 70k and then 65k broke, probably tied to liquidation levels. This exacerbated the move down to 60k,” he explained in a Telegram chat.
Options expert disagrees
Tony Stewart, founder of Pelion Capital and an options expert, believes IBIT options added to the market chaos, but doesn’t go so far as to blame a single fund blowup for the whole crash and record activity.
He argued on X, citing Amberdata, that $150 million of the $900 million in premiums came from buying back put options. In short, traders who had previously sold (shorted) puts faced significant losses as IBIT crashed and those puts surged in value, so they repurchased them to cut their risk.
Those were “certainly painful” closes, he said on X, adding that the remaining portion of the $900 in premiums comprised mostly smaller trades, which is pretty standard for the hectic trading day.
In essence, to Stewart, the record activity is just the messy noise of a broadly panicked market, not a smoking gun pointing to a single way. “This [hedge fund blowup theory] is inconclusive from the Options standpoint. It also doesn’t seem enough tbh in size,” he concluded.
Still, he acknowledged the possibility that some activity could have been hidden in over-the-counter (privately negotiated) deals.
Conclusion
While Parker connected the dots to point to a hedge fund blowup, Stewart challenged the same with hard data.
In any case, this episode highlights that IBIT options are now large enough to wield influence, and traders might want to keep track of them just as they do ETF inflows.
Crypto World
Ethereum’s Vitalik Buterin Makes a New Bet on Zcash and Privacy
Ethereum founder Vitalik Buterin has donated to Shielded Labs, backing development of Crosslink, a proposed consensus upgrade for Zcash.
The move signals a deepening commitment by Buterin to privacy-preserving infrastructure, as well as growing interest in strengthening finality and settlement guarantees in proof-of-work blockchains.
Sponsored
Vitalik Doubles Down on Privacy Infranstructure in Crypto
Shielded Labs is developing Crosslink, a parallel finality layer designed to sit on top of Zcash’s existing proof-of-work consensus.
In simple terms, Crosslink adds a second confirmation system that locks in transactions faster and more decisively. This reduces the risk of chain reorganizations, rollbacks, and double-spend attacks.
As a result, exchanges can shorten confirmation times, cross-chain bridges gain stronger security guarantees, and applications become easier to build on Zcash.
Sponsored
What Shielded Labs Does for Zcash
Shielded Labs is a Zcash-focused research and engineering group working on core protocol upgrades rather than applications or tooling.
Its mandate centers on improving Zcash’s long-term security, usability, and cryptographic guarantees—especially around shielded transactions and privacy-first design.
Buterin’s support comes amid a broader shift in his public advocacy toward privacy and resilience over growth metrics or convenience.
In recent months, he has repeatedly argued that blockchains must optimize for worst-case scenarios, not best-case user experience.
That includes resisting censorship, minimizing trust assumptions, and protecting users even under hostile conditions.
Sponsored
Privacy, in that framing, is not optional. It is core infrastructure.
The Privacy Push Is More Critical Than Ever
Buterin has warned that financial transparency without strong cryptographic privacy creates long-term risks, including surveillance, coercion, and systemic fragility.
He has increasingly praised systems that embed privacy at the protocol level rather than layering it on as an optional feature. Zcash’s shielded transaction model aligns closely with that philosophy.
Sponsored
By backing Shielded Labs, Buterin is effectively endorsing privacy-preserving design paired with stronger settlement guarantees—two areas he sees as underinvested across the industry.
A Signal to the Broader Crypto Ecosystem
The donation also lands at a moment when Ethereum itself is reassessing parts of its scaling and security roadmap.
While Buterin has criticized superficial innovation and “copy-paste” infrastructure elsewhere, his support for Zcash highlights what he sees as meaningful progress: protocol-level upgrades that improve safety, finality, and user protection.
In that sense, the move is less about Ethereum versus Zcash—and more about the kind of blockchain architecture Buterin believes will survive long term.
Crypto World
RNBW Tanks 65% Below ICO Price on First Day of Trading
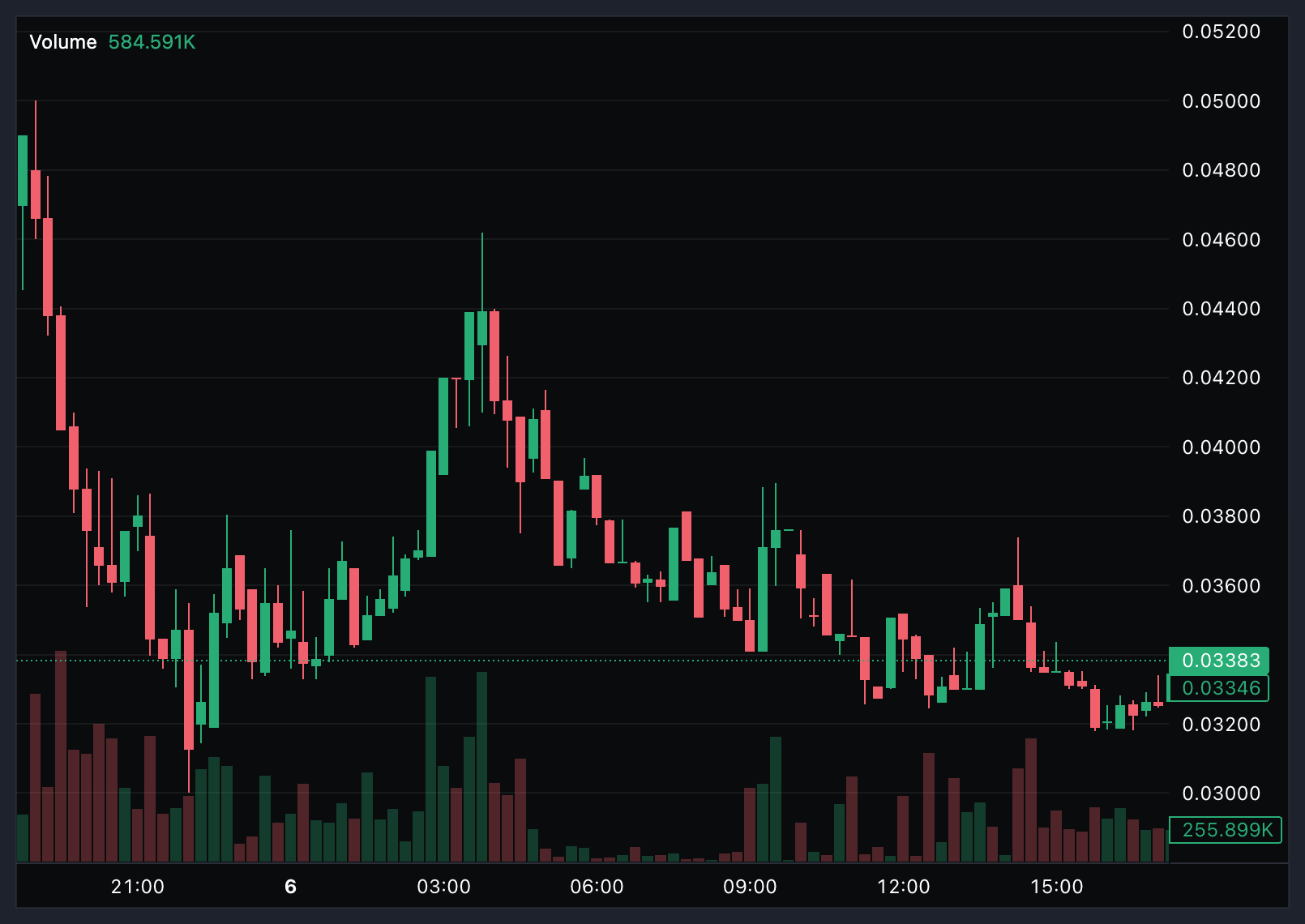
The launch was plagued by reports of delayed token distribution to early investors and technical issues.
Self-custodial Ethereum wallet Rainbow debuted its native token RNBW yesterday, Feb. 5. But the project’s token generation event (TGE) on Base, and the token’s debut for trading across exchanges, were met with reports of delayed distribution to ICO participants, which contributed to the token’s poor day-one performance.

According to Coinbase data, RNBW hit a high of $0.05 on its first day of trading, but fell quickly and closed the daily session around $0.034, down more than 30%, putting its fully diluted valuation around $34 million.
That left most bettors on Polymarket scrambling, having expected the FDV to hit roughly $100 million just a day after the TGE.
Today, RNBW fell further, trading around $0.032 by press time, making its FDV around $32.17 million.
ICO Investors in the Red
The price is far below what early buyers paid. Rainbow conducted its initial coin offering (ICO) in mid-December 2025 via CoinList, where investors were offered RNBW at $0.1 per token. The sale saw 30 million RNBW tokens, or 3% of total supply, sold at an FDV of $100 million, meaning participants in that sale are now down more than 65% on their investments.
For U.S. investors, the situation could be even worse as their full token unlock won’t happen until December of this year, according to CoinList’s terms and conditions.
Back in 2022, Rainbow raised $18 million in a Series A funding round led by Seven Seven Six, the VC firm from Reddit co-founder Alexis Ohanian, bringing total funding to $21 million. The multi-chain wallet is known for its rewards program and gamification, where users can earn points for their on-chain activity.
The firm explicitly connected RNBW with its points system when it first announced the token in September, and later specified that users who earned points in the wallet were eligible for a token airdrop.
‘No Better Day for TGE’
The token’s drop came amid a broader market bloodbath that wiped out $2.6 billion in liquidations in a single day. Total crypto market capitalization fell to $2.3 trillion as Bitcoin slid toward $60,000, reaching roughly 50% below its all-time high of $126,080, set in October.
Soon after its TGE, Rainbow’s cofounder Mike Demarais indicated in an X post that some users had not received their claimed tokens, explaining “it’s because our backend token indexer has been getting slammed.”
As frustration over the messy launch mounted, Rainbow CEO Alex LaPrade took to X on Thursday evening eastern time to say he still believes “there was no better day for TGE than today,” noting that the project had planned to launch its token on Feb. 5 back in December. LaPrade added:
“TGE isn’t the finish line. Having a token live in market brings more scrutiny — both positive and negative.”
But the CEO’s public statement didn’t succeed in calming all investors. Some quickly fired back at the CEO, accusing the project of late token distribution to CoinList pre-sale participants, as well as to points earners, calling it a scam and demanding refunds.
Last year, MetaMask confirmed that it has plans to launch its own token, after years of hinting and speculation.
Crypto World
Bitcoin price bounces from multi-year channel support, is the bottom in?
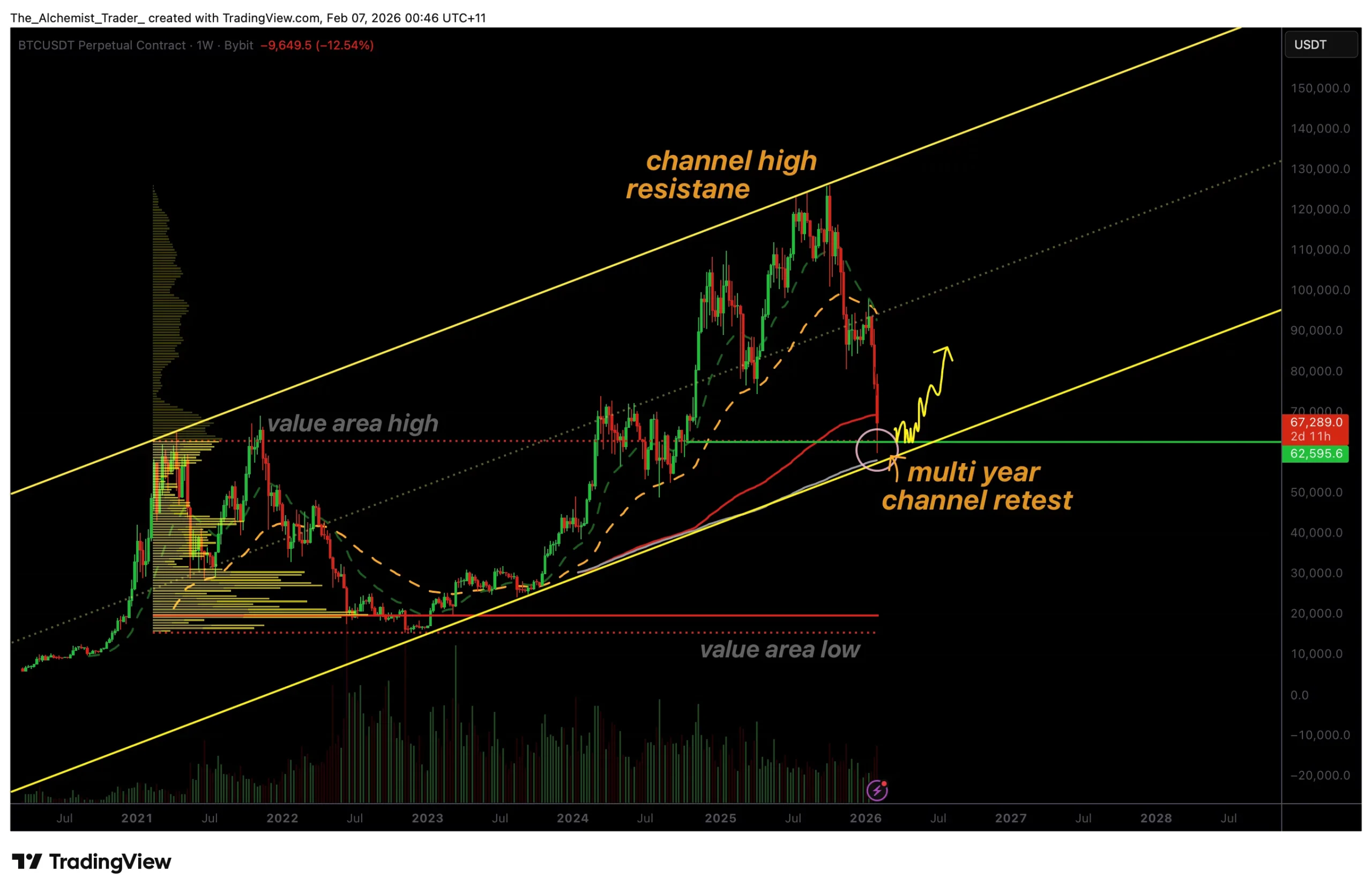
Bitcoin price has rebounded from a critical multi-year channel support near $62,500, raising the question of whether a high-timeframe bottom may be forming.
Summary
- $62,500 marks multi-year channel support, active since March 2021
- Confluence with value area high strengthens the bounce, increasing reaction probability
- Accumulation is required, to confirm a sustainable move toward the channel midpoint
Bitcoin (BTC) price action has recently reacted from a major technical support zone that has defined market structure for several years. After an extended bearish expansion, BTC has revisited the lower boundary of a multi-year ascending channel that has remained intact since March 2021. This reaction has drawn renewed attention from traders, as the level coincides with additional technical confluence that historically has led to meaningful high-timeframe pivots.
While short-term volatility remains elevated, the broader structure suggests Bitcoin may be entering a critical decision phase. Whether this bounce develops into a sustained recovery or fails into another leg lower will largely depend on how the price behaves around this key support region in the coming sessions.
Bitcoin price key technical points
- $62,500 aligns with multi-year channel low, active since March 2021
- Confluence with value area high strengthens support, increasing reaction probability
- Accumulation behavior is needed, to confirm a sustainable rotation higher
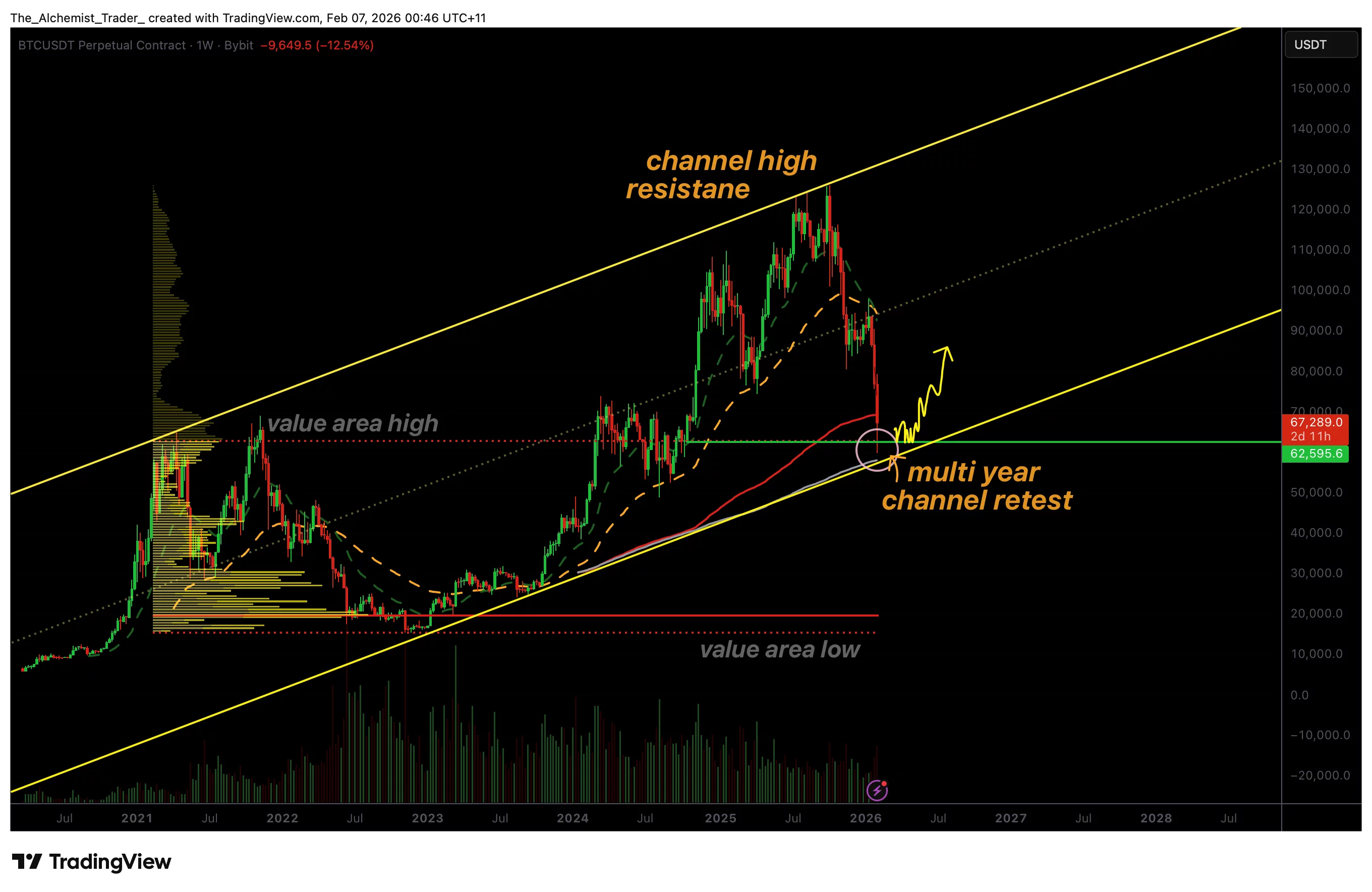
From a higher-timeframe perspective, Bitcoin’s current location is technically significant. The multi-year channel, which has guided price action since early 2021, has consistently acted as both support and resistance during major market cycles. Each historical retest of the channel’s lower boundary has resulted in strong reactions, often marking the transition from bearish phases into broader recovery structures.
The recent bounce from the $62,500 region once again highlights the importance of this channel. This level not only represents the channel low but also aligns with the value area high of the prior range, adding further structural relevance. When multiple high-timeframe levels converge, the probability of a meaningful reaction increases substantially.
Importance of holding value area support
Beyond the channel structure, Bitcoin’s ability to hold above the value area high is a key factor in determining whether this move can evolve into a sustained rotation. Acceptance above this region suggests that buyers are willing to transact at higher prices following the recent sell-off, a necessary condition for trend stabilization.
If price continues to defend this zone on a closing basis, it reinforces the idea that the recent bearish expansion may be transitioning into a consolidation or accumulation phase. Failure to hold, however, would indicate that demand remains insufficient and could expose Bitcoin to another test of lower liquidity zones.
Accumulation phase remains the missing piece
Although the initial bounce is technically constructive, confirmation remains incomplete without evidence of accumulation. Accumulation phases typically follow sharp bearish expansions and are characterized by sideways price action, declining volatility, and gradual absorption of supply by stronger hands.
In Bitcoin’s case, such a phase would help establish a durable base around the $62,000–$63,000 region. Without this basing behavior, any upside movement risks being corrective rather than trend-defining. Traders should closely monitor volume behavior, as rising participation during consolidation signals increasing confidence among buyers.
Potential rotation toward channel midpoint
If accumulation develops and support remains intact, the technical roadmap opens the door to a rotational move toward the midpoint of the multi-year channel. Historically, these rotations have provided substantial upside opportunities, particularly when initiated from channel extremes.
However, it is important to distinguish between a rotation and a full trend reversal. While a move toward the channel midpoint would be constructive, reclaiming higher resistance levels would still be required to confirm a broader bullish continuation.
What to expect in the coming price action
From a market structure, price action, and support perspective, the $62,000–$62,500 region represents a pivotal zone for Bitcoin. Holding above this level keeps the multi-year channel intact and supports the case for a developing bottom. A failure to maintain support would invalidate the bullish rotation thesis and reopen downside risk.
For now, Bitcoin remains at a high-timeframe inflection point. Confirmation through basing, accumulation, and improving volume will be essential before declaring a definitive bottom. Until then, traders should expect volatility and remain focused on how price behaves around this critical support zone.
-

 Video4 days ago
Video4 days agoWhen Money Enters #motivation #mindset #selfimprovement
-

 Tech3 days ago
Tech3 days agoWikipedia volunteers spent years cataloging AI tells. Now there’s a plugin to avoid them.
-

 Politics5 days ago
Politics5 days agoSky News Presenter Criticises Lord Mandelson As Greedy And Duplicitous
-

 Crypto World7 days ago
Crypto World7 days agoU.S. government enters partial shutdown, here’s how it impacts bitcoin and ether
-

 Sports6 days ago
Sports6 days agoSinner battles Australian Open heat to enter last 16, injured Osaka pulls out
-
 Crypto World6 days ago
Crypto World6 days agoBitcoin Drops Below $80K, But New Buyers are Entering the Market
-

 Tech8 hours ago
Tech8 hours agoFirst multi-coronavirus vaccine enters human testing, built on UW Medicine technology
-
 Crypto World5 days ago
Crypto World5 days agoMarket Analysis: GBP/USD Retreats From Highs As EUR/GBP Enters Holding Pattern
-
Sports18 hours ago
New and Huge Defender Enter Vikings’ Mock Draft Orbit
-

 NewsBeat13 hours ago
NewsBeat13 hours agoSavannah Guthrie’s mother’s blood was found on porch of home, police confirm as search enters sixth day: Live
-

 Business1 day ago
Business1 day agoQuiz enters administration for third time
-

 NewsBeat4 days ago
NewsBeat4 days agoUS-brokered Russia-Ukraine talks are resuming this week
-

 Sports5 days ago
Sports5 days agoShannon Birchard enters Canadian curling history with sixth Scotties title
-

 NewsBeat5 days ago
NewsBeat5 days agoGAME to close all standalone stores in the UK after it enters administration
-

 NewsBeat2 days ago
NewsBeat2 days agoStill time to enter Bolton News’ Best Hairdresser 2026 competition
-

 Crypto World3 days ago
Crypto World3 days agoRussia’s Largest Bitcoin Miner BitRiver Enters Bankruptcy Proceedings: Report
-

 NewsBeat51 minutes ago
NewsBeat51 minutes agoDriving instructor urges all learners to do 1 check before entering roundabout
-

 Crypto World1 day ago
Crypto World1 day agoHere’s Why Bitcoin Analysts Say BTC Market Has Entered “Full Capitulation”
-
 Crypto World1 day ago
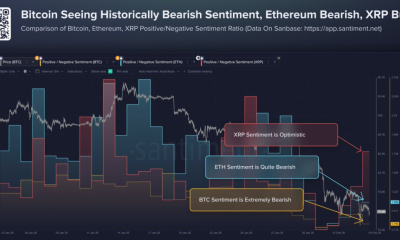
Crypto World1 day agoWhy Bitcoin Analysts Say BTC Has Entered Full Capitulation
-

 NewsBeat4 days ago
NewsBeat4 days agoImages of Mamdani with Epstein are AI-generated. Here’s how we know













