Crypto World
BTC and XRP Crash Over? Analyst Pinpoints Exact Rebound Timeline


The timeframe might be shorter than you expect.
The cryptocurrency market is bleeding out once again, led by bitcoin’s decline to under $67,000 for the first time since last Friday’s calamity.
However, one analyst believes there’s finally good news for BTC and XRP, and he even provided a more precise timing for the potential rebound.
The primary cryptocurrency has been in a free-fall state for weeks. It stood over $90,000 on January 28, but dumped by $30,000 since then to bottom out, at least for now, at $60,000 last Friday.
It tried to recover some ground since then and tapped $72,000 on a couple of occasions, but was stopped yesterday again and driven to under $67,000 as of press time.
Approximately at the time when the latest correction took place, popular analyst Ali Martinez said on X that the early TD Sequential buy signal had flashed for BTC. Moreover, he was precise with the timing of the potential rebound, claiming that it could be in the next 3-9 days.
Early TD Sequential buy signal on Bitcoin $BTC, suggesting a potential rebound could take shape over the next 3–9 days. pic.twitter.com/E1poXoOcNI
— Ali Charts (@alicharts) February 10, 2026
The metric, developed by Tom DeMark, identifies potential market reversal points, usually after a strong move in either direction. Martinez has frequently posted about the TD Sequential for several cryptocurrencies, and the indicator’s success rate has been rather impressive, especially for Ripple’s XRP.
You may also like:
Before the latest drop, the cross-border token also flashed a buy signal. Although it has since retraced by 3-4%, Martinez reminded that the TD Sequential has “perfectly timed” the local top for XRP in the past, and could signal a rapid rebound now.
The TD Sequential perfectly timed the local top on $XRP, and now it’s flashing a buy signal. pic.twitter.com/5FI3Pepsnz
— Ali Charts (@alicharts) February 10, 2026
SECRET PARTNERSHIP BONUS for CryptoPotato readers: Use this link to register and unlock $1,500 in exclusive BingX Exchange rewards (limited time offer).
Crypto World
North Korea Linked Hackers Deploy New Crypto Malware
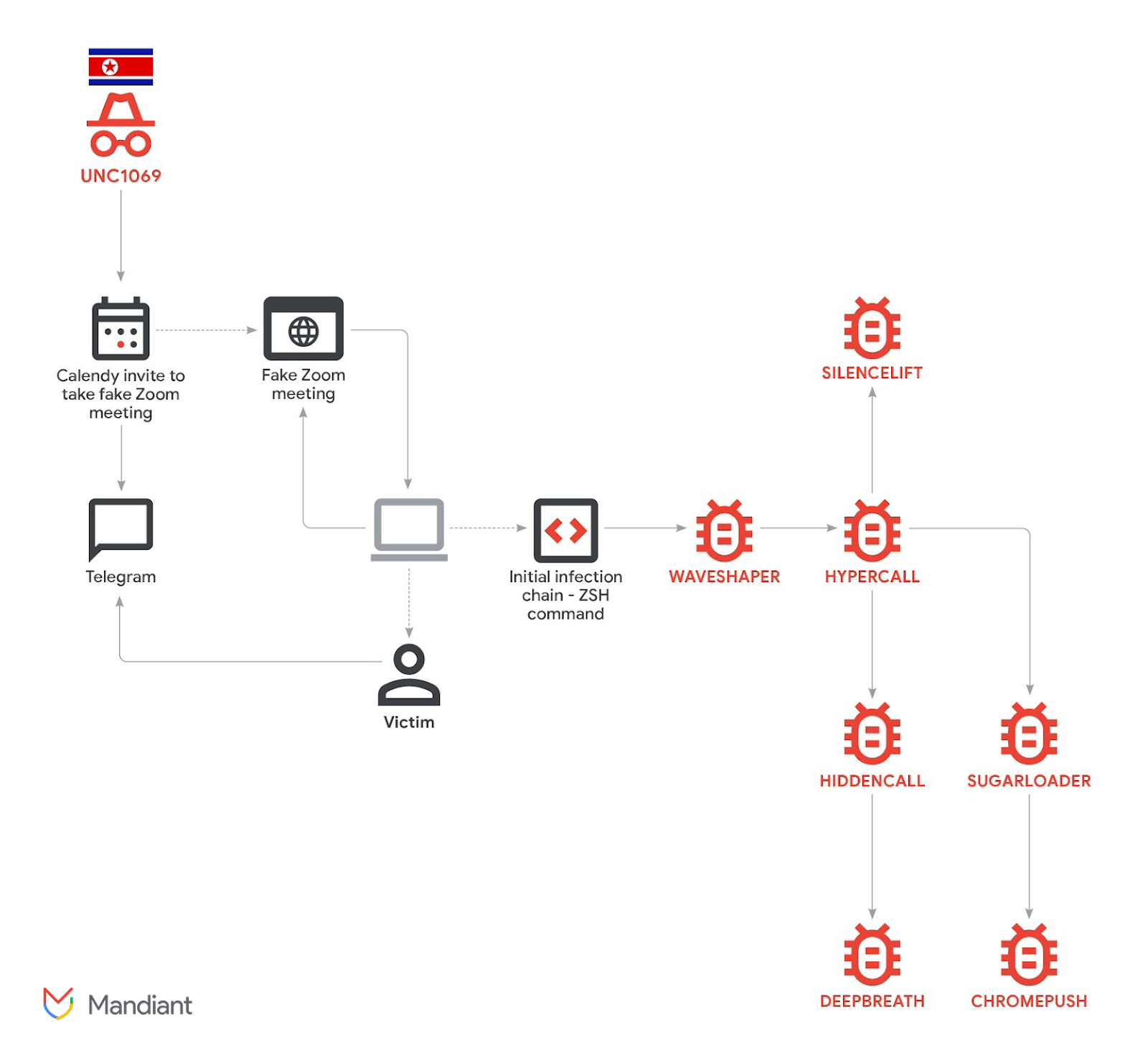
North Korea-linked threat actors are escalating social engineering campaigns targeting cryptocurrency and fintech companies, deploying new malware designed to harvest sensitive data and steal digital assets.
In a recent campaign, a threat cluster tracked as UNC1069 deployed seven malware families aimed at capturing and exfiltrating victim data, according to a Tuesday report from Mandiant, a US cybersecurity firm that operates under Google Cloud.
The campaign relied on social engineering schemes involving compromised Telegram accounts and fake Zoom meetings with deepfake videos generated through artificial intelligence tools.
“This investigation revealed a tailored intrusion resulting in the deployment of seven unique malware families, including a new set of tooling designed to capture host and victim data: SILENCELIFT, DEEPBREATH and CHROMEPUSH,” the report states.

Related: CZ sounds alarm as ‘SEAL’ team uncovers 60 fake IT workers linked to North Korea
Mandiant said the activity represents an expansion of the group’s operations, primarily targeting crypto firms, software developers and venture capital companies.
The malware included two newly discovered, sophisticated data-mining viruses, named CHROMEPUSH and DEEPBREATH, which are designed to bypass key operating system components and gain access to personal data.
The threat actor with “suspected” North Korean ties has been tracked by Mandiant since 2018, but AI advancements helped the malicious actor scale up its operations and include “AI-enabled lures in active operations” for the first time in November 2025, according to a report at the time from the Google Threat Intelligence Group.
Cointelegraph contacted Mandiant for additional details regarding the attribution, but had not received a response by publication.
Related: Balancer hack shows signs of months-long planning by skilled attacker
Attackers are stealing crypto founder accounts to launch ClickFix attacks
In one intrusion outlined by Mandiant, attackers used a compromised Telegram account belonging to a crypto founder to initiate contact. The victim was invited to a Zoom meeting featuring a fabricated video feed in which the attacker claimed to be experiencing audio problems.
The attacker then directed the user to run troubleshooting commands in their system to fix the purported audio issue in a scam known as a ClickFix attack.
The provided troubleshooting commands had embedded a hidden single command that initiated the infection chain, according to Mandiant.

North Korea-linked illicit actors have been a persistent threat to both crypto investors and Web3-native companies.
In June 2025, four North Korean operatives infiltrated multiple crypto firms as freelance developers, stealing a cumulative $900,000 from these startups, Cointelegraph reported.
Earlier that year, the Lazarus Group was linked to the $1.4 billion hack of Bybit, one of the largest crypto thefts on record.
Magazine: Coinbase hack shows the law probably won’t protect you — Here’s why
Crypto World
As bitcoin (BTC) price extends declines, industry figures say it’s time to buy: Crypto Daybook Americas
By Francisco Rodrigues (All times ET unless indicated otherwise)
Bitcoin dropped for a third straight day after failing to remain above the $70,000 hit during the weekend recovery as spot trading volumes thinned and theCrypto Fear and Greed Index held in “extreme fear” territory.
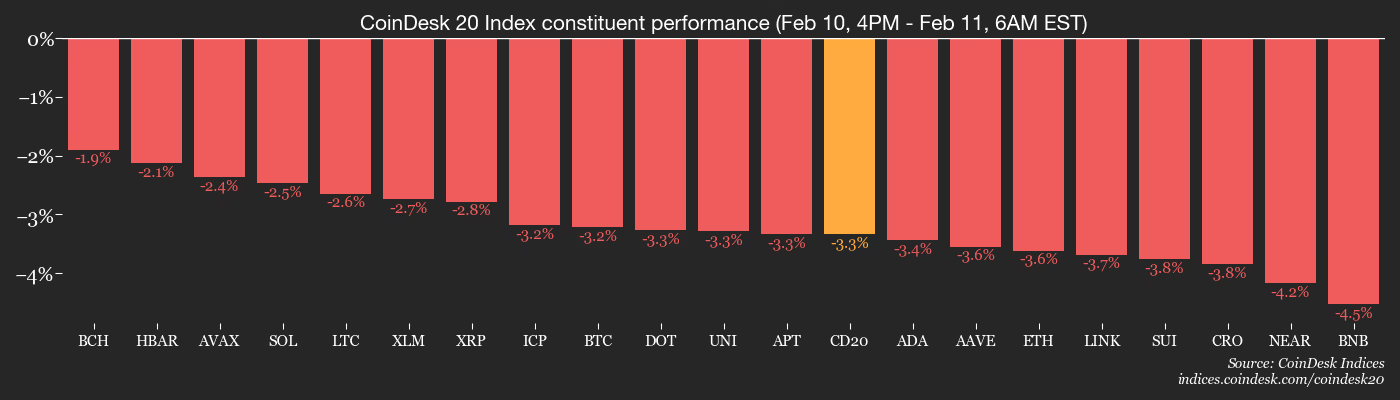
The broader crypto market capitalization has slipped to about $2.28 trillion, with the CoinDesk 20 (CD20) index losing 3.4% over the past 24 hours. Even so, onchain data aggregator Glassnode described the pullback as modest by past standards, with no signs of panic selling seen in prior cycle peaks.
Despite the lower volumes and poor sentiment, inflows to spot bitcoin ETFs have been steady over the past three days, helping absorb some selling pressure. The market is now in a price discovery phase, according to Wintermute.
“With spot volumes still relatively light, leverage is driving short term moves as was illustrated by BTC squeezing back up from the lows last friday on the back of heavily crowded perp shorts,” Wintermute desk strategist Jasper De Maere wrote in an emailed note. “It’s likely the market will continue to whip across this range as its still in price discovery.“
Major figures appear to remain bullish. Speaking at Consensus Hong Kong, Tom Lee, chief investment officer of Fundstrat and chairman of ether treasury firm BitMine Immersion (BMNR), told investors they should look for entry points rather than try to time a bottom.
On CNBC, Michael Saylor, executive chairman of bitcoin treasury firm Strategy (MSTR), reiterated his long-term bet on the cryptocurrency, saying he expects it to outperform traditional equities despite the drawdown.
Weak U.S. retail sales have moderately lifted U.S. interest rate-cut expectations and weighed on the dollar. Now, attention will switch to today’s nonfarm payrolls figures and inflation data, which could further influence risk appetite. Stay alert.
Read more: For analysis of today’s activity in altcoins and derivatives, see Crypto Markets Today
What to Watch
For a more comprehensive list of events this week, see CoinDesk’s “Crypto Week Ahead“.
- Crypto
- Feb. 11: Immutable to complete the merge of Immutable X and Immutable zkEVM.
- Macro
- Feb. 11, 8:30 a.m.: U.S. nonfarm payrolls for January Est. 70K (Prev. 50K)
- Feb. 11, 8:30 a.m.: U.S. unemployment rate for January Est. 4.4%(Prev. 4.4%)
- Feb. 11, 8:30 a.m.: U.S. average hourly earnings for January YoY Est. 3.8% (Prev. 3.6%)
- Earnings (Estimates based on FactSet data)
Token Events
For a more comprehensive list of events this week, see CoinDesk’s “Crypto Week Ahead“.
- Governance votes & calls
- Feb. 11: Ripple to host XRP Community Day on X Spaces discussing XRP adoption, regulated finance and innovation.
- Unlocks
- Token Launches
- Feb. 11: Coinbase to list RaveDAO (RAVE), DeepBook (DEEP), and Walrus (WAL).
Conferences
For a more comprehensive list of events this week, see CoinDesk’s “Crypto Week Ahead“.
Market Movements
- BTC is up 0.25% from 4 p.m. ET Tuesday at $66,868.63 (24hrs: -3.14%)
- ETH is down 2.96% at $1,947.84 (24hrs: -3.25%)
- CoinDesk 20 is down 2.75% at 1,900.89 (24hrs: -3.53%)
- Ether CESR Composite Staking Rate is up 1 bp at 2.83%
- BTC funding rate is at -0.0023% (-2.536% annualized) on Binance

- DXY is down 0.3% at 96.50
- Gold futures are up 1.73% at $5,117.80
- Silver futures are up 6.22% at $85.39
- Nikkei 225 closed up 2.28% at 57,650.54
- Hang Seng closed up 0.31% at 27,266.38
- FTSE is up 0.50% at 10,405.94
- Euro Stoxx 50 is down 0.41% at 6,022.26
- DJIA closed on Tuesday up 0.1% at 50,188.14
- S&P 500 closed down 0.33% at 6,941.81
- Nasdaq Composite closed down 0.59% at 23,102.47
- S&P/TSX Composite closed up 0.71% at 33,256.83
- S&P 40 Latin America closed down 0.57% at 3,746.47
- U.S. 10-Year Treasury rate is down 1 bps at 4.135%
- E-mini S&P 500 futures are unchanged at 6,966.50
- E-mini Nasdaq-100 futures are unchanged at 25,218.00
- E-mini Dow Jones Industrial Average Index futures are up 0.13% at 50,338.00
Bitcoin Stats
- BTC Dominance: 59.12% (-0.29%)
- Ether-bitcoin ratio: 0.02914 (-0.81%)
- Hashrate (seven-day moving average): 1,002 EH/s
- Hashprice (spot): $33.56
- Total fees: 2.6 BTC / $179,640
- CME Futures Open Interest: 120,785 BTC
- BTC priced in gold: 13.1 oz.
- BTC vs gold market cap: 4.46%
Technical Analysis

- BTC/USD is currently hovering below the 200-week exponential moving average, a critical support level that must be reclaimed to prevent further downside.
- The market now awaits the weekly close to confirm whether this breach marks a definitive breakdown or a temporary deviation.
Crypto Equities
- Coinbase Global (COIN): closed on Tuesday at $162.51 (-2.83%), -3.39% at $157.00 in pre-market
- Circle Internet (CRCL): closed at $59.75 (-0.58%), -1.84% at $58.65
- Galaxy Digital (GLXY): closed at $21.19 (+0.19%), -1.75% at $20.82
- Bullish (BLSH): closed at $32.05 (+0.00%), -1.68% at $31.51
- MARA Holdings (MARA): closed at $7.66 (-4.96%), -3.13% at $7.42
- Riot Platforms (RIOT): closed at $14.83 (-0.94%), -2.29% at $14.49
- Core Scientific (CORZ): closed at $18.13 (-2.26%), -2.48% at $17.68
- CleanSpark (CLSK): closed at $10.03 (-1.57%), -2.49% at $9.78
- CoinShares Valkyrie Bitcoin Miners ETF (WGMI): closed at $42.62 (-2.76%)
- Exodus Movement (EXOD): closed at $10.86 (+1.12%)
Crypto Treasury Companies
- Strategy (MSTR): closed at $133.00 (-3.93%), -3.12% at $128.85
- Strive (ASST): closed at $9.18 (-9.51%), -3.27% at $8.88
- SharpLink Gaming (SBET): closed at $6.65 (-6.47%), -0.60% at $6.61
- Upexi (UPXI): closed at $0.98 (-7.14%), +1.96% at $0.99
- Lite Strategy (LITS): closed at $1.03 (-1.90%)
ETF Flows
Spot BTC ETFs
- Daily net flows: $166.5 million
- Cumulative net flows: $54.98 billion
- Total BTC holdings ~1.27 million
Spot ETH ETFs
- Daily net flows: $13.8 million
- Cumulative net flows: $11.91 billion
- Total ETH holdings ~5.84 million
Source: Farside Investors
While You Were Sleeping
Crypto World
Ethereum price prediction amid aggressive whale accumulation near $2k

- Ethereum whales continue to aggressively accumulate ETH amid falling prices.
- The dip below $2,000 offers an attractive entry point for bulls.
- Ethereum price touched intraday lows of $1,930 on Wednesday, February 11, 2026.
Ethereum has dipped below the $2,000 level again, with a 3% decline in the past 24 hours pushing the top altcoin to lows of $1,930 in early trading on February 11, 2026.
The decline mirrored Bitcoin’s retreat below $67,000, with the bellwether digital asset down 3% over the same period, trading around $66,805.
But despite the strong bearish sentiment across the cryptocurrency market, whales appear unfazed and are using the dip to aggressively add to their positions.
Ethereum whales buy the dip near $2k
On-chain data shows Ethereum has attracted aggressive whale accumulation for several months, despite a sharp decline in the altcoin’s price.
According to details shared by CryptoQuant on X, large holders began ramping up their positions in July 2025.
This trend has continued even as the ETH price plunged from its peak amid a bearish flip in the last quarter of the year, with inflows into accumulation addresses hitting record highs amid sustained buying.
Notably, analysts say the loading up has continued after the ETH price fell below the realized value of accumulation addresses.
This scenario also played out in April 2025, when the Ethereum price plunged to lows of $1,470 amid a broader market correction.
However, bulls quickly recovered as whales bought the dip, and the altcoin’s price went on to touch its all-time high near $5,000 in August 2025.
Recent data shows exchange balances have fallen to multi-year lows, with whales adding to their holdings as retail sells amid broader market panic.
This pattern persists as prices falter in early 2026.
With whales’ buying power intact, current levels are attractive, which has seen entities like Bitmine Immersion Technologies fully take advantage.
The company recently added over 40,600 ETH and currently holds over 4.3 million Ether tokens acquired at an average price of $2,125.
Of this, it has staked over 2.97 million ETH, which accounts for more than 68% of its holdings.
Tom Lee(@fundstrat)’s #Bitmine is still buying $ETH and staking it.
5 hours ago, #Bitmine staked another 140,400 $ETH($282M).
In total, #Bitmine has staked 2.97M $ETH($6.01B), 68.7% of its total holdings.https://t.co/yCucFPLdGs pic.twitter.com/R13lzSIQmE
— Lookonchain (@lookonchain) February 11, 2026
Ethereum price prediction
The crypto fear and greed index hovers in extreme fear territory, which means a short-term bearish outlook.
Ethereum has tapped this sentiment as bulls struggle near $2,000, with the altcoin’s current dollar value more than 60% down since touching the all-time high near $5,000.
On the technical front, prices are below key exponential moving averages (EMAs), and oscillators favour bears.
Ethereum charts formed a death cross in November.
This strengthened on February 5, 2026, when Bitcoin nosedived to $60k, and ETH plummeted past support at $2k to hit new lows near $1,740.
Despite a rebound to above $2k, downward pressure remains, and a pullback to that year-to-date low is possible.
If bears take further control, ETH could target $1,500-$1,300 next.

However, aggressive buying even as ETH falls below realized prices of accumulation addresses indicates a long-term conviction.
Analysts forecast a significant rebound, with institutional demand and network growth driving the next leg up.
On-chain metrics, including ETF inflows, will be key.
Notably, outflows have shrunk since the $1.4 billion in monthly flows exited Ethereum spot ETFs in November 2025, and the current total net assets sit at over $11.7 billion.
Recently, Bitmine’s Tom Lee said he expects a V-shaped recovery for ETH.
Crypto World
Aviva Investors to tokenize funds on XRP Ledger in Ripple partnership


Aviva Investors, the asset management arm of U.K. insurer Aviva (AV), plans to tokenize traditional fund structures on the XRP Ledger (XRPL) in a deal with blockchain firm Ripple, the companies said in a press release Wednesday.
The collaboration will see Ripple support Aviva Investors in issuing and managing tokenized funds on XRPL, a public blockchain designed for payments and financial transactions. The move marks Aviva Investors’ first foray into tokenization as it looks to integrate blockchain-based products into its lineup.
For Ripple, the agreement is a first partnership with a Europe-based investment manager, expanding its push to bring regulated financial assets onchain.
Asset managers have increasingly turned to tokenization to modernize fund infrastructure, using digital tokens to represent shares in money market funds, private credit, real estate and other strategies on a blockchain.
The approach promises faster settlement, lower operational costs and broader distribution, while enabling features such as fractional ownership and automated compliance.
Major firms including BlackRock, Franklin Templeton and Hamilton Lane have already introduced tokenized products, signaling a shift from pilot projects to live, regulated offerings aimed at institutional investors.
Aviva Investors and Ripple said they will work together through 2026 and beyond to develop tokenized fund structures on XRPL.
The ledger, which started up in 2012, has processed more than 4 billion transactions and supports over 7 million wallets, according to Ripple. It is maintained by 120 independent validators and does not rely on energy-intensive mining.
“We believe there are many benefits that tokenisation can bring to investors, including improvements in terms of both time and cost efficiency,” said Jill Barber, chief distribution officer at Aviva Investors, in the release.
“We are committed to adopting technological advancements that we believe can bring about positive change for our business, and we think tokenized funds can be hugely beneficial to our clients,” she added.
Read more: Tokenization still at start of hype cycle, but needs more use cases, specialists say
Crypto World
Sam Bankman-Fried Accuses DOJ of silencing witnesses, targets judge in new trial bid


FTX founder Sam Bankman-Fried has returned to social media, alleging that U.S. prosecutors improperly pressured witnesses during his criminal trial and arguing that his conviction should be overturned.
Summary
- Sam Bankman-Fried has resurfaced on X, alleging U.S. prosecutors improperly pressured witnesses during his FTX criminal trial and claiming the conviction should be overturned.
- He also called for U.S. District Judge Lewis Kaplan to recuse himself, accusing the judge of bias and prejudging defendants in his case.
- Reaction on X has been sharply negative, with users dismissing his claims and reiterating that misuse of customer funds constitutes fraud regardless of solvency.
Sam Bankman-Fried demands judge’s recusal
In a post published on X, Bankman-Fried claimed that “new evidence” shows the Biden administration’s Department of Justice threatened multiple witnesses into silence or encouraged them to change their testimony.
He said this alleged conduct undermines the integrity of the trial and warrants throwing out his conviction.
Bankman-Fried also called for U.S. District Judge Lewis Kaplan to recuse himself from ruling on the matter. He accused Kaplan of prejudging defendants and stacking proceedings against him, citing what he described as similar treatment toward former FTX executive Ryan Salame and U.S. President Donald Trump.
The comments follow Bankman-Fried’s recent legal filings seeking a new trial, in which his defense argues that jurors were denied access to exculpatory evidence and that the court improperly limited witness testimony.
His legal team has previously contended that key evidence related to FTX’s internal operations and bankruptcy process was excluded, weakening his ability to present a full defense.
At this stage, Bankman-Fried’s allegations remain unproven.
Bankman-Fried was convicted in 2023 on multiple counts of fraud and conspiracy tied to the collapse of FTX and is currently serving a lengthy federal prison sentence. His appeals and post-conviction motions remain ongoing, with courts yet to determine whether any procedural errors rise to the level required for a retrial.
Reaction on X has been swift and overwhelmingly hostile. Many users rejected Bankman-Fried’s claims outright, arguing that misappropriating customer assets constitutes fraud regardless of solvency, with one post likening it to theft even if the property is later returned.
Others responded more viscerally, using profanity and personal attacks to dismiss SBF’s credibility and citing sworn testimony from former associates as evidence against him, while some also questioned why he is still able to post publicly from jail following his unanimous conviction.
Crypto World
Binance and Franklin Templeton Enable Tokenized Money Market Funds as Institutional Trading Collateral

TLDR:
- Eligible clients can use Franklin Templeton’s tokenized money market funds as Binance trading collateral
- Assets remain in third-party Ceffu custody while value is mirrored within Binance’s trading environment
- Program reduces counterparty risk while enabling institutions to earn yield on collateral assets
- Initiative represents first concrete implementation of September 2025 strategic partnership agreement
Binance and Franklin Templeton have launched an institutional collateral program enabling tokenized money market fund shares as trading collateral.
The program allows eligible clients to use assets issued through Franklin Templeton’s Benji Technology Platform as off-exchange collateral on Binance.
This marks the first initiative under their strategic partnership announced in September 2025. The program aims to improve capital efficiency while reducing counterparty risk.
Off-Exchange Collateral Program Reduces Risk for Institutional Traders
The new program addresses a major challenge facing institutional market participants. Traders can now use tokenized money market fund shares as collateral without parking assets on an exchange.
The collateral value is mirrored within Binance’s trading environment through Ceffu’s custody infrastructure. Meanwhile, the actual tokenized assets remain securely held off-exchange in third-party custody.
This structure reduces counterparty risk for institutional clients. Traders earn yield on their money market fund holdings while supporting trading activity.
The arrangement eliminates choosing between custody security and trading flexibility. Institutions maintain regulatory protections on their assets throughout the process.
Ceffu, Binance’s institutional crypto-native custody partner, provides the underlying infrastructure. The custody layer enables assets to stay off-exchange while their value supports trading positions.
“Institutions increasingly require trading models that prioritize risk management without sacrificing capital efficiency,” said Ian Loh, CEO of Ceffu.
Binance announced the program launch on social media. The exchange highlighted that this initiative represents the first step under their collaboration with Franklin Templeton. The partnership focuses on bridging traditional finance with digital asset markets.
Traditional Finance and Digital Assets Converge Through Tokenization
Roger Bayston, Head of Digital Assets at Franklin Templeton, emphasized the partnership’s institutional focus. “Since partnering in 2025, our work with Binance has focused on making digital finance actually work for institutions,” Bayston said.
He added that the off-exchange collateral program lets clients put their assets to work in third-party custody while safely earning yield. That’s the future Benji was designed for, he noted.
Catherine Chen, Head of VIP & Institutional at Binance, described the collaboration as a natural progression. “Partnering with Franklin Templeton to offer tokenized real-world assets as off-exchange collateral is a natural next step in our mission,” Chen stated.
She explained that innovating ways to use traditional financial instruments on-chain opens new opportunities for investors. The approach shows how blockchain technology can make markets more efficient, according to Chen.
The program responds to institutional demand for specific collateral characteristics. Institutions seek stable, yield-bearing assets supporting continuous settlement cycles. Tokenized money market funds meet these requirements while fitting existing governance frameworks.
Market infrastructure must align with institutional standards to support broader adoption. Binance positions the program as meeting demand for stable collateral on regulated platforms.
Enhanced capital efficiency benefits traders managing positions across both traditional and digital markets.
Crypto World
Extreme FUD Persists on Social Media Despite BTC’s $60K Dip Recovery


Extreme FUD lingers after Bitcoin’s $60,000 rebound, with bearish social sentiment outweighing bullish posts.
Bitcoin (BTC) slipped back below $67,000 on Wednesday, February 11, extending a volatile stretch that began with last week’s drop to $60,000.
Despite that rebound from the lows, social data shows fear remains elevated, with traders split over whether the worst of the sell-off is over.
Social Sentiment Stays Bearish as Volatility Spikes
Data shared by on-chain analytics firm Santiment shows a high ratio of bearish to bullish posts even after Bitcoin recovered from its $60,000 dip. According to the firm, retail traders seem hesitant to buy at current levels, while larger holders are facing less resistance in accumulating during periods of fear.
Santiment added that, historically, rebounds have often followed spikes in fear, though it did not claim this guarantees a bottom.
Meanwhile, short-term price action is still fragile, with market watcher Ash Crypto reporting that Bitcoin’s fall below $67,000 had liquidated roughly $127 million in long positions within four hours.
At the time of writing, market data from CoinGecko showed BTC trading around the $66,700 region, down about 3% in the last 24 hours and nearly 13% on the week. Over the past 30 days, the flagship cryptocurrency has fallen more than 27%, and it remains 47% below its October 2025 all-time high.
The 24-hour range between $66,600 and $69,900 is a reflection of ongoing intraday swings, while weekly price action has spanned from about $62,800 to $76,500, showing just how unstable conditions are.
You may also like:
Volatility metrics support that view, with Binance data cited by Arab Chain analysts showing that Bitcoin’s seven-day annualized volatility has climbed to around 1.51, its highest reading since 2022. However, 30-day and 90-day measures remain lower at 0.81 and 0.56, suggesting recent turbulence has not yet evolved into a sustained high-volatility regime. According to the analysts, the average true range as a percentage sits near 0.075, which historically has been a compressed level that often comes right before a larger directional move.
Bear Market Comparisons Resurface
An earlier report this week noted that Bitcoin has closed three consecutive weeks below its 100-week moving average, a pattern seen in previous bear markets. CryptoQuant founder Ki Young Ju wrote on February 9 that “Bitcoin is not pumpable right now,” arguing that selling pressure is limiting upside follow-through.
Other commentators, including Doctor Profit, have described the current structure as a wide consolidation range between $57,000 and $87,000, warning that sideways trading could precede another leg lower.
Furthermore, macro data is adding to the cautious tone, with XWIN Research Japan writing that weaker U.S. retail sales and easing wage growth mean that consumption is slowing, which may weigh on risk assets in the short term. The firm also noted a persistently negative Coinbase Premium Gap since late 2025, suggesting there’s weak U.S. spot demand compared to derivatives-driven activity.
Yet not all industry voices are focused solely on price cycles, with WeFi’s Maksym Sakharov saying he believes Bitcoin sentiment will eventually strengthen despite falling prices, but for different reasons than in past rallies.
“I believe Bitcoin sentiment will turn even stronger despite the falling prices, but this time it won’t be only about price or speculation, but also about real adoption,” Sakharov said.
In the meantime, BTC is sitting in a narrow zone between fear-driven pessimism and technical support near $60,000, with traders watching whether high volatility resolves higher or breaks lower in the weeks ahead.
SECRET PARTNERSHIP BONUS for CryptoPotato readers: Use this link to register and unlock $1,500 in exclusive BingX Exchange rewards (limited time offer).
Crypto World
Franklin Templeton to Let Tokenized Money Funds Back Binance Trades

Global investment manager Franklin Templeton announced the launch of an institutional off‑exchange collateral program with Binance that lets clients use tokenized money market fund (MMF) shares to back trading activity while the underlying assets remain in regulated custody.
According to a Wednesday news release shared with Cointelegraph, the framework is intended to reduce counterparty risk by reflecting collateral balances inside Binance’s trading environment, rather than moving client assets onto the exchange.
Eligible institutions can pledge tokenized MMF shares issued via Franklin Templeton’s Benji Technology Platform as collateral for trading on Binance.
The tokenized fund shares are held off‑exchange by Ceffu Custody, a digital asset custodian licensed and supervised in Dubai, while their collateral value is mirrored on Binance to support trading positions.
Franklin Templeton said the model was designed to let institutions earn yield on regulated money market fund holdings while using the same assets to support digital asset trading, without giving up existing custody or regulatory protections.
Related: Franklin Templeton expands Benji tokenization platform to Canton Network
“Our off‑exchange collateral program is just that: letting clients easily put their assets to work in regulated custody while safely earning yield in new ways,” said Roger Bayston, head of digital assets at Franklin Templeton, in the release.

The initiative builds on a strategic collaboration between Binance and Franklin Templeton announced in 2025 to develop tokenization products that combine regulated fund structures with global trading infrastructure.
Off‑exchange collateral to cut counterparty risk
The design mirrors other tokenized real‑world asset collateral models in crypto markets. BlackRock’s BUIDL tokenized US Treasury fund, issued by Securitize, for example, is also accepted as trading collateral on Binance, as well as other platforms, including Crypto.com and Deribit.
That model allows institutional clients to post a low-volatility, yield‑bearing instrument instead of idle stablecoins or more volatile tokens.
Other issuers and venues, including WisdomTree’s WTGXX and Ondo’s OUSG, are exploring similar models, with tokenized bond and short‑term credit funds increasingly positioned as onchain collateral in both centralized and decentralized markets.
Related: WisdomTree’s USDW stablecoin to pay dividends on tokenized assets
Regulators flag cross‑border tokenization risks
Despite the trend of using tokenized MMFs as collateral, global regulators have warned that cross‑border tokenization structures can introduce new risks.
The International Organization of Securities Commissions (IOSCO) has cautioned that tokenized instruments used across multiple jurisdictions may exploit differences between national regimes and enable regulatory arbitrage if oversight and supervisory cooperation do not keep pace.
Cointelegraph asked Franklin Templeton how the tokenized MMF shares are regulated and protected and how the model was stress‑tested for extreme scenarios, but had not received a reply by publication.
Magazine: Getting scammed for 100 Bitcoin led Sunny Lu to create VeChain
Crypto World
Bank Negara Malaysia Plans to Launch Stablecoin and Tokenized Deposit Initiatives

TLDR
- Bank Negara Malaysia is testing ringgit stablecoins and tokenized deposits in 2026.
- Standard Chartered and Capital A lead the ringgit stablecoin project.
- The projects focus on improving wholesale payment systems.
- Maybank and CIMB are developing tokenized deposits for payments.
- BNM aims to assess financial stability and set policy by end of 2026
Bank Negara Malaysia (BNM) has revealed three new initiatives for 2026, focusing on digital assets such as ringgit stablecoins and tokenized deposits. The central bank’s Digital Asset Innovation Hub (DAIH) will evaluate these projects, focusing on their use in wholesale payment systems. BNM intends to assess the impact of these innovations on financial stability and will provide clarity by the end of 2026.
Malaysia Ringgit Stablecoin Settlement Project
One of the initiatives involves a ringgit stablecoin settlement system, developed by Standard Chartered Bank Malaysia in collaboration with Capital A. The project aims to streamline business-to-business transactions within Malaysia using a digital currency backed by the local currency.
The stablecoin system will be tested in a controlled environment, with both local and international corporate clients involved. The project will enable BNM to assess the effects of stablecoin use on monetary policy and financial stability.
It will also explore the potential for cross-border payments and integrate with the central bank’s other digital asset-related work. The project could pave the way for the adoption of stablecoins in Malaysia’s financial sector.
Tokenized Deposits for Payments
Another initiative focuses on tokenized deposits for payment systems, driven by two major banks: Maybank and CIMB. Both institutions will work on creating tokenized digital representations of deposits that can be used for payments.
These projects aim to modernize payment systems and provide efficient alternatives to traditional bank deposits. Testing will be conducted in partnership with financial institutions and other regulators to ensure that the systems meet regulatory standards.
BNM will evaluate how tokenized deposits impact payment flows and their integration with the broader financial ecosystem. The central bank expects the findings from these projects to inform future policy decisions by the end of 2026.
Crypto World
EU Parliament Backs Digital Euro to Bolster Payments Sovereignty
The European Parliament threw its weight behind the European Central Bank’s (ECB) digital euro project in a vote that framed money and payments as a strategic asset in an era of rising geopolitical tensions.
Lawmakers adopted the annual ECB report by 443 votes in favor, 71 against and 117 abstentions, backing amendments that describe the digital euro as “essential” to strengthening European Union monetary sovereignty, reducing fragmentation in retail payments and bolstering the integrity of the single market.
The text places growing emphasis on how public money in digital form can curb Europe’s reliance on non‑EU payment providers and private instruments.
Members of the European Parliament (MEPs) also underlined that the ECB must remain independent and free from political pressure, arguing that safeguarding central bank autonomy was key to maintaining price stability and market confidence.

During the plenary debate, Johan Van Overtveldt, MEP and former Belgian finance minister, flagged that “the independence of the ECB is not a technical detail.”
He warned that history showed political interference with central banks “invariably leads to inflation, financial instability and even nasty political turmoil.”
Related: EU council endorses offline and online versions of digital euro
He argued that reaffirming independence is “even more important in the current global context,” likening monetary and financial stability to utilities such as water and electricity whose importance is only truly noticed when they fail.
Digital euro as public good and geopolitical hedge
The adopted resolution states that, even as the ECB develops a digital euro, cash should retain an important role in the euro area economy, and both physical and digital euros will be legal tender.
The parliamentary backing comes amid a broader push by central bankers and economists to frame the digital euro as a public good and a geopolitical hedge.
Last month, ECB executive board member Piero Cipollone called the project “public money in digital form” and tied it directly to concerns about the “weaponisation of every conceivable tool.”
He argued that Europe needed a retail payment system “fully under our control” and built on European infrastructure rather than foreign schemes.
Earlier in January, 70 economists and policy experts urged MEPs to “let the public interest prevail” on the digital euro, warning that without a strong public option, private stablecoins and foreign payment giants could gain even greater influence over Europe’s digital payments, deepening dependencies in times of stress.
Magazine: How crypto laws changed in 2025 — and how they’ll change in 2026
-

 Politics3 days ago
Politics3 days agoWhy Israel is blocking foreign journalists from entering
-

 NewsBeat2 days ago
NewsBeat2 days agoMia Brookes misses out on Winter Olympics medal in snowboard big air
-

 Sports4 days ago
Sports4 days agoJD Vance booed as Team USA enters Winter Olympics opening ceremony
-
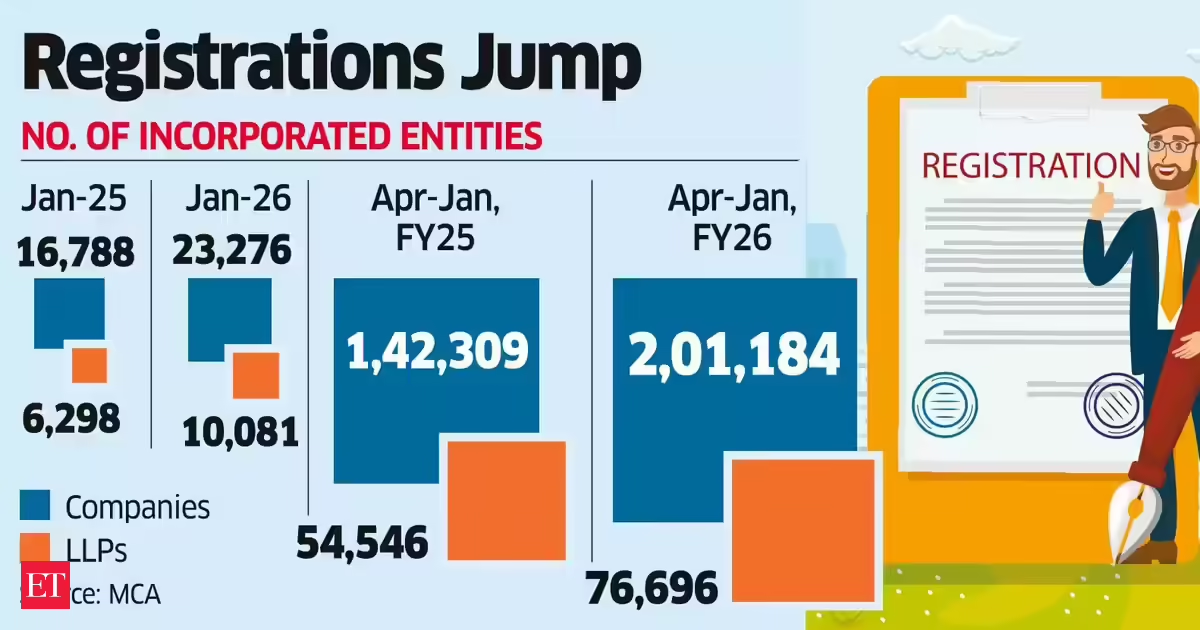
 Business3 days ago
Business3 days agoLLP registrations cross 10,000 mark for first time in Jan
-

 Tech5 days ago
Tech5 days agoFirst multi-coronavirus vaccine enters human testing, built on UW Medicine technology
-

 Tech9 hours ago
Tech9 hours agoSpaceX’s mighty Starship rocket enters final testing for 12th flight
-

 NewsBeat3 days ago
NewsBeat3 days agoWinter Olympics 2026: Team GB’s Mia Brookes through to snowboard big air final, and curling pair beat Italy
-

 Sports2 days ago
Sports2 days agoBenjamin Karl strips clothes celebrating snowboard gold medal at Olympics
-

 Politics3 days ago
Politics3 days agoThe Health Dangers Of Browning Your Food
-
Sports4 days ago
Former Viking Enters Hall of Fame
-
Sports5 days ago
New and Huge Defender Enter Vikings’ Mock Draft Orbit
-

 Business3 days ago
Business3 days agoJulius Baer CEO calls for Swiss public register of rogue bankers to protect reputation
-

 NewsBeat5 days ago
NewsBeat5 days agoSavannah Guthrie’s mother’s blood was found on porch of home, police confirm as search enters sixth day: Live
-

 Business6 days ago
Business6 days agoQuiz enters administration for third time
-

 Crypto World20 hours ago
Crypto World20 hours agoBlockchain.com wins UK registration nearly four years after abandoning FCA process
-
 Crypto World1 day ago
Crypto World1 day agoU.S. BTC ETFs register back-to-back inflows for first time in a month
-

 NewsBeat2 days ago
NewsBeat2 days agoResidents say city high street with ‘boarded up’ shops ‘could be better’
-
Sports2 days ago
Kirk Cousins Officially Enters the Vikings’ Offseason Puzzle
-
 Crypto World1 day ago
Crypto World1 day agoEthereum Enters Capitulation Zone as MVRV Turns Negative: Bottom Near?
-

 NewsBeat6 days ago
NewsBeat6 days agoStill time to enter Bolton News’ Best Hairdresser 2026 competition









