Crypto World
The Next Phase of Crypto Hacks May Start With a Video Call
A North Korea–nexus threat actor is enhancing its social engineering playbook. The group is integrating AI-enabled lures into crypto-focused hacks, according to a new report from Google’s Mandiant team.
The operation reflects a continued evolution in state-linked cyber activity targeting the digital asset sector, which saw a notable increase in 2025.
Sponsored
Sponsored
Fake Zoom Call Triggers Malware Attack on Crypto Firm
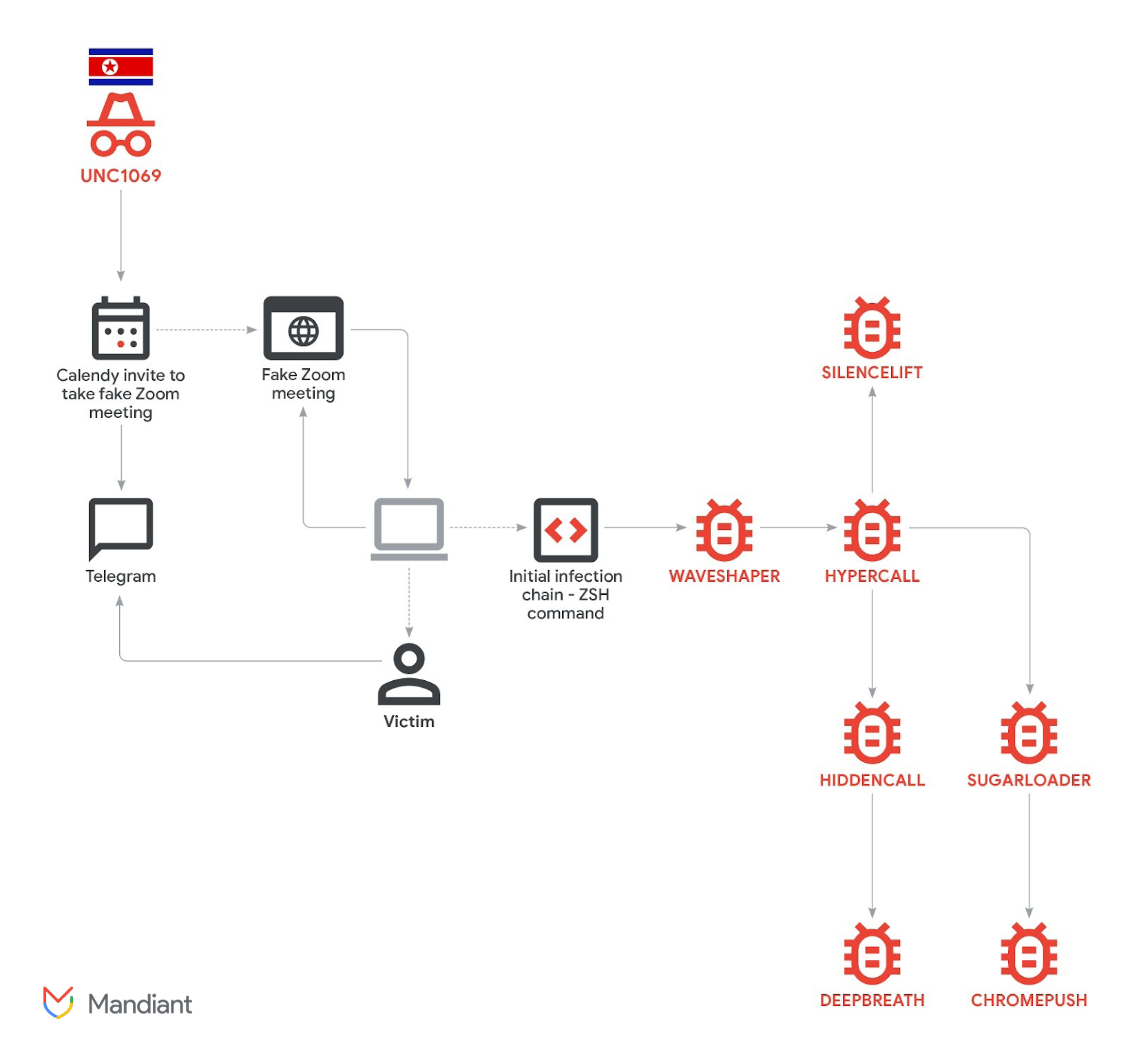
In its latest report, Mandiant detailed its investigation into an intrusion targeting a FinTech company in the cryptocurrency sector. The attack was attributed to UNC1069. It is a financially motivated threat group active since at least 2018, with links to North Korea.
“Mandiant has observed this threat actor evolve its tactics, techniques, and procedures (TTPs), tooling, and targeting. Since at least 2023, the group has shifted from spear-phishing techniques and traditional finance (TradFi) targeting towards the Web3 industry, such as centralized exchanges (CEX), software developers at financial institutions, high-technology companies, and individuals at venture capital funds,” the report read.
According to investigators, the intrusion began with a compromised Telegram account belonging to a crypto industry executive. The attackers used the hijacked profile to contact the victim. They gradually built trust before sending a Calendly invitation for a video meeting.
The meeting link directed the target to a fake Zoom domain hosted on infrastructure controlled by the threat actors. During the call, the victim reported seeing what appeared to be a deepfake video of a CEO from another cryptocurrency company.
“While Mandiant was unable to recover forensic evidence to independently verify the use of AI models in this specific instance, the reported ruse is similar to a previously publicly reported incident with similar characteristics, where deepfakes were also allegedly used,” the report added.
The attackers created the impression of audio problems in the meeting to justify the next step. They instructed the victim to run troubleshooting commands on their device.
Sponsored
Sponsored
Those commands, tailored for both macOS and Windows systems, secretly initiated the infection chain. This led to the deployment of multiple malware components.
Mandiant identified seven distinct malware families deployed during the intrusion. The tools were designed to steal Keychain credentials, extract browser cookies and login data, access Telegram session information, and collect other sensitive files.
Investigators assessed that the objective was twofold: to enable potential cryptocurrency theft and harvest data that could support future social engineering attacks.
The investigation revealed an unusually large volume of tooling dropped onto a single host. This suggested a highly targeted effort to harvest as much data as possible from the compromised individual.
The incident is part of a broader pattern rather than a standalone case. In December 2025, BeInCrypto reported that North Korean-linked actors siphoned more than $300 million by posing as trusted industry figures during fraudulent Zoom and Microsoft Teams meetings.
The scale of activity throughout the year was even more striking. In total, North Korean threat groups were responsible for $2.02 billion in stolen digital assets in 2025, a 51% increase from the previous year.
Chainalysis also revealed that scam clusters tied on-chain to AI service providers show significantly higher operational efficiency than those without such links. According to the firm, this trend suggests a future in which AI becomes a standard component of most scam operations.
With AI tools growing more accessible and advanced, creating convincing deepfakes is easier than ever. The coming time will test whether the crypto sector can adapt its security fast enough to confront these advanced threats.
Crypto World
Ethereum (ETH) Price Analysis: Whale Buying Intensifies as Network Staking Demand Explodes
Key Highlights
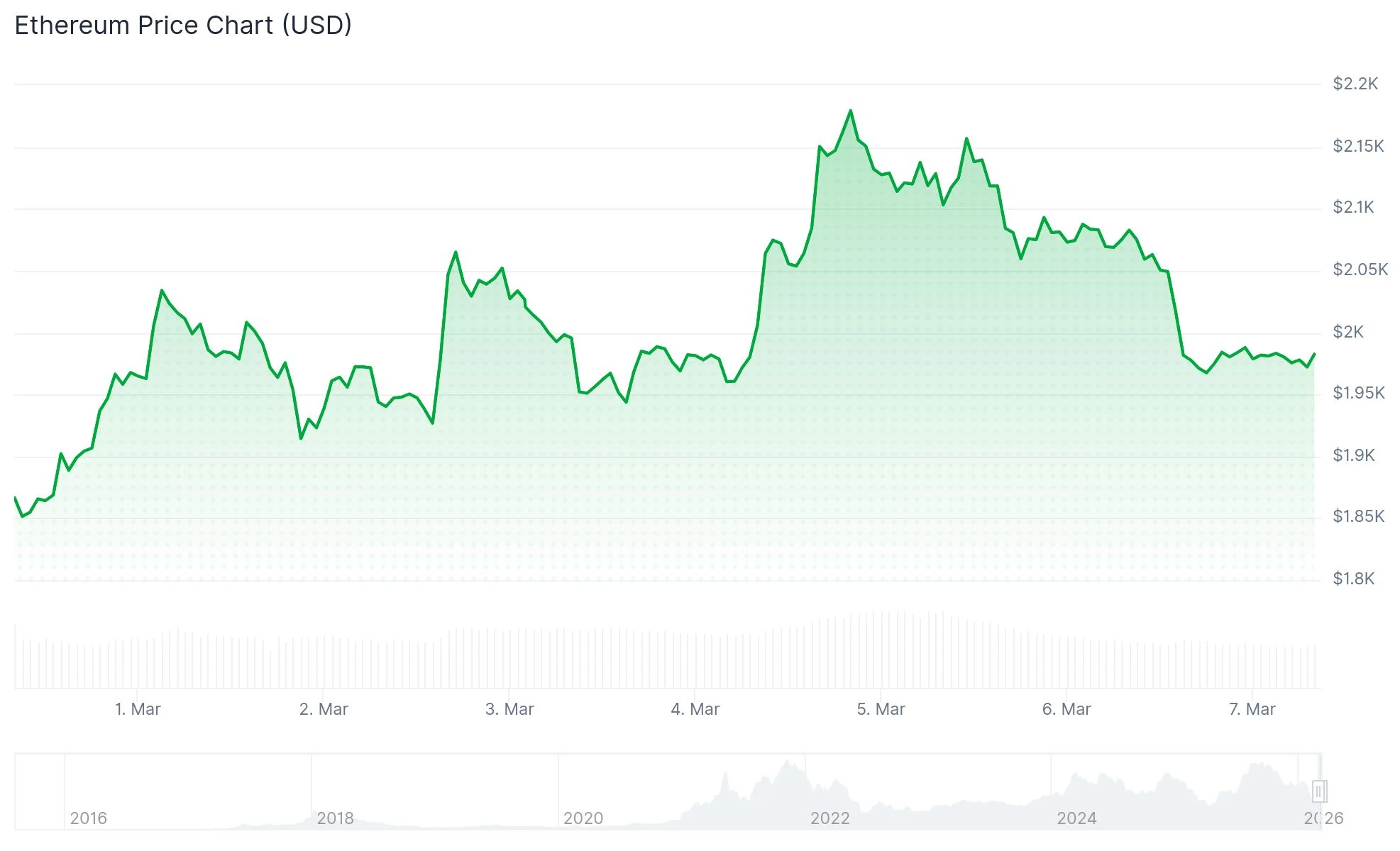
- ETH recovered from $1,830 lows to approach $2,200 before consolidating around the $2,000 zone
- Whale wallets and veteran holders continue accumulating at the current $2,000 support threshold
- Spot Ethereum ETFs in the United States experienced $90 million in net outflows over the past week
- The validator entry queue has exploded to 3.4 million ETH, a dramatic increase from 904,000 in early January
- Ethereum co-founder Vitalik Buterin unveiled the Minimmit proposal to streamline finality from two rounds to one
Ethereum’s recent price action has been marked by significant volatility. After dropping to approximately $1,830 in late February, the asset staged an impressive recovery, climbing to nearly $2,200. Following this rally, ETH has retraced and is currently consolidating around the psychologically important $2,000 threshold.
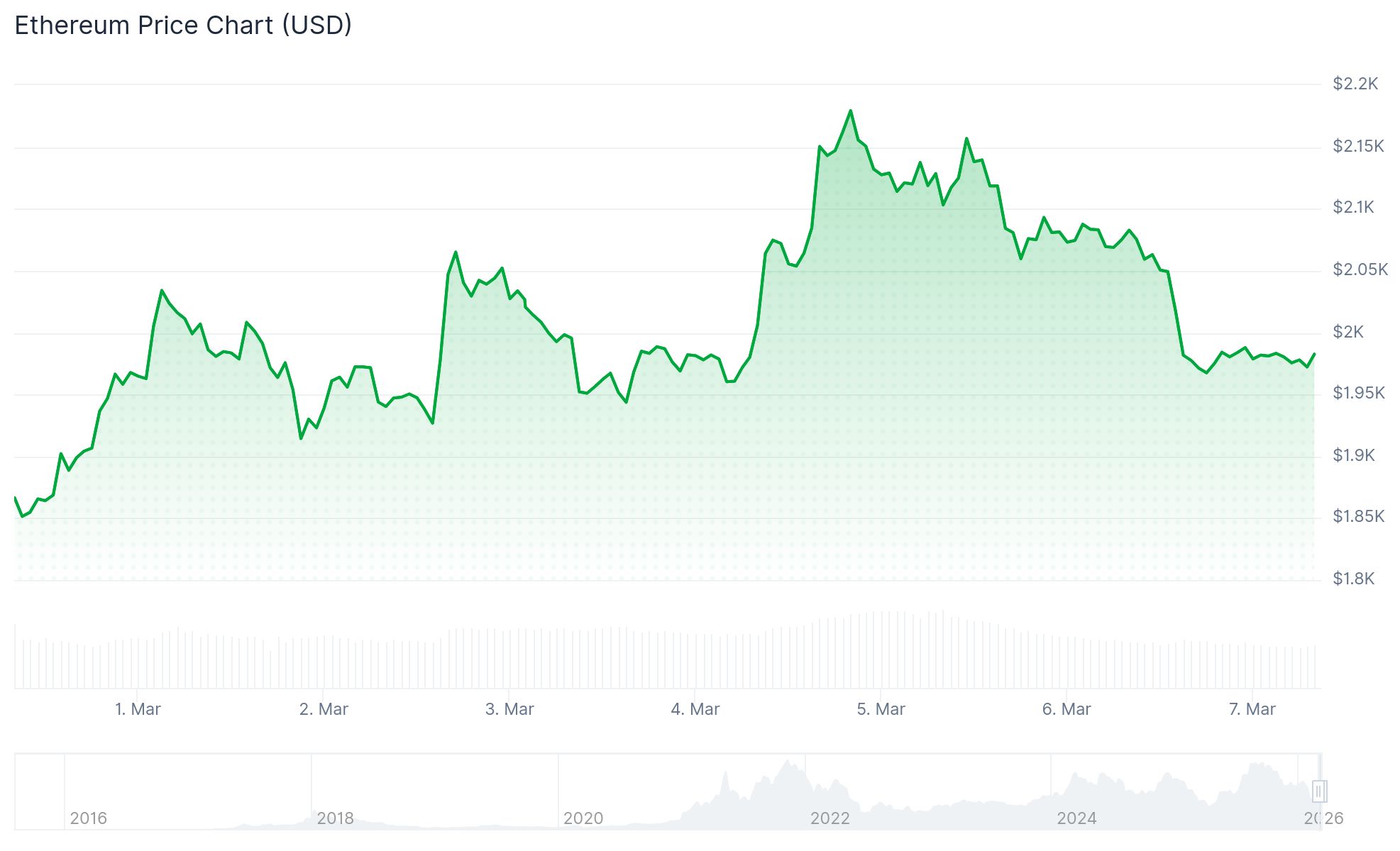
The $2,000 price point has emerged as a critical battleground. Blockchain analytics reveal that major wallet addresses have been accumulating during recent price weakness. Instead of distributing holdings, long-term market participants are increasing their positions. Futures market data indicates that derivatives traders maintain predominantly bullish positioning.
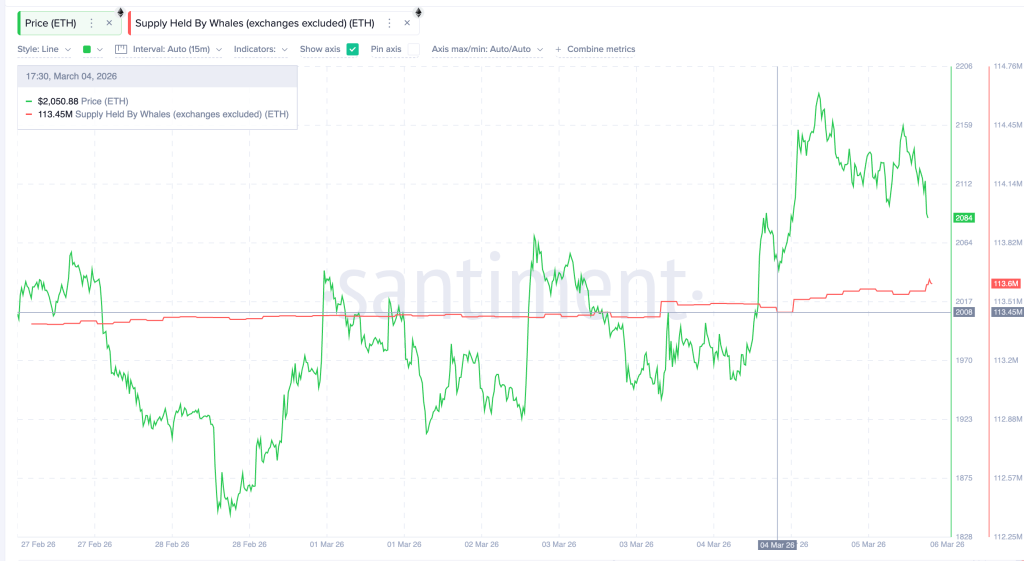
Analysis of cost-basis metrics reveals substantial ETH volume last changed hands near the $2,000 mark. This concentration suggests numerous investors have breakeven positions at current levels, creating a natural incentive to defend this price floor.
From a technical perspective, Ethereum is developing a converging wedge pattern. The asset attempted to breach $2,200 resistance but was rejected, establishing a lower peak. Meanwhile, an ascending support trendline continues to provide upside momentum. This compression pattern indicates an imminent breakout.
Should ETH successfully clear $2,200, technical analysts identify $2,400 and $2,750 as subsequent resistance targets. Conversely, a breakdown below $2,000 would likely expose support areas near $1,850 and $1,750.
Institutional ETF Withdrawals Create Headwinds
Spot Ethereum exchange-traded funds in the United States recorded $90 million in net withdrawals over the recent trading week. This outflow pattern suggests certain institutional participants are reducing their exposure. The capital exit has contributed to diminished near-term buying momentum.
The overall market sentiment remains measured. Macroeconomic uncertainties continue to influence investor behavior, with some large-scale market participants apparently trimming positions in anticipation of potential economic shifts.
Despite these challenges, Ethereum’s price has maintained its position above crucial long-term support levels. Bearish forces have been unable to trigger a more substantial downturn.
Technical indicators present a mixed picture. The Relative Strength Index currently sits at 49, indicating neutral momentum. The MACD remains in negative territory at -55.8. However, both the Commodity Channel Index and Stochastic Oscillator readings suggest building upward pressure.
Staking Demand Reaches Unprecedented Levels
Demand for Ethereum staking has accelerated dramatically. The validator activation queue has ballooned to 3.4 million ETH, representing a substantial increase from approximately 904,000 ETH recorded in early January. Current estimates place the waiting period at roughly 60 days.
Corporate entities and cryptocurrency exchanges are increasingly choosing to stake their ETH holdings rather than liquidate them. Market observers note that institutional players are prioritizing yield generation over keeping assets dormant.
In parallel developments, Vitalik Buterin introduced a significant proposal to enhance Ethereum’s consensus mechanism. The Minimmit proposal aims to replace the existing two-round Casper FFG finality protocol with a more efficient single-round alternative.
This architectural change involves important compromises. While fault tolerance would decrease from 33% to 17%, Buterin contends that censorship resistance would improve, and the threshold required to finalize invalid chain history would increase from 67% to 83% of staked ETH.
This modification represents one component of Ethereum’s comprehensive development strategy to reduce slot times from the current 12 seconds to potentially 2 seconds, while achieving single-digit second finality.
Ethereum is presently trading around $2,000, representing a significant decline from its previous cycle peak near $4,900.
Crypto World
Binance, CZ Cleared in US Civil Suit Over Alleged Terror Financing

A US federal judge has dismissed a civil lawsuit seeking to hold cryptocurrency exchange Binance and its founder Changpeng Zhao responsible for transactions allegedly linked to terrorist organizations involved in dozens of attacks worldwide.
Key Takeaways:
- A US federal judge dismissed a lawsuit accusing Binance and Changpeng Zhao of enabling crypto transactions tied to terrorist attacks.
- The court ruled that plaintiffs failed to show Binance intentionally supported or was directly linked to the alleged attacks.
- Plaintiffs may amend and refile the complaint despite the case being dismissed.
In a decision issued March 6, US District Judge Jeannette Vargas in Manhattan ruled that the plaintiffs failed to establish a credible connection between Binance and the attacks, according to a report by Reuters.
The lawsuit was filed by 535 plaintiffs, including victims and family members of victims, who claimed that digital asset transactions conducted through the exchange supported violent operations carried out between 2017 and 2024.
Plaintiffs Accuse Binance of Enabling Crypto Transfers Tied to 64 Attacks
The complaint alleged that several groups designated as foreign terrorist organizations, including Hamas, Hezbollah, Iran’s Revolutionary Guard, Islamic State, Kataib Hezbollah, Palestinian Islamic Jihad and Al-Qaeda, used cryptocurrency transactions facilitated through Binance to move funds connected to at least 64 attacks.
According to the filing, hundreds of millions of dollars in crypto transactions were allegedly processed through accounts associated with these groups.
The plaintiffs also argued that billions of dollars in trading activity with Iranian users indirectly benefited groups linked to the attacks.
Judge Vargas concluded that the allegations did not demonstrate that Binance or Zhao intentionally supported the operations.
In her ruling, she stated that the plaintiffs had not plausibly shown the defendants “culpably associated themselves with these terrorist attacks” or acted in a way that helped bring them about.
The judge added that the connection between the exchange and the alleged actors appeared limited to standard customer relationships.
According to the ruling, the groups or their affiliates simply held accounts and conducted transactions on Binance in what the court described as an “arms’ length relationship.”
Vargas also criticized the scale of the lawsuit, noting that the complaint stretched across 891 pages and included more than 3,100 paragraphs.
Despite the seriousness of the accusations, she described the filing as unnecessarily lengthy.
The court allowed the plaintiffs the opportunity to revise and refile their complaint.
In court filings, Binance and Zhao rejected the accusations and reiterated their condemnation of terrorism. Zhao also argued that the lawsuit attempted to capitalize on the exchange’s earlier legal troubles.
Binance reached a settlement with US authorities in November 2023, agreeing to pay $4.32 billion in penalties after pleading guilty to violations involving anti-money-laundering and sanctions laws.
Binance Denies Iranian Sanctions Violations in Response to US Senate Probe
On Friday, Binance rejected allegations that it violated Iranian sanctions in a letter responding to an inquiry from US Senator Richard Blumenthal.
The probe followed a Wall Street Journal report claiming the platform processed roughly $1.7 billion in transactions linked to Iranian entities and sanctions-evasion activity connected to Russia.
In its response, Binance called the reporting “false” and unsupported by credible evidence. The exchange said it takes regulatory obligations seriously and disputed claims that it knowingly facilitated transactions tied to sanctioned parties.
Binance also stated that it investigated two Hong Kong-based partners mentioned in the report, Hexa Whale and Blessed Trust.
According to the company, internal reviews were launched after law enforcement inquiries, leading to the removal of Hexa Whale from the platform in August 2025 and Blessed Trust in January 2026 as part of its compliance process.
The post Binance, CZ Cleared in US Civil Suit Over Alleged Terror Financing appeared first on Cryptonews.
Crypto World
Florida Senate Approves First Stablecoin Bill, Awaits DeSantis’ Signature
Florida lawmakers have approved a state-level framework regulating payment stablecoins, moving the legislation to Governor Ron DeSantis’ desk for final approval.
In a Friday post on X, Samuel Armes, founder of the Florida Blockchain Business Association, revealed that Senate Bill 314 has cleared the Florida Senate unanimously. The measure is set to become law once signed by DeSantis, which Armes expects within the next month.
“It has now passed the Senate and the House, and will be signed by DeSantis within the next 30 days!” he wrote on X.
The bill establishes regulatory guidelines for payment stablecoin issuers operating in Florida. Working alongside House Bill 175, the measure introduces consumer protection standards and financial oversight rules aligned with the federal GENIUS Act, which was signed into law in July.
Related: Florida narrows scope of revived Bitcoin reserve proposal for 2026
Florida bill amends money laundering law to include stablecoins
Under SB 314, Florida’s Control of Money Laundering in Money Services Business Act will be amended to explicitly include stablecoins. The update requires stablecoin issuers to comply with existing financial regulations while banning unlicensed issuance within the state. The legislation also clarifies that certain payment stablecoins will not be classified as securities.
Issuers based outside Florida must notify the state’s Office of Financial Regulation (OFR) before operating. Oversight will depend on the structure of the issuer. Some stablecoin operators will fall exclusively under the OFR, while others will face joint supervision alongside the Office of the Comptroller of the Currency.
The law also addresses potential risks tied to stablecoin incentives. Qualified issuers will be barred from paying interest or yield to holders if federal rules prohibit such payments.
Related: Trump sues JPMorgan in Florida court for $5B over debanking claims: Report
Florida revisits state crypto investment bill
In October last year, Florida lawmakers revived efforts to integrate cryptocurrencies into state investment strategies. The Florida House Bill 183, filed by Republican Representative Webster Barnaby, would allow the state and certain public entities to allocate up to 10% of their funds into digital assets. The revised proposal expands beyond Bitcoin (BTC) to include crypto exchange-traded products, crypto securities, non-fungible tokens and other blockchain-based assets.
HB 183 is a revised version of HB 487, which was withdrawn in June after failing to advance in a House operations subcommittee.
Magazine: Bitcoin may take 7 years to upgrade to post-quantum — BIP-360 co-author
Crypto World
Bitcoin Dip May Continue as Retail Buys Under $70K, Santiment Says

Bitcoin has shown renewed volatility as buyers and sellers clash at key levels. Retail participants have been loading up after the price dipped below $70,000, while larger holders have been trimming positions. Over a period spanning Feb. 23 to Mar. 3, Bitcoin traded roughly between $62,900 and $69,600, underscoring the tug-of-war between accumulation by smaller wallets and profit-taking by whales. The latest moves come as the market tries to discern whether the correction is over or if another leg lower lies ahead, particularly after a brief rally that pushed the price toward $74,000 before retreating.
Key takeaways
- Retail demand increased as Bitcoin failed to sustain a break above $70,000, while large holders began to reduce their exposure after a sharp rally past $74,000.
- Whales, defined as wallets holding 10–10,000 BTC, reportedly accumulated heavily in late February into early March when the price moved in the $62,900–$69,600 range.
- From the Wednesday peak, these whales offloaded roughly 66% of their recent purchases, even as smaller holders continued to add to positions below 0.01 BTC.
- The Crypto Fear & Greed Index sank to 12, placing the market in “Extreme Fear” as the pullback intensified.
- Spot Bitcoin ETFs posted the largest outflow day in three weeks, with about $348.9 million sliding out of 11 products, signaling a shift in near-term demand dynamics.
Tickers mentioned: $BTC
Sentiment: Bearish
Price impact: Negative. Bitcoin traded around the mid-$60k range after peaking near $74k earlier in the week.
Trading idea (Not Financial Advice): Hold — watch for a clearer bid near key support zones before committing further risk).
Market context: The move comes amid a broader sell-off in risk assets and shifting ETF flows, with on-chain behavior showing growing retail interest while wholesale players trim exposure. The combination of real-time price action and fund outflows suggests sentiment remains cautious, even as some participants see value in recent pullbacks.
Why it matters
The paradox in today’s Bitcoin dynamics rests on diverging activity between retail and whale cohorts. Santiment highlighted that, after Bitcoin breached the $74,000 mark, “key stakeholders began taking profit,” a pattern that can precede further near-term weakness if demand does not re-emerge. The dataset shows that while smaller holders were accumulating, larger holders were actively realizing gains, a combination that can slow the pace of a sustained rally even when retail buyers persist.
From a price-structure perspective, the volatility has shifted the narrative from a straight-line ascent to a more cautious outlook. The market technicals are complicated by macro considerations, including risk-off sentiment and liquidity conditions that influence whether a deeper correction can be avoided. The latest price action—moving down from $74k and hovering in the low to mid-$60k zone—echoes a broader market that is trying to price in both the potential for a rebound and the risk that the lows might retest if demand falters. This is reinforced by the fear gauge in crypto markets, which dropped into Extreme Fear and reflects a broader uncertainty among participants about near-term direction.
On the ETF side, the data point of $348.9 million in net outflows across eleven spot Bitcoin ETF products marks the largest single-day drain in three weeks. The outflows could reflect profit-taking amid the pullback, but they also underscore that ETF-driven demand has not yet returned to the pace seen during prior uplegs. In a broader sense, the ETF flows are part of a larger mosaic—retail demand, institutional positioning, and on-chain behavior—that determines whether a low-risk entry point emerges or if the market faces another test of support around the $60k–$68k corridor.
Analysts have stressed that the pattern of rising retail accumulation while whales exit could signal that the correction isn’t fully complete. If demand from smaller investors remains resilient while large holders refrain from aggressive buying, Bitcoin could spend more time consolidating before the next leg higher. As Mn Trading Capital founder Michael van de Poppe noted in a subsequent post, a lack of support in the $67k–$68k region could lead to a renewed test of liquidity lows before buyers step in again. That view dovetails with the chart-level work some observers conduct to determine whether the market is forming a basin or merely pausing amid a broader downtrend.
The history of Bitcoin’s volatility also provides a frame for current conditions. After an all-time high near $126,000 in October, the price dipped to around $60,000 in February—a level some analysts consider a potential floor, though that assessment remains contested as new data flows in. The mix of lower price levels and risk-off currents creates an environment where both the narrative of value and the mechanics of supply-and-demand play critical roles in the next few weeks. The current data points—retail accumulation, whale distribution, ETF outflows, and the fear index—should be weighed together when evaluating potential trajectories for Bitcoin in the near term.
For market participants, the takeaway is that the market continues to reflect a balance of risk appetite and caution. The conditional nature of the moves—where strong on-chain demand from smaller buyers exists alongside prudence from larger holders—means that a decisive breakout or breakdown will likely require a fresh catalyst, whether it be macro news, regulatory signals, or a notable shift in ETF flows. Until then, traders will be watching price interaction around the $67k–$68k zone and the evolving sentiment indicators that accompany daily price changes.
What to watch next
- Monitor Bitcoin’s price behavior around the $67k–$68k support region; a break below could imply deeper liquidity testing.
- Track the ongoing flow of spot Bitcoin ETFs in upcoming reporting periods to gauge institutional demand resilience or fatigue.
- Observe the divergence between retail accumulation and whale distribution to assess whether the imbalance signals a longer bottom-building phase.
- Watch the Crypto Fear & Greed Index and related sentiment metrics for any reversal that might precede a price bounce.
Sources & verification
- Santiment: analysis noting wholesale profit-taking at $74k and heavy accumulation by whales between Feb. 23 and Mar. 3.
- CoinMarketCap price data referenced for current price context.
- Crypto Fear & Greed Index data source used to frame sentiment movement.
- Michael van de Poppe’s public commentary on price support in the $67k–$68k zone.
- Farside ETF flow data, outlining the $348.9 million net outflows across 11 spot Bitcoin ETF products.
Bitcoin (CRYPTO: BTC) market dynamics and potential path forward
Bitcoin (CRYPTO: BTC) has once again proven that market direction hinges on a combination of on-chain activity, macro risk sentiment, and fund flows. The latest sequence—retail accumulation even as whales take profits, followed by a price retreat from a $74k high—underscores the complexity of pricing in a market where multiple participant types pursue different time horizons. The data from Santiment points to a tactical pattern that, if repeated, could foretell continued volatility in the near term. On the other hand, ETF outflows remind market watchers that demand from traditional vehicles remains a critical swing factor that can either accelerate a rebound or extend the correction depending on how flows align with price action. The next few weeks will likely hinge on whether the $67k–$68k band provides a durable foundation or if liquidity tests push the price toward the next set of support levels, potentially revisiting the sub-$60k region if demand falters.
Bitcoin’s current trajectory remains a reading of market mood as much as a function of technical levels. Traders will want to align price action with the evolving narratives around risk appetite, regulatory signals, and the appetite of institutional players for exposure to a volatile asset class. The ongoing tension between retail demand and wholesale posture will continue to shape the path of least resistance for Bitcoin in the near term, even as the longer-term thesis remains intact for those who view the asset as a hedge against inflation and a flexible store of value in a volatile macro landscape.
Sources and verification: Santiment report on this week’s market dynamics; CoinMarketCap price data; Crypto Fear & Greed Index page; Michael van de Poppe’s X post; Farside ETF flow data.
Crypto World
Dubai Regulator VARA Issues Cease and Desist Orders to 2 Crypto Exchanges


The local regulator said the two exchanges have been offering trading services without the necessary approval.
The Virtual Asset Regulatory Authority (VARA), which is the main watchdog for cryptocurrency-related businesses in Dubai, has issued a formal cease and desist order to KuCoin and MEXC.
The regulator argued that it had come to its attention that the popular trading platforms “may be providing Virtual Asset activities to Dubai residents without the necessary regulatory approvals and misrepresenting” their legal statuses.
Aside from the cease and desist issued to all unlicensed VA activities, the official statement on KuCoin reads that investors and consumers must be aware of the potential risks.
“Engaging with unlicensed companies that are not in compliance with VARA Regulations, associated Rulebooks, and relevant UAE legislation exposes users to significant financial risks and potential legal consequences for violating regulatory requirements or criminal laws.”
It reasserted that KuCoin does not hold any license to provide crypto services in or from Dubai, which means that all such activities advertised or conducted by the exchange were “therefore in breach of the VARA Regulations.”
Dubai’s VARA introduced the comprehensive regulatory framework four years ago and requires all service providers to be licensed to operate legally in the jurisdiction.
A day before this notice against KuCoin, the regulator issued a similar alert against one of its competitors – MEXC. The message was identical, instructing a cease and desist order on all of its activities in and from Dubai.
Binance Free $600 (CryptoPotato Exclusive): Use this link to register a new account and receive $600 exclusive welcome offer on Binance (full details).
LIMITED OFFER for CryptoPotato readers at Bybit: Use this link to register and open a $500 FREE position on any coin!
Crypto World
Bitcoin’s Four-Year Cycle May Be Ending, Fidelity Research Suggests
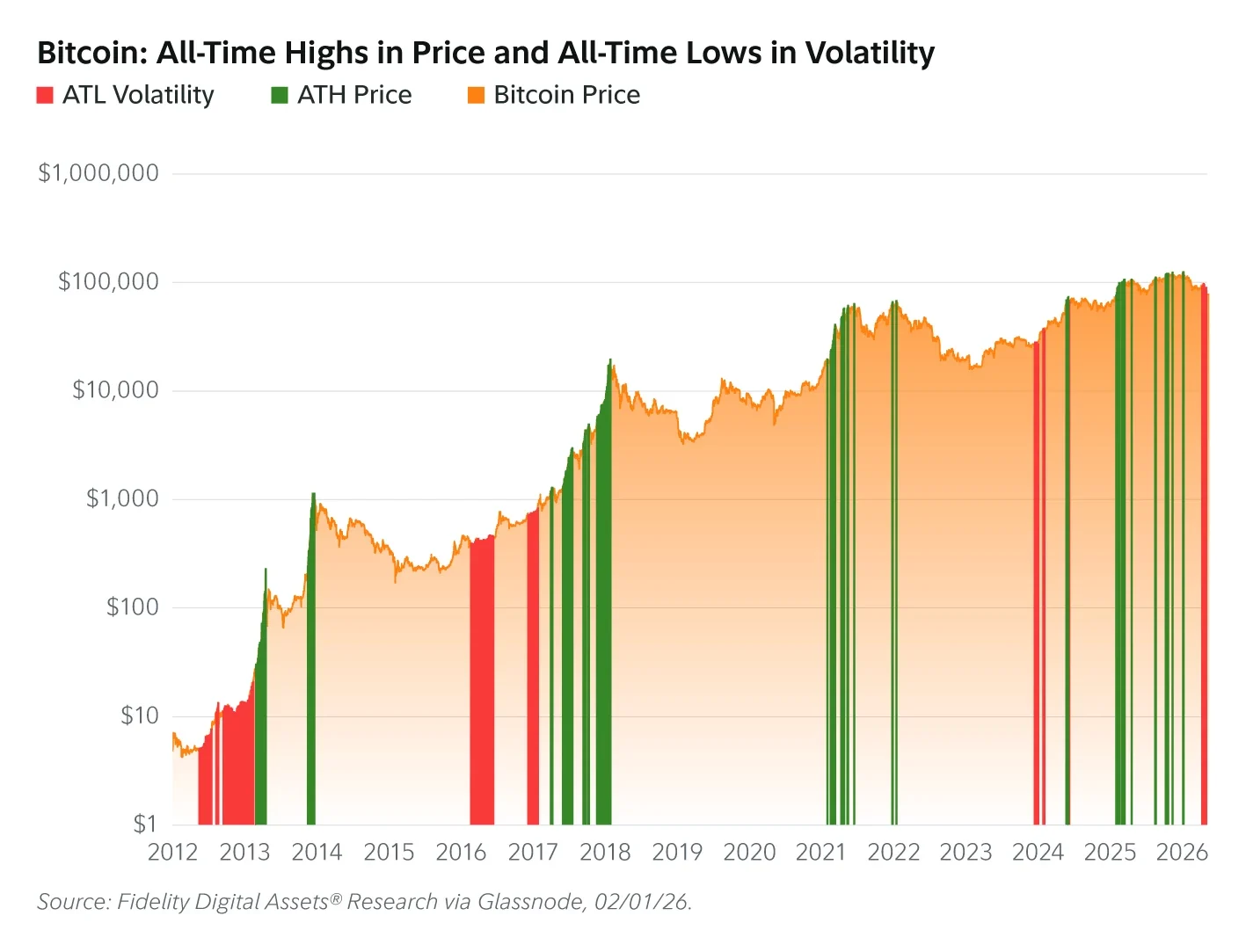
TLDR:
- Fidelity data shows Bitcoin volatility hitting record lows even months after the 2025 price peak near $126,000.
- Public companies and ETFs now hold nearly 12% of Bitcoin supply, signaling major institutional accumulation.
- Bitcoin’s MVRV ratio has stayed near 2x realized value this cycle, far below peaks seen in past bull markets.
- Fidelity’s profit-to-volatility ratio has remained above 0.015 since 2023, marking the longest stability period.
Bitcoin’s market behavior may be entering a new phase, according to recent research from Fidelity Digital Assets.
The firm argues that long-standing boom-and-bust cycles could weaken as institutional demand reshapes the market. Data shows volatility hitting record lows even months after Bitcoin reached new price highs.
The question now is whether the classic four-year Bitcoin cycle still defines the crypto market.
Bitcoin Volatility Trends Challenge the Classic Four-Year Cycle
Bitcoin reached a market capitalization near $2.5 trillion during its October 2025 peak. Prices climbed above $126,000 during that rally.
However, volatility moved in the opposite direction. One-year realized volatility recorded 17 new all-time lows in January 2026.
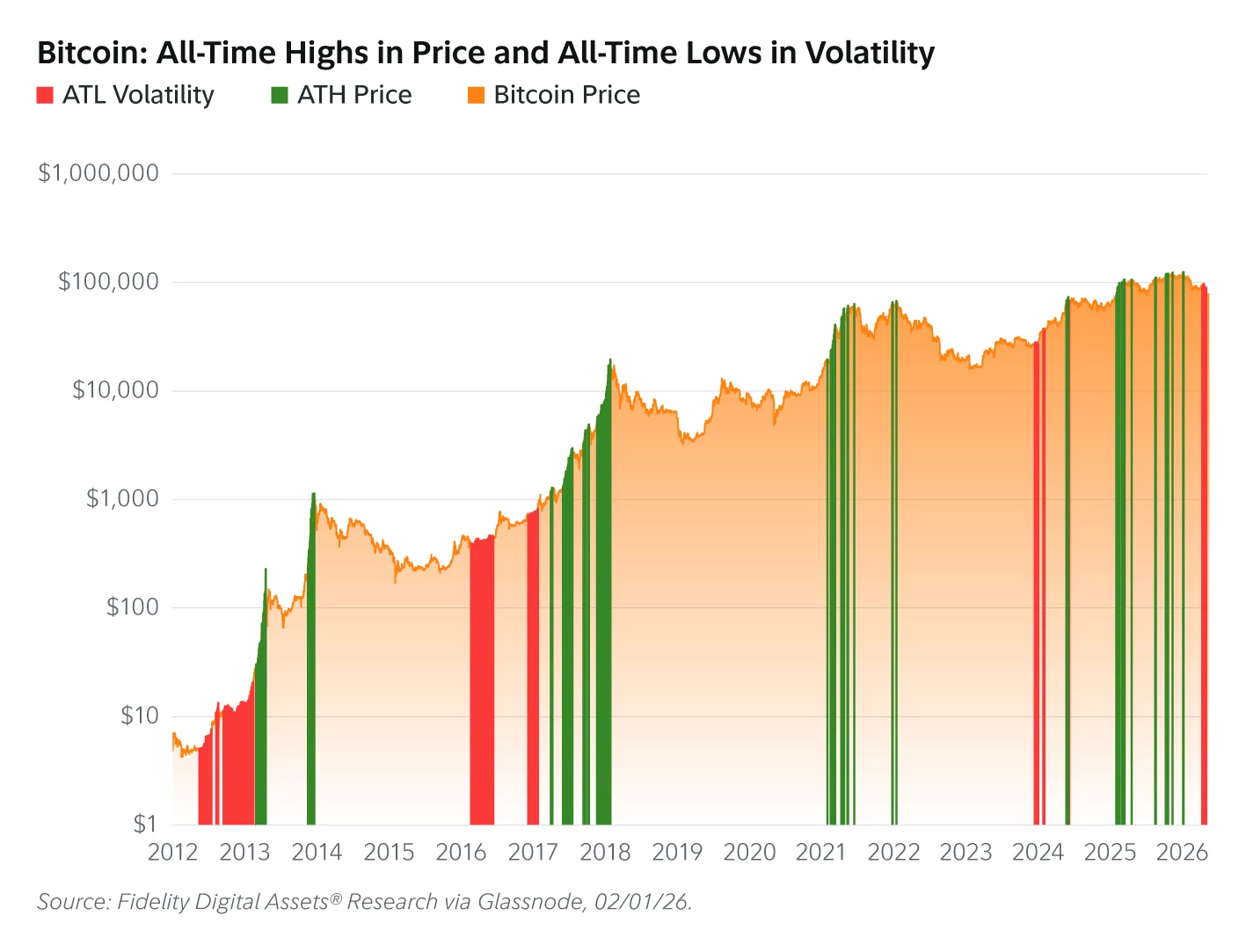
According to Fidelity Digital Assets research, this pattern differs sharply from previous cycles. Historically, volatility surged as Bitcoin approached market peaks.
The current trend suggests a shift toward a larger and more liquid market. Fidelity compared Bitcoin’s growth to large-cap technology companies reaching maturity.
The firm notes that Bitcoin’s market size has expanded rapidly across cycles. The asset is now twice as large as its 2021 peak valuation.
It also stands nearly ten times larger than the 2017 cycle peak. Compared with 2013, Bitcoin’s market capitalization has expanded more than 200-fold.
Fidelity’s data shows volatility began declining in late 2023. At the time, Bitcoin traded near $27,000 before starting its latest rally.
Institutional Demand Reshapes Bitcoin Market Structure
Demand patterns have changed significantly as institutions enter the market. Public companies and exchange-traded products now hold a growing share of supply.
According to Fidelity Digital Assets, 49 public companies hold more than 1,000 Bitcoin each. Combined holdings exceed one million BTC.
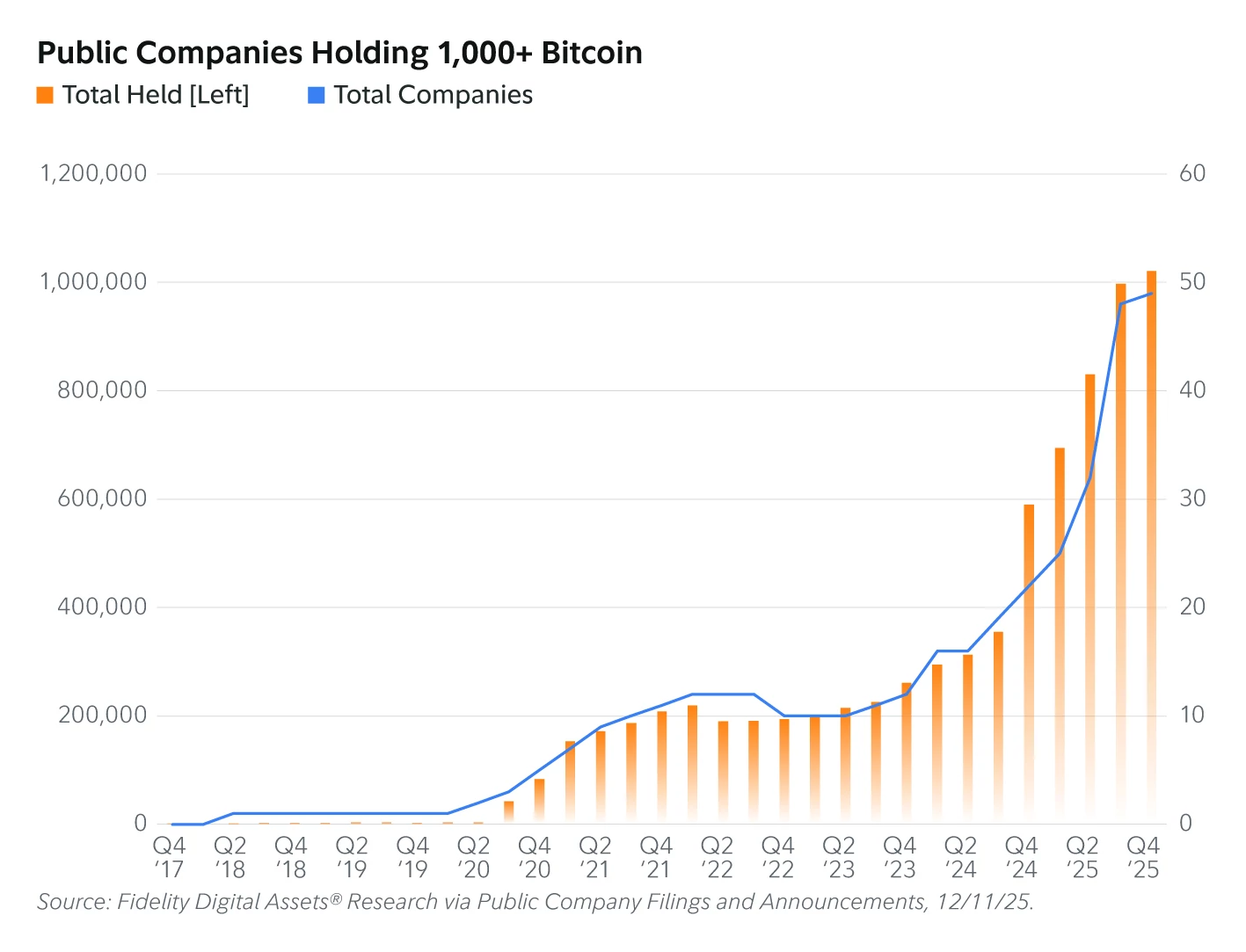
That amount represents more than five percent of Bitcoin’s circulating supply. The cohort has steadily increased holdings since early 2020.
Exchange-traded products have accelerated institutional accumulation. Spot Bitcoin ETPs launched in the United States in January 2024.
By January 2026, those vehicles collectively held nearly 1.3 million Bitcoin. This equals roughly 6.4 percent of the circulating supply.
Fidelity reported that the leading Bitcoin ETF surpassed $75 billion in assets within two years. Gold’s GLD ETF required almost seven years to reach that milestone.
On-chain metrics also suggest a calmer market cycle. Bitcoin’s market value to realized value ratio has remained near two throughout the current bull market.
Earlier cycles saw sharper expansions. The ratio reached six during 2013 and four during both the 2017 and 2021 cycles.
Fidelity estimates that reaching a ratio of four again would imply a $4.5 trillion Bitcoin market cap. That level corresponds to roughly $225,000 per coin.
The firm also introduced a “Profit to Volatility Ratio” metric. It compares profitable addresses with realized volatility.
That ratio has remained above 0.015 since late 2023. Fidelity describes this period as the longest stretch of stability in Bitcoin’s history.
Crypto World
AI Model Finds 22 Firefox Vulnerabilities in Two Weeks

TLDR:
- Claude Opus 4.6 found 22 Firefox bugs in 2 weeks, 14 flagged high-severity by Mozilla researchers.
- The 14 high-severity finds equal nearly a fifth of all such Firefox bugs Mozilla fixed in 2025.
- Claude succeeded in building working exploits in only 2 of several hundred automated attempts.
- Anthropic spent roughly $4,000 in API credits testing Claude’s exploit development capabilities.
Anthropic’s Claude Opus 4.6 identified 22 security vulnerabilities inside Firefox in just two weeks. Fourteen of those bugs were classified as high-severity by Mozilla. That figure represents nearly a fifth of all high-severity Firefox flaws remediated throughout 2025.
The findings emerged from a structured research partnership between Anthropic and Mozilla.
Claude AI Uncovers High-Severity Firefox Bugs at Record Speed
The collaboration began as an internal model evaluation.
Anthropic wanted a harder benchmark after Claude Opus 4.5 nearly solved CyberGym, a known security reproduction test. Engineers built a dataset of prior Firefox CVEs and tested whether the model could reproduce them.
Claude Opus 4.6 replicated a high percentage of those historical vulnerabilities. That raised a concern: some CVEs may already have existed in Claude’s training data.
Anthropic then redirected the effort toward finding entirely new bugs in the current Firefox release.
Within twenty minutes of beginning exploration, Claude flagged a Use After Free vulnerability inside Firefox’s JavaScript engine. Three separate Anthropic researchers validated the bug independently.
A bug report, alongside a Claude-authored patch, was filed in Mozilla’s Bugzilla tracker.
By the time that first report was submitted, Claude had already produced fifty additional crashing inputs. Anthropic ultimately scanned nearly 6,000 C++ files and submitted 112 unique reports to Mozilla. Most fixes shipped to users in Firefox 148.0.
Firefox 148 Ships Fixes as AI Exploit Research Raises New Alarms
Mozilla triaged the bulk submissions and encouraged Anthropic to send all findings without manual validation. That approach accelerated the pipeline significantly. Mozilla researchers have since begun testing Claude internally for their own security workflows.
Anthropic also tested whether Claude could move beyond discovery into active exploitation.
Researchers gave Claude access to the reported vulnerabilities and asked it to build working exploits. The goal was to demonstrate a real attack by reading and writing a local file on a target system.
Across several hundred attempts, spending roughly $4,000 in API credits, Claude succeeded in only two cases.
According to Anthropic’s published findings, the model is substantially better at finding bugs than exploiting them. The cost gap between discovery and exploitation runs at least an order of magnitude.
The exploits that did work required a test environment stripped of standard browser security features. Firefox’s sandbox protections were not present.
Anthropic noted that sandbox-escaping vulnerabilities do exist and that Claude’s output represents one component of a broader exploit chain.
Anthropic urged software developers to accelerate secure coding practices. The company also outlined a “task verifier” method, where AI agents check their own fixes against both vulnerability recurrence and regression tests.
Mozilla’s transparent triage process helped shape that approach throughout the research.
Crypto World
Flow Network Incident Resolved as HTX Restores Full FLOW Services

TLDR:
- HTX confirms all FLOW assets remained intact during the Flow network incident and verification process
- Flow developers patched the vulnerability responsible for abnormal transactions on December 27
- HTX restored FLOW trading, deposits, and withdrawals after verifying network stability
- Exchange removed its January notice following Flow’s detailed post-incident security report
Flow blockchain’s December security incident has reached a full resolution after coordination between the network and major exchange HTX.
The update confirms the vulnerability responsible for abnormal transactions has been patched and network operations restored. HTX also verified that all user-held FLOW tokens on its platform remain intact.
Trading, deposits, and withdrawals for the token have resumed normal operations.
Flow Network Incident Resolved as HTX Confirms Normal Operations
The Flow ecosystem shared an update confirming that the issue reported on December 27 has been fully resolved. The incident involved abnormal transactions triggered by a technical vulnerability on the network.
HTX activated internal emergency procedures once it detected the event. The exchange maintained communication with Flow ecosystem partners while monitoring the situation.
The latest update indicates that developers patched the vulnerability and restored normal network activity. The Flow team also identified and addressed abnormal minted assets during the review process.
Flow stated that ecosystem services have stabilized after the corrective actions. Network operations now function normally across supported platforms.
HTX verified user asset balances during the investigation period. The exchange reported that all FLOW tokens held by customers remain fully validated.
HTX Restores FLOW Trading, Deposits, and Withdrawals
HTX confirmed that FLOW trading resumed after reviewing the network’s recovery. Deposits and withdrawals for the token now operate without restrictions.
The exchange initially issued a notice about the incident on January 13. That notice questioned the security status of the Flow network at the time.
HTX later removed the notice after reviewing the Flow Foundation’s post-incident report. According to HTX, the report provided detailed explanations addressing earlier concerns.
The exchange stated that the new information clarified how developers handled the vulnerability. It also confirmed that the response restored stability across the network.
Flow Foundation acknowledged the collaboration between both organizations during the investigation period. The foundation stated it expects continued cooperation with HTX moving forward.
HTX reiterated that user asset security remains its top priority. The exchange said it will continue monitoring supported networks and working with ecosystem partners.
The update confirms the incident no longer affects current operations. FLOW trading infrastructure across HTX now runs under normal conditions.
Crypto World
BTC slips below $68,000 as dollar posts steepest weekly gain


Bitcoin fell to $67,960 by Saturday morning, down 3.4% over the past 24 hours and retreating sharply from the past week’s high. The move fits what has become a recurring script in recent months, with late-week selling dragging prices toward the lower end of the range heading into Saturday.
Majors took the harder hit again. Ether dropped 4.4% to $1,974, solana fell 4% to $84.31, dogecoin lost 2.9% to $0.09, and BNB slid 2.6% to $627. XRP fell 2.2% to $1.37.
The weekly picture tells a more nuanced story though. Bitcoin is still up 3.6% over seven days. Ether has gained 2.6%. BNB added 2.1%. The mid-week surge absorbed the war shock and then some, even if Friday’s pullback took the shine off.
Meanwhile, the dollar posted its steepest weekly gain in a year, strengthening as markets priced in higher energy costs, stickier inflation, and a Fed that has even less room to cut rates. That’s a direct headwind for bitcoin and every other asset denominated against the dollar.
“As tensions escalated in the Middle East last week, investors moved quickly to the safety of the U.S. dollar, which strengthened as markets began pricing in higher energy prices and reignited inflation fears, potentially delaying Federal Reserve rate cuts,” said Björn Schmidtke, CEO of Aurelion, in an email to CoinDesk.
The on-chain data paints a fragile picture beneath the surface. Glassnode data shows 43% of bitcoin’s total market supply is now sitting at a loss. That’s a significant overhang.
As bitcoin recovers, those underwater holders have an incentive to sell into any rally to break even, creating persistent resistance on the way up. It’s one reason the push to $74,000 on Thursday couldn’t hold. Every bounce toward higher prices runs into supply from people who’ve been waiting months to get out.
One bright spot came from stablecoin flows. Messari recorded a 415% jump in net stablecoin inflows to $1.7 billion over the week, with daily transfers up nearly 10%. That’s potentially dry powder waiting to be deployed, and it suggests retail isn’t entirely absent despite the fear-heavy sentiment. Whether that capital rotates into bitcoin or waits for lower prices is the question.
The war continues to set the tempo. The U.S.-Iran conflict showed no signs of resolution this week. Oil remains elevated. The Strait of Hormuz is still disrupted. And the macro backdrop of strong dollar, sticky inflation, and delayed rate cuts is the worst combination for risk assets.
Bitcoin’s week looked impressive in headlines, touching $74,000 mid-week, but the round trip from $68,000 to $74,000 and back to $68,000 is just another lap of the range.
Crypto World
Bitcoin Dip May Not Be Over As Retail Ramps Up Buying: Santiment
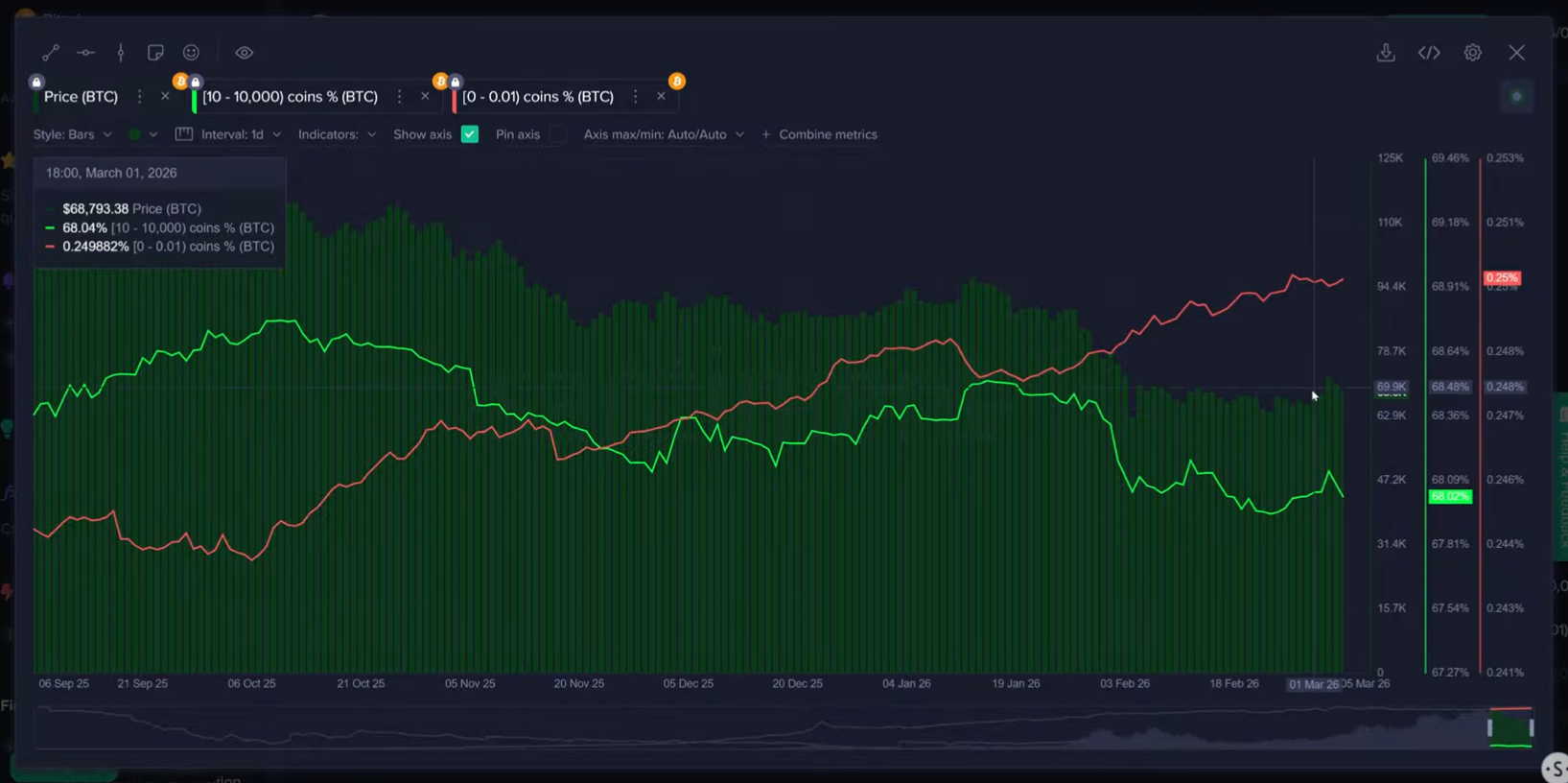
Retail investors have been scooping up Bitcoin after it slipped below $70,000, but whale activity suggests the price could still head lower if past patterns repeat, according to crypto sentiment platform Santiment.
“The moment Bitcoin hit $74k, these key stakeholders began taking profit,” Santiment said in a report on Friday.
Santiment explained that whales — those holding between 10 and 10,000 Bitcoin (BTC) — “accumulated heavily” between Feb. 23 and Mar. 3, when Bitcoin was trading between $62,900 and $69,600.

Since Wednesday, when Bitcoin climbed past $70,000 and touched $74,000, the cohort has offloaded around 66% of their recent purchases, Santiment said. Meanwhile, retail investors — those holding below 0.01 Bitcoin — have been increasing their positions.
Correction may not be over yet, says Santiment
“When retail buys while whales sell, it typically signals that the correction is not yet over,” Santiment said. Bitcoin is trading at $67,984 at the time of publication, according to CoinMarketCap.
Bitcoin’s price decline led the Crypto Fear & Greed Index to fall 6 points, pushing it further into “Extreme Fear” territory with a score of 12 on Saturday.
MN Trading Capital founder Michael van de Poppe shared a similar outlook, saying a further decline is possible. “If Bitcoin doesn’t find support in this $67-68K region, then we’re likely going to retest the lows for liquidity before bouncing back upwards,” van de Poppe said in an X post on Friday.
Spot Bitcoin ETFs post largest outflow day in three weeks
The decline coincided with US-based spot Bitcoin ETFs posting their largest outflow day since Feb. 12, with a total of $348.9 million in net outflows across the 11 ETF products, according to Farside data.
Related: Trump’s National Cyber Strategy pledges to support crypto and blockchain
Bitcoin’s price fell as low as $60,000 on Feb. 6 during its downtrend from the October all-time high of $126,000 before showing a modest recovery. Economist Timothy Peterson suggests this level could be the floor for the time being.
“This valuation level has always marked a bottom for Bitcoin. About 99.5% chance it stays above $60k,” Peterson said in an X post, referring to the Bitcoin Price to Metcalfe Value chart.
Magazine: The debate over Bitcoin’s four-year cycle is over: Benjamin Cowen
-

 Politics4 days ago
Politics4 days agoAlan Cumming Brands Baftas Ceremony A ‘Triggering S**tshow’
-

 Tech6 days ago
Tech6 days agoUnihertz’s Titan 2 Elite Arrives Just as Physical Keyboards Refuse to Fade Away
-
Business17 hours ago
Form 8K Entergy Mississippi LLC For: 6 March
-

 NewsBeat6 days ago
NewsBeat6 days agoAbusive parents will now be treated like sex offenders and placed on a ‘child cruelty register’ | News UK
-

 Fashion14 hours ago
Fashion14 hours agoWeekend Open Thread: Ann Taylor
-

 NewsBeat7 days ago
NewsBeat7 days agoDubai flights cancelled as Brit told airspace closed ’10 minutes after boarding’
-

 NewsBeat7 days ago
NewsBeat7 days agoThe empty pub on busy Cambridge road that has been boarded up for years
-

 NewsBeat6 days ago
NewsBeat6 days ago‘Significant’ damage to boarded-up Horden house after fire
-

 Tech2 days ago
Tech2 days agoBitwarden adds support for passkey login on Windows 11
-

 Entertainment5 days ago
Entertainment5 days agoBaby Gear Guide: Strollers, Car Seats
-

 Sports2 days ago
Sports2 days ago499 runs and 34 sixes later, India beat England to enter T20 World Cup final | Cricket News
-

 NewsBeat6 days ago
NewsBeat6 days agoEmirates confirms when flights will resume amid Dubai airport chaos
-
Politics6 days ago
FIFA hypocrisy after Israel murder over 400 Palestinian footballers
-

 NewsBeat5 days ago
NewsBeat5 days agoIs it acceptable to comment on the appearance of strangers in public? Readers discuss
-

 Tech6 days ago
Tech6 days agoViral ad shows aged Musk, Altman, and Bezos using jobless humans to power AI
-
 Video5 days ago
Video5 days agoHow to Build Finance Dashboards With AI in Minutes
-

 Fashion6 days ago
Fashion6 days agoOn the Scene at the 57th Annual NAACP Image Awards: Teyana Taylor in Black Ashi Studio, Colman Domingo in Yellow Sergio Hudson, Chloe Bailey in Christian Siriano, and More!
-

 Business3 days ago
Business3 days agoGuthrie Disappearance Enters Fifth Week as Family Visits Memorial
-

 NewsBeat5 days ago
NewsBeat5 days agoUkraine-Russia war latest: Belgium releases video showing forces boarding Russian shadow fleet oil tanker
-

 Crypto World6 days ago
Crypto World6 days agoUS Judge Lets Binance Unregistered Token Class Action Proceed





 BNB (@cz_binance)
BNB (@cz_binance) 





