Crypto World
Why Address Poisoning Works Without Stealing Private Keys
Key takeaways
-
Address poisoning exploits behavior, not private keys. Attackers manipulate transaction history and rely on users mistakenly copying a malicious lookalike address.
-
Cases such as the 50-million-USDT loss in 2025 and the 3.5 wBTC drain in February 2026 demonstrate how simple interface deception can lead to massive financial damage.
-
Copy buttons, visible transaction history and unfiltered dust transfers make poisoned addresses appear trustworthy within wallet interfaces.
-
Because blockchains are permissionless, anyone can send tokens to any address. Wallets typically display all transactions, including spam, which attackers use to plant malicious entries.
Most crypto users believe that their funds stay secure as long as their private keys are protected. However, as a rising number of scams show, this is not always the case. Scammers have been using an insidious tactic, address poisoning, to steal assets without ever accessing the victim’s private key.
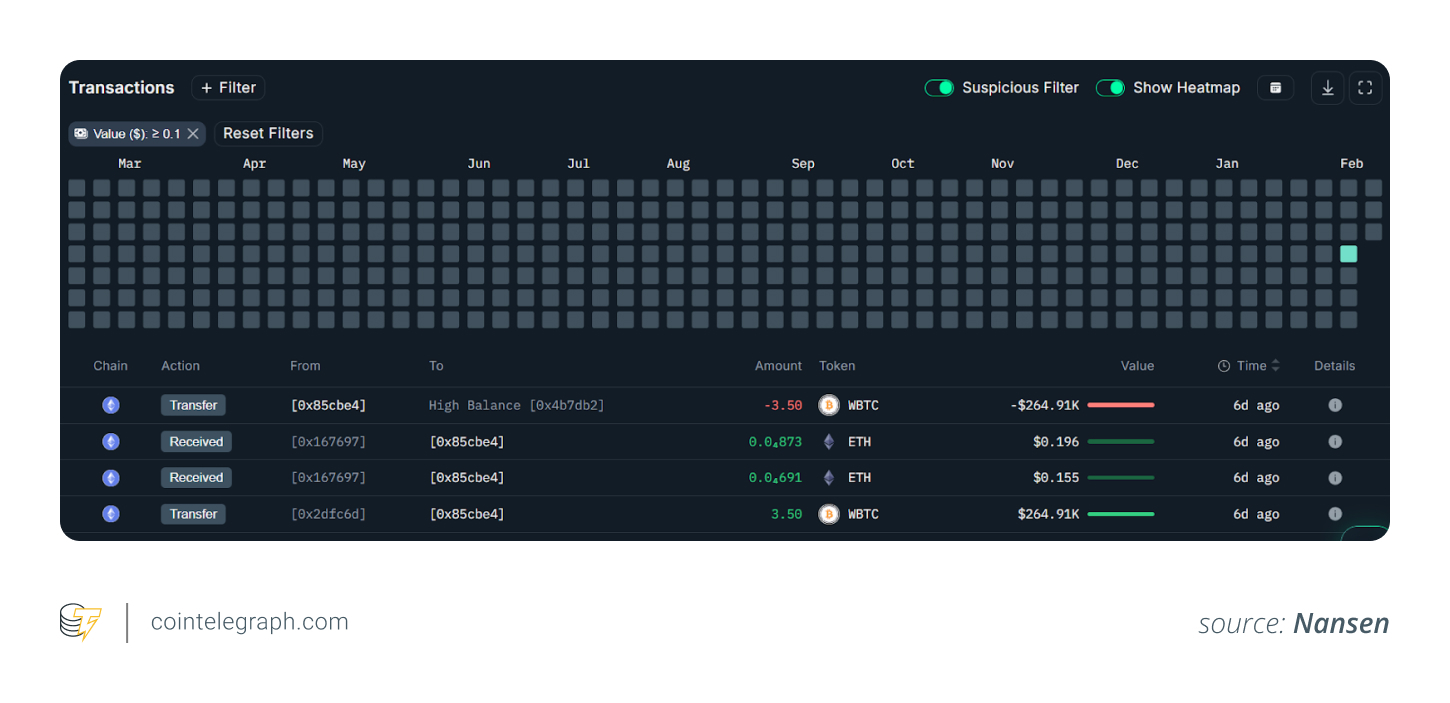
In February 2026, a phishing scheme targeted a Phantom Chat feature. Using an address poisoning tactic, attackers successfully drained roughly 3.5 Wrapped Bitcoin (wBTC), worth more than $264,000.
In 2025, a victim lost $50 million in Tether’s USDt (USDT) after copying a poisoned address. Such incidents have highlighted how poor interface design and everyday user habits can result in massive losses.

Prominent crypto figures like Binance co-founder Changpeng “CZ” Zhao have publicly urged wallets to add stronger safeguards following address poisoning incidents.
This article explains how address poisoning scams exploit user behavior rather than private key theft. It details how attackers manipulate transaction history, why the tactic succeeds on transparent blockchains and what practical steps users and wallet developers can take to reduce the risk.
What address poisoning really involves
Unlike traditional hacks that target private keys or exploit code flaws, address poisoning manipulates a user’s transaction history to deceive them into sending funds to the wrong address.
Usually, the attack proceeds in the following way:
-
Scammers identify high-value wallets via public blockchain data.
-
They create a wallet address that closely resembles one the victim often uses. For example, the attacker may match the first and last few characters.
-
They send a small or zero-value transaction to the victim’s wallet from this fake address.
-
They rely on the victim copying the attacker’s address from their recent transaction list later.
-
They collect the funds when the victim accidentally pastes and sends them to the malicious address.
The victim’s wallet and private keys remain untouched, and blockchain cryptography stays unbroken. The scam thrives purely on human error and trust in familiar patterns.
Did you know? Address poisoning scams surged alongside the rise of Ethereum layer-2 networks, where lower fees make it cheaper for attackers to mass-send dust transactions to thousands of wallets at once.
How attackers craft deceptive addresses
Crypto addresses are lengthy hexadecimal strings, often 42 characters on Ethereum-compatible chains. Wallets usually show only a truncated version, such as “0x85c…4b7,” which scammers take advantage of. Fake addresses have identical beginnings and endings, while the middle portion differs.
Legitimate address (example format):
0x742d35Cc6634C0532925a3b844Bc454e4438f44e
Poisoned lookalike address:
0x742d35Cc6634C0532925a3b844Bc454e4438f4Ae
Scammers use vanity address generators to craft these near-identical strings. The fake one appears in the victim’s transaction history thanks to the dusting transfer. To users, it looks trustworthy at a glance, especially since they rarely verify the full address string.
Did you know? Some blockchain explorers now automatically label suspicious dusting transactions, helping users spot potential poisoning attempts before interacting with their transaction history.
Why this scam succeeds so well
There are several intertwined factors that make address poisoning devastatingly effective:
-
Human limitations in handling long strings: Because addresses are not human-friendly, users rely on quick visual checks at the beginning and end. Scammers exploit this tendency.
-
Convenient but risky wallet features: Many wallets offer easy copy buttons next to recent transactions. While this feature is helpful for legitimate use, it becomes risky when spam entries sneak in. Investigators such as ZachXBT have pointed to cases where victims copied poisoned addresses directly from their wallet UI.

3. No need for technical exploits: Because blockchains are public and permissionless, anyone can send tokens to any address. Wallets usually display all incoming transactions, including spam, and users tend to trust their own history.
The vulnerability lies in behavior and UX, not in encryption or key security.
Why keys aren’t enough protection
Private keys control authorization, meaning they ensure only you can sign transactions. However, they cannot verify whether the destination address is correct. Blockchain’s core traits — permissionless access, irreversibility of transactions and trust minimization — mean malicious transactions get permanently recorded.
In these scams, the user willingly signs the transfer. The system functions exactly as designed, and the flaw lies in human judgment.
Underlying psychological and design issues involve:
-
Routine habits: People tend to repeatedly send funds to the same addresses, so they copy from their transaction history instead of reentering addresses.
-
Cognitive strain: Transactions involve multiple steps, such as addresses, fees, networks and approvals. Many users find scrutinizing every character tedious.
-
Truncated displays: Wallet UIs hide most of the address, leading to partial checks.
Did you know? In certain cases, attackers automate address lookalike generation using GPU-powered vanity tools, allowing them to produce thousands of near-identical wallet addresses within minutes.
Practical ways to stay safer
While address poisoning exploits user behavior rather than technical vulnerabilities, small changes in transaction habits can significantly reduce the risk. Understanding a few practical safety measures can help crypto users avoid costly mistakes without requiring advanced technical knowledge.
For users
Simple verification habits and transaction discipline can significantly reduce your chances of falling victim to address poisoning scams.
-
Build and use a verified address book or whitelist for frequent recipients.
-
Verify the full address. Use a checker or compare it character by character before making payments.
-
Never copy addresses from recent transaction history. Instead, reenter addresses or use bookmarks.
-
Ignore or report unsolicited small transfers as potential poisoning attempts.
For wallet developers
Thoughtful interface design and built-in safeguards can minimize user error and make address poisoning attacks far less effective.
-
Filtering or hiding low-value spam transactions
-
Similarity detection for recipient addresses
-
Pre-signing simulations and risk warnings
-
Built-in poisoned address checks via onchain queries or shared blacklists.
Cointelegraph maintains full editorial independence. The selection, commissioning and publication of Features and Magazine content are not influenced by advertisers, partners or commercial relationships.
Crypto World
Base To Shift From Optimism Tech Stack to a ‘Unified’ Architecture
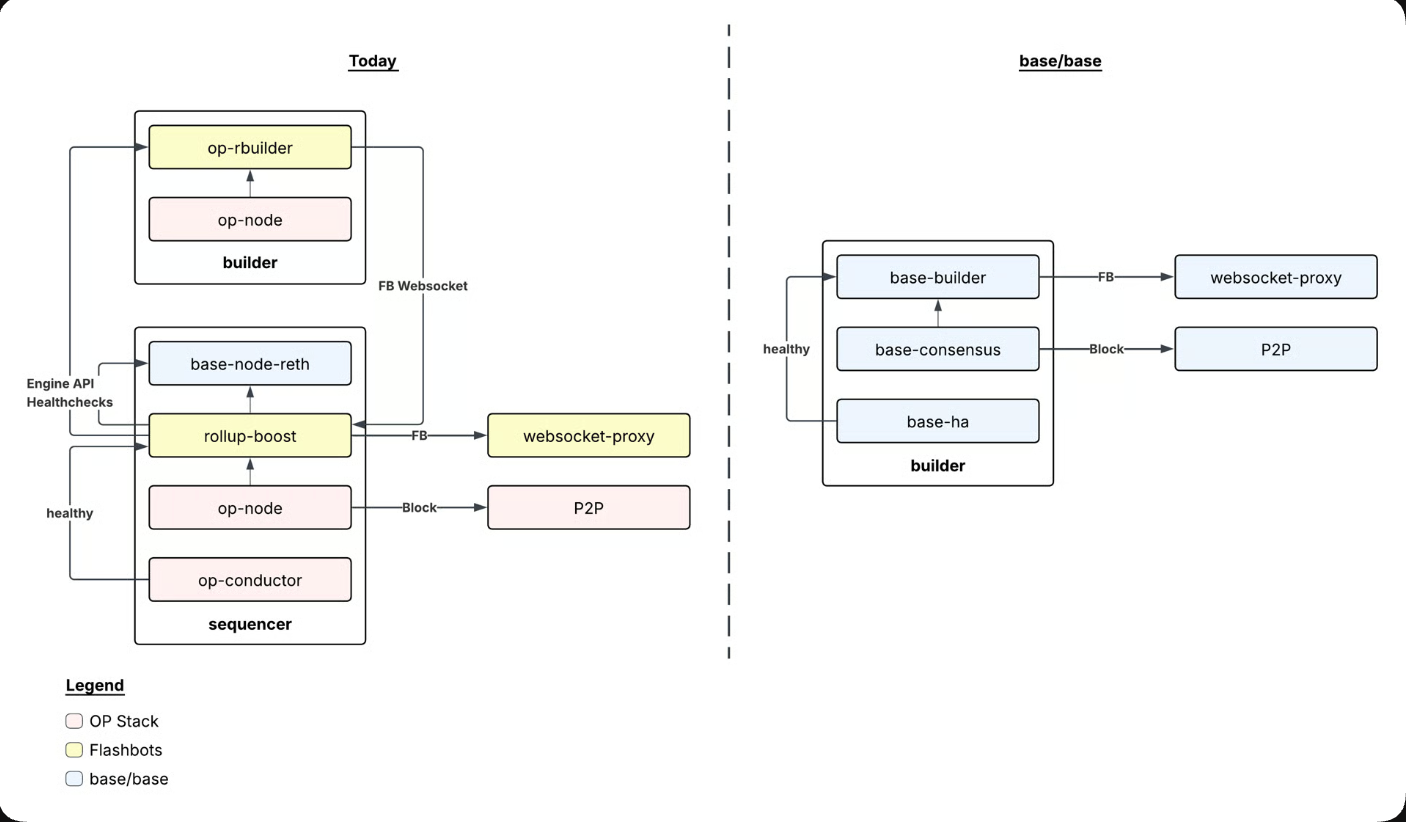
Base, the decentralized Ethereum layer-2 scaling network, said Wednesday that it is transitioning from running on Optimism’s L2 tech stack to its own unified software architecture.
Launched in 2023 as an Optimism chain, Base is shifting to its own tech stack to reduce dependence on external service providers and shorten the time to ship new upgrades, according to an announcement from Base. The team said:
“Consolidating into Base changes how Base packages and releases software for the network. We will ship one official distribution for each upgrade: a single Base binary for operating nodes on the network.”
The transition is also expected to simplify the Base network’s sequencer, which helps network validators to order transactions, the Base engineering team said.

The rollout will take place in four phases, according to the project’s roadmap, with node runners required to switch to the new Base client over the next several months for official upgrades.
Related: Base says configuration change caused transaction delays, fixes issue
Ethereum co-founder changes tune on layer-2 scaling networks
Earlier this month, Vitalik Buterin, the co-founder of the Ethereum L1 blockchain network, reversed course on scaling Ethereum through L2s.

L2s are taking longer than initially thought to transition to fully decentralized models, Buterin said, adding that the Ethereum L1 is already scaling on its own and features record-low network fees.
“The original vision of L2s and their role in Ethereum no longer makes sense, and we need a new path,” Buterin said in February.
Buterin’s comments drew mixed reactions from L2 teams, with some agreeing that scaling networks must pivot beyond being a cheaper execution layer for Ethereum.
“It’s great to see Ethereum scaling L1 — this is a win for the entire ecosystem. Going forward, L2s can’t just be ‘Ethereum but cheaper,’” Base founder Jesse Pollak said in response.

Other L2 founders contend that scaling layers are already in alignment with the network’s long-term goals.
There are more than 128 different Ethereum L2 scaling networks at the time of publication, according to L2Beat.
Magazine: Coinbase and Base: Is crypto just becoming traditional finance 2.0?
Crypto World
Retail Investors Hit Record $48 Billion Stock Buying Spree as Institutional Investors Head for the Exit

TLDR:
- Retail investors recorded the largest-ever three-week stock buying spree, surpassing GameStop and 2021 crypto mania levels.
- Household equity allocations reached 45–49%, exceeding the dot-com bubble’s 40% peak by as many as nine percentage points.
- The money market-to-market cap ratio sits at 0.19, matching the 2021 peak and far below the 0.35 threshold for a real market bottom.
- Institutions sold $31 billion in April while Warren Buffett held a record $325 billion cash position, signaling elite-level caution.
Retail investors have funneled $48 billion into equities over just three weeks, marking the largest retail buying spree ever recorded.
This surge surpasses even the GameStop frenzy and the 2021 crypto market euphoria. It also exceeds the retail activity recorded before the 2022 market downturn.
Meanwhile, household equity allocations have reached 45–49%, well above the dot-com bubble’s 40% peak. Several market indicators are now flashing levels not seen since prior major corrections.
Household Allocations and Cash Levels Raise Red Flags
Retail investors are currently allocating a historic share of household wealth to equities. That figure sits between 45 and 49%, surpassing the dot-com bubble’s peak of 40%. The dot-com collapse that followed wiped out trillions in market value across two years.
Crypto analyst Leshka.eth posted on X, noting that the money market-to-market cap ratio stands at 0.19. That matches the exact reading from the 2021 market peak. Analysts typically look for a ratio of 0.35 or higher before calling a real market bottom.
By that measure, the market would need roughly 84% more cash on the sidelines to reach normal levels. The common argument that sidelined cash will rescue equity markets does not hold up against this data. The numbers tell a different story from the bullish narrative.
This pattern mirrors conditions seen before the 2000 and 2008 crashes. In both cases, retail confidence peaked just before institutions began quietly reducing exposure. History shows this sequence has repeated without exception.
Margin Debt and Institutional Behavior Signal Caution
Margin debt has climbed to over $800 billion, approaching record territory. The last two times margin debt peaked at similar levels were March 2000 and October 2007. Both periods preceded market drawdowns exceeding 50%.
The put/call ratio has also dropped to extreme lows. Retail investors are currently buying three times more call options than put options. That level of directional confidence has historically appeared just before sharp market reversals.
Institutional behavior is moving in the opposite direction. According to the same post by Leshka.eth, institutions sold $31 billion worth of equities in April alone, while retail continued to buy. Warren Buffett’s cash position has also reached a record $325 billion.
Past cycles reinforce this concern. In 2022, retail bought $33 billion before a crash and sold $10 billion at the bottom. In 2007, retail equity funds saw $72 billion in inflows, followed by $234 billion in outflows during the crisis. The 2000 peak followed the same script, with record retail flows into tech funds right at the top.
Crypto World
SOL Traders Lose Reasons To Hold As Solana Activity Slumps
Key takeaways:
-
SOL is struggling to hold $80 as a 75% drop in futures’ open interest shows that traders are heading for the exits rather than opening new bets.
-
Solana remains heavily dependent on retail and memecoin activity, while Ethereum maintains its lead in high-value decentralized finance.
Solana’s native token, SOL (SOL), has hit a wall, repeatedly failing to break back above $89 over the last two weeks. This sluggish price action follows a rejection at $145 in mid-January and a sharp drop to $67.60 during the Feb. 6 crash. Demand for bullish leverage has essentially evaporated as traders brace for more pain.

Those betting against SOL are currently paying an annual rate of 20% just to keep their short positions open, a rare and aggressive move. When funding rates remain negative for over a week, it shows bears have strong conviction. In contrast, ETH’s annualized funding rate sat at 1% on Wednesday. While that’s below the usual 6% neutral mark, it’s nowhere near the lopsided levels seen in SOL.
Frustration is mounting as SOL underperformed the rest of the crypto market by 11% over the past 30 days.

Even though SOL remains among the top seven cryptocurrencies by market cap, the 67% slide from its $253 peak in September 2025 has left a mark on both onchain activity and derivatives. In fact, SOL futures open interest has dropped 75% from its $13.5 billion high seen only five months ago.
Solana “death spiral” feared
This price slump is also hurting the decentralized applications (DApps) built on Solana. Revenues are down across the board, from staking and decentralized exchanges to launchpads and lending platforms. Investors are starting to worry about a “death spiral,” in which falling prices reduce incentives, making it harder for people to justify holding SOL for the long haul.

Weekly DApp revenue on Solana dropped to $22.8 million, the lowest since October 2024. Notably, the memecoin launchpad Pump generated $9.1 million in revenue over those seven days, accounting for 40% of the network’s total revenue. In comparison, weekly DApps revenue on Ethereum totaled $16 million, up 2% from the previous month.
Related: Pump.fun rolls out trader cashbacks in tweak to memecoin model
Unlike Solana, the top revenue-generating DApps on Ethereum are Sky, Flashbots, and Aave — key infrastructure players for decentralized finance. Essentially, Solana is heavily dependent on retail onboarding and the memecoin sector, while Ethereum has secured its lead in total value locked (TVL) and use cases that require higher decentralization.
This weak institutional demand is visible in SOL exchange-traded funds (ETFs). Solana’s high transaction volume and second-place TVL haven’t been enough to convince traditional investors to buy into SOL ETFs offered by Bitwise, Fidelity, Grayscale, 21Shares, CoinShares and REX-Osprey.

While relevant, Solana’s $2.1 billion in ETF assets under management is still 86% behind Ethereum’s $15.8 billion. Many investors have lost confidence that demand for Solana DApps will spike anytime soon, likely a side effect of the heavy hype around memecoins and launchpads.
For SOL to regain its bullish momentum, it will likely need a push from sectors like artificial intelligence infrastructure and prediction markets. These areas show promise, but the competition is fierce.
Presently, weak SOL derivatives and Solana onchain metrics are a warning sign. Any further disappointment may trigger another price drop, putting the already shaky $78 support level at serious risk.
This article does not contain investment advice or recommendations. Every investment and trading move involves risk, and readers should conduct their own research when making a decision. While we strive to provide accurate and timely information, Cointelegraph does not guarantee the accuracy, completeness, or reliability of any information in this article. This article may contain forward-looking statements that are subject to risks and uncertainties. Cointelegraph will not be liable for any loss or damage arising from your reliance on this information.
Crypto World
Bitcoin ETFs Extend Losses as Solana Funds Keep Ground
US-listed spot Bitcoin exchange-traded funds (ETFs) continued to bleed on Wednesday as market sentiment remained negative and BTC briefly dipped below $66,000.
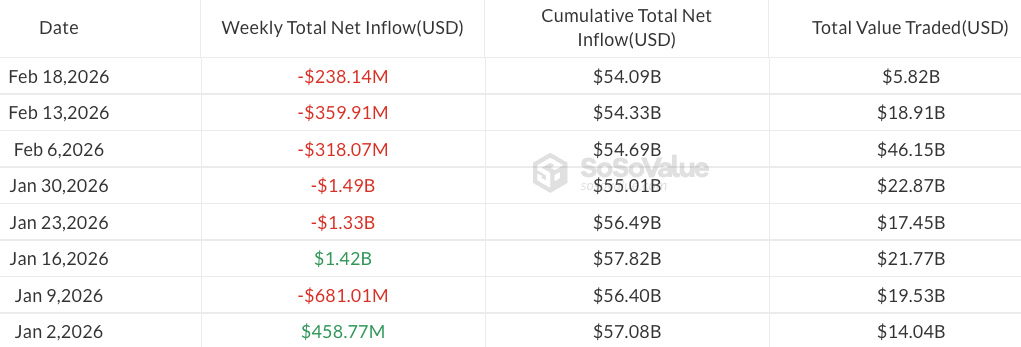
Spot Bitcoin ETFs recorded $133.3 million in net outflows on Wednesday, bringing weekly losses to $238 million, according to SoSoValue data. BlackRock’s iShares Bitcoin Trust (IBIT) led outflows, with over $84 million exiting.
Trading volumes remained subdued at less than $3 billion, highlighting a persistent lack of activity even as analysts had previously noted potential inflection points amid the slowdown in outflows.

If the ETFs fail to recover in Thursday and Friday sessions, this week will mark the first five-week outflow streak for Bitcoin (BTC) ETFs since last March.
Year-to-date, Bitcoin ETFs have seen about $2.5 billion in outflows, leaving assets under management at $83.6 billion.
Solana ETFs keep bucking the trend after launch in late 2025
While Ether (ETH) and XRP (XRP) ETFs posted modest daily outflows of $41.8 million and $2.2 million, respectively, Solana (SOL) funds continued to buck the trend.
Solana ETFs have recorded a six-day streak of inflows, with year-to-date gains totaling around $113 million. Trading activity, however, remains subdued compared with past months, as February inflows of $9 million so far are well below $105 million in January and December 2025’s $148 million.

Since their October 2025 launch, US spot Solana ETFs have accumulated almost $700 million in assets under management, trailing XRP funds, which have amassed $1 billion since their November debut.
Crypto market remains in extreme fear, BTC down 24% year-to-date
The ongoing sell-off in Bitcoin ETFs comes as the Crypto Fear & Greed Index continues to signal persistent negative sentiment.
Even though Bitcoin has slightly recovered from multi-month lows near $60,000 logged in early February, the index has remained mostly in “Extreme Fear” territory.

At the time of writing, Bitcoin traded at $67,058 on Coinbase, down about 24% year-to-date. Analysts at major financial institutions, including Standard Chartered, have predicted that BTC could fall as low as $50,000 before potentially recovering to $100,000 later in 2026.
Related: Bitwise, GraniteShares join race for prediction market-style ETFs
According to the crypto analytics platform CryptoQuant, Bitcoin’s short-term Sharpe ratio has reached levels historically associated with “generational buying zones.”
“The arrows in the chart illustrate this clearly: each prior extreme negative reading was followed by violent recoveries to new highs,” CryptoQuant analyst Ignacio Moreno De Vicente said.
Magazine: Did a Hong Kong fund kill Bitcoin? Bithumb’s ‘phantom’ BTC: Asia Express
Crypto World
Ledn’s $188M Bitcoin-Backed ABS Deal Enters US Bond Market
Bitcoin-backed loan platform Ledn sold about $188 million of bonds tied to Bitcoin‑collateralized consumer loans into the mainstream asset‑backed securities (ABS) market, Bloomberg reported on Wednesday, citing people familiar with the matter.
In a first-of-its-kind deal, one of the two tranches — the investment‑grade portion — was reportedly priced at a spread of about 335 basis points over a benchmark rate, implying that investors are demanding 3.35 percentage points in extra yield to hold crypto‑linked credit risk rather than conventional consumer ABS.
The deal is structured through Ledn Issuer Trust 2026‑1, which securitizes a pool of 5,441 short‑term, fixed‑rate balloon loans extended to 2,914 US borrowers, backed by 4,078.87 Bitcoin (BTC) held as collateral, according to S&P Global Ratings’ preliminary documentation on Feb. 9.
How the structure and ratings stack up
Balloon loans are structured with relatively small periodic payments and a large lump‑sum “balloon” payment at maturity, which keeps near‑term payments low but leaves a sizeable principal balance due at the end.
S&P assigned preliminary BBB‑ (sf) and B‑ (sf) ratings to the $160 million senior Class A notes and $28 million subordinated Class B notes, respectively.
Related: $25B crypto lending market now led by ‘transparent’ players: Galaxy
A BBB- rating is the lowest tier of investment-grade debt, reflecting an adequate capacity to meet financial commitments but higher vulnerability to adverse conditions than higher‑rated bonds, while B‑ sits in deep non‑investment‑grade “junk” territory, where default risk is materially higher.
Jefferies Financial Group acted as the sole structuring agent and bookrunner, as a major Wall Street dealer intermediated between institutional fixed‑income investors and this new form of crypto‑linked exposure.
BTC increasingly seen as legitimate collateral
Bitwise head of research Europe, Andre Dragosch, told Cointelegraph that the fact that Ledn was able to package these loans into a traditional ABS implied that BTC is “increasingly seen as safe and legit collateral by traditional financial institutions.”
He highlighted major banks like JPMorgan offering BTC-backed loans to customers as a further indication of this. “Bitcoin is increasingly being integrated into traditional finance as the new pristine collateral,” he said.
Jinsol Bok, research lead at Four Pillars global crypto research company, told Cointelegraph that this means liquidity no longer needs to remain locked up and “can instead be expanded into new lending,” adding that the size of the BTC collateralized lending market could “grow far beyond its current level in the future.”
Related: Anchorage–Mezo partnership opens institutional access to BTC-backed loans
He said that unlike real estate mortgages, BTC collateralized loans could be transparently tracked onchain and liquidated in a programmable manner. “For this reason, I believe that the risks associated with ABS in this context do not need to be excessively overstated.”
What investors are buying
Asset‑backed securities are bonds funded by pools of loans, so investors in Ledn’s notes do not own Bitcoin (BTC) directly.
Instead, they take on credit and structural risk to a pool of BTC‑secured loans whose performance depends on borrower repayments and the lender’s ability to liquidate collateral during market stress.
“These loans generally have a low default rate because they tend to have low LTV [loan-to-value] ratios and are well capitalized with BTC,” Dragosch said.
Founded in 2018, Ledn says it has funded over $9.5 billion in loans so far in over 100 countries. The company received a strategic investment from Tether, the issuer of the USDt (USDT) stablecoin, in November 2025.

Cointelegraph reached out to Ledn for comment but had not received a response by publication time.
Big questions: Should you sell your Bitcoin for nickels for a 43% profit?
Crypto World
DOGE price eyes $0.20 if X, CLARITY Act spark breakout above $0.18
DOGE price slips ~1% in 24h, holding $0.09–$0.10 as traders eye X, CLARITY Act.
Summary
- DOGE price is trading around $0.098–$0.099, holding $0.09–$0.10 support but stuck below major MAs and a structural daily downtrend.
- Resistance sits near $0.104–$0.116, with $0.116 flagged as pivotal level aligning with upper Bollinger Band and 50% Fib of January’s drop.
- Base case is range‑bound; break above $0.116 could target $0.15–$0.20, while a clean loss of $0.09 risks a retest of yearly lows.
Dogecoin (DOGE) price is clinging to support just under the $0.10 mark, trading around $0.0988 as meme‑coin bulls try to turn a shaky bounce into a sustained reversal. Analysts describe the move as a “fragile recovery” after DOGE defended key support but failed to break out of its broader downtrend.
Market backdrop and key levels
Dogecoin is changing hands near $0.098–$0.099 today, marginally lower over the past 24 hours as liquidity concentrates around a tight support zone. A recent weekly analysis notes that DOGE “is currently trading at $0.099, staging a recovery attempt after successfully defending a critical support zone,” but stresses that “the daily chart confirms that Dogecoin remains in a structural downtrend.” Technicians flag resistance around $0.104–$0.116, with one wave analysis pointing to $0.1160 as “pivotal resistance,” aligning with the upper Bollinger Band and a 50% Fibonacci retracement of January’s selloff.
Crypto.news warns that the token “dropped to the important support level at $0.100, much lower than this month’s high of $0.1176,” and now trades below all major moving averages, with momentum gauges stuck in bearish territory. In parallel, bitcoin is trading near $66,879, down about 1.2% on the day, while ether changes hands around $2,466, up just under 1% over the same period, underscoring a cautious, range‑bound majors environment.
Catalysts and near‑term outlook
Sentiment hinges on two overlapping narratives: regulatory clarity and big‑tech integration. A recent outlook argues DOGE “could reach $0.20 in February 2026” if market growth, meme‑coin rotation and risk appetite align, but stresses that breaking “significant technical resistance levels” around $0.18–$0.20 with high volume is essential. Separate coverage highlights that DOGE’s recent spikes have tracked rumors around X’s crypto‑trading features and potential payment support, with one desk noting the coin “jumped 15.25% to $0.1113” following X’s trading announcement as volume surged to $1.76 billion on strong whale activity.
For now, the base case is range‑bound: DOGE holding the $0.09–$0.10 floor while facing overhead supply into the low‑$0.11s. A decisive close above $0.116 with expanding volume would open room toward $0.15, while a loss of $0.09 support risks a retest of the yearly lows. Traders watching this compressing range are effectively betting on whether the next major impulse comes from Washington’s CLARITY Act headlines or the next product move out of X.
Crypto World
Aptos Tokenomics Overhaul Targets Deflationary APT Supply Through Performance-Driven Mechanisms

TLDR:
- Aptos Foundation proposes cutting annual staking rewards from 5.19% to 2.6% to reduce long-term token emissions.
- A hard protocol-level cap of 2.1 billion APT will permanently limit total supply once approved through governance.
- Decibel DEX’s fully onchain execution model is projected to burn over 32 million APT annually at 100+ markets.
- Aptos Foundation will permanently stake 210 million APT, removing nearly 18% of circulating supply from distribution.
Aptos tokenomics is undergoing a structural overhaul designed to replace bootstrap-era subsidies with performance-linked supply mechanics.
The Aptos Foundation has outlined seven reform proposals tied to network activity, burn rates, and staking adjustments.
These changes target a crossover point where token removals exceed new token issuance. With major institutions already active onchain and a new decentralized exchange launching, the network is positioning itself for an institutional-grade economic model.
Hard Supply Cap and Staking Rate Cuts Anchor the Reform
The most definitive change proposed is a hard protocol-level cap of 2.1 billion APT. Currently, 1.196 billion APT circulate with no ceiling on future minting. The cap would close that open-ended issuance permanently once approved through governance.
Alongside the cap, the Aptos Foundation plans to propose cutting the annual staking reward rate from 5.19% to 2.6%.
The prior rate had already been reduced via AIP-119. This further cut aims to slow new token issuance without removing validator incentives entirely.
“Aptos Foundation believes it is critical to balance strong validator incentives with long-term supply discipline.” — Aptos Foundation
To balance the reduction, the Foundation is exploring a tiered staking model. Participants committing to longer lock-up periods would receive higher reward rates than short-term stakers.
Validator costs are also expected to drop through new architecture proposed in AIP-139, keeping operations viable even at lower reward rates.
Gas Fee Increase and Decibel DEX Drive Burn Acceleration
Aptos tokenomics reform also targets the burn side of the equation through a proposed 10x gas fee increase. All transaction fees on Aptos are permanently burned, so raising fees directly accelerates APT removal from circulation. Even after the increase, stablecoin transfers would cost roughly $0.00014, remaining the lowest globally.
The launch of Decibel, a fully onchain decentralized exchange incubated by Aptos Labs, adds a structural burn mechanism.
Unlike most DEX platforms, Decibel executes every order, match, and cancel onchain. That architecture generates high transaction volume continuously, which translates directly into sustained APT burns.
“The more markets listed and products supported by Decibel, the higher operational TPS is necessary. As Decibel approaches 100+ markets going into next year, it is projected to burn over 32 million APT per year.” — Aptos Foundation
At scale, Decibel is projected to burn over 32 million APT annually as it approaches 100 active markets. As throughput grows toward 10,000 TPS and beyond, that figure scales commensurately.
Together with the gas fee increase, this creates compounding deflationary pressure tied directly to trading activity.
Foundation Lock-Up, Buybacks, and Performance Grants Complete the Framework
The Aptos Foundation has committed to permanently staking 210 million APT, removing those tokens from any future sale or distribution. This represents roughly 18% of the current circulating supply.
The Foundation will fund its operations through staking rewards on these locked tokens rather than token sales.
“This is functionally equivalent to a token burn with 210 million APT removed from any sale or distribution.” — Aptos Foundation
On top of that, the Foundation is exploring a programmatic buyback program. The program would use cash reserves and revenue from licensing and ecosystem investments to purchase APT in the open market. Buyback timing would be based on market conditions rather than a fixed schedule.
Grant issuance is also being restructured around milestone-based vesting. Future grants tied to Aptos’s global trading engine positioning will only vest when specific performance targets are met.
If KPIs are missed, grants are deferred, not canceled, until those targets are achieved. This directly links token issuance to measurable network outcomes.
Taken together, these mechanisms are intended to create a crossover point where APT burned and locked consistently exceeds APT issued.
Natural unlock reductions are already underway, with the four-year investor and contributor unlock cycle concluding in October 2026, cutting annualized supply unlocks by 60%. Foundation grant distributions are also falling over 50% year-over-year from 2026 to 2027.
The combination of those natural dynamics with the proposed structural reforms positions APT supply for a sustained deflationary trajectory as high-throughput financial applications continue to scale on the network.
Crypto World
Coinbase Unlocks $100,000 Borrowing Power for XRP, DOGE, ADA, and LTC Holders

TLDR:
- Coinbase onchain loans now accept XRP, DOGE, ADA, and LTC as collateral, capped at $100,000 in USDC.
- The lending product has surpassed $1.9 billion in total loan originations since its initial Bitcoin launch.
- Altcoin borrowers face a tighter 49% LTV limit, with liquidation triggering at 62.5% due to price volatility.
- Wrapping native assets like XRP for use on Base may constitute a taxable event under current U.S. tax rules.
Coinbase onchain loans have expanded to include four new cryptocurrencies as eligible collateral. XRP, Dogecoin (DOGE), Cardano (ADA), and Litecoin (LTC) holders in the U.S. can now borrow up to $100,000 in USDC.
The loans run through the Morpho lending protocol on Base, Coinbase’s Ethereum layer-2 network. Users post their crypto holdings as collateral and receive USDC without selling their assets. New York residents remain excluded from the service at this time.
Coinbase Expands Collateral Options Beyond Bitcoin and Ether
Coinbase originally launched its onchain loan product with Bitcoin support before adding Ether. That early offering allowed BTC holders to borrow up to $5 million and ETH holders up to $1 million in USDC. The product has now crossed $1.9 billion in total loan originations since its launch.
The four newly added assets carry a lower borrowing cap of $100,000 each. Their combined market capitalization stood at around $117 billion at the time of the announcement, according to CoinGecko data.
That figure is less than half of Ethereum’s total market value, though all four coins maintain a consistent retail following.
Jacob Frantz, product lead at Coinbase, explained the thinking behind the move:
“No matter what you’re holding, you should be able to leverage your crypto without having to sell. Being able to borrow against more tokens means more opportunity to make your crypto work for you.” — Jacob Frantz, Product Lead, Coinbase
Coinbase has indicated plans to extend the service internationally in the future.
Loan-to-Value Ratios Reflect Altcoin Volatility
The loan-to-value ratio, or LTV, is central to how these loans operate. It measures loan size against the current market value of the posted collateral. As collateral prices drop or interest builds, the LTV rises accordingly.
Bitcoin and Ether borrowers can access up to 75% LTV, with liquidation triggering at 86%. XRP, DOGE, ADA, and LTC holders face tighter terms, borrowing up to 49% LTV, with liquidation set at 62.5%. The stricter limits reflect the higher price volatility these altcoins carry compared to Bitcoin and Ether.
There is no fixed repayment schedule attached to these loans. However, borrowers must keep their LTV below the liquidation threshold at all times.
Coinbase sends alerts as frequently as every 30 minutes as a borrower’s ratio approaches the danger zone, providing an added layer of risk management.
Tax Considerations and Platform Restrictions Apply
Crypto-backed loans are often seen as a way to avoid triggering capital gains taxes. Since no sale occurs, the tax event is deferred. That said, liquidations can create taxable events, according to law firm Greenspoon Marder LLP.
There is also a wrapping issue to consider. Assets like XRP are wrapped before use on Base, Coinbase’s Ethereum-compatible network.
Under current U.S. tax rules, converting a native asset to its wrapped version counts as a taxable event. Coinbase has acknowledged this and noted it does not provide tax advice.
One additional restriction applies to loan proceeds. Borrowers cannot use the USDC received to trade on the Coinbase exchange.
This steers users toward practical uses, such as covering expenses or making purchases, rather than leveraged speculation.
Interest rates on Morpho markets fluctuate based on supply and demand within each lending pool, so rates are not fixed at the time of borrowing.
Crypto World
AlienWP Relaunches as Alien Wise Play: Expanding Into iGaming News, Casino Reviews, and a New Player Dashboard App
February 2026 — AlienWP.com, a long-established digital platform has officially relaunched as Alien Wise Play, a new independent hub focused on online casino reviews, iGaming news, and player-first safety tools.
The brand’s expansion marks a significant new chapter for the AlienWP domain, bringing its legacy of clarity, transparency, and user-focused guidance into the rapidly growing world of online gaming and digital gambling.
A New Focus on Trust, Transparency, and Smarter Play
Alien Wise Play has been created to help players navigate an increasingly complex online casino landscape, where licensing standards, bonus terms, payout reliability, and player protections can vary significantly between operators.
The platform provides structured casino reviews, clear educational content, and ongoing iGaming news coverage, with a focus on transparency rather than hype.
“At its core, Alien Wise Play is about helping players make smarter decisions online,” said a spokesperson for the project. “The casino space is crowded, and users deserve independent information they can actually trust.”
Introducing the Wise Play Score
A central feature of the new platform is the Wise Play Score, an independent rating system designed to assess casinos based on the factors that matter most to players.
Rather than relying on subjective star ratings or promotional rankings, the Wise Play Score evaluates operators across areas such as licensing, payment reliability, bonus fairness, game quality, and customer support — providing a clear trust-focused score from 0 to 10.
The company emphasised that scores cannot be bought or influenced through commercial partnerships, and that player safety remains the top priority.
Expanding Into iGaming News and Industry Coverage
Alongside casino reviews and rankings, Alien Wise Play is also launching as a growing source of iGaming news, covering major developments across the online gambling industry.
The site will publish updates on licensing changes, operator launches, regulatory trends, and emerging topics such as crypto gaming, responsible gambling tools, and player protection standards.
This broader editorial direction positions Alien Wise Play as more than an affiliate comparison site — aiming instead to become a trusted industry resource for both players and operators.
Future Plans: A Mobile-First Player Dashboard App
Looking ahead, Alien Wise Play confirmed that it is currently developing a new mobile-first web app designed to give players something the industry has long lacked: a personal dashboard to manage online casinos in one place.
The upcoming app will allow users to save favourite casinos, track bonuses, compare platforms using the Wise Play Score, and receive useful alerts.
The platform is being built as a utility layer above casinos, focused on organisation, safety, and informed decision-making.
The app is expected to launch in stages later this year.
About Alien Wise Play
Alien Wise Play is an independent online casino review and iGaming news platform built to promote transparency, player safety, and responsible gambling. The site provides structured casino profiles, trust-based scoring, bonus tracking tools, and educational content to help users play smarter.
Originally launched in 2013 as AlienWP, the platform has evolved into a modern resource focused on the future of online gaming and digital entertainment.
For more information, visit https://alienwp.com
Media Contact
Press & Partnerships
Email: contact@kooc.co.uk
Website: alienwp.com
Crypto World
Ripple (XRP) Drops 5% Daily, Bitcoin (BTC) Slips to $67K: Market Watch
M, HASH, and ZEC have plunged the most in the past 24 hours.
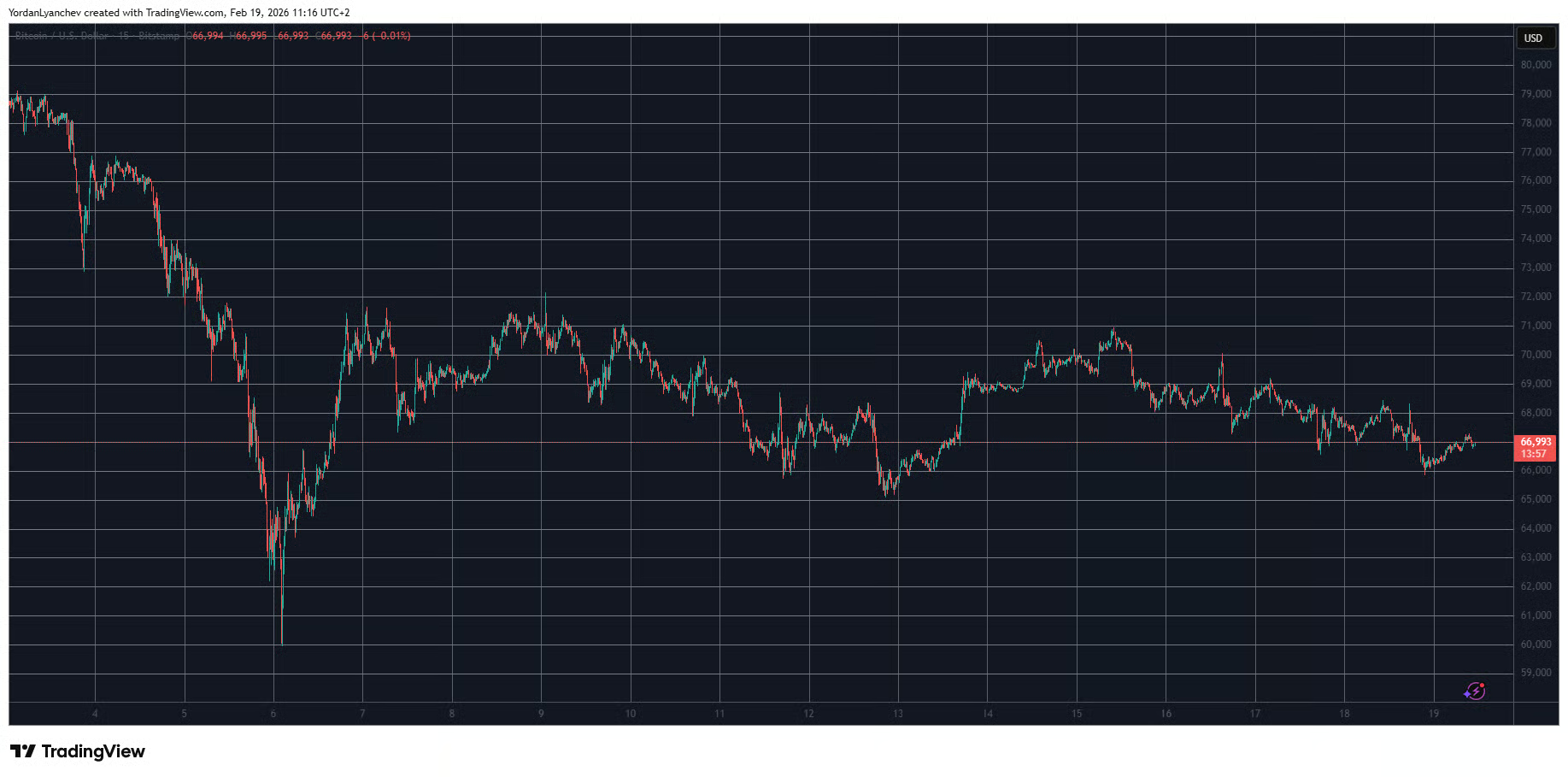
Bitcoin’s struggles since the beginning of the business week continued in the past 24 hours as the asset dipped below $66,000 before rebounding slightly to $67,000 as of now.
Most altcoins are in the red as well, with ETH losing the $2,000 support once again. XRP is among the poorest performers among the larger caps.
BTC Down to $67K
Although the primary cryptocurrency bounced off immediately on February 6 when it plunged to a 15-month low at $60,000 to $72,000, it has been unable to stage a more profound recovery since then. Just the opposite, it was rejected several times at the $71,000-$72,000 resistance, with the latest example taking place over the past weekend.
At the time, BTC jumped to $71,000 and was close to breaking above it. However, the bears quickly intercepted the move and drove the asset south to $67,000 on Tuesday. The adverse price moves continued yesterday, and bitcoin dipped below $66,000 for the first time since last Friday.
It managed to rebound since that weekly low, and now sits at $67,000. However, this still means that it’s over 1.5% down on the day. Its market capitalization has fallen below $1.340 trillion, while its dominance over the alts struggles below 56.5% on CG.
Alts Back in Red
Almost all altcoins are in the red once again today. Ethereum’s adventure above $2,000 was short-lived once again, and the asset is back below it as of press time. XRP and SOL have dropped the most from the larger caps, with losses of nearly 5%. As a result, XRP trades inches above $1.40 while SOL is down to $82.
DOGE, ADA, BNB, LINK, and CC are also in the red by up to 4%, while ZEC has plunged by 8.5% to $260. Further losses are evident from M and Hash, both of which have dumped by more than 10%.
The total crypto market cap has erased another $50 billion daily and is down to $2.370 trillion on CG.
SECRET PARTNERSHIP BONUS for CryptoPotato readers: Use this link to register and unlock $1,500 in exclusive BingX Exchange rewards (limited time offer).
Disclaimer: Information found on CryptoPotato is those of writers quoted. It does not represent the opinions of CryptoPotato on whether to buy, sell, or hold any investments. You are advised to conduct your own research before making any investment decisions. Use provided information at your own risk. See Disclaimer for more information.
-
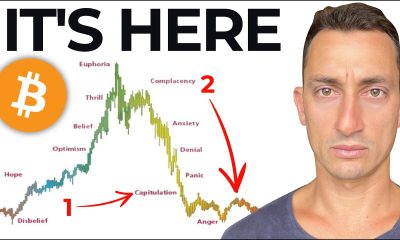
 Video3 days ago
Video3 days agoBitcoin: We’re Entering The Most Dangerous Phase
-

 Tech4 days ago
Tech4 days agoLuxman Enters Its Second Century with the D-100 SACD Player and L-100 Integrated Amplifier
-
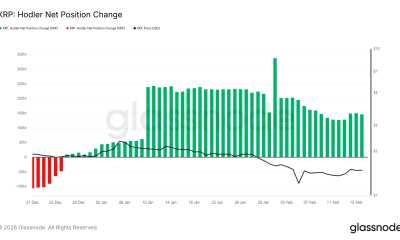
 Crypto World2 days ago
Crypto World2 days agoCan XRP Price Successfully Register a 33% Breakout Past $2?
-

 Sports2 days ago
Sports2 days agoGB's semi-final hopes hang by thread after loss to Switzerland
-

 Video6 days ago
Video6 days agoThe Final Warning: XRP Is Entering The Chaos Zone
-

 Tech2 days ago
Tech2 days agoThe Music Industry Enters Its Less-Is-More Era
-

 Business1 day ago
Business1 day agoInfosys Limited (INFY) Discusses Tech Transitions and the Unique Aspects of the AI Era Transcript
-

 Video2 days ago
Video2 days agoFinancial Statement Analysis | Complete Chapter Revision in 10 Minutes | Class 12 Board exam 2026
-

 Entertainment21 hours ago
Entertainment21 hours agoKunal Nayyar’s Secret Acts Of Kindness Sparks Online Discussion
-
 Crypto World5 days ago
Crypto World5 days agoBhutan’s Bitcoin sales enter third straight week with $6.7M BTC offload
-

 Tech1 day ago
Tech1 day agoRetro Rover: LT6502 Laptop Packs 8-Bit Power On The Go
-

 Sports7 hours ago
Sports7 hours agoClearing the boundary, crossing into history: J&K end 67-year wait, enter maiden Ranji Trophy final | Cricket News
-

 Entertainment13 hours ago
Entertainment13 hours agoDolores Catania Blasts Rob Rausch For Turning On ‘Housewives’ On ‘Traitors’
-

 NewsBeat4 days ago
NewsBeat4 days agoThe strange Cambridgeshire cemetery that forbade church rectors from entering
-

 Business7 days ago
Business7 days agoBarbeques Galore Enters Voluntary Administration
-

 Crypto World6 days ago
Crypto World6 days agoKalshi enters $9B sports insurance market with new brokerage deal
-

 Business1 day ago
Business1 day agoTesla avoids California suspension after ending ‘autopilot’ marketing
-

 Crypto World16 hours ago
Crypto World16 hours agoWLFI Crypto Surges Toward $0.12 as Whale Buys $2.75M Before Trump-Linked Forum
-
 Crypto World7 days ago
Crypto World7 days agoEthereum Price Struggles Below $2,000 Despite Entering Buy Zone
-

 NewsBeat4 days ago
NewsBeat4 days agoMan dies after entering floodwater during police pursuit









