Tech
A warning to Seattle: Don’t become the next Cleveland


Consider a successful mid-sized American city. One with decades of population growth. Median household incomes on par with or exceeding New York City. A bustling port in a prime location. Bold civic architecture. A vibrant arts and cultural scene. And home to some of the world’s biggest and most valuable companies.
That could be Seattle. It also describes Cleveland about 75 years ago. In the 1950s, Cleveland was an epicenter for the era’s “Big Tech.” Industrial giants like Standard Oil, Westinghouse, Republic Steel, and Sherwin Williams were all founded in Cleveland. Like engineering outposts in Seattle, other leading companies including General Motors and U.S. Steel were well represented locally.
Yet Cleveland’s success unraveled remarkably quickly. Within 20 years, when the Cuyahoga River caught fire in 1969, the city was seared into history as “the mistake on the lake.” The population has declined by 60% since 1950 (and is still shrinking). Cleveland has gone from the seventh largest U.S. city in the country to the 56th. Median household incomes are now less than half the national average — and less than 40% of the Seattle area.
Today in Seattle tech circles there is great trepidation about the region’s next act. Seattle is not punching above its weight in the AI era the way we did in the software era. We might not even be punching our weight.
Entrepreneurs, executives, investors, and technologists are departing, either because they don’t think they can be competitive here in the white-hot AI market and/or are concerned about a deteriorating business environment. And the exodus appears to be accelerating.
You might take solace that our little corner of the country hosts two of the world’s five biggest companies (which is a little crazy). But it is easy to believe both Amazon and Microsoft are past peak employee count, as they become more capital-intensive and lean into AI-driven productivity. Other local tech companies and engineering centers are also shrinking, while new job listings have plummeted.
While the tech sector confronts existential dread, the political class in Seattle and Washington state seems oblivious. They don’t have much to say about creating jobs or nurturing industries of the future (or even of the present). Revenue is their focus above all else, with considerably less emphasis on how our taxes translate into efficient and effective provision of government services.

The traditional Seattle civic partnership between business and government has frayed. Few lessons have been learned from Boeing’s slow-motion migration out of the Seattle area (Washington is now home to just over a third of Boeing employees, and due to decrease further).
Relations between the tech industry and government are rocky, with the industry seen almost exclusively as a bottomless source of revenue. It would be shocking — but not surprising — to one day learn Amazon and/or Microsoft are moving their headquarters out of the state. (Bellevue already looks like Amazon’s HQ1 in all but name).
The tech boom has been an immense boon for Seattle, as the city attracted talent from all over the world. Seattle’s population has grown by almost 40% in the 21st century, and the City of Seattle rode that tailwind. The city’s inflation-adjusted budget grew over three times faster than the population over the same period.
That growth raises some obvious questions. Are city services three times better? How long can government spending keep outgrowing the population? What happens if population growth slows — or even reverses?
Meanwhile, city issues loom large in the desirability of doing business in Seattle. Downtown is barren, with record vacancies. Public safety, housing and homelessness are perennial hot topics, but progress is scarcer. After the recent election, we’re apparently going to take another shot at those persistent problems with progressive panaceas that have seen limited success, both locally and elsewhere.

Completely missing from any discussion is the crisis in our schools, where the majority of fourth and eighth graders in Seattle are not proficient in reading or math. Education is one of the most effective solutions to many social ailments — and a mandatory prerequisite for an advanced civilization — yet we’ve seemingly given up.
Which brings us back to Cleveland. When its fortunes began to shift, Cleveland’s politicians made a bad situation worse. A confrontational, short-term posture from government made it easy for companies to put Cleveland plants at the top of their closure lists. Contrast that with another Rust Belt city, Pittsburgh, where politicians and business worked together to accept and manage the inevitable transition. They defined the post-industrial playbook for cities — one Cleveland belatedly adopted.
Seattle has always been a lucky city. Prosperity has often come from unexpected sources. The Alaska gold rush was, quite literally, a gold rush. Bill #1 (Boeing) made Seattle synonymous with aerospace. Proximity to Alaska gave us a competitive container port, while rival ports like Portland and San Francisco dried up. Bill #2 (Gates) catalyzed a software industry in Seattle (and beyond). Jeff (Bezos) famously drove to Seattle in his Chevy Blazer, where he pioneered e-commerce and created a million and a half jobs along the way.
Maybe the luck holds and the next big thing just shows up. It could be space, energy, robotics, biotech or something unimaginable today. Hopefully we get lucky again, but hope, as they say, is not a strategy.
So I’ll offer a catchphrase as you think about Seattle’s next act: Don’t be Cleveland.
(I want to be very clear that I mean no offense to Cleveland. The people there today are still digging out of a hole created decades ago. Let’s learn from them and not repeat the errors of their forebears.)
Tech
RRAM hasn't delivered yet, but stacked memory is being pitched to run neural networks in place
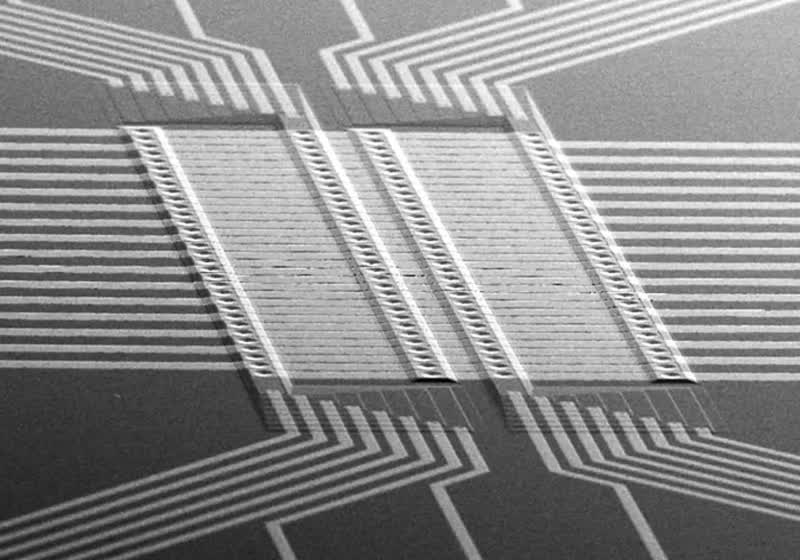
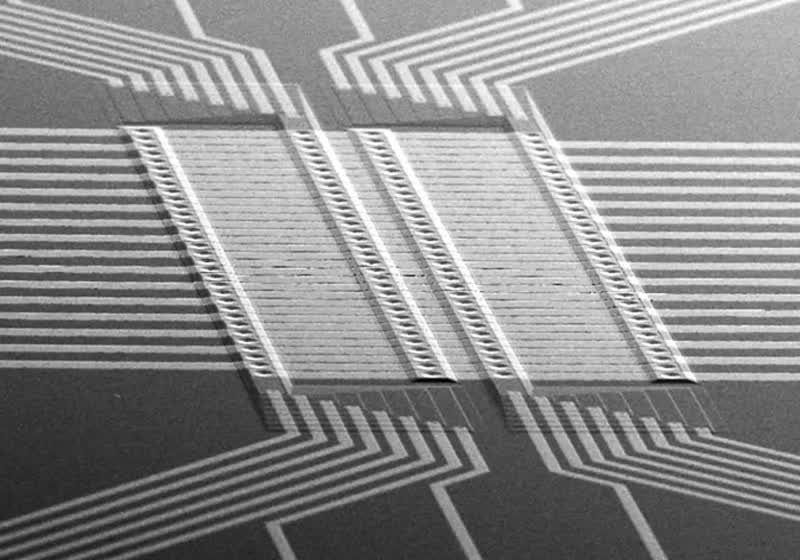
A team at the University of California, San Diego has redesigned how RRAM operates in an effort to accelerate the execution of neural network models. According to UCSD electrical engineer Duygu Kuzum, the approach could eventually enable a new class of local AI applications, assuming the technology’s remaining challenges can…
Read Entire Article
Source link
Tech
Google now helps you wipe your sensitive personal data and photos from Search
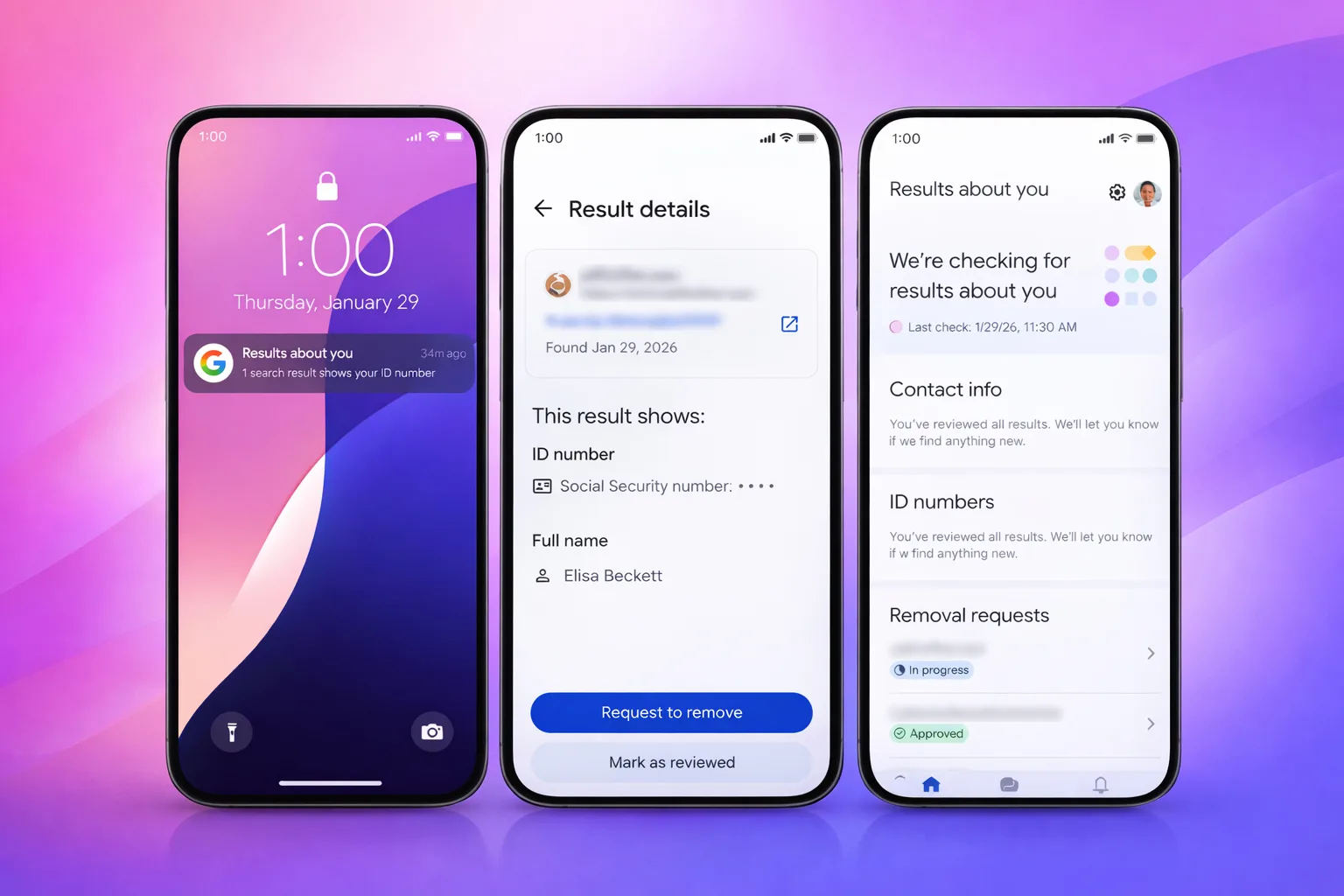
Google Search can make information easy to find, but it can also make your personal data surface in ways that feel invasive or even dangerous. This is why Google is rolling out new tools that give people more control over what shows up about them online.
The company says it is expanding its Search removal features to make it simpler to take down sensitive personal information and explicit images that never should have been public in the first place.
How to remove personal information from Search
Google’s “Results about you hub” can now help you find and remove search results that contain sensitive government-issued identification numbers. This includes things like passport numbers, driver’s license numbers, and other official ID info that could be misused if they appear online.

To use this feature, you sign in to your Google account and select ‘Results about you,’ where you can fill out the information you want to track. Google will proactively scan Search for results that match your personal information and alert you if it finds something.
From there, you can review each result and request removal directly within the tool. You can also manually submit a removal request if you come across sensitive information yourself. Google says it will review these requests and remove results that violate its policies.
How to remove explicit images from Search

Google is also simplifying the process for removing explicit images, especially those shared without consent. You can now request the removal of explicit images more easily, including submitting multiple images at once rather than filing separate requests.
Once an image is removed, Google will also offer an option to proactively filter out similar explicit images from future Search results, to prevent similar content from resurfacing.

You can now track all your removal requests in one place through the Results about you hub, with email updates to keep you informed whenever the status changes.
Google also points out that removing information from Search does not erase it from the internet altogether, but it can still go a long way in protecting your privacy.
The update also comes as Google shuts down its dark web reports, which previously alerted users when their name, phone number, or email surfaced online in a data breach.
Google says those alerts did not always help people take meaningful action, something the new removal tools are designed to address.
Tech
Microsoft releases Windows 10 KB5075912 extended security update


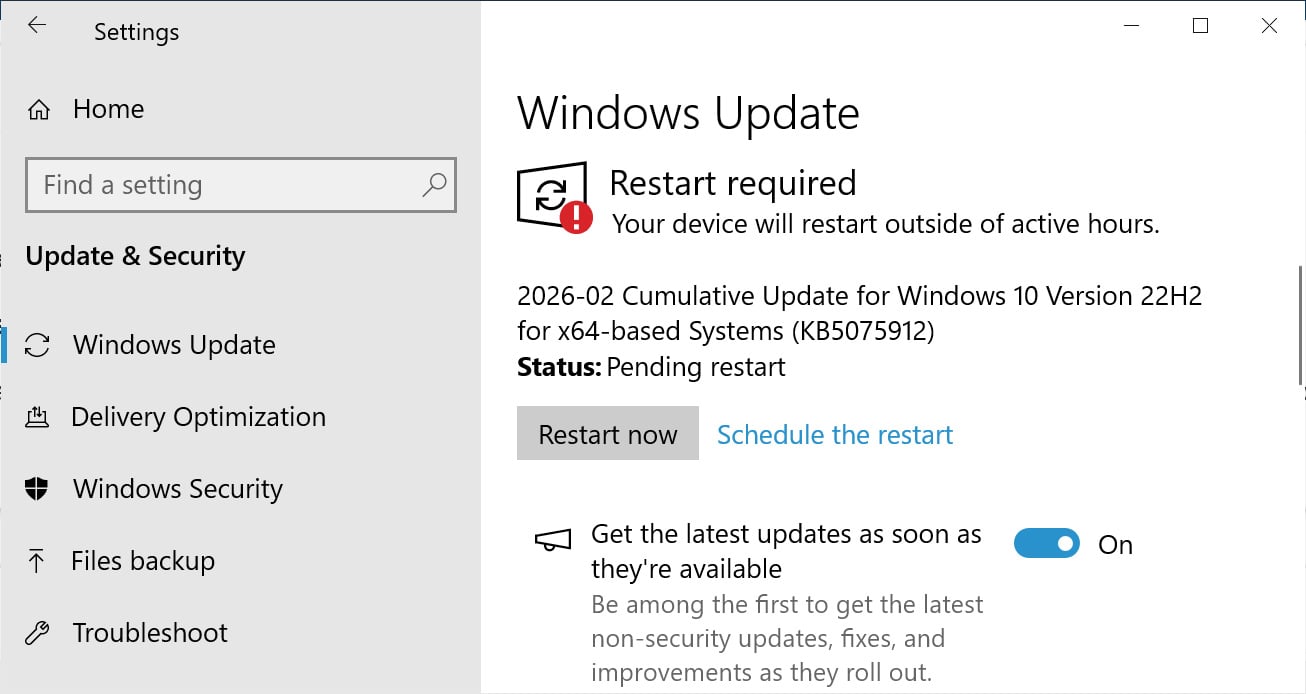
Microsoft has released the Windows 10 KB5075912 extended security update to fix February 2026 Patch Tuesday vulnerabilities, including six zero-days, and continue rolling out replacements for expiring Secure Boot certificates.
If you are running Windows 10 Enterprise LTSC or are enrolled in the ESU program, you can install this update like normal by going into Settings, clicking on Windows Update, and manually performing a ‘Check for Updates.’
Source: BleepingComputer
After installing this update, Windows 10 will be updated to build 19045.6937, and Windows 10 Enterprise LTSC 2021 will be updated to build 19044.6937.
What’s new in Windows 10 KB5075912
Microsoft is no longer releasing new features for Windows 10, and the KB5075912 update contains only security fixes and bug fixes introduced by previous security updates.
With today’s February 2026 Patch Tuesday, Microsoft has fixed 58 vulnerabilities, including six actively exploited zero-day flaws.
KB5075912 also fixes a known issue that prevented Windows 10 devices from shutting down or hibernating if System Guard Secure Launch is enabled.
The complete list of fixes is below:
- [Fonts] This update includes changes to Chinese fonts to meet GB18030-2022A compliance.
- [OS Security (known issue)] Fixed: After installing the Windows security update released on or after January 13, 2026, some Secure Launch-capable PCs with Virtual Secure Mode (VSM) enabled are unable to shut down or enter hibernation. Instead, the device restarts.
- [Folders] Fixed: This update fixes an issue that affects folder renaming with desktop.ini files in File Explorer. The LocalizedResourceName setting was ignored, so custom folder names did not show. Now, custom folder names appear as expected.
- [Graphics] Fixed: A stability issue affecting certain graphics processing units (GPUs) configurations.
- [Secure Boot] With this update, Windows quality updates include a broad set of targeting data that identifies devices and their ability to receive new Secure Boot certificates. Devices will receive the new certificates only after they show sufficient successful update signals, which helps ensure a safe and phased rollout.
Since June 2025, Microsoft has warned that multiple Windows Secure Boot certificates from 2011 are expiring in June 2026, and warned that if they are not updated, it would breach Secure Boot protections.
These certificates are used to validate Windows boot components, third-party bootloaders, and Secure Boot revocation updates, and if expired, could allow threat actors to bypass security protections.
As part of today’s update, Microsoft continues to roll out the new Secure Boot certificates to targeted systems, with updates to additional systems being installed as the targeting scope expands.
Microsoft states that there are no known issues with this update.
Tech
New Linux botnet SSHStalker uses old-school IRC for C2 comms


A newly documented Linux botnet named SSHStalker is using the IRC (Internet Relay Chat) communication protocol for command-and-control (C2) operations.
The protocol was invented in 1988, and its adoption peaked during the 1990s, becoming the main text-based instant messaging solution for group and private communication.
Technical communities still appreciate it for its implementation simplicity, interoperability, low bandwidth requirements, and no need for a GUI.
The SSHStalker botnet relies on classic IRC mechanics such as multiple C-based bots and multi-server/channel redundancy instead of modern C2 frameworks, prioritizing resilience, scale, and low cost over stealth and technical novelty.
According to researchers at threat intelligence company Flare, this approach extends to other characteristics of SSHStalker’s operation, like using noisy SSH scans, one-minute cron jobs, and a large back-catalog of 15-year old CVEs.
“What we actually found was a loud, stitched-together botnet kit that mixes old-school IRC control, compiling binaries on hosts, mass SSH compromise, and cron-based persistence. In other words scale-first operation that favors reliability over stealth,” Flare says.
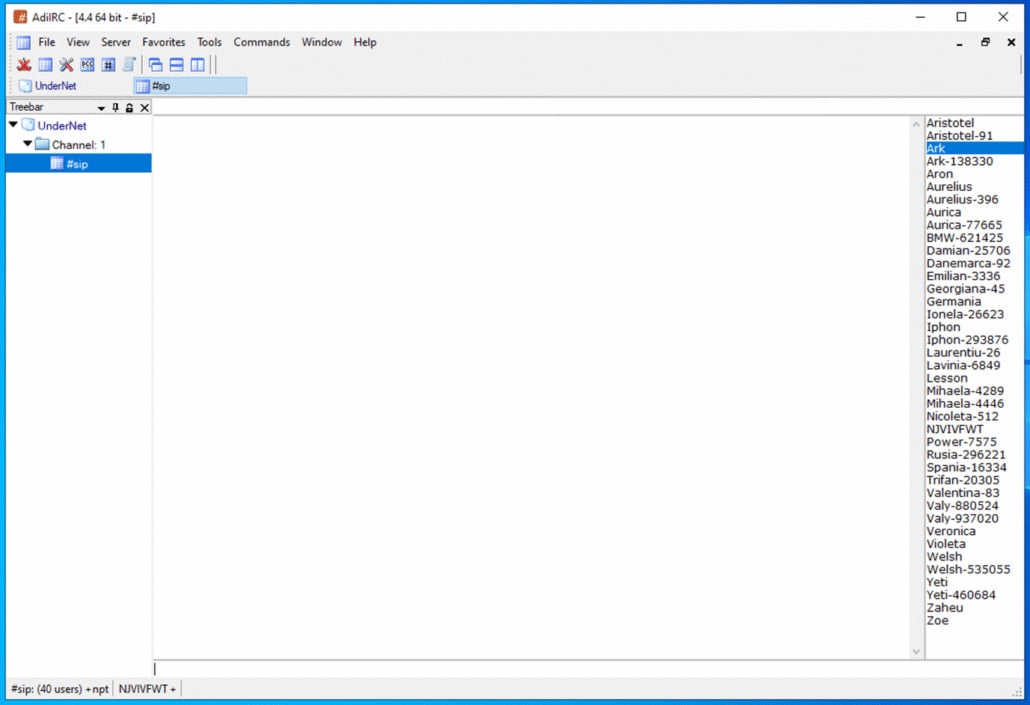
Source: Flare
SSHStalker achieves initial access through automated SSH scanning and brute forcing, using a Go binary that masquerades as the popular open-source network discovery utility nmap.
Compromised hosts are then used to scan for additional SSH targets, which resembles a worm-like propagation mechanism for the botnet.
Flare found a file with results from nearly 7,000 bot scans, all from January, and focused mostly on cloud hosting providers in Oracle Cloud infrastructure.
Once SSHStalker infects a host, it downloads the GCC tool for compiling payloads on the victim device for better portability and evasion.
The first payloads are C-based IRC bots with hard-coded C2 servers and channels, which enroll the new victim in the botnet’s IRC infrastructure.
Next, the malware fetches archives named GS and bootbou, which contain bot variants for orchestration and execution sequencing.
Persistence is achieved via cron jobs that run every 60 seconds, invoking a watchdog-style update mechanism that checks whether the main bot process is running and relaunches it if it is terminated.
The botnet also contains exploits for 16 CVEs targeting Linux kernel versions from the 2009-2010 era. This is used to escalate privileges after the earlier brute-forcing step grants access to a low-privileged user.
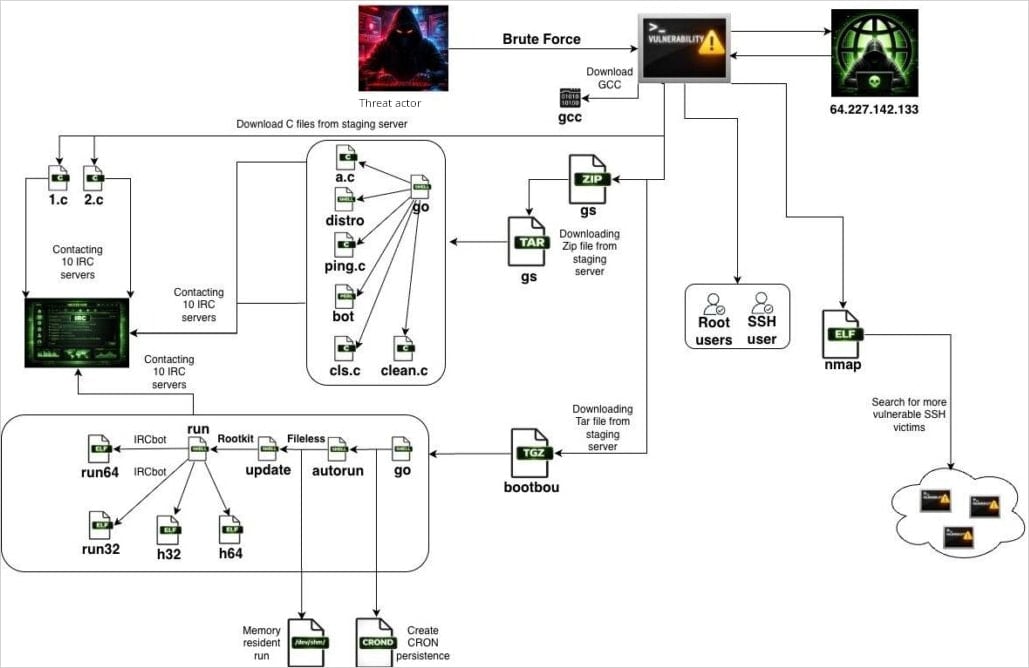
Source: Flare
Regarding monetization, Flare noticed that the botnet performs AWS key harvesting and website scanning. It also includes cryptomining kits such as the high-performance Ethereum miner PhoenixMiner.
Distributed denial-of-service (DDoS) capabilities are also present, though the researchers noted they have not yet observed any such attacks. In fact, SSHStalker’s bots currently just connect to the C2 and then enter an idle state, suggesting testing or access hoarding for now.
Flare has not attributed SSHStalker to a particular threat group, though it noted similarities with the Outlaw/Maxlas botnet ecosystem and various Romanian indicators.
The threat intelligence company suggests placing monitoring solutions for compiler installation and execution on production servers, and alerts for IRC-style outbound connections. Cron jobs with short execution cycles from unusual paths are also big red flags.
Mitigation recommendations include disabling SSH password authentication, removing compilers from production images, enforcing egress filtering, and restricting execution from ‘/dev/shm.’
Tech
Lost Soviet Moon Lander May Have Been Found

An anonymous reader shares a report: In 1966, a beach-ball-size robot bounced across the moon. Once it rolled to a stop, its four petal-like covers opened, exposing a camera that sent back the first picture taken on the surface of another world. This was Luna 9, the Soviet lander that was the earliest spacecraft to safely touchdown on the moon. While it paved the way toward interplanetary exploration, Luna 9’s precise whereabouts have remained a mystery ever since.
That may soon change. Two research teams think they might have tracked down the long-lost remains of Luna 9. But there’s a catch: The teams do not agree on the location. “One of them is wrong,” said Anatoly Zak, a space journalist and author who runs RussianSpaceWeb.com and reported on the story last week. The dueling finds highlight a strange fact of the early moon race: The precise resting places of a number of spacecraft that crashed or landed on the moon in the run up to NASA’s Apollo missions are lost to obscurity. A newer generation of spacecraft may at last resolve these mysteries.
Luna 9 launched to the moon on Jan. 31, 1966. While a number of spacecraft had crashed into the lunar surface at that stage of the moon race, it was among the earliest to try what rocket engineers call a soft landing. Its core unit, a spherical suite of scientific instruments, was about two feet across. That size makes it difficult to spot from orbit. “Luna 9 is a very, very small vehicle,” said Mark Robinson, a geologist at the company Intuitive Machines, which has twice landed spacecraft on the moon.
Tech
Rivian R2 Prototype First Drive Reviews Point to a Quick, Capable, and Ready to Play Electric SUV


Rivian’s R2 Prototype has hit road with early reviews, and it’s a capable electric SUV that truly delivers on the adventure promise without breaking the bank like its larger siblings do. The test rides were place on California highways, curvy back roads, and rocky off-road trails near Rivian’s Irvine headquarters. Most reviewers agree that the R2 retains the adventurous spirit of the larger R1 models while also making it more fun and approachable for daily driving.
The power comes from two motors, and this all-wheel drive configuration generates a 656 horsepower and 609 pound-feet of torque. It accelerates from 0 to 60 mph in around 3.6 seconds and feels robust even at highway speeds. In normal mode, the R2 runs largely on rear-wheel drive for improved fuel efficiency, but when necessary, it uses the front motor. Sport mode engages full all-wheel drive for a faster reaction.
Sale
VOLPAM Electric Scooter Adult, 19 MPH & 15 Miles Range, 350W Motor, 8.5″ Solid Tires, Lightwight Foldable…
- ✅【 Powerful Performance】Equipped with a 350W brushless motor, this adult electric scooter reaches 19MPH and handles 15° inclines with ease…
- ✅【Long-Lasting Battery】This e scooter has 19 miles max long range on a single 4-5 hours fast charge, making it ideal for everyday commutes…
- ✅ 【Safety First】Scooter stay protected with a drum brake + EABS electronic brake system for quick, stable stopping. The bright LED headlight…
The R2 handles quite well and stays grounded in corners. The steering feels natural and connected, with plenty of feedback that increases as you request more. Body control is outstanding, especially given the high ground clearance and all-terrain tyres with tall sidewalls. Roll remains well under control, and the chassis responds quickly and without drama. The R2 feels lighter on its feet because to its unibody structure, lower weight (about 4,850 to 5,000 pounds), and lower center of gravity. When cruising, the ride is nice, but when you push harder, it tightens up. Steel coil springs and semi-active dampers handle uneven roads with ease, providing an excellent balance between pavement and dirt.
Off-road performance stands up well on the trails it was tested on, with 9.6 inches of ground clearance and angles that allow you to tackle tough terrain with confidence. The long-travel suspension articulates well, and torque vectoring maintains traction without the use of typical locking differentials. When the wheels begin to spin, the brakes come into action, but there is some initial slip before they fully intervene.
Inside, the room is surprisingly generous for a tiny SUV. Tall adults may comfortably sit into the back seats, which provide 40.4 inches of legroom and headroom. The inside remains clutter-free, featuring a large central touchscreen and a smaller driver display. The haptic steering wheel on the column controls climate, drive modes, and other settings via rolling, tilting, and pushing actions, and the feedback is satisfactory, but they are currently working on adjusting the prototypes. There is plenty of storage space, ranging from dual gloveboxes to a flat-folding rear section that can accommodate a fitted mattress for overnight use. The low beltline and upright windows provide excellent visibility.
The EPA cycle shows a range of more than 300 miles, thanks to a compact battery pack and a well-designed interior. Filling up is also much faster than you’d think, with the R2 going from 10 to 80 percent in less than half an hour at a fast charging station, and with a native NACS port, it’s virtually ready to go at any Tesla Supercharger.
The price starts about $45,000, with dual-motor variants costing $50,000 or $55,000, depending on how specced out you want to get. The truth is, that puts the R2 in a really good position in the market; it’s like a true alternative to the more mainstream electric crossovers (Tesla Model Y), but with one significant bonus: you can actually take it off the beaten track and get a real rush of performance.
Tech
North Korean hackers use new macOS malware in crypto-theft attacks


North Korean hackers are running tailored campaigns using AI-generated video and the ClickFix technique to deliver malware for macOS and Windows to targets in the cryptocurrency sector.
The threat actor’s goal is financial, as suggested by the role of the tools used in an attack on a fintech company investigated by Google’s Mandiant researchers.
During the response engagement, the researchers found seven distinct macOS malware families and attributed the attack to UNC1069, a threat group they’ve been tracking since 2018.
Infection chain
The attack had a strong social engineering component as the victim was contacted over the Telegram messaging service from a compromised account of an executive at a cryptocurrency company.
After building a rapport, the hackers shared a Calendly link that took the victim to a spoofed Zoom meeting page on the attacker’s infrastructure.
According to the target, the hackers showed a deepfake video of a CEO at another cryptocurrency company.
“Once in the ‘meeting,’ the fake video call facilitated a ruse that gave the impression to the end user that they were experiencing audio issues,” Mandiant researchers say.
Under this pretext, the attacker instructed the victim to troubleshoot the problems using commands present on a webpage. Mandiant found commands on the page for both Windows and macOS that would start the infection chain.
Huntress researchers documented a similar attack method in mid-2025 and attributed it to the BlueNoroff group, another North Korean adversary also known as Sapphire Sleet and TA44, that targeted macOS systems using a different set of payloads.
macOS malware
Mandiant researcher found evidence of AppleScript execution once the infection chain started, but could not recover the contents of the payload, followed by deploying a malicious Mach-O binary. In the next stage, the attacker executed seven distinct malware families:
- WAVESHAPER – C++ backdoor that runs as a background daemon, collects host system information, communicates with C2 over HTTP/HTTPS using curl, and downloads and executes follow-on payloads.
- HYPERCALL – Golang-based downloader that reads an RC4-encrypted configuration file, connects to C2 over WebSockets on TCP 443, downloads malicious dynamic libraries, and reflectively loads them into memory.
- HIDDENCALL – Golang-based backdoor reflectively injected by HYPERCALL that provides hands-on keyboard access, supports command execution and file operations, and deploys additional malware.
- SILENCELIFT – Minimal C/C++ backdoor that beacons host information and lock screen status to a hard-coded C2 server and can interrupt Telegram communications when executed with root privileges.
- DEEPBREATH – Swift-based data miner deployed via HIDDENCALL that bypasses macOS TCC protections by modifying the TCC database to gain broad filesystem access and steals keychain credentials, browser data, Telegram data, and Apple Notes data.
- SUGARLOADER – C++ downloader that uses an RC4-encrypted configuration to retrieve next-stage payloads and was made persistent via a manually created launch daemon.
- CHROMEPUSH – C++ browser data miner deployed by SUGARLOADER that installs as a Chromium native messaging host masquerading as a Google Docs Offline extension and collects keystrokes, credentials, cookies, and optionally screenshots.
.jpg)
Source: Mandiant
Of the malware found, SUGARLOADER has the most detections on the VirusTotal scanning platform, followed by WAVESHAPER, which is flagged by just two products. The rest are not present in the platform’s malware database.
Mandiant says that SILENCELIFT, DEEPBREATH, and CHROMEPUSH represent a new set of tooling for the threat actor.
The researchers describe as unusual the volume of malware deployed on a host against a single individual.
This confirms a targeted attack focused on collecting as much data as possible for two reasons: “cryptocurrency theft and fueling future social engineering campaigns by leveraging victim’s identity and data,” Mandiant says.
Since 2018, UNC1069 has demonstrated its ability to evolve by adopting new techniques and tools. In 2023, the bad actor switched to targets in the Web3 industry (centralized exchanges, developers, venture capital funds).
Last year, the threat actor changed its target to financial services and the cryptocurrency industry in verticals such as payments, brokerage, and wallet infrastructure.
Tech
Hubble’s Sharpest Look Yet at a Star’s Final Act in the Egg Nebula
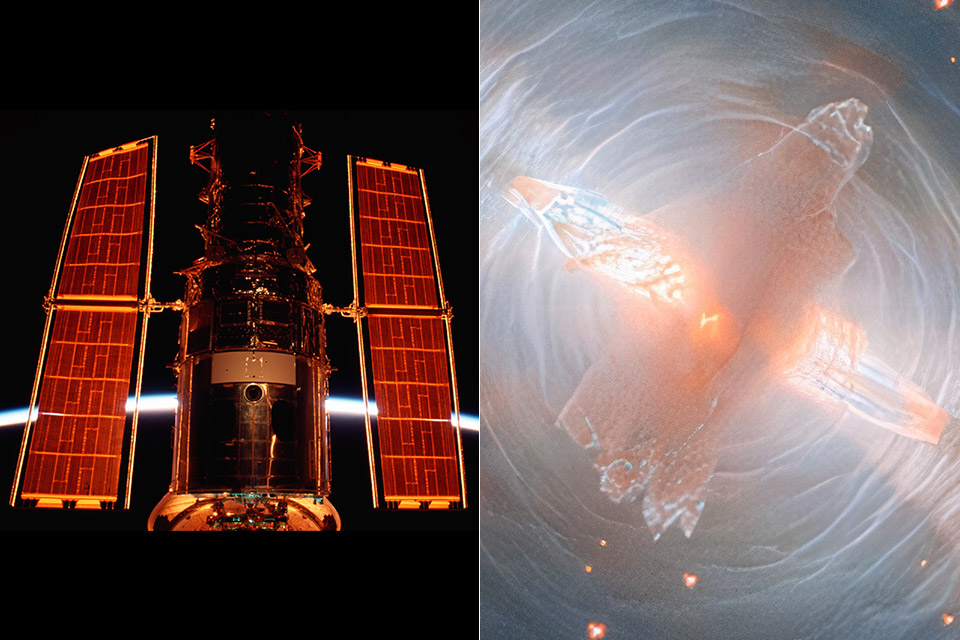
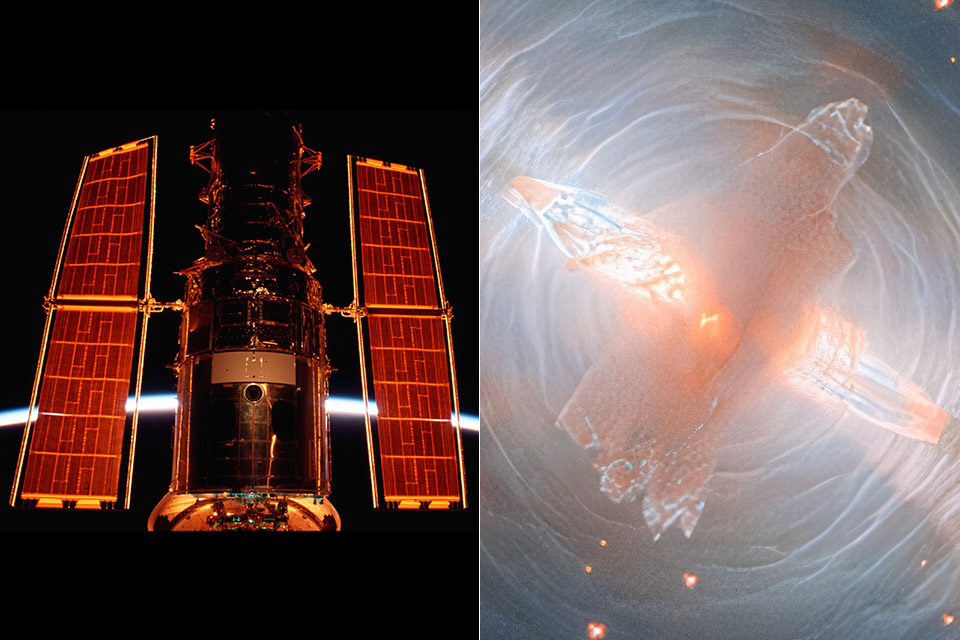
A star almost identical to our sun is nearing the end of its life in the Cygnus constellation, about 1000 light years away. Astronomers call this spectacle the Egg Nebula, or CRL 2688 for short. Hubble’s most recent image provides a magnificent view of this particular object in unprecedented detail, thanks to the combination of new data and previously captured images. What we get is a stunning display of light cutting through the dust.
A star almost identical to our sun is nearing the end of its life in the Cygnus constellation, about 1000 light years away. Astronomers call this spectacle the Egg Nebula, or CRL 2688 for short. Hubble’s most recent image provides a magnificent view of this particular object in unprecedented detail, thanks to the combination of new data and previously captured photographs. What we get is a stunning display of light cutting through the dust.
NASA Lunar Telescope for Kids – 90x Magnification, Includes Two Eyepieces, Tabletop Tripod, and Finder…
- INSPIRE CURIOSITY – The NASA Lunar Telescope allows your child to see the moon in incredible detail; the perfect gift for girls and boys interested…
- HIGH-QUALITY OPTICAL GLASS AND FINDER SCOPE – This easy-to-use telescope comes with a finder scope, low power, and high-power eyepieces; when used…
- TABLETOP TRIPOD & SMOOTH MOUNT SYSTEM – Use the included tripod to steady your Lunar Telescope for optimal viewing, with a smooth mounting system…
The core star is hidden deep in the center, enveloped by a thick cloud of gas and dust that allows very little light to pass through. What does pass through is compressed into two narrow beams of light that sweep outward, revealing the fast-moving clouds of material being ejected from the star. Those clouds glow orange in infrared, adding some color to the image. You can also observe faster-moving clouds of heated molecular hydrogen that light brightly in the infrared, adding depth to the scene.
Over the previous 5000 years, the star has lost its outer layers in large concentric rings of gas. These rings are made up of tiny arcs of gas that accumulate every few hundred years. Now, these rings reflect the star’s light in a fashion that resembles ripples on water – and the dust produced by these outbursts is what shapes the nebula that bears its name, since the dense core is like the yolk of an egg wrapped up in darker, dustier layers.

This is only transient; it will only last a few thousand years. The star has depleted all of its hydrogen and helium fuel, and what remains of its outer layers are floating away, while the center is becoming increasingly hot. Eventually, that center will cause the surrounding gas to glow, similar to the Helix Nebula or Butterfly Nebula. As of now, the Egg Nebula is in its pre-planetary phase, a brief period before winds and radiation begin to obscure the picture.
Hubble first observed the Egg Nebula in 1997, when a picture revealed the hidden light source. In 2003, we were able to get a full picture of the ripple patterns surrounding the nebula, and in 2012, we got an even closer look at the central cloud and outflows. Today’s image combines all of that data with some new frames to provide the sharpest look yet, courtesy of the Wide Field Camera 3.
Tech
MoFi Electronics Introduces UltraPhono Pro: More Affordable High-End MM/MC Phono Preamp

Vinyl isn’t having a moment anymore, it’s entrenched. Turntables are selling, cartridges are backordered, and phono preamps are once again a real battleground instead of an afterthought. With the $2,495 UltraPhono Pro, MoFi Electronics finally fills a very obvious gap in its lineup by bringing much of the sonic DNA of its flagship MasterPhono down to a price point where the fight actually is.
Designed by Peter Madnick and built around the same ultra-low-noise circuit concepts and parts philosophy that made the MasterPhono a serious contender at the top end, the UltraPhono Pro strips away the excess and focuses on what matters: clean gain, flexibility for MM and MC cartridges, and musical accuracy.
Just as importantly, it gives MoFi a credible sub-$2,500 answer to established heavyweights like Pro-Ject, EAR, E.A.T., MOON by Simaudio, Rega, and Musical Fidelity; a segment where serious vinyl listeners actually shop. In short, this is MoFi admitting the obvious: the market below its halo gear is thriving, and now they’re properly in the game.

From MasterPhono to UltraPhono Pro: Flagship Design, Scaled for the Real World
Designed by veteran engineer Peter Madnick, the MoFi Electronics MasterPhono was MoFi’s no-holds-barred statement piece: a fully discrete, all-analog phono preamplifier built to handle literally any MM or MC cartridge on the planet, including ultra-low-impedance moving coils via its current-input architecture. Its dual-chassis design isolates the power supply from the audio circuits to keep noise vanishingly low, while cascaded voltage regulation, passive RIAA with ultra-tight tolerances, and fully balanced DC-coupled circuitry deliver reference-grade accuracy (±0.05 dB RIAA) and serious signal-to-noise performance.
Add extensive front-panel configurability, multiple gain and loading options, balanced and single-ended I/O, metering, remote control, and firmware upgradability, and the $5,000 MasterPhono firmly established MoFi as a serious electronics brand—not just a turntable and cartridge company.
The new MoFi Electronics UltraPhono Pro is a clear and deliberate trickle-down from the MasterPhono’s design philosophy. By stripping away the dual-chassis construction, extreme configurability, and flagship-level excess, MoFi delivers a far more approachable phono stage, at roughly fifty percent less cost, without abandoning the engineering fundamentals that made the MasterPhono credible in the first place. The UltraPhono Pro keeps the focus where it belongs: ultra-low noise, fully discrete analog circuitry, and cartridge flexibility that actually matters to real-world vinyl listeners.

Despite its streamlined approach, the UltraPhono Pro is anything but entry-level. It delivers up to 71 dB of gain, maintains a wide and linear frequency response from 10 Hz to 50 kHz (±0.2 dB), and achieves exceptionally accurate RIAA equalization rated at ±0.05 dB. Noise performance is equally impressive, allowing low-output moving-coil cartridges to play against a quiet, stable background with excellent dynamic contrast.
User-facing features are practical and thoughtfully implemented. Front-panel controls include mono mode, mute, a subsonic filter, and dimmable faceplate illumination. Cartridge matching is straightforward and flexible, with multiple loading options for moving-coil cartridges and selectable gain settings that support both single-ended and balanced system integration.
Key Features
- Single-input architecture derived directly from the MasterPhono
- Fully discrete J-FET and MOSFET input and output stages
- Fully balanced, DC-coupled, servo-controlled signal path from the high-pass filter to the outputs
- Passive RIAA equalization with zero global feedback
- Seven-stage regulated, fully balanced power supply
- Five selectable resistive loading options via front-panel–controlled, hermetically sealed gold-on-gold relays: 100, 300, 500, 1k, and 47k ohms
- Gain settings of 40 dB, 52 dB, and 65 dB (plus +6 dB via XLR outputs)
- Ultra-low-noise design using premium-grade electronic components
- Critical resistors specified at 0.1 percent or 0.5 percent tolerance
- Passive RIAA network using polypropylene film/foil capacitors matched to better than 1 percent
- Thermally coupled critical components to minimize performance drift with temperature changes
- Maximum signal-to-noise ratio (A-weighted): 93 dB (MM) / 85 dB (MC)

Comparison
| UltraPhono Pro | MasterPhono | |
| MSRP | $2,495 | $5,995 |
| Inputs | RCA jack, voltage mode, single-ended | Current mode & Voltage mode, balanced and unbalanced |
| 100 Ohms, 300 Ohms, 500 Ohms, 1k Ohms, 47k Ohms | 15 Ohms, 30 Ohms, 50 Ohms, 75 Ohms, 100 Ohms, 500 Ohms, 1K Ohms, 10K Ohms, 47K Ohms+150pF, & Option | |
| Gain | RCA output: 40db, 52db, 65db Balanced output: 46db, 58db, 71db |
(MM) 40db, (MM) 50db, (MC) 60db, (MC) 70db |
| Output Impedance (Balanced) | 230 Ohms | 230 Ohms |
| Output Impedance (Unbalanced) | 115 Ohms | 115 Ohms |
| Maximum Output | 1% THD, 10 Volts RMS | 1% THD, 10 Volts RMS |
| THD | 110mV@1kHz 40db gain: 0.005% A-Weighted | 5mV@1KHZ MM low: < 0.01% A-Weighted |
| 10mV@1kHz 65db gain: 0.005% A-Weighted | 5mV@1KHZ MM high: < 0.01% A-Weighted | |
| 1mV@1kHz 40db gain: 0.010% A-Weighted | 0.5mV@1KHZ MC low: < 0.005% A-Weighted | |
| 1mV@1kHz 65db gain: 0.013% A-Weighted | 0.5mV@1KHZ MC high: < 0.005% A-Weighted | |
| RIAA Accuracy | +/- 0.05db | +/- 0.1db using passive R-C technology |
| Frequency Response | 10Hz – 50kHz +/- 0.20db | 10Hz – 50KHz +/- 0.20db no filter-3.5db @ 10Hz filter ON |
| Dimensions (WxHxD) | 17” x 2.5” x 11.375” (43.2 x 6.4 x 28.8 cm) |
17” x 3” x 17” (43.2 x 7.6 x 43.2 cm) |
| Weight | 7 lbs (3.2 kg) | 15 lbs (6.8 kg) |
| AC Mains | 100VAC – 260VAC, auto switching | 100VAC – 260VAC, auto switching |
In short, the UltraPhono Pro doesn’t try to replace the MasterPhono, it translates its core engineering into a price and feature set that makes sense for the crowded, highly competitive mid-to-upper phono preamp market.

The Bottom Line
The MoFi Electronics UltraPhono Pro delivers genuine high-end phono design with fully discrete circuitry, very low noise, accurate RIAA, and balanced operation at a price where serious vinyl listeners actually shop. It’s built for MM and MC users who want flexibility and precision without paying for flagship excess, and it stands out by sounding like a scaled-down reference component rather than a dressed-up midrange box.
Where to buy: $2,495 at Music Direct | SkyFi Audio
Related Reading:
Tech
Which is better for you in 2026?
Buying a smartphone in 2026 is a far cry from where we were 10 years ago, with less obvious reasons to go with either iOS or Android – but the choice remains one of the most significant you’ll make in your digital life.
Whether you’re looking at the iPhone 17 or an Android flagship like the Samsung Galaxy S25 Ultra, the gap in hardware has shrunk massively – but the way you interact with the phones is still completely different.
Here, we explain the fundamental differences between Android and iOS in 2026 to help you decide which is better for your needs.
Market share
If you look at the global market share, Android continues to dominate the vast majority of the planet with a massive 72% using the platform. Apple’s iOS, on the other hand, only accounts for a 28% share.
Android’s dominance is driven mainly by the sheer variety of hardware available at pretty much every price point, from budget-friendly blowers in emerging markets to ultra-premium foldables. That said, while iOS’ 28% share may sound small in comparison, it’s worth noting that it dominates in more premium markets like the UK and US.
That might not sound like something you should care about, but if you want to use the same platform-exclusive features as your friends – namely things like iMessage on iOS – you’ll want to make sure you make the right choice.
Updates
A few years ago, Apple would’ve had a massive win on its hands with its iOS update system – but the Android competition has come along leaps and bounds more recently.
Apple’s approach to software updates is still the stronger of the two, with Apple dropping new versions of iOS on all supported devices on the same day, ensuring that even three- or four-year-old iPhones get the latest software updates as soon as they’re available.


Android makers have made big strides in this department, with the likes of Samsung, Google, Honor and Motorola now offering up to seven years of support, but the rollout of this software is much more fragmented. Sure, you might get the Android 17 update, but it won’t be as soon as it’s released, and it might be available for other phones from the same brand first.
Also, that’s pretty much exclusive to flagships – if you buy a mid-range or budget device from a brand like Xiaomi, you’re at the mercy of a more limited software promise. This means that while the hardware might last, the software experience can feel dated much faster on Android than on iOS.
Software experience
Using an iPhone in 2026 is a largely smooth, polished experience with impressive visuals thanks to the Liquid Glass UI introduced with iOS 26 in late 2025.
Apple’s interface feels like a premium, more curated experience where the software just kind of works in the background without much setup or intervention needed, but it also means you’re locked into Apple’s infamous walled garden – even if those towering walls are slowly beginning to crumble.


Android, on the other hand, is designed for those who want greater control and customisation in their smartphone.
From the deep customisation available on Android skins to the ability to swap out your entire home screen launcher or icon packs, Android feels more like a tool that adapts to your needs – though that does depend on the Android you’re using, as different Android skins offer different levels of visual customisation.
You do need more time and patience, especially if you get into the nitty-gritty of Android customisation, but it’s usually a well-rewarded task.
Apps
The days of “iOS gets it first” are largely over for major releases, but the App Store still feels like the more polished storefront of the two – though with Apple set to introduce more ads to the App Store experience, that could soon change.
That said, Apple’s strict app vetting process and the limited number of screen sizes to accommodate generally result in higher-quality UI and better optimisation. After all, it’s much easier for devs to polish an app for five iPhones than for five hundred different models of Android.


Google Play offers more freedom than Apple’s App Store, offering powerful system-level utilities, retro game emulators and niche productivity tools that Apple simply wouldn’t allow on its platform. It also features most, if not all, major apps available on iOS, though there are still a few iOS exclusives floating around – especially when it comes to big-screen tablet apps.
For the average user, the difference between the two storefronts is negligible, but for power users who want to use their phone as a genuine pocket computer with super-niche apps, Android remains the better choice.
Security and privacy
It feels like Apple’s entire brand is centred around privacy, and in 2026, features like App Tracking Transparency and Advanced Data Protection remain industry-leading.
That’s because Apple produces not only the hardware but every aspect of the software experience, from custom silicon to encrypted iCloud backups, it can offer a level of security that’s difficult to replicate on the Android side of things.


Android’s security model is more fragmented in comparison. While Google has hardened the OS significantly and introduced a range of privacy-focused features, the “open” nature of Android places greater responsibility on users to avoid installing dodgy apps from random websites that might contain malware.
Specific manufacturers offer deeper security features, with the likes of Samsung’s Knox and Motorola’s ThinkShield for Mobile featuring more robust features to protect your data from hacks, but it’s not consistent among all Android manufacturers.
AI
Artificial Intelligence, or AI, is the buzzword in the smartphone world at the moment, with pretty much every smartphone manufacturer seemingly cramming as many AI features into their smartphones as possible. That said, the playing field is far from level.
While Apple has marketed Apple Intelligence as a seamless, integrated experience, it’s clear that Android brands have a massive lead in both capability and accuracy. The fact that Apple is using Gemini to power its long-awaited (and delayed) redesigned Siri experience should speak volumes to this fact.


Whether it’s the more sophisticated generative object removal offered by Samsung’s Galaxy AI or the multi-modal on-device processing from the latest Pixel phones, Android AI tools generally feel more robust and less prone to hallucinations that still plague Apple’s efforts.
That said, much of this power is becoming platform-agnostic. Many popular AI tools, including the full suite of Gemini features, are available as apps on both iOS and Android, meaning you aren’t necessarily locked out of top-tier AI just because you chose an iPhone.
The real difference is how companies handle the data; Apple continues to lean heavily on Private Cloud Compute to handle cloud-based AI processing of sensitive data, while Google and other Android manufacturers offer a mix of on-device and cloud-based processing depending on what it needs.
Verdict
When it comes to the all-important decision of choosing between iOS and Android, there’s no wrong choice, only a choice of priorities.
If you want an easy-to-use phone with a wide variety of high-quality apps that works well with other Apple gear and offers the most polished experience, the iPhone remains the best pick.
That said, if you want the best AI tech and the freedom to make your phone look and act exactly how you want, with niche system-level apps and extensive customisation, Android is your best bet.
-

 Tech7 days ago
Tech7 days agoWikipedia volunteers spent years cataloging AI tells. Now there’s a plugin to avoid them.
-

 Politics2 days ago
Politics2 days agoWhy Israel is blocking foreign journalists from entering
-

 NewsBeat1 day ago
NewsBeat1 day agoMia Brookes misses out on Winter Olympics medal in snowboard big air
-

 Sports4 days ago
Sports4 days agoJD Vance booed as Team USA enters Winter Olympics opening ceremony
-

 Tech4 days ago
Tech4 days agoFirst multi-coronavirus vaccine enters human testing, built on UW Medicine technology
-
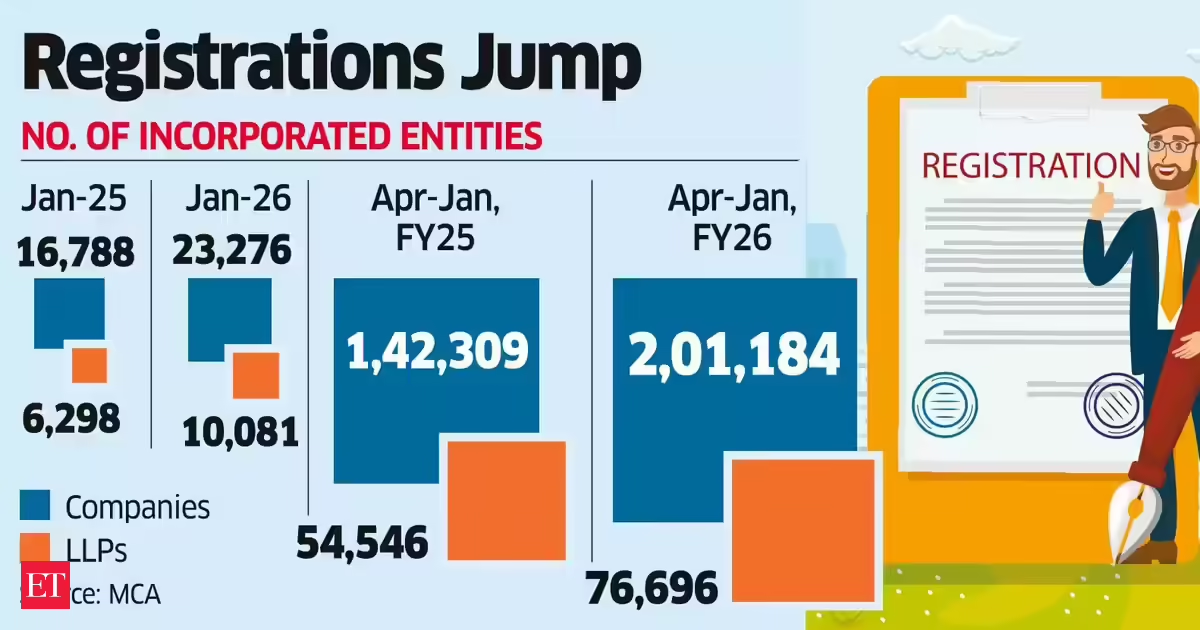
 Business2 days ago
Business2 days agoLLP registrations cross 10,000 mark for first time in Jan
-

 NewsBeat2 days ago
NewsBeat2 days agoWinter Olympics 2026: Team GB’s Mia Brookes through to snowboard big air final, and curling pair beat Italy
-

 Sports2 days ago
Sports2 days agoBenjamin Karl strips clothes celebrating snowboard gold medal at Olympics
-
Sports3 days ago
Former Viking Enters Hall of Fame
-

 Politics2 days ago
Politics2 days agoThe Health Dangers Of Browning Your Food
-
Sports5 days ago
New and Huge Defender Enter Vikings’ Mock Draft Orbit
-

 Business3 days ago
Business3 days agoJulius Baer CEO calls for Swiss public register of rogue bankers to protect reputation
-

 NewsBeat4 days ago
NewsBeat4 days agoSavannah Guthrie’s mother’s blood was found on porch of home, police confirm as search enters sixth day: Live
-

 Business5 days ago
Business5 days agoQuiz enters administration for third time
-

 Crypto World7 hours ago
Crypto World7 hours agoBlockchain.com wins UK registration nearly four years after abandoning FCA process
-
 Crypto World16 hours ago
Crypto World16 hours agoU.S. BTC ETFs register back-to-back inflows for first time in a month
-

 NewsBeat2 days ago
NewsBeat2 days agoResidents say city high street with ‘boarded up’ shops ‘could be better’
-
Sports1 day ago
Kirk Cousins Officially Enters the Vikings’ Offseason Puzzle
-
 Crypto World16 hours ago
Crypto World16 hours agoEthereum Enters Capitulation Zone as MVRV Turns Negative: Bottom Near?
-

 NewsBeat6 days ago
NewsBeat6 days agoStill time to enter Bolton News’ Best Hairdresser 2026 competition














