Crypto World
5 Proven Use Cases That Drive Adoption

If you’re a founder, product owner, or growth lead building a Web3 platform, you’ve probably felt this pressure already: everyone says you need a token, but nobody tells you how to make that token useful after launch. The truth is, most projects don’t fail at fundraising or smart contract deployment; they fail at adoption. Users join, speculate, and disappear because the token isn’t connected to real product value. That’s exactly why utility token use cases matter. When designed correctly, they turn tokenomics into a product engine that drives retention, rewards real engagement, unlocks premium access, and creates demand that grows with your platform.
In this guide, we’re breaking down 5 proven utility token use cases for startups, platforms, and Web3 brands, with practical insights you can actually apply before you commit to token development. No hype, no generic theory, just the real patterns that help tokens earn usage, not just attention.
5 Utility Token Use Cases That Turn Tokenomics Into Product Adoption
So what does real utility look like in practice? These are the 5 proven use cases that consistently turn tokenomics into product adoption.
Use Case #1: Token-Gated Access (Membership, Features, Premium Zones)
Best for:
- Communities
- Creator brands
- SaaS-like Web3 products
- NFT ecosystems
- Alpha groups + research platforms
- Marketplaces with premium tools
What it solves:
Most Web3 products struggle with retention. Users join, explore, and leave because there is no sticky reason to stay. Token-gated access fixes that by making the token a key, not a coin, and the right token development services help you implement it securely across web and mobile.
How it works:
Users must hold or spend tokens to unlock:
- Premium features
- Exclusive content
- Early drops
- Gated communities
- VIP support
- Advanced analytics dashboards
- Private launches/allowlists
Why it’s proven:
This use case is simple, powerful, and easy to communicate. It also naturally creates a holding incentive without forcing artificial staking mechanics.
Where token development fits:
You’ll implement access control in your dApp (web/mobile), map it to wallet ownership, and create smart contract logic to validate token holdings or token burns/spends for entry.
Use Case #2: Rewards & Loyalty (Earn-to-Engage That Doesn’t Break Tokenomics)
Best for:
- Web3 brands
- Marketplaces
- Consumer apps
- Games
- Community-driven platforms
- Campaigns & growth loops
What it solves:
Founders want growth, but paid acquisition is expensive. Web3 users also don’t stay loyal unless the product gives them a reason. Rewards-based utility turns your token into a behavior engine, and a trusted token development company can build it with secure logic and tracking.
How it works:
Users earn tokens for actions like:
- Onboarding and referrals
- Creating content
- Providing liquidity (where applicable)
- Completing missions
- Voting or participating
- Trading volume milestones
- Reviews, feedback, or moderation
Why it’s proven:
Because it creates a measurable flywheel: Action → Reward → Engagement → Repeat action
The trap to avoid:
Over-rewarding creates sell pressure and turns your token into free money. The solution is to reward actions that produce value and tie rewards to usage, which is essential in crypto token development.
Use reward mechanisms like:
- Vesting schedules
- Dynamic reward rates
- Caps per wallet
- Reward multipliers for long-term users
- Redeem rewards for benefits (not just cash-out)
Where token development fits:
This requires on-chain token logic + off-chain tracking (events, analytics, anti-fraud) + a clean reward claim system.
Design Your Token Utility Loop With Experts
Use Case #3: Fee Discounts + Payment Utility (The “Reason to Spend” Model)
Best for:
- Exchanges
- Launchpads
- DeFi platforms
- Marketplaces
- Payment-style apps
- Services platforms
What it solves:
One of the biggest token problems is this: users don’t have a reason to spend it. Fee utility solves that immediately.
How it works:
Users get discounted fees when they pay using your token:
- Trading fees
- Listing fees
- Launchpad participation fees
- Protocol fees
- Marketplace fees
- Subscription payments
You can also allow token payments for:
- In-app purchases
- Premium plans
- Upgrades
- Service bookings
- API usage
Why it’s proven:
It’s easy to understand and directly tied to savings. It also connects token value to platform activity; if the platform grows, demand grows.
Best implementation patterns:
Pay fees in tokens = discount
Hold token = lower-tier fees
Stake token = premium fee tier (more advanced)
Where token development fits:
You’ll need token payment routing, fee logic, treasury handling, and potentially swap support (so users can pay fees even if they hold another asset).
Use Case #4: Staking for Benefits (Not Just APY)
Best for:
- Platforms with recurring usage
- DeFi ecosystems
- Gaming economies
- Launchpads
- Brands with strong community incentives
What it solves:
Staking becomes dangerous when it’s only about APY. That’s when tokens inflate, emissions spike, and long-term value collapses. But staking becomes powerful when it’s tied to real platform benefits, and the right token development services help you design it sustainably.
How it works:
Users stake tokens to unlock:
- Higher reward multipliers
- Priority access to drops
- Allocation boosts
- Governance power
- Premium support
- Higher referral commissions
- Revenue-sharing (where legally viable)
Why it’s proven:
Staking increases retention and reduces circulating supply pressure when paired with real reasons to stake.
The smarter staking approach:
Instead of “stake to earn more tokens,” shift to: stake to get more platform value.
Examples:
- Stake to unlock higher tiers
- Stake to access premium tools
- Stake to get better marketplace exposure
- Stake to reduce platform fees
Where token development fits:
This requires staking contracts, lock and unstake logic, reward rules, and a front-end dashboard that clearly shows benefits and timelines, and experienced token development services help you ship it without security gaps.
Use Case #5: Governance & Ecosystem Control (When Community Decisions Matter)
Best for:
- Protocols and DAOs
- Platforms with many stakeholders
- Ecosystems with grants, partners, builders
- Products evolving through community input
What it solves:
Centralized decisions kill community trust. But unstructured governance kills product velocity. Good governance utility creates structured decentralization.
How it works:
Token holders can vote on:
- Feature priorities
- Treasury allocations
- Grant programs
- Fee changes
- Ecosystem partnerships
- Community initiatives
Why it’s proven:
Governance increases community ownership. It also creates “skin in the game” that’s deeper than speculation, and a trusted token development company can build secure voting and proposal systems.
The mistake to avoid:
Governance should not be cosmetic. If voting doesn’t affect anything meaningful, users stop caring.
Practical governance model:
- Vote on community grants
- Vote on roadmap priorities
- Vote on fee discounts or reward campaigns
- Scale later into deeper protocol-level governance.
Where token development fits:
You’ll need voting systems, proposal frameworks, quorum logic, and secure execution pathways (multi-sig, timelocks, or DAO tooling).
Now that you’ve seen the 5 most proven utility token models, the next step is choosing the right combination based on your product type, growth goals, and user behavior.
How to Choose the Right Utility Token Use Case (Fast Decision Framework)
If you’re stuck between multiple options, use this simple filter before you move into token development.
If your product needs retention, choose:
- Token-gated access or staking for benefits
If your product needs growth, choose:
If your product needs revenue, choose:
- Fee discounts and payment utility
If your product needs community trust, choose:
The best strategy for most startups is not to use all five utilities at once. It is choosing two utility layers that reinforce each other and create repeat usage. Proven utility combinations that work:
- Access + rewards
- Fee discounts + staking tiers
- Rewards + governance
- Staking + launchpad allocations
If you want to implement these utilities the right way, partner with expert token development services.
Final Take
The strongest projects in Web3 are not winning because they launched a token. They are winning because their tokens are tied to real product outcomes like access, usage, savings, and community ownership. That is what creates repeat demand, long-term retention, and credibility in front of users and stakeholders. If you are planning token development, do not start with spreadsheets, hype cycles, or influencer timelines. Start with a utility that your users can feel inside the product from day one. That is how you avoid dead tokens and build something that scales beyond the launch.
When you are ready to execute, Antier is the partner teams choose for secure architecture, production-grade smart contracts, and utility-first design. Our token development services help you build tokens that integrate cleanly with your platform, strengthen tokenomics, and drive adoption with real use cases. Talk to Antier today and turn your token idea into a working product that users actually stick with. Book a consultation now.
Frequently Asked Questions
01. Why do most Web3 projects fail after launching their tokens?
Most Web3 projects fail not at fundraising or smart contract deployment, but at adoption, as users often leave due to the token not being connected to real product value.
02. What is a proven use case for utility tokens that enhances user retention?
Token-gated access is a proven use case that enhances user retention by requiring users to hold or spend tokens to unlock premium features, exclusive content, and other benefits.
03. How can token development services help with utility token implementation?
Token development services can help implement access control in dApps, map it to wallet ownership, and create smart contract logic to validate token holdings or token burns/spends for entry.
Crypto World
Fake Trezor, Ledger Letters Target Crypto Wallet Users

Users of crypto hardware wallets Ledger and Trezor are again reporting receiving physical letters aimed at stealing their seed recovery phrases — the latest attack on users exposed across numerous data leaks over the past six years.
Cybersecurity expert Dmitry Smilyanets was one of the first to report receiving a spurious letter from Trezor on Feb. 13, which demands users perform an “Authentication Check” by Feb. 15 or risk having their device restricted.
Smilyanets said the scam includes a hologram along with a QR code that takes users to a scam website. The letter is made to appear signed by Matěj Žák, who is described as the “Ledger CEO” (the real Matěj Žák is the CEO of Trezor).
A Ledger user reported receiving a similar letter last year in October, with the letter claiming recipients must complete mandatory “Transaction Check” procedures.

Scanning a malicious QR code for “mandatory” checks
The QR code reportedly takes the victim to a malicious website made to look like Ledger and Trezor setup pages, tricking users into entering their wallet recovery phrases.
Once entered, the recovery phrase is transmitted to the threat actor through a backend API, enabling them to import the victim’s wallet onto their own device and steal funds from it.
Related: Phishing scammers spoof Ledger’s email to send bogus data breach notice
Legitimate hardware wallet companies never ask users to share their recovery phrases through any method, including website, email, or snail mail.
Not the first time letters have been sent
Ledger and its third-party partners have suffered multiple large-scale data breaches over the past few years, resulting in leaks of customer data, including physical addresses used for postal purposes, and physical threats.
Meanwhile, Trezor flagged a security breach that exposed the contact information of nearly 66,000 customers in January 2024.
In 2021, scammers mailed counterfeit Ledger Nano hardware wallets to victims of the 2020 Ledger data breach.
Physical letters prompting victims to scan QR codes were sent in April 2025, while in May, hackers used fake Ledger Live apps to steal seed phrases and drain crypto from victims.
Ledger alerted users to the physical mail phishing scam on its website in October.
Magazine: Coinbase misses Q4 earnings, Ethereum eyes ‘V-shaped recovery’: Hodler’s Digest
Crypto World
XRP Price Prediction as token surges after Ripple CEO joins CFTC Advisory Committee
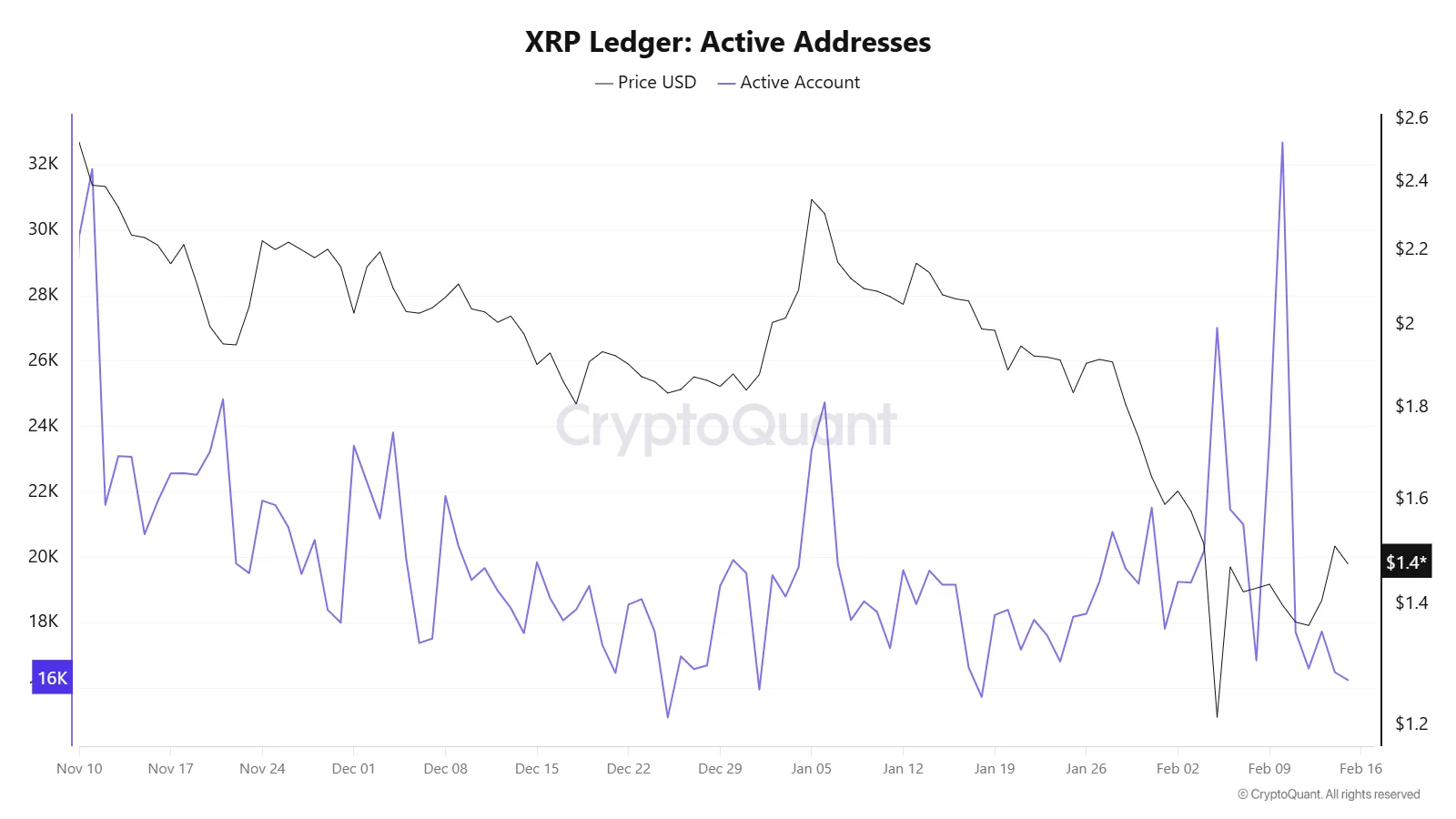
XRP price jumped after Ripple CEO Brad Garlinghouse joined the U.S. Commodity Futures Trading Commission’s (CFTC) Global Markets Advisory Committee, a move seen as strengthening Ripple’s regulatory standing in Washington.
Summary
- XRP surged after Ripple CEO Brad Garlinghouse joined the CFTC’s Innovation Advisory Committee, signaling stronger regulatory engagement.
- On-chain data shows a recent spike in XRP Ledger active addresses above 30,000, pointing to renewed network activity and speculative interest.
- Technically, XRP trades near $1.46, with resistance at $1.60 and $1.74, while support stands at $1.35 and $1.20.
However, the token has since pulled back and is trading lower at press time.
Ripple CEO’s CFTC role sparks market reaction
Executives from Coinbase, Ripple and Solana were named to the CFTC’s Innovation Advisory Committee, a group focused on digital asset policy, market structure and emerging financial technologies.
The development signals deeper engagement between major crypto firms and U.S. regulators at a time when the industry is pushing for clearer oversight frameworks.
For XRP (XRP) investors, Garlinghouse’s appointment is being interpreted as a constructive step toward regulatory normalization following years of legal scrutiny.
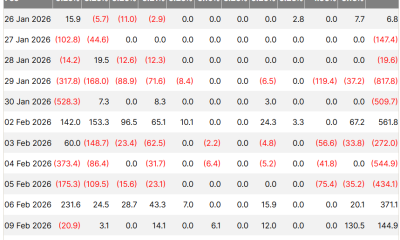
On-chain data supports the renewed interest. The XRP Ledger active addresses chart shows notable spikes in network activity in recent weeks, including a sharp surge above 30,000 active accounts in early February.
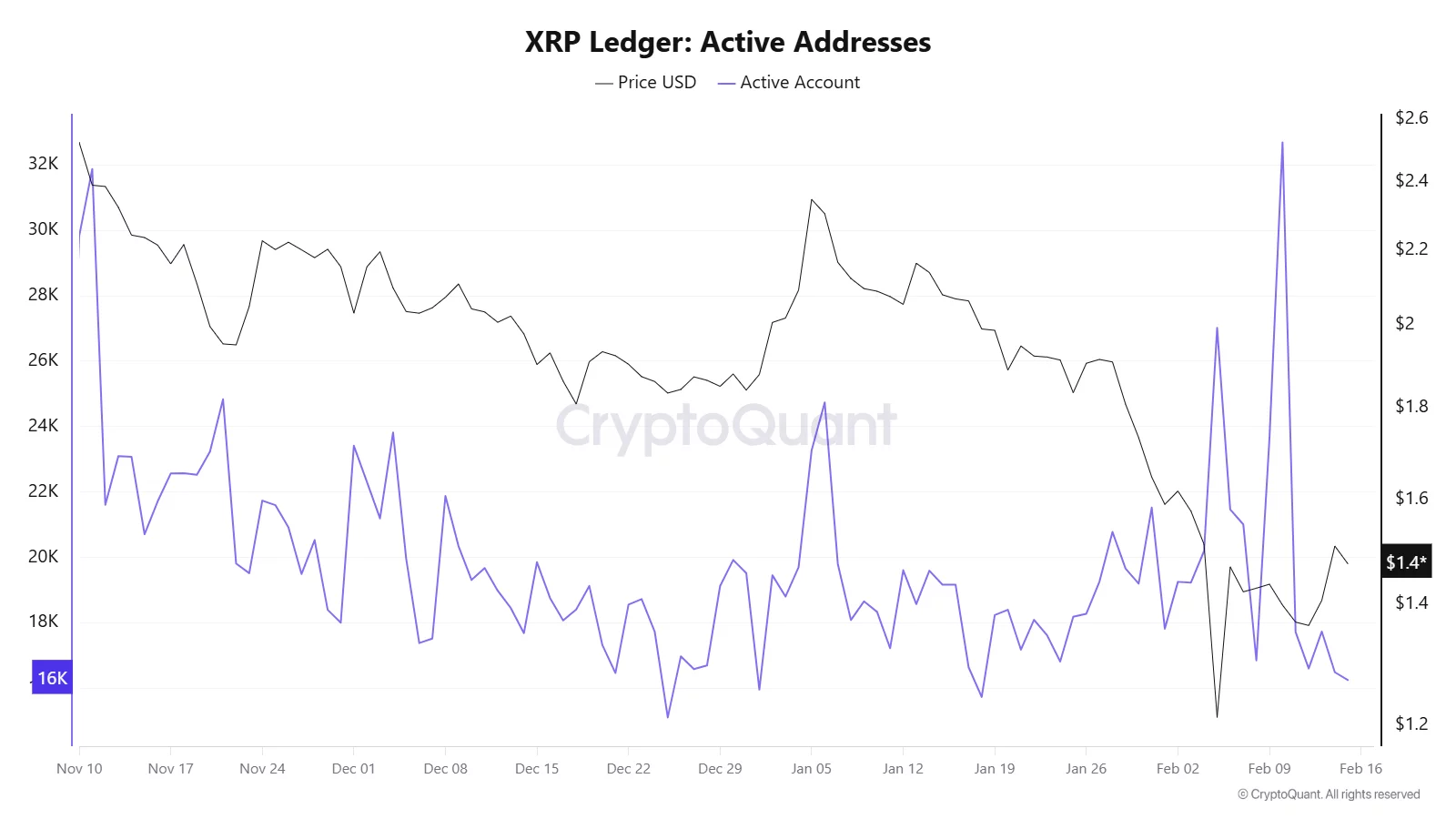
While activity has since cooled toward the 16,000–18,000 range, the earlier spike coincided with heightened price volatility, suggesting speculative participation and renewed user engagement.
What XRP price analysis suggests
At press time, XRP is trading near $1.46 on the daily chart. The token recently rebounded from a sharp drop toward the $1.20 region but remains under technical pressure.
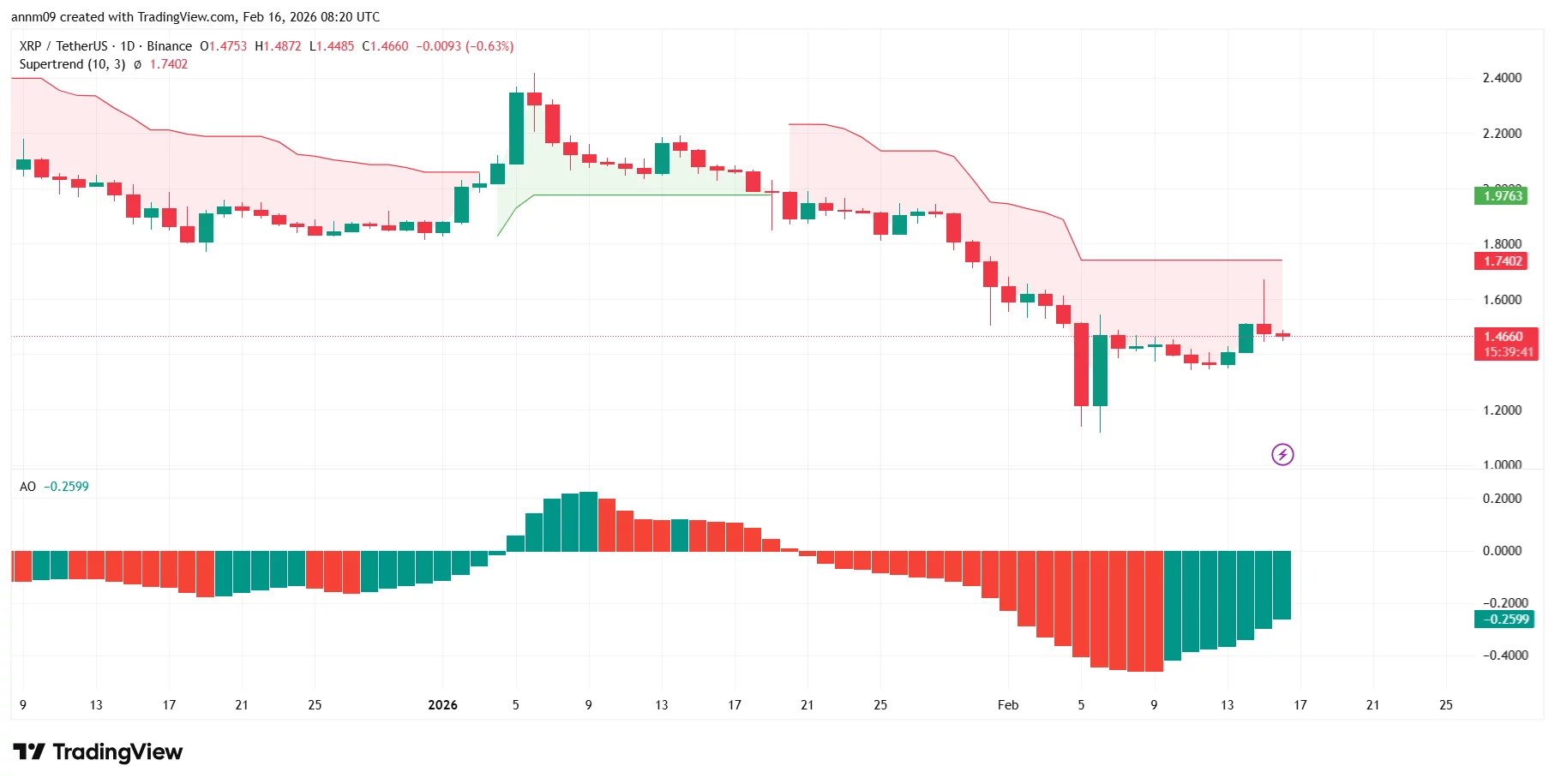
The Supertrend indicator (10,3) remains in bearish territory, with the trend line positioned around $1.74, signaling that the broader trend has not yet flipped bullish.
Meanwhile, the Awesome Oscillator, although still below the zero line, is printing rising green bars. This indicates bearish momentum is fading and a potential shift could be forming if buyers maintain pressure.
Immediate resistance sits near $1.60, followed by the stronger Supertrend barrier around $1.74. A daily close above that level could open the door toward the $1.90–$2.00 region.
On the downside, support lies near $1.35, with the recent swing low around $1.20 acting as critical structural support. A breakdown below $1.35 could expose XRP to another retest of that lower zone.
For now, XRP appears to be stabilizing, but a confirmed trend reversal will require a break above key resistance levels.
Crypto World
Russian crypto trading tops $640M a day, finance ministry reveals


Russia’s cryptocurrency market is experiencing a surge in transactional activity, with daily trading volumes reaching an estimated 50 billion rubles, roughly $640 million, according to Deputy Finance Minister Ivan Chebeskov.
Summary
- Russia’s Finance Ministry says crypto trading volumes have reached 50 billion rubles ($640 million) per day, or roughly $129 billion annually, much of it outside formal oversight.
- Lawmakers are preparing a sweeping regulatory framework that would introduce mandatory exchange licensing by 2027 and stricter supervision of crypto platforms.
- Proposed rules include potential retail investment caps, asset approval controls by the central bank, and penalties for unlicensed operators, while keeping the ban on crypto payments in place.
Booming crypto trade meets regulatory push
Speaking at the Alfa Talk forum on digital assets, Chebeskov said this “turnover of more than 10 trillion rubles annually” highlights the depth of crypto involvement among Russians, much of it occurring outside formal regulatory oversight.
“We’ve always said that millions of citizens are involved in this activity, representing trillions of rubles in terms of use and savings. One example is the daily cryptocurrency turnover in our country—around 50 billion rubles. That’s a turnover of more than 10 trillion rubles per year, which is currently occurring outside the regulated zone, outside our control,” the deputy minister explained.
Officials note that millions of citizens are participating in crypto trading, investing and savings, but most of these transactions currently take place through unregulated channels, leaving them beyond the attention of authorities.
Against this backdrop, Russian regulators are pushing to bring much of the crypto market under formal scrutiny. Lawmakers plan to present a comprehensive crypto regulation bill to the State Duma by June 2026, with the aim of adopting a legal framework that would take effect by July 1, 2027.
Under the draft legislation, all cryptocurrency exchanges would need licenses, and operating without approval could be penalized similarly to illegal banking. Retail investors would face annual limits on crypto purchases — proposed at about 300,000 rubles (≈ $4,000) — and qualification tests before they can trade.
Privacy-oriented cryptocurrencies could be restricted, and the central bank would have discretion over which assets are approved for legal trading beginning in mid-2027.
Major Russian exchanges, including the Moscow and St. Petersburg exchanges, have been preparing to launch regulated crypto trading platforms once the legal foundation is finalized. These efforts reflect broader policy shifts aimed at moving users away from “gray market” activity toward licensed, transparent venues.
The proposed rules also keep the long-standing ban on using crypto for domestic payments but open regulated trading as an investment vehicle. The combined push from the Ministry of Finance, the Bank of Russia, and the State Duma signals a strategic effort to balance market growth, investor protection and financial stability while reining in unregulated activity.
Crypto World
Coinbase retail traders buy Bitcoin and Ethereum dips, internal data shows


Coinbase CEO Brian Armstrong says retail users kept buying Bitcoin and Ethereum on price dips, with most Coinbase client balances in February at or above December levels.
Summary
- Coinbase internal data shows retail users increased BTC and ETH purchases during recent dips.
- Most Coinbase client crypto balances in February stayed equal to or higher than December levels.
- Analysts say resilient retail demand contrasts with softer institutional flows and may impact near-term market structure.
Coinbase CEO Brian Armstrong reported that retail investors increased cryptocurrency purchases during recent market declines, according to internal company data.
Armstrong stated in a post on social media platform X that individual investors on Coinbase demonstrated buying activity during price drops for Bitcoin and Ethereum. The executive cited internal trading data showing increased retail trading volume correlating with price declines.
“According to our data, individual users on Coinbase have been quite resilient in these market conditions: they took advantage of the dips to buy,” Armstrong stated. “We saw increases for retail users across Bitcoin and Ethereum.”
The Coinbase chief executive noted that retail investors exhibited holding behavior during short-term price volatility. Armstrong reported that most client cryptocurrency balances in February remained at or above December levels.
Bitcoin (BTC) and altcoin markets experienced sharp declines in recent weeks, with recovery attempts ongoing, according to market data.
Market analysts noted the contrast between retail buying activity and slower institutional fund inflows during the period. The divergence represents a significant factor in short-term supply and demand dynamics, according to industry observers.
Analysts stated that additional market catalysts would be needed for increased retail demand to shift broader market trends, given current macroeconomic conditions and derivatives market structure.
Coinbase operates as a cryptocurrency exchange platform serving retail and institutional clients.
Crypto World
Key macro data puts crypto markets on watch as CPI, PCE and Fed speak


Crypto and stock markets face a packed macro week, with CPI, PCE, Fed minutes and spending data set to test rate‑cut bets after mixed inflation and rising tensions.
Summary
- January CPI eased to its lowest core reading since 2021, briefly lifting crypto before gains faded.
- Markets now focus on retail sales, durable goods, PCE and Fed minutes to gauge rate‑cut timing.
- Bitcoin and Ethereum stay volatile as geopolitical risks and macro uncertainty cap risk appetite.
Financial markets are preparing for several key economic data releases this week that could influence cryptocurrency and stock prices, following mixed signals from last week’s inflation data.
January’s Consumer Price Index came in slightly below expectations, with headline inflation at 2.38% year-on-year and core CPI at 2.5%, marking the lowest level since early 2021, according to government data. The figures initially boosted stock and cryptocurrency markets on Friday, though cryptocurrency gains retreated over the weekend.
Traditional U.S. markets will be closed Monday for the President’s Day holiday. The ADP employment update is scheduled for Tuesday, followed by the January Retail Sales report. Wednesday will bring consumer spending data with the delayed December Durable Goods Orders numbers, along with Federal Reserve meeting minutes and 10 central bank speaker events.
The December Personal Consumption Expenditures (PCE) inflation report, considered a key indicator by the Federal Reserve, is expected to be released later this week. Goldman Sachs raised its PCE outlook following the January CPI data, estimating that the core PCE price index rose 0.40% in January, according to reports. The economists attributed the projection to rising consumer electronics and IT prices, which carry heavier weighting in PCE calculations than in CPI. A global shortage of RAM and storage components, driven by AI data center demand, has contributed to increased computer and component prices.
The CME Fed Watch Tool shows a 90% probability that interest rates will remain unchanged at the Federal Reserve‘s March meeting, according to current market pricing.
Cryptocurrency markets have declined in the past 24 hours, with total market capitalization falling. Bitcoin retreated from recent highs during early Asian trading on Monday and has remained rangebound for the past ten days. Ethereum prices have fallen sharply, while alternative cryptocurrencies have continued to decline.
The Kobeissi Letter noted that geopolitical tensions and macroeconomic uncertainty remain elevated, cautioning that volatility could continue this week.
Crypto World
The RWA War: Stablecoins, Speed, and Control


Consensus Hong Kong 2026 was, by many accounts, an RWA conference that happened to be about crypto. Across main stages, side events, and sponsored panels, real-world asset tokenization dominated the conversation — but not in the way it did a year ago.
The pitch decks have given way to genuine disagreements about architecture, regulation, and what tokenization actually solves. Here’s what’s actually being argued.
Stablecoins Are RWA — and Everyone Now Agrees
One of the clearest points of consensus was that the most successful RWA already exists. “The most successful RWA is USDT,” said CJ Fong, Managing Director and Head of APAC and EMEA Sales at GSR, during a panel at the main conference.
At the Gate’s side event, Chunda McCain, co-founder of Paxos Labs, described surging demand for PAXG, the firm’s gold-backed token, as evidence that stablecoins are expanding beyond dollar pegs into commodities and treasuries. Paxos secured its OCC conditional license in December and holds regulatory approvals in Singapore, Finland, and Abu Dhabi — a multi-jurisdictional strategy built around the assumption that stablecoins and tokenized assets are converging.
Brian Mehler, CEO of payment blockchain Stable, reinforced the point from the infrastructure side. His company’s USDT Zero system eliminates gas fees entirely — send 100 USDT, and 99.999 USDT arrives. At the Stablecoin Odyssey side event, Mehler compared the goal to Swift: the user shouldn’t know they’re on a blockchain.
The implication is that the stablecoin-RWA boundary is increasingly artificial. As stablecoins back themselves with T-bills, gold, and structured products, and as RWA platforms settle in USDC, the two categories are merging into a single tokenized finance layer.
The Architecture War: Permissioned vs Permissionless
The sharpest disagreement at the conference came from two companies that nominally do the same thing.
At the Consensus mainstage session “Tokenizing the Planet,” Graham Ferguson, Head of Ecosystem at Securitize, and Min Lin, Managing Director of Global Expansion at Ondo, laid out fundamentally different visions.
Securitize advocates for native token issuance under a permissioned framework. Ferguson argued that wrapper models — where an existing off-chain asset is wrapped into an on-chain token — create distance between the underlying asset and the investor, weakening protection. With BlackRock’s BUIDL fund surpassing $1 billion in AUM, he pointed to the track record of issuing securities directly on-chain with compliance built in.
Ondo takes the opposite path: permissionless wrappers that prioritize DeFi composability and global distribution. Min Lin argued that the model integrates more quickly with existing DeFi protocols and removes gatekeepers, an advantage particularly relevant for reaching investors across Asia. The company is actively expanding into Hong Kong, Singapore, and Japan.
In a follow-up interview with BeInCrypto, Ferguson questioned whether wrapper models can provide adequate investor protection. He also detailed Securitize’s plans to expand DeFi partnerships while maintaining its permissioned architecture.
The binary may already be outdated, though. At Stablecoin Odyssey’s RWA panel, Conflux CSO Forgiven described a live hybrid case: renewable energy assets packaged by a financial company and wrapped into a DeFi protocol. It’s a permissionless distribution of a regulated, real-world asset — a structure that doesn’t fit neatly into either camp.
Settlement Speed: The Argument That Keeps Winning
If one claim was repeated most across venues, it was that tokenization’s killer feature isn’t access or transparency — it’s speed.
Conflux’s Forgiven offered the most concrete benchmark: deposit USDC, receive immediate confirmation; request redemption, get USDC back within one hour. “Faster than T+0,” he noted, against traditional settlement cycles that can stretch to days.
The composability argument extends this further. Multiple panelists across sessions noted a limitation in traditional finance. Buying an asset and using it as collateral immediately is structurally impossible. On-chain, it’s native functionality.
Stable’s Mehler highlighted a practical pain point that bridges theory and reality: during the recent market selloff, ETH gas price volatility doubled transaction costs for businesses moving stablecoins. His fixed-cost USDT transfer model eliminates that variable, which matters when enterprises are processing thousands of transactions daily.
Physical Assets: Where the Narrative Meets Friction
The precious metals session at HashKey Cloud’s event provided a reality check. Ronald Tan, Director of Silver Times Limited, walked through the logistics of the silver market: warehouse costs, transportation challenges, and US-China export restrictions that don’t vanish when a token is minted.
This is the gap between financial RWA and physical RWA. Treasuries and fund shares can settle instantly because the underlying asset is already recorded in the ledger. Metals, energy, and real estate require verification that the physical asset exists and is properly custodied.
Paxos’s PAXG experience — gold tokens backed by allocated bars in London vaults — shows it can work at scale, but McCain acknowledged the company is committing additional resources to meet surging demand. The infrastructure for physical-asset tokenization is real, but far from trivial.
Asia as the Center of Gravity
Across all sessions, Asia — and Hong Kong specifically — emerged as the gravitational center of the RWA narrative.
Ondo is targeting Hong Kong, Singapore, and Japan for expansion. Securitize’s Ferguson told BeInCrypto that the company would prioritize jurisdictions with regulatory clarity, naming the same cities. Paxos already holds a Singapore MAS license. HashKey, as both an event host and a market participant, anchored multiple panels on Hong Kong’s positioning.
Forgiven of Conflux described its company as a rare Chinese blockchain project using real names. Its renewable energy RWA product was designed specifically for the Hong Kong market.
The subtext is clear: while US regulatory battles over stablecoin legislation and the Clarity Act continue — a point Anthony Scaramucci made forcefully in his own Consensus appearance — Asia is building the infrastructure and establishing the precedents.
What’s Actually at Stake
The RWA conversation at Consensus Hong Kong revealed an industry that has moved past the question of whether tokenization will happen. The arguments now center on how—permissioned or permissionless, financial or physical, institutional or retail-first—and the answers are diverging by asset class, jurisdiction, and business model.
The stablecoin-RWA convergence may prove to be the most consequential shift. If the most successful tokenized assets are stablecoins, and stablecoins are increasingly backed by real-world assets, the entire framing of RWA as a separate sector may not survive 2026.
The post The RWA War: Stablecoins, Speed, and Control appeared first on BeInCrypto.
Crypto World
Crypto funds bleed for fourth straight week as US investors pull back
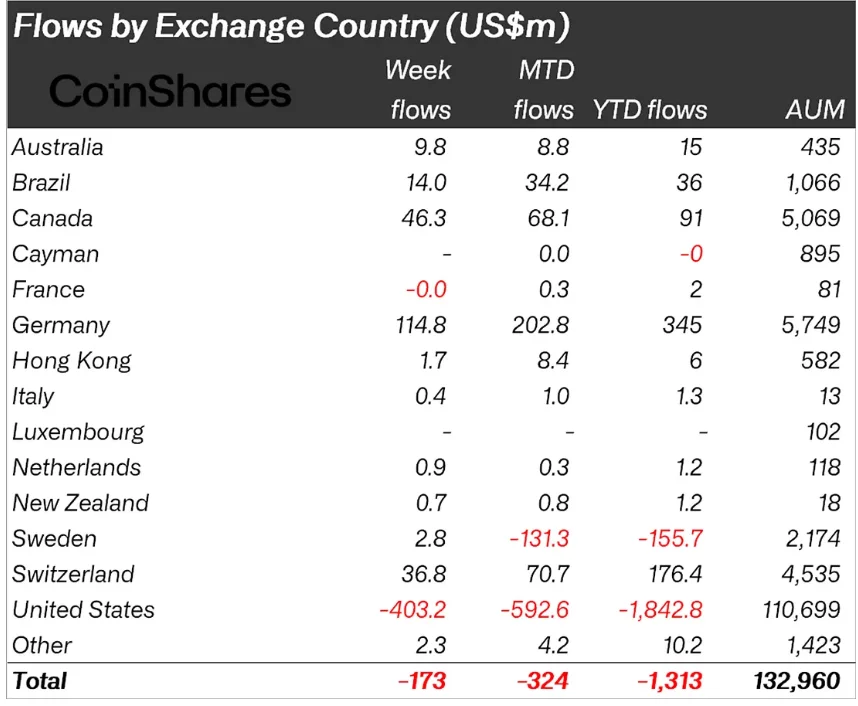
Crypto funds recorded a fourth consecutive week of outflows, with $173 million withdrawn, according to CoinShares’ latest weekly fund flows report.
Summary
- Digital asset investment products saw $173 million in outflows, marking a fourth consecutive week of withdrawals and bringing the four-week total to $3.74 billion.
- The US led the downturn with $403 million in outflows, while Europe and Canada recorded $230 million in combined inflows, highlighting sharp regional divergence.
- Bitcoin and Ethereum bore the brunt of selling, while XRP and Solana continued to attract capital.
The latest decline brings total outflows over the past four weeks to $3.74 billion, underscoring persistent investor caution amid price weakness and macro uncertainty.
The week began on a stronger footing, with $575 million in inflows, but sentiment quickly reversed. Midweek outflows reached $853 million, likely driven by further downside in crypto prices. Conditions improved slightly on Friday after weaker-than-expected US CPI data, which helped trigger $105 million in inflows.
Trading activity also cooled. Exchange-traded product (ETP) volumes fell sharply to $27 billion, down from a record $63 billion the previous week.
US leads crypto fund outflows as Europe and Canada diverge
Regional data revealed a stark divergence in sentiment. The United States accounted for $403 million in outflows, while other regions collectively posted $230 million in inflows.
Germany led with $115 million in inflows, followed by Canada ($46.3 million) and Switzerland ($36.8 million). The data suggests that while US investors remain risk-off, appetite for digital assets persists in parts of Europe and North America.
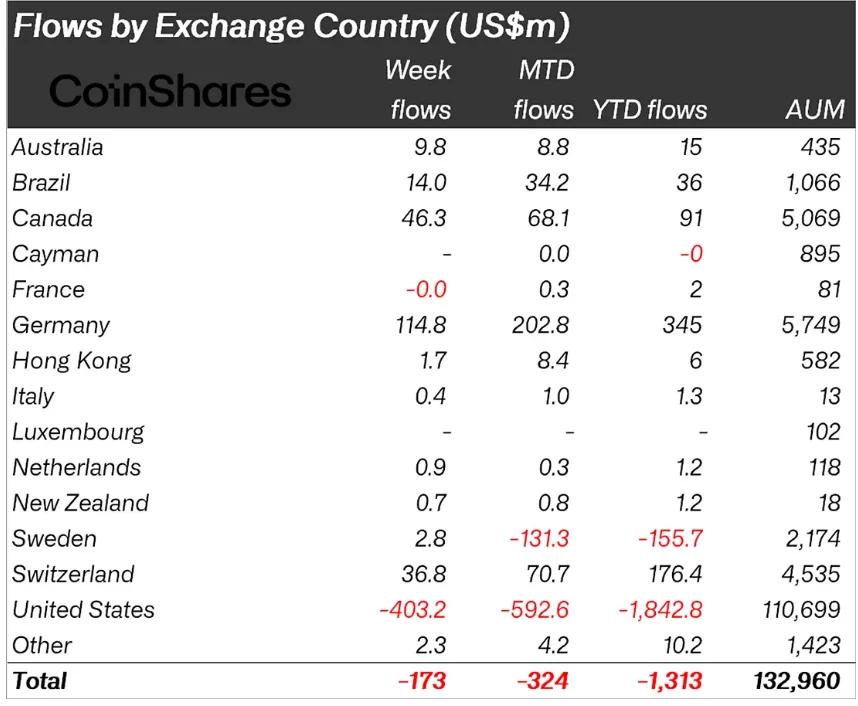
Bitcoin and Ethereum under pressure, altcoins show resilience
Bitcoin (BTC) bore the brunt of the sell-off, with $133 million in outflows last week. Ethereum (ETH) followed with $85.1 million in withdrawals.
Interestingly, short Bitcoin products also saw outflows totaling $15.4 million over the past two weeks, a pattern CoinShares notes is often observed near potential market bottoms.
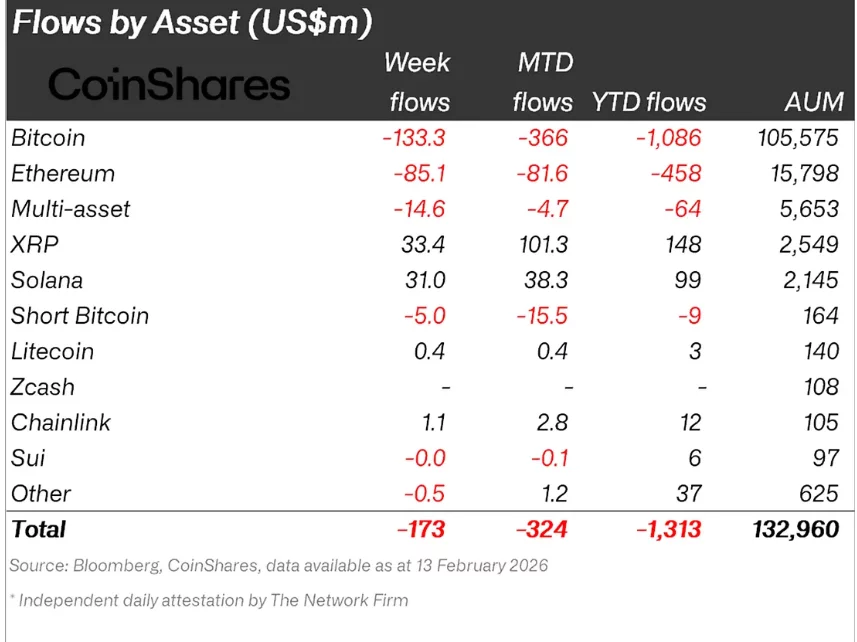
In contrast, select altcoins continued to attract capital. The Ripple token (XRP) led with $33.4 million in inflows, followed closely by Solana (SOL) and Chainlink (LINK). The selective resilience suggests investors are rotating exposure rather than exiting the asset class entirely.
Despite the recent drawdown, total assets under management remain substantial, highlighting that institutional engagement in digital assets continues even amid short-term volatility.
Crypto World
Bitcoin faces quantum scrutiny as leveraged shorts eye liquidation risk zone


Bitcoin faces quantum computing scrutiny and heavy leveraged short positioning, with SOPR stabilization, ETF inflows and CME gap levels shaping whether a 10% move triggers a cascade of liquidations.
Summary
- Quantum computing risks are drawing institutional attention, raising governance and upgrade questions as ETF-driven ownership concentrates capital.
- CoinGlass maps show clustered short liquidations near 10% above spot, while CME gap zones and weekend liquidity amplify the risk of sharp squeezes.
- SOPR signals show short-term selling pressure easing and ETF flows flipping positive, hinting at a potential rebound if key trigger levels break.
Bitcoin’s potential vulnerability to quantum computing threats has drawn attention from institutional investors, while derivatives markets show concentrated short positions vulnerable to liquidation on a 10% price rally, according to market data and industry observers.
Venture capitalist Nic Carter stated that large institutional holders could pressure Bitcoin developers if potential quantum computing threats are not addressed, according to reports from Coin Bureau. The comments come as institutional exposure to Bitcoin has expanded through spot exchange-traded funds and custodial products.
Liquidation data analyzed over the weekend indicated that a significant volume of short positions would face unwinding on a 10% upside move, while substantial long positions remained exposed to liquidation on an equivalent decline, according to trader Ted Pillows, who shared the analysis on social media platform X.
Pillows’ figures showed that leveraged short positions outweighed vulnerable long positions, creating conditions where an upward price movement could trigger rapid buybacks. The analysis identified specific trigger levels that could open a path toward higher price zones, while noting a nearby area tied to a Chicago Mercantile Exchange futures gap.
CoinGlass liquidation maps reflected elevated leverage across derivatives venues, with open interest clustering around round-number strikes. The positioning followed weekend momentum periods, when reduced liquidity often amplifies price movements.
On-chain analyst miracleyoon observed that the Short-Term Holder Spent Output Profit Ratio moved below the 0.95 capitulation zone before recovering toward 1.0. The metric measures whether short-term holders sell at a profit or loss and often signals shifts in local trend behavior, according to the analyst.
The analyst stated that sustained positioning above 1.0 would imply absorbed selling pressure and could extend a technical rebound, while failure to hold that threshold would reopen range-bound conditions. The recent drawdown lacked the intensity seen on August 5, 2024, when the ratio fell toward 0.9, according to the analysis.
CryptoQuant contributor Amr Taha compared retail flows on cryptocurrency exchange Binance with institutional exchange-traded fund activity. On February 6, retail-driven sell pressure exceeded 28,000 Bitcoin, coinciding with a price drop, according to Taha’s data. A second wave on February 13 surpassed 12,000 Bitcoin, even as prices attempted stabilization.
Spot Bitcoin exchange-traded funds posted their first positive net flow day since January on February 6, according to the same analysis. BlackRock’s iShares Bitcoin Trust led with notable inflows, followed by Fidelity’s Wise Origin Bitcoin Fund, suggesting institutions accumulated holdings during periods of retail selling.
Carter framed the quantum computing issue as governance pressure rather than an immediate technical flaw, arguing that capital concentration alters power dynamics within open-source systems, according to Coin Bureau’s report. The discussions have resurfaced as more corporate treasuries and asset managers have allocated capital through regulated investment vehicles.
Analyst Teddy Bitcoins stated that the current market structure mirrored the 2022 price decline, projecting a potential substantial decline in 2026 based on chart symmetry. The thesis relied on cyclical behavior patterns rather than immediate catalysts, according to the analyst’s commentary.
The quantum risk discussion intersects with leverage imbalances and on-chain stabilization signals, reflecting different time horizons from short-term liquidations to multi-year structural considerations. Markets have absorbed these factors simultaneously, adjusting exposure across spot and derivatives venues.
Traders are monitoring whether Bitcoin prices can sustain momentum above key trigger levels to force short covering, while failure to defend nearby support levels could revive gap-fill scenarios. Developers face renewed debate over cryptographic upgrade paths as institutional ownership increases, though immediate price movements appear more likely to emerge from leveraged positioning dynamics.
Crypto World
SBI Holdings says $10B XRP talk is false, here’s what’s real


SBI Holdings has pushed back against claims circulating on social media that it holds $10 billion worth of XRP, clarifying that the figure is inaccurate and misrepresents the company’s actual exposure to Ripple.
Summary
- SBI Holdings denied holding $10 billion in XRP, correcting viral social media claims that overstated its token exposure.
- CEO Yoshitaka Kitao clarified that SBI owns around 9% of Ripple Labs, not a multibillion-dollar stash of XRP tokens.
- The company described its Ripple equity stake as a potential “hidden asset,” suggesting long-term strategic value rather than direct crypto holdings.
SBI Holdings denies $10B XRP claims
The confusion appears to have stemmed from a widely shared post stating that SBI, a long-time partner of Ripple, was a “holder of $10 billion in XRP” while expanding its footprint in Asia through the acquisition of Singapore-based crypto platform Coinhako.
However, SBI Holdings Chairman and CEO Yoshitaka Kitao publicly corrected the claim. In a reply on X, Kitao stated: “Not $10 bil. in XRP, but around 9% of Ripple Lab. So our hidden asset could be much bigger.”
The clarification makes a key distinction: SBI does not directly hold $10 billion worth of XRP tokens. Instead, the Japanese financial services giant owns approximately 9% of Ripple Labs, the U.S.-based blockchain payments company closely associated with XRP.
SBI has been one of Ripple’s most prominent strategic partners in Asia for years, backing joint ventures and promoting the use of Ripple’s cross-border payment solutions across the region. Its equity stake in Ripple Labs represents a corporate investment, not a treasury holding of XRP tokens.
Kitao’s reference to a “hidden asset” suggests that SBI views its Ripple equity stake as potentially undervalued, particularly if Ripple’s valuation strengthens following regulatory clarity and continued expansion.
The incident shows how quickly misinformation can spread in crypto markets, especially when equity investments and token holdings are conflated. The takeaway is clear: SBI’s exposure to Ripple is significant, but it is tied to ownership in the company itself, not a multibillion-dollar XRP stockpile.
Crypto World
Dogecoin and These 2 Tokens Could Trigger a Meme Coin Rally
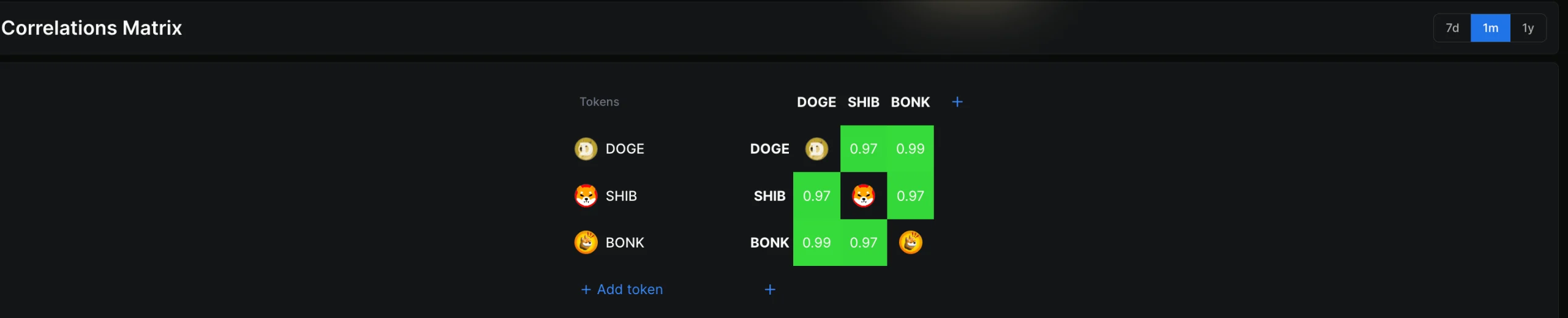
Dogecoin price may still hold the clues to whether meme coin season returns. Between February 6 and February 15, Dogecoin rallied about 47%. During the same period, the total meme coin market cap climbed by around 43%. This shows Dogecoin is still moving in step with the broader sector and continues to lead it.
Now, two of the most closely aligned meme coins, BONK and Shiba Inu, are already forming breakout patterns. Their next move may depend on whether Dogecoin confirms its own bullish structure. Together, correlation, holder behavior, and price structure suggest Dogecoin still remains the key signal for the meme coin cycle.
BONK and Shiba Inu Are Already Showing Breakout Structures
BONK and Shiba Inu currently have an extremely high correlation with Dogecoin. Correlation measures how closely assets move together.
A correlation of 1 means they move almost identically. Over the past month, BONK and Dogecoin reached a correlation as high as 0.99. Shiba Inu reached about 0.97 to 0.99 on weekly and monthly timeframes.
Sponsored
Sponsored
Want more token insights like this? Sign up for Editor Harsh Notariya’s Daily Crypto Newsletter here.
This makes their price structures important early signals.
BONK is forming an inverse head and shoulders pattern on the 12-hour chart. This pattern forms when sellers lose strength and buyers gradually take control. The breakout level sits near $0.0000075. If BONK breaks above this level, the pattern projects a move toward $0.000010, which would be about a 43% rally from the neckline.

The pattern weakens with a drop under $0.0000063 and invalidates under $0.0000051.
Shiba Inu (SHIB) is forming a bullish flag pattern. A bullish flag happens when the price pauses briefly after a rally before continuing higher. The breakout level sits near $0.0000069. If Shiba Inu breaks above this level, it could rise toward $0.0000099, representing a 43% gain.
A dip under $0.0000057 can come close to invalidating the SHIB breakout theory. However, these breakouts may still depend on Dogecoin confirming its own direction.
Meme Coin Market Cap Still Follows Dogecoin’s Lead
The broader meme coin market continues to mirror Dogecoin’s movement.
Between February 6 and February 15, the meme coin market cap increased roughly 43%. Dogecoin price increased slightly more, climbing 47% during the same period.
Sponsored
Sponsored
Even after the recent pullback, the meme coin market cap has fallen only about 12.5%, holding most of its gains. This shows the overall cycle has weakened but not collapsed.
Dogecoin still dominates the meme coin sector with a market cap of nearly $17 billion, representing over 50% of the entire meme coin market, at press time. Because of this dominance, Dogecoin often determines whether meme coin rallies expand or fade.
This makes Dogecoin’s own structure the most important signal.
Holders and Whales Are Quietly Positioning Again
On-chain data shows stronger holders are increasing control while short-term traders exit.
One key metric is Spent Coins Age Band. This measures how many coins of different holding ages are being spent. When these coins move, it often means that holder cohorts are selling. When the metric falls, it shows holders are staying inactive and holding.
This metric dropped sharply from 461 million coins to 168 million coins, a decline of about 64%. Similar drops previously appeared near local bottoms.
Sponsored
Sponsored
For example:
- On February 10, the metric reached a local low. Dogecoin price then rose about 22% within four days.
- On January 26, another local low appeared. Dogecoin price rose about 6% within two days.
Another indicator called HODL Waves shows how long investors hold their coins. Short-term holders, holding coins for one to three months, reduced their share from 10.41% to 5.70%, a drop of about 45%. This shows speculative traders exited.
Meanwhile, stronger holders increased exposure. Coins held for six to twelve months increased from 10.48% to 11.22%, a 7% increase. This shows growing conviction.
Whales also accumulated. Wallets holding over one billion DOGE (the biggest whales) increased holdings from 70.56 billion to 70.84 billion coins, adding roughly 280 million coins.
This shift shows stronger hands replacing weaker ones.
Sponsored
Sponsored
Dogecoin Price Pattern Now Holds the Key Meme Coin Season Signal
Despite the recent 13% pullback, Dogecoin’s price structure remains bullish. On the 12-hour chart, Dogecoin is forming a cup and handle pattern. This pattern often appears before continuation rallies.
The cup formed between late January and early February. The current pullback forms the handle. Importantly, the handle support near $0.103 remains intact, showing buyers are still active. The key breakout level now sits near $0.117, which is also a down-sloping neckline resistance.
If Dogecoin breaks above $0.117, the pattern projects a move toward $0.180, representing roughly a 50% rally, per pattern projection. Supporting this, the Smart Money Index, which tracks experienced investor activity, remains above its signal line. This suggests larger investors have not exited.
However, risks remain. If Dogecoin falls below $0.098, the pattern would weaken. A drop below $0.091 would invalidate the bullish structure.
For now, Dogecoin price continues to hold the strongest clues for meme coin season. BONK and Shiba Inu are already preparing breakout structures.
But whether those breakouts fully develop may depend on Dogecoin confirming its own move first.
-

 Sports5 days ago
Sports5 days agoBig Tech enters cricket ecosystem as ICC partners Google ahead of T20 WC | T20 World Cup 2026
-

 Tech6 days ago
Tech6 days agoSpaceX’s mighty Starship rocket enters final testing for 12th flight
-
 Crypto World7 days ago
Crypto World7 days agoU.S. BTC ETFs register back-to-back inflows for first time in a month
-
 Video11 hours ago
Video11 hours agoBitcoin: We’re Entering The Most Dangerous Phase
-

 Tech2 days ago
Tech2 days agoLuxman Enters Its Second Century with the D-100 SACD Player and L-100 Integrated Amplifier
-

 Video4 days ago
Video4 days agoThe Final Warning: XRP Is Entering The Chaos Zone
-

 Crypto World6 days ago
Crypto World6 days agoBlockchain.com wins UK registration nearly four years after abandoning FCA process
-
 Crypto World5 days ago
Crypto World5 days agoPippin (PIPPIN) Enters Crypto’s Top 100 Club After Soaring 30% in a Day: More Room for Growth?
-
 Crypto World3 days ago
Crypto World3 days agoBhutan’s Bitcoin sales enter third straight week with $6.7M BTC offload
-
 Video5 days ago
Video5 days agoPrepare: We Are Entering Phase 3 Of The Investing Cycle
-
 Crypto World7 days ago
Crypto World7 days agoEthereum Enters Capitulation Zone as MVRV Turns Negative: Bottom Near?
-

 NewsBeat1 day ago
NewsBeat1 day agoThe strange Cambridgeshire cemetery that forbade church rectors from entering
-

 Business5 days ago
Business5 days agoBarbeques Galore Enters Voluntary Administration
-

 Crypto World6 days ago
Crypto World6 days agoCrypto Speculation Era Ending As Institutions Enter Market
-
 Crypto World4 days ago
Crypto World4 days agoEthereum Price Struggles Below $2,000 Despite Entering Buy Zone
-

 Politics6 days ago
Politics6 days agoWhy was a dog-humping paedo treated like a saint?
-

 NewsBeat2 days ago
NewsBeat2 days agoMan dies after entering floodwater during police pursuit
-
 Crypto World3 days ago
Crypto World3 days agoBlackRock Enters DeFi Via UniSwap, Bitcoin Stages Modest Recovery
-

 NewsBeat3 days ago
NewsBeat3 days agoUK construction company enters administration, records show
-

 Sports6 days ago
Sports6 days agoWinter Olympics 2026: Australian snowboarder Cam Bolton breaks neck in Winter Olympics training crash



















