Crypto World
Kaspersky finds Keenadu Android malware preinstalled on devices

Editor’s note: In an era of increasingly covert software supply chain threats, Kaspersky’s Keenadu discovery highlights how malware can slip into devices at multiple points—from preinstalled firmware to apps from official stores. This briefing breaks down what Keenadu is, how it operates, and what consumers and vendors should watch for as mobile devices become more integrated with smart ecosystems. While the study is technical, the takeaway is clear: routine device updates and robust security layers remain essential for staying ahead of evolving threats.
Key points
- Keenadu is Android malware that can be preinstalled in firmware, embedded in system apps, or downloaded from official stores.
- Used for ad fraud and can give attackers full control over the device in some variants.
- As of February 2026, over 13,000 infected devices reported; Russia, Japan, Germany, Brazil and others affected.
- Variants include firmware-integrated backdoors, system-app implants, and malicious apps on Google Play.
- Some infected apps on Google Play have been removed; risk persists with other app stores and APKs.
Why this matters
Preinstalled malware threatens users at the earliest moment of device setup, bypassing typical defenses and elevating the risk profile for mobile ecosystems. The Keenadu case underscores the need for rigorous supply-chain verification and proactive security solutions that monitor firmware and app-level integrity.
What to watch next
- Ongoing updates from Kaspersky on Keenadu variants and distribution vectors.
- Monitoring for new devices affected via firmware supply chains or app stores.
- User guidance to apply firmware updates and use reputable security software to detect such threats.
Disclosure: The content below is a press release provided by the company/PR representative. It is published for informational purposes.
Kaspersky finds Keenadu Android malware preinstalled on devices
Kaspersky has detected a new malware for Android devices that it dubbed Keenadu. This malware is distributed in multiple forms – it can be preinstalled directly into devices’ firmware, embedded within system apps, or even downloaded from official app stores such as Google Play. Currently Keenadu is used for ad fraud, with attackers using infected devices as bots to deliver link clicks on ads, but it can also be used for malicious purposes, with some variants even allowing full control of the victim’s device.
As of February 2026, Kaspersky mobile security solutions detected over 13,000 devices infected with Keenadu. The highest numbers of the attacked users have been observed in Russia, Japan, Germany, Brazil, the Netherlands, Turkiye, and other countries have been affected.
Integrated into device firmware
Similar to the Triada backdoor that Kaspersky detected in 2025, some versions of Keenadu are integrated into the firmware of several models of Android tablets at one of the supply chain stages. In this variant, Keenadu is a fully functional backdoor that provides the attackers with unlimited control over the victim’s device. It can infect every app installed on the device, install any apps from APK files and give them any available permissions. As a result, all information on the device, including media, messages, banking credentials, location, etc., can be compromised. The malware even monitors search queries that the user inputs into the Chrome browser in incognito mode.
When integrated into the firmware, the malware behaves differently depending on several factors. It will not activate if the language set on the device is one of Chinese dialects, and the time is set to one of Chinese time zones. It will also not launch if the device doesn’t have Google Play Store and Google Play Services installed.
Embedded within system apps
In this variant, the functionality of Keenadu is limited – it cannot infect every app on the device, but since it exists within a system app (which has elevated privileges compared to usual apps), it can still install any side apps that the attackers choose without the user knowing. What’s more, Kaspersky discovered Keenadu embedded within a system application responsible for unlocking the device with the user’s face. The attackers could potentially acquire victim’s face data. In some cases, Keenadu was embedded within the home screen app which is responsible for the home screen interface.
Embedded within apps distributed through Android app stores
Kaspersky experts also discovered that several apps distributed on Google Play are infected with Keenadu. These are apps for smart home cameras, and they’ve been downloaded over 300,000 times. As of the time of publication, these apps have been removed from Google Play. When the apps are launched, attackers may launch invisible web browser tabs within the apps, that can be used to browse through different websites without the user knowing. Previous research from other cybersecurity researchers also showed similar infected apps being distributed via standalone APK files or through other app stores.


Infected apps on Google Play
As our recent research showed, preinstalled malware is a pressing issue on multiple Android devices. Without any actions on the user side, a device can be infected right out of the box. It is important for users to understand this risk and use security solutions that can detect this type of malware. Vendors likely didn’t know about the supply chain compromise that resulted in Keenadu infiltrating devices, as the malware was imitating legitimate system components. It is important to check every stage of the production process to ensure that device firmware is not infected,” comments Dmitry Kalinin, security researcher at Kaspersky.
See the post on Securelist for more information.
Recommendations:
- Use a reliable security solution to be promptly notified of similar threats on your device.
- If you are using a device with infected firmware, check for firmware updates. After the update, run a scan of the device with a security solution.
- If a system app is infected, we recommend that users stop using it and then disable it. If a launcher app is infected, we recommend disabling the default launcher and using third-party launchers.
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. With over a billion devices protected to date from emerging cyberthreats and targeted attacks, Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative solutions and services to protect individuals, businesses, critical infrastructure and governments around the globe. The company’s comprehensive security portfolio includes leading digital life protection for personal devices, specialized security products and services for companies, as well as Cyber Immune solutions to fight sophisticated and evolving digital threats. We help millions of individuals and nearly 200,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.
Crypto World
XRP Ledger rolls out members-only DEX for regulated institutions
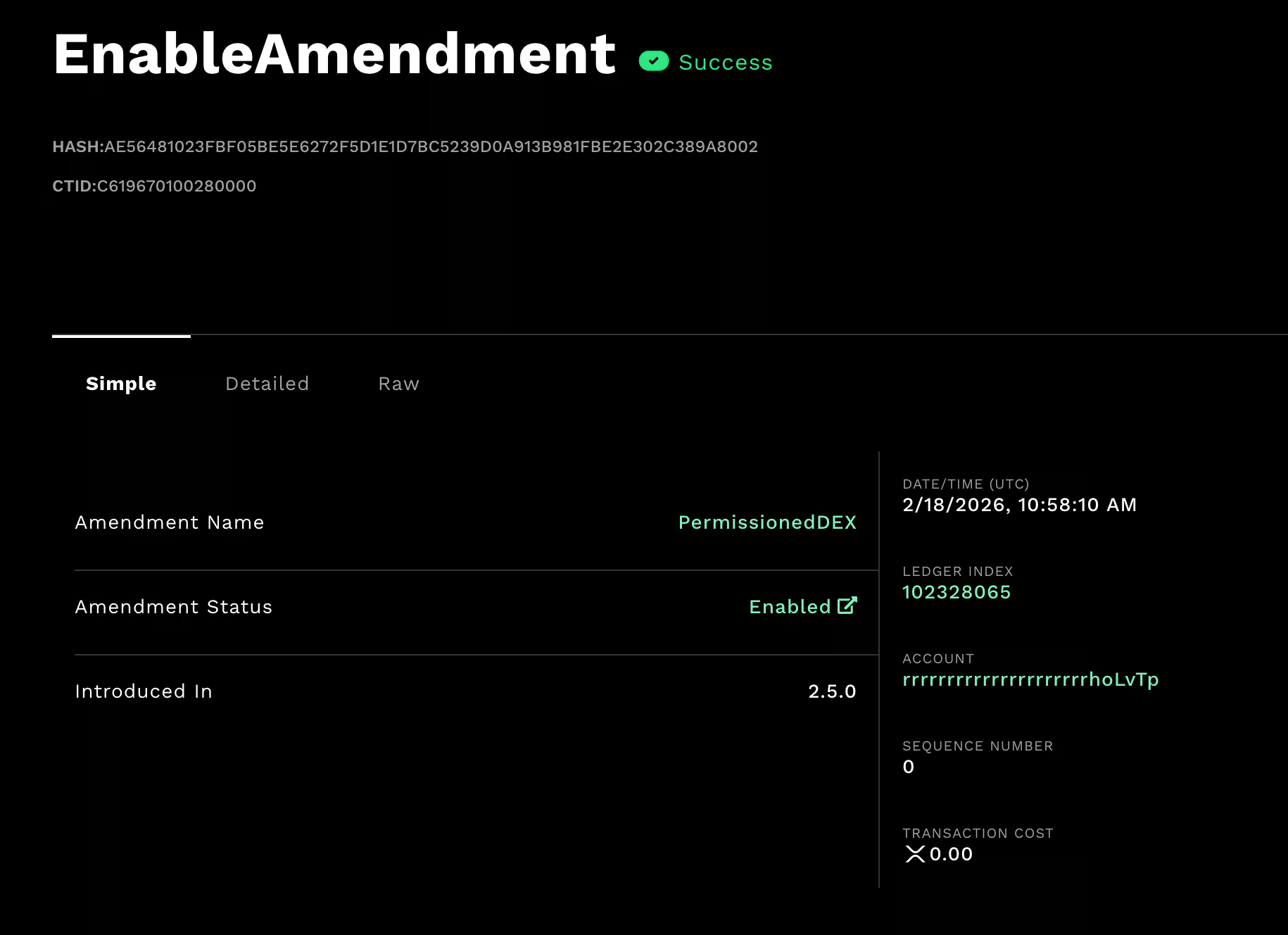
The XRP Ledger has activated a new “Permissioned DEX” amendment, a technical upgrade designed to let regulated institutions trade on XRPL without opening markets to everyone.
The change, known as XLS-81, allows the creation of permissioned decentralized exchanges that work like XRPL’s existing built-in DEX, but with a key difference.

A permissioned domain can restrict who is allowed to place offers and who is allowed to accept them, creating a gated trading venue where participation can be tied to compliance requirements such as KYC and AML checks.
Think of it as a ‘members only’ marketplace, while still keeping the trading mechanics native to the ledger.
The feature is aimed at banks, brokers and other firms that may want onchain settlement and liquidity but cannot interact with fully open DeFi markets. For these players, the ability to control access is not optional but forms the minimum requirement.
The activation also adds to a growing set of “institutional DeFi” primitives XRPL has been rolling out this month. Token Escrow, or XLS-85, went live last week, extending XRPL’s native escrow system beyond XRP to all trustline-based tokens and Multi-Purpose Tokens, including stablecoins such as RLUSD and tokenized real-world assets.
Together, the two upgrades create a more complete toolkit for regulated finance on XRPL. Token escrow allows conditional settlement for assets issued on the network, while the permissioned DEX provides a controlled venue for trading them.
That combination is central to use cases like tokenized funds, stablecoin FX rails, and regulated secondary markets for tokenized assets.
While the changes are unlikely to matter to most retail traders day to day, they signal XRPL’s direction. It is building infrastructure for institutions first, even if that means leaning into gated markets rather than the fully open DeFi model that defined the last cycle.
Crypto World
Aptos (APT) declines 3%, leading index lower
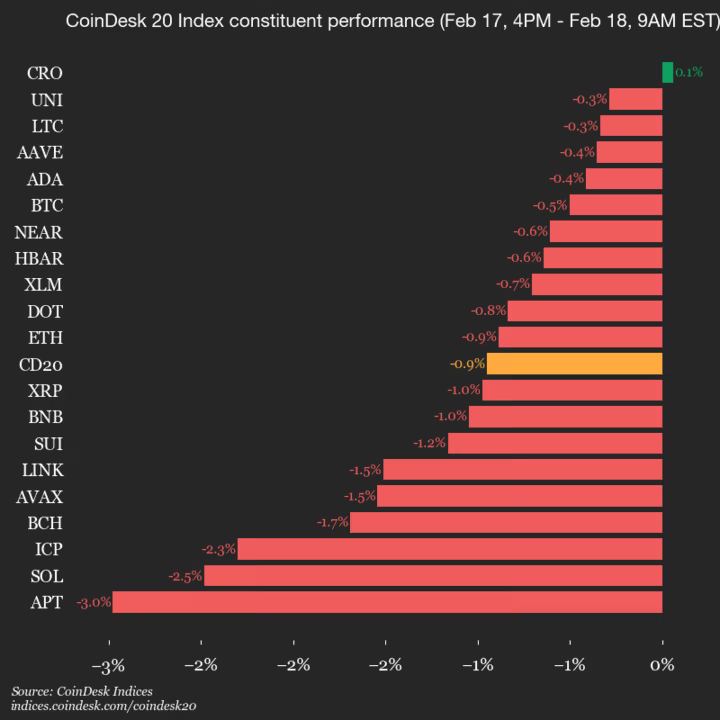
CoinDesk Indices presents its daily market update, highlighting the performance of leaders and laggards in the CoinDesk 20 Index.
The CoinDesk 20 is currently trading at 1962.18, down 0.9% (-18.81) since 4 p.m. ET on Tuesday.
One of the 20 assets is trading higher.

Leaders: CRO (+0.1%) and UNI (-0.3%).
Laggards: APT (-3.0%) and SOL (-2.5%).
The CoinDesk 20 is a broad-based index traded on multiple platforms in several regions globally.
Crypto World
MYX closes strategic funding round led by Consensys


Disclosure: This article does not represent investment advice. The content and materials featured on this page are for educational purposes only.
MYX has completed and closed a strategic funding round led by Consensys ahead of its V2 launch.
Onchain derivatives protocol MYX has completed a strategic funding round led by Consensys, with participation from Consensys Mesh and Systemic Ventures, ahead of the MYX V2 launch. With the closing of this round, Consensys has officially become the largest investor in MYX. The raise supports the rollout of MYX’s Modular Derivative Settlement Engine, marking the platform’s transition into core infrastructure for omnichain derivatives.
MYX V2 represents a structural shift in how onchain derivatives are built and settled. Rather than operating as a vertically integrated dapp, MYX now serves as a modular settlement layer that other products and platforms can build upon.
At the protocol level, MYX V2 integrates account abstraction via EIP-4337 and EIP-7702 alongside Chainlink’s latest permissionless oracle stack. Together, these components are designed to remove long-standing frictions in onchain trading including slow listings for long-tail assets as well as inefficient use of capital and complex transaction flows.
MYX V2 enables gasless, one-click trading while preserving non-custodial control and introduces a Dynamic Margin system that supports up to 50x leverage without relying on traditional order book depth. This architecture allows MYX to offer oracle-anchored pricing that eliminates slippage for large orders, significantly reducing execution risk for professional traders.
By decoupling liquidity depth from execution quality, MYX aims to eliminate the trade-off between access and execution that onchain perps traders deal with every day. MYX states that with this approach, traders no longer need to wait for deep order books, ladder into positions, or eat slippage when trading size, especially in new or volatile markets. Pricing is anchored directly to oracles rather than transient market depth, allowing positions to be opened and closed at predictable prices regardless of local liquidity conditions.
According to the team, the result is materially lower effective trading costs than underlying spot markets, immediate access to newly emerging assets, and consistent execution even during periods of market stress. These mechanics are not discretionary or market-maker dependent; they are enforced by deterministic economic models, robust margin systems, and conservative security assumptions designed to perform under real trading conditions.
Disclosure: This content is provided by a third party. Neither crypto.news nor the author of this article endorses any product mentioned on this page. Users should conduct their own research before taking any action related to the company.
Crypto World
Bitcoin stays volatile while MUFG says stables work better as money


Bitcoin slips ~2% in 7d as MUFG touts stablecoins’ price-stable payments.
Summary
- TC trades near $68k, with a 7d move of about -2.25%, and a 24h range around $66.7k–$69.1k.
- MUFG’s Hardman says stablecoins better meet money’s role via price stability, fast settlement, and low-cost transfers versus BTC’s higher volatility.
- Stablecoins, often fiat-pegged, are gaining attention as digital cash and could see higher adoption in payments while BTC remains mainly a store-of-value asset.
An analyst at Mitsubishi UFJ Financial Group has stated that stablecoins represent a more suitable currency option than Bitcoin for payment purposes, according to recent commentary from the Japanese financial institution.
Lee Hardman, an analyst at MUFG, one of Japan’s three largest banks, said stablecoins have attracted increased attention compared to other digital assets due to their function as digital cash.
Hardman stated that stablecoins better fulfill the requirements of money by offering price stability and fast, low-cost payment services, according to the analyst’s assessment. The analyst noted that Bitcoin’s high price volatility limits its use as a daily payment method.
Stablecoins are pegged to fiat currencies and maintain stable value, making them more likely to be used as a medium of exchange and payment, Hardman said.
The comments come as interest in Bitcoin and cryptocurrencies continues to expand globally, with financial institutions increasingly evaluating various digital asset classes for potential use cases.
Crypto World
What Happens to ETH if $2K Support Is Decisively Lost?
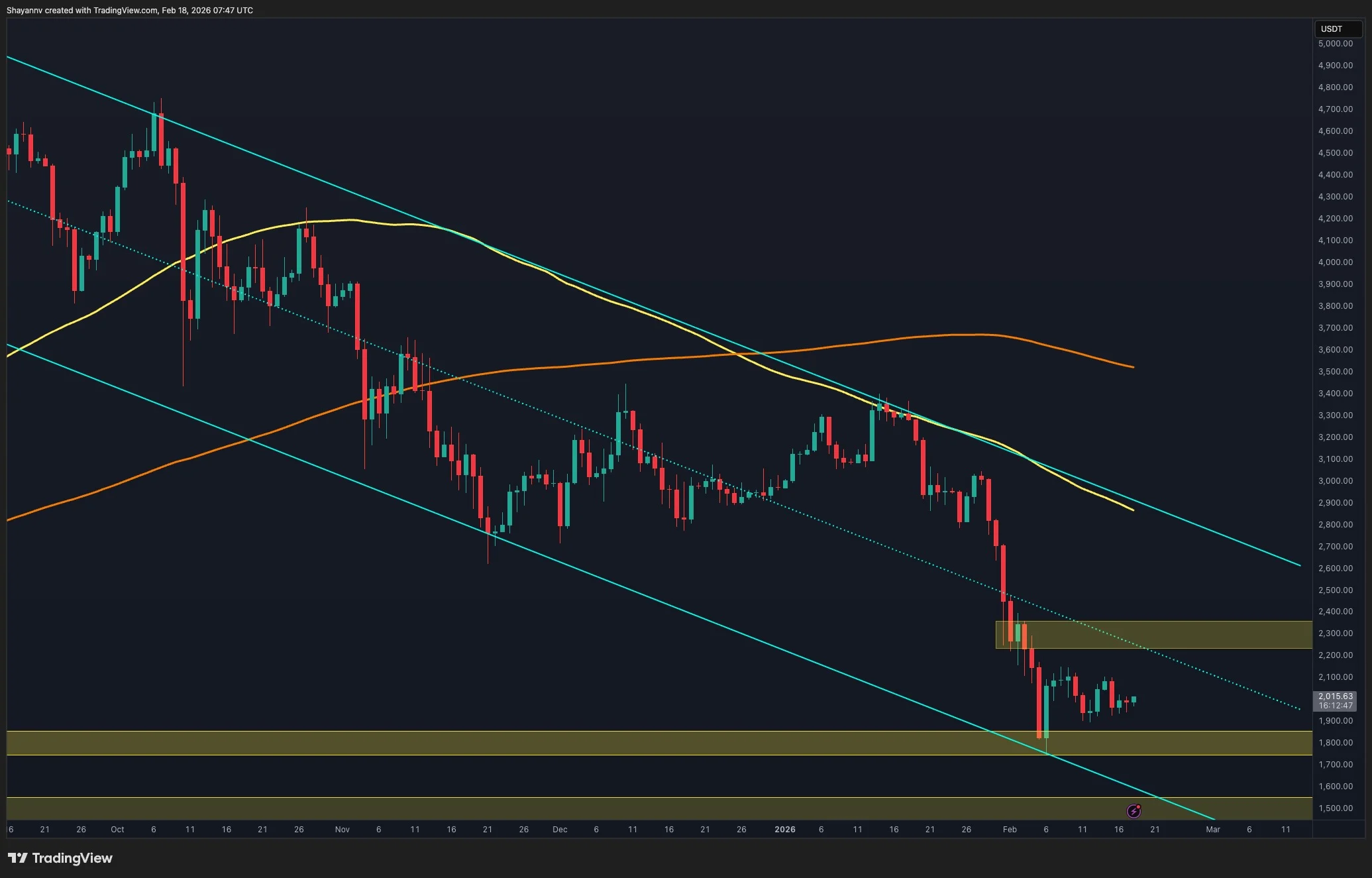
After the aggressive sell-off toward the $1.8K region, the market has transitioned into choppy consolidation, while lower timeframes are now approaching a decisive breakout point. The key question is whether this compression resolves to the upside or results in continuation within the dominant downtrend structure.
Ethereum Price Analysis: The Daily Chart
On the daily timeframe, Ethereum is exhibiting clear consolidation behaviour following its sharp decline. The price action has become increasingly choppy, reflecting equilibrium between buyers and sellers. Instead of impulsive continuation, the market is printing overlapping candles with limited directional commitment.
This consolidation is confined between the $1.8K static support base and the channel’s midline acting as dynamic resistance. The mid-boundary of the descending channel continues to cap bullish attempts, preventing a structural trend reversal. Meanwhile, the $1.8K zone remains a strong demand area that has repeatedly absorbed selling pressure.
As long as the price remains trapped between these two boundaries, the primary scenario is range-bound fluctuation. A confirmed breakout above the channel’s midline would open the path toward higher resistance zones, while a breakdown below $1.8K would invalidate the equilibrium and likely trigger another impulsive leg lower.
ETH/USDT 4-Hour Chart
Zooming into the 4-hour timeframe, the market structure becomes more compressed. Ethereum has formed a clear triangle pattern, with descending resistance and rising support squeezing the price into a narrow apex. This pattern reflects volatility contraction and typically precedes an expansion phase.
The asset is now approaching the final portion of the triangle, suggesting that a breakout is imminent. Given the recent higher lows inside the pattern and the improving short-term structure, the probability of an upside breakout is increasing. The targets are clearly defined on the chart, with the first resistance zone aligned with the previously marked supply region above the pattern at the $2.4K area.
However, failure to break upward and a decisive breakdown below the ascending support would shift momentum back in favour of sellers.
Sentiment Analysis
The Binance ETH/USDT liquidation heatmap reveals significant liquidity dynamics around the current range. A dense liquidity cluster is positioned above the current price, indicating a concentration of short liquidation levels. Such clusters often act as magnets, drawing the price upward to trigger liquidations before a potential reaction.
At the same time, a developing liquidity concentration below the market reflects the accumulation of long positions. This suggests that traders are increasingly positioning for upside continuation, building long exposure near the consolidation zone.
The interaction between these liquidity pools increases the likelihood of a volatility expansion. A breakout to the upside could trigger short liquidations above the price, accelerating the move. Conversely, a downside sweep could target the long liquidity cluster before a potential rebound.
Overall, Ethereum is in a compression phase. The daily chart reflects equilibrium within a broader downtrend, the 4-hour chart shows a triangle nearing resolution, and liquidity positioning suggests that a decisive breakout move is approaching.
SECRET PARTNERSHIP BONUS for CryptoPotato readers: Use this link to register and unlock $1,500 in exclusive BingX Exchange rewards (limited time offer).
Disclaimer: Information found on CryptoPotato is those of writers quoted. It does not represent the opinions of CryptoPotato on whether to buy, sell, or hold any investments. You are advised to conduct your own research before making any investment decisions. Use provided information at your own risk. See Disclaimer for more information.
Crypto World
AMLBot Says Social Engineering Drove 65% of Crypto Incidents in 2025
About two-thirds of crypto incidents investigated by blockchain analytics company AMLBot in 2025 were driven by social engineering rather than technical exploits, according to a report based on the company’s internal casework.
AMLBot said 65% of the incidents it reviewed last year involved access and response failures, such as compromised devices, weak verification and delayed detection, instead of vulnerabilities in blockchains or smart contracts.
The company said its analysis drew on about 2,500 internal investigations and should not be read as an industry-wide measure of crypto crime, according to a Wednesday report shared with Cointelegraph.
Primary attack vectors included device compromises via chat scams, impersonation scams, and other investment and phishing scams involving social manipulation.
Crypto phishing attacks are social engineering schemes that don’t require hacking code. Instead, attackers share fraudulent links to steal victims’ sensitive information, such as the private keys to crypto wallets.
The findings suggest that security improvements at the protocol level may not be enough to protect users if scammers can bypass safeguards by targeting people directly.

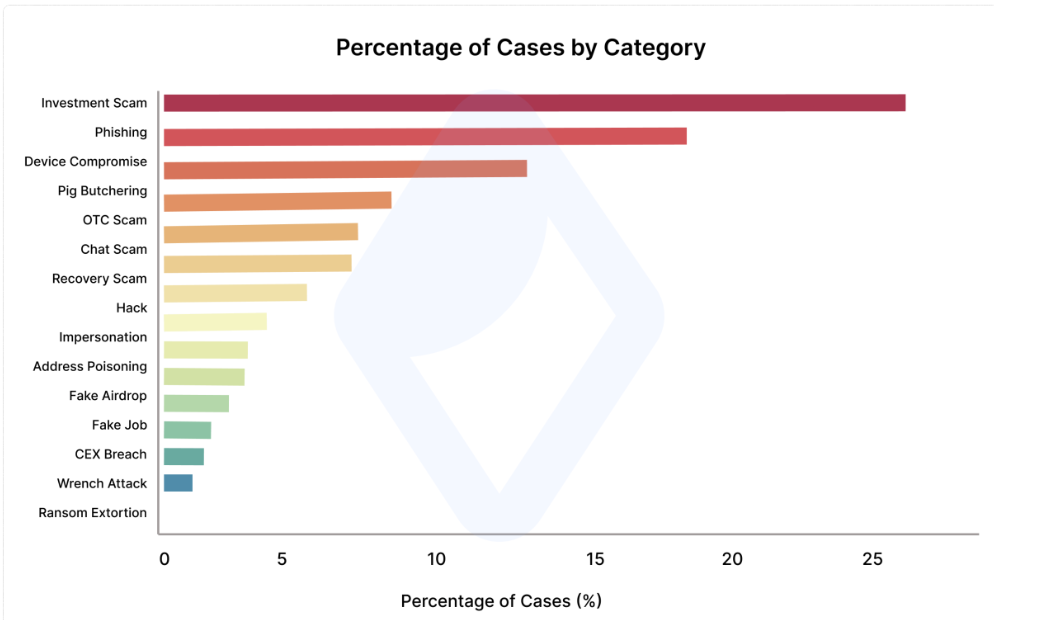
Investment scams and phishing lead by case count
Investment scams accounted for the largest share of cases (25%), followed by phishing attacks (18%) and device compromises (13%), as the most damaging categories in terms of case frequency.
Related: 22 Bitcoin worth $1.5M vanish from Seoul police custody
Pig-butchering scams accounted for 8%, over-the-counter (OTC) fraud for 8%, and chat-based impersonation represented 7%, collectively making up the second tier of the most frequent attacks.

Impersonation linked to $9 million in recent losses
AMLBot traced at least $9 million in stolen digital assets to impersonation-related attacks over the past three months.
Impersonation is the most damaging attack vector in terms of social engineering scams, Slava Demchuk, CEO of AMLBot, told Cointelegraph. “Attackers continue to exploit and trick victims with a ruthless game of charades, posing as trusted entities,” he said. “Sometimes they’re exchange support teams, investment partners, project managers or reps.”
Demchuk urged users not to share private keys or recovery phrases and to be wary of urgent requests involving fund transfers or wallet access, which he said are common entry points for social engineering scams.
Related: Binance confirms employee targeted as three arrested in France break-in
To protect against impersonation attacks, Demchuk urged crypto investors not to share their private keys and recovery phrases.
He also advised investors to ignore “urgent requests involving fund transfers of wallet access,” which are usually the first point of contact for social engineering scams.
CertiK reports January spike in crypto losses
Crypto scams saw an uptick in January, when scammers stole $370 million, the highest monthly figure in 11 months, according to crypto security company CertiK.

$311 million of the total value was attributed to phishing scams, with a particularly damaging social engineering scam costing one victim around $284 million.
Magazine: Meet the onchain crypto detectives fighting crime better than the cops
Crypto World
Ether briefly priced at $1 after glitch on DeFi app, triggering $1.8M in bad debt


A pricing error that lasted only minutes has left DeFi lender Moonwell with nearly $1.8 million in bad debt after a software glitch caused the value of Coinbase Wrapped ETH (cbETH) to drop to $1, instead of roughly $2,200, on the platform.
The technical glitch happened because a system update caused the platform to value cbETH based only on its relationship to ETH (about 1.12), forgetting to factor in the actual USD price of ether.
As a result, the protocol interpreted cbETH as being worth around $1.12, per an incident summary.
The issue began when a governance proposal enabled new Chainlink oracle configurations across Moonwell markets on Base and Optimism networks. An oracle is a tool that fetches real-time data before it is added to a blockchain.
In lending protocols such as Moonwell, users deposit assets like cbETH as collateral and borrow other tokens against them. If collateral falls below required thresholds, positions are automatically liquidated by bots that repay debt and seize collateral at a discount.
Once cbETH appeared to collapse from over $2,000 to just above $1, liquidation bots moved quickly. Because the protocol believed the token was nearly worthless, liquidators were able to repay roughly $1 of debt to seize one cbETH.
Risk manager Anthias Labs said 1,096.317 cbETH ($2.44 million) was seized, wiping out borrower collateral while leaving the protocol with bad debt across several markets.
The distorted pricing also allowed a smaller group of users to deposit minimal collateral and borrow cbETH at the artificially low valuation, further increasing losses.
Moonwell reduced supply and borrow caps within minutes to contain damage. However, correcting the oracle required a governance vote and a five day timelock, preventing an immediate fix.
The episode is the latest reminder that price oracles are foundational infrastructure and a key point of failure for DeFi applications. When they misfire, the smart contracts do exactly what they are programmed to do, but the balance sheet absorbs the consequences.
Meanwhile, security auditor Krum Pashov noted that GitHub commits tied to the proposal were co-authored by Claude Opus 4.6, an AI coding assistant, prompting debate over whether automated “vibe coding” contributed to the faulty oracle logic.
🚨Claude Opus 4.6 wrote vulnerable code, leading to a smart contract exploit with $1.78M loss
cbETH asset’s price was set to $1.12 instead of ~$2,200. The PRs of the project show commits were co-authored by Claude – Is this the first hack of vibe-coded Solidity code? pic.twitter.com/4p78ZZvd67
— pashov (@pashov) February 17, 2026
Crypto World
$1.78M ‘Vibe-Coded’ Oracle Bug Puts AI-Coauthored Contracts Under Scrutiny
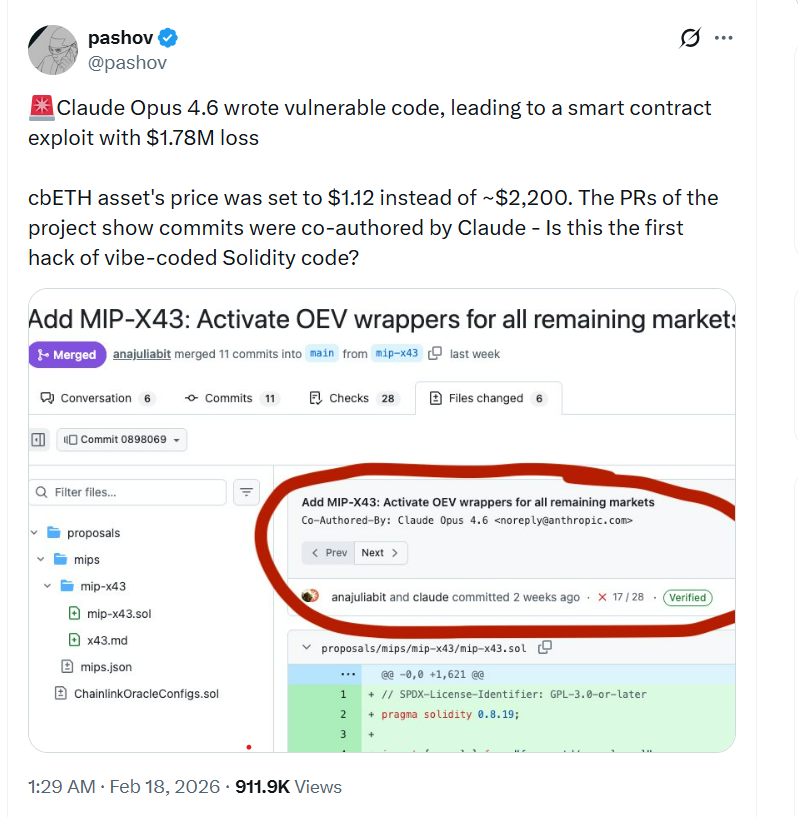
Moonwell, a decentralized finance (DeFi) lending protocol deployed on Base and Optimism, was exploited for about $1.78 million after a pricing oracle for Coinbase Wrapped Staked ETH (cbETH) returned a value of about $1.12 instead of $2,200, creating a mispricing that attackers were able to use for profit.
Moonwell said in an incident post-mortem that a governance proposal executed on Sunday misconfigured the cbETH oracle by using the cbETH/ETH exchange rate alone, causing the system to report cbETH at about $1.12. The protocol said liquidation bots and opportunistic borrowers exploited the mispricing, leaving roughly $1.78 million in bad debt.
The pull requests for the affected contracts show multiple commits co-authored by Anthropic’s Claude Opus 4.6, prompting security auditor Pashov to publicly flag the incident as an example of artificial intelligence-written or AI-assisted Solidity backfiring.
Speaking to Cointelegraph about the incident, he said that he had linked the case to Claude because there were multiple commits in the pull requests that were co-authored by Claude, meaning that “the developer was using Claude to write the code, and this has led to the vulnerability.”
Pashov cautioned, however, against treating the flaw as uniquely AI-driven. He described the oracle issue as the kind of mistake “even a senior Solidity developer could have made,” arguing that the real problem was a lack of sufficiently rigorous checks and end-to-end validation.

Initially, he said that he believed there had been no testing or audit at all, but later acknowledged that the team said it had unit and integration tests in a separate pull request and had commissioned an audit from Halborn.
In his view, the mispricing “could have been caught with an integration test, a proper one, integrating with the blockchain,” but he declined to criticise other security firms directly.
Related: How South Korea is using AI to detect crypto market manipulation
Small loss, big governance questions
The dollar amount of the exploit is small compared to some of DeFi’s largest incidents, such as the Ronin bridge exploit in March 2022, where attackers stole more than $600 million, or other nine-figure bridge and lending protocol hacks.
What makes Moonwell notable is the mix of AI co-authorship, a basic-seeming price configuration failure on a major asset, and existing audits and tests that failed to catch it.
Pashov said his own company would not fundamentally change its process, but if code appeared “vibe coded,” his team would “have a bit more wide open eyes” and expect a higher density of low-hanging issues, even though this particular oracle bug “was not that easy” to spot.
“Vibe coding” vs disciplined AI use
Fraser Edwards, co-founder and CEO of cheqd, a decentralized identity infrastructure provider, told Cointelegraph that the debate around vibe coding masks “two very different interpretations” of how AI is used.
Related: How AI crypto trading will make and break human roles
On one side, he said, are non-technical founders prompting AI to generate code they cannot independently review; on the other, experienced developers using AI to accelerate refactors, pattern exploration and testing inside a mature engineering process.
AI-assisted development “can be valuable, particularly at the MVP [minimal viable product] stage,” he noted, but “should not be treated as a shortcut to production-ready infrastructure,” especially in capital-intensive systems like DeFi.
Edwards argued that all AI-generated smart contract code should be treated as untrusted input, subject to strict version control, clear code ownership, multi-person peer review and advanced testing, especially around high-risk areas such as access controls, oracle and pricing logic, and upgrade mechanisms.
“Ultimately, responsible AI integration comes down to governance and discipline,” he said, with clear review gates, separation between code generation and validation, and an assumption that any contract deployed in an adversarial environment may contain latent risk.
Magazine: South Korea gets rich from crypto… North Korea gets weapons
Crypto World
American crypto investors are scared, confused about this year’s new IRS transaction reporting


A recent poll of 1,000 American investors in digital assets found that over half are scared they’ll face an IRS tax penalty this year as new transparency rules governing crypto exchanges take effect.
The data collected at the end of January by crypto tax platform Awaken Tax canvassed U.S. holders’ concerns about a radical shift from self-disclosure to automatic reporting of transactions.
This has been enacted through the introduction of the “Digital Asset Proceeds From Broker Transactions,” or Form 1099-DA, which tens of millions of Americans will be made aware of over the next month or so.
The new rules are designed to clamp down on crypto tax evasion and compel brokers, such as crypto exchange Coinbase (COIN), to report all sales and exchanges of digital assets that took place during 2025 to the tax agency.
The aim is to give tax authorities a clear view of investor gains and losses by opening up customer data inside exchanges for the first time, allowing the IRS to compare what crypto brokers report with what taxpayers file.
While the goal is to remove any margin of error, the rules are a “blunt instrument,” created by legislators who know nothing about crypto, according to Awaken Tax founder Andrew Duca.
“It means crypto is being treated like stocks, but it doesn’t behave in that way. Real crypto users will move assets between multiple wallets and interact with decentralized finance (DeFi) protocols, using pretty complex trading strategies,” Duca said.
Companies like Coinbase can provide information only on the proceeds of sales of crypto and are unable to report tax basis for any given digital asset — typically the purchase price plus acquisition costs — which can then be used to calculate capital gains or losses upon its sale.
“Coinbase actually cannot send the right information, because you can imagine if someone has bitcoin in a cold storage wallet ledger, they send it to Coinbase to sell. Coinbase doesn’t know your acquisition price, what you bought it for. So Coinbase is sending incorrect forms to the IRS. The 1099-DA form reports proceeds, but it doesn’t report tax basis,” Duca said.
Coinbase is well aware of the confusion this will cause. The onus falls on the holder of crypto to “patch” what’s missing in terms of their crypto acquisition costs and actual tax basis via the IRS’s updated Form 8949, Duca said.
Duca acknowledges that crypto tax compliance is extremely low: Under 20% of crypto holders report what they ought to, he said.
“It’s really not been thought out well and is kind of horrible for crypto users. But it’s what they could do the quickest and the easiest,” Duca said. “They just added this super blunt instrument to try to get that 20% up to 80% in a year.”
Crypto World
Develop a Hyper Casual Game Like Flappy Bird in 2 Weeks
The hyper casual gaming market moves faster than almost any other segment in the gaming industry. Trends emerge overnight, player attention shifts quickly, and the games that capture momentum early often dominate downloads and ad revenue. In this environment, speed is not just an advantage, it is a business strategy.
A Flappy Bird–style hyper casual game, built around a simple yet addictive core loop, remains one of the most powerful formats for rapid market entry. Its simplicity allows faster development, faster testing, and faster monetization validation.
However, here is the reality many enterprises tend to overlook. Building a hyper casual game in 2 weeks is not about rushing development. It is all about having the right development team, pipeline, and production discipline.
When executed correctly by a trusted hyper casual game development company, a 2-week MVP can help enterprises test concepts, validate monetization models, and enter the market before competitors react.
Why Flappy Bird–Style Games Are Ideal for Rapid Development
Flappy Bird–style games are often misunderstood as “easy to build.” In reality, they are simple in structure but demanding in execution. Their minimalism is precisely what enables speed but also what exposes poor quality quickly. When a game has only one mechanic, there is nowhere to hide flaws. These games succeed because they:
- Deliver instant engagement
- Require zero onboarding time
- Encourage repeated play
- Generate strong ad impressions per session
- Create addictive retry loops
However, for enterprises, the appeal is strategic rather than just creative. A Flappy Bird–style game allows businesses to:
- Validate a concept quickly
- Test a theme or brand engagement
- Trial monetization models
- Enter a new market with minimal delay
- Gather behavioral data rapidly
The short session design also aligns perfectly with ad-driven monetization, making them commercially viable testing tools. However, achieving this requires expert tuning, such as physics, input response, and difficulty curves must feel precise. Otherwise, players churn within minutes. This is exactly the reason why experienced hyper casual game developers matter.
What a Realistic 2-Week Development Timeline Looks Like
A credible 2-week timeline is structured, not chaotic. It follows a clear production plan.
Days 1–2: Concept Finalization & Scope Lock
The team defines:
- Core gameplay loop
- Visual direction
- Monetization approach
- Target platform
- Success KPIs
This stage prevents scope creep and keeps production focused. Enterprises that skip proper scoping often face delays later.
Days 3–6: Core Development
Developers build:
- Player controls
- Physics tuning
- Game loop logic
- UI framework
- Base art assets
At this stage, the goal is playability, not perfection. A professional hyper casual game development company uses reusable frameworks to accelerate this phase.
Days 7–10: Polish & Monetization Integration
This includes:
- Ad network integration
- Rewarded ad logic
- Basic analytics setup
- UI polish
- Sound and feedback tuning
Monetization is integrated early to validate revenue potential.
Days 11–14: Testing & Soft Launch Prep
The focus now shifts to:
- Bug fixes
- Performance optimization
- Device compatibility
- Soft launch build preparation
Testing ensures the game feels stable and smooth across devices.
Why the “Right Team” Matters More Than the Timeline
A 2-week build is only realistic when the hyper casual game development team has:
- Proper hyper casual game development experience & expertise
- Proven pipelines
- Reusable code frameworks
- Structured production workflows
- Clear communication loops
Without these, a 2-week target becomes unrealistic. The right team turns speed into a repeatable process rather than a risky gamble.
Planning to Build a Hyper Casual Game Like Flappy Bird in Quick Time?
Business Benefits of a 2-Week Hyper Casual MVP
A 2-week MVP is not about saving time alone. It is about creating a structured experimentation cycle. For enterprises, this becomes a business strategy.
1. Fast Market Validation
A rapid MVP allows enterprises to test hypotheses instead of relying on assumptions. Rather than debating whether an idea will work, companies can:
- Launch quickly
- Measure retention
- Track session lengths
- Analyze user behavior
- Evaluate monetization performance
This plays a significant role in replacing guesswork with real data. For decision-makers, this data-driven approach reduces strategic uncertainty and supports smarter investment decisions.
2. Lower Initial Investment Risk
Traditional game development often demands significant upfront budgets. Hyper casual MVPs allow staged investment. Enterprises can:
- Test multiple ideas simultaneously
- Scale only the winners
- Drop underperforming concepts early
- Optimize budget allocation
This portfolio-style strategy is widely used by successful publishers. Instead of betting big on one idea, enterprises run controlled experiments.
3. Competitive Speed Advantage
In hyper casual game development, timing influences success heavily. Launching early allows a company to:
- Capture user attention before trends peak
- Establish early app store presence
- Gain organic installs
- Collect data before competitors enter
Even a few weeks can determine whether a concept feels fresh or saturated. Speed becomes a competitive moat.
4. Data-Driven Scaling Decisions
A soft-launched MVP produces valuable metrics such as:
- Day 1 and Day 7 retention
- Ad engagement rates
- CPI vs LTV performance
- Drop-off points
This data, in turn, plays a crucial role in informing:
- Whether to invest further
- Which features to expand
- How to refine monetization
- Which markets to target
Enterprises that scale based on data outperform those relying on intuition.
Common Factors That Delay Hyper Casual Game Development
Hyper casual game development projects often slow down due to avoidable issues.
1. Changing Scope Midway
Scope creep is the biggest enemy of rapid development. Adding some features all of a sudden, like:
- Extra levels
- Complex UI
- Narrative elements
- Multiplayer modes
Quickly breaks the 2-week timeline. Successful teams lock scope early and treat the MVP as a test, not a final product.
2. Overcomplicating Mechanics
Hyper casual games thrive on simplicity. When teams add:
- Multiple controls
- Advanced progression
- Layered systems
The game loses clarity, and development slows. Enterprises must respect the “one core loop” philosophy.
3. Ignoring Analytics Setup
Without analytics, an MVP loses its purpose. Analytics track:
- Retention
- User behavior
- Monetization efficiency
Skipping this step means launching blind. Enterprises should view analytics as essential, not optional.
4. Skipping Early Testing
Unpolished physics or laggy controls ruin user experience. Even some of the simplest games need:
- Device testing
- Performance checks
- Input responsiveness tuning
Quality issues harm retention immediately.
5. Lack of Structured Pipeline
Ad-hoc development wastes time. A structured pipeline, on the other hand, includes:
- Pre-defined frameworks
- Asset templates
- Clear milestones
- Reusable systems
Experienced teams rely on repeatable processes.
Why Enterprises Partner with a Hyper Casual Game Development Company
Building internally may seem attractive, but it often slows execution. A specialized hyper casual game development company provides:
1. Speed-Ready Pipelines
They use proven frameworks, reducing setup time. This, in turn, allows faster prototyping and iteration.
2. Monetization Expertise
The revenue model of hyper casual games depends on ads and a retention balance. Experts optimize:
- Ad frequency
- Placement strategy
- Rewarded formats
Poor monetization design hurts revenue.
3. Analytics Integration
Professionals set up tracking from day one. This ensures every launch produces usable insights.
4. Performance Optimization
Players in the hyper casual gaming model expect instant load and smooth play. Developers therefore optimize for:
- Low memory usage
- Smooth FPS
- Fast loading times
5. Rapid Iteration Capability
Experienced teams iterate weekly or even faster. This allows constant improvement post-launch.
Conclusion
In hyper casual gaming, ideas alone do not win. Execution speed does. A Flappy Bird–style hyper casual game built in 2 weeks can become a powerful validation tool, revenue channel, or user acquisition engine when developed correctly.
However, the real question is not whether it can be built quickly. The ideal question is whether it is built by an experienced hyper casual game development team that knows how to make speed work in your favor.
Antier, a top-rated hyper casual game development company, works with enterprises and studios to deliver hyper casual games quickly without compromising quality. The support from the team includes:
- End-to-end hyper casual development
- Monetization-ready builds
- Analytics integration
- Rapid MVP pipelines
- Post-launch optimization
The focus is not just launching fast; it is launching smart. Get in touch with us today to build your next hyper casual hit.
Frequently Asked Questions
01. Why are Flappy Bird-style games considered ideal for rapid development in the hyper casual gaming market?
Flappy Bird-style games are ideal for rapid development because their simple structure allows for quick concept validation, minimal onboarding time, and strong ad impressions, making them effective tools for testing and monetization.
02. What is the significance of having the right development team for building a hyper casual game in 2 weeks?
The right development team is crucial for building a hyper casual game in 2 weeks as it ensures proper execution, structured production discipline, and the ability to deliver a high-quality MVP that can validate concepts and monetization models effectively.
03. What does a realistic 2-week development timeline for a hyper casual game involve?
A realistic 2-week development timeline involves a structured plan that includes days for concept finalization, scope locking, defining the core gameplay loop, visual direction, and monetization approach, ensuring a focused and efficient development process.
-

 Sports7 days ago
Sports7 days agoBig Tech enters cricket ecosystem as ICC partners Google ahead of T20 WC | T20 World Cup 2026
-
 Video2 days ago
Video2 days agoBitcoin: We’re Entering The Most Dangerous Phase
-

 Tech3 days ago
Tech3 days agoLuxman Enters Its Second Century with the D-100 SACD Player and L-100 Integrated Amplifier
-

 Video5 days ago
Video5 days agoThe Final Warning: XRP Is Entering The Chaos Zone
-

 Tech1 day ago
Tech1 day agoThe Music Industry Enters Its Less-Is-More Era
-

 Sports1 day ago
Sports1 day agoGB's semi-final hopes hang by thread after loss to Switzerland
-
 Crypto World1 day ago
Crypto World1 day agoCan XRP Price Successfully Register a 33% Breakout Past $2?
-

 Business14 hours ago
Business14 hours agoInfosys Limited (INFY) Discusses Tech Transitions and the Unique Aspects of the AI Era Transcript
-

 Video1 day ago
Video1 day agoFinancial Statement Analysis | Complete Chapter Revision in 10 Minutes | Class 12 Board exam 2026
-

 Tech5 hours ago
Tech5 hours agoRetro Rover: LT6502 Laptop Packs 8-Bit Power On The Go
-
 Crypto World4 days ago
Crypto World4 days agoBhutan’s Bitcoin sales enter third straight week with $6.7M BTC offload
-
 Crypto World7 days ago
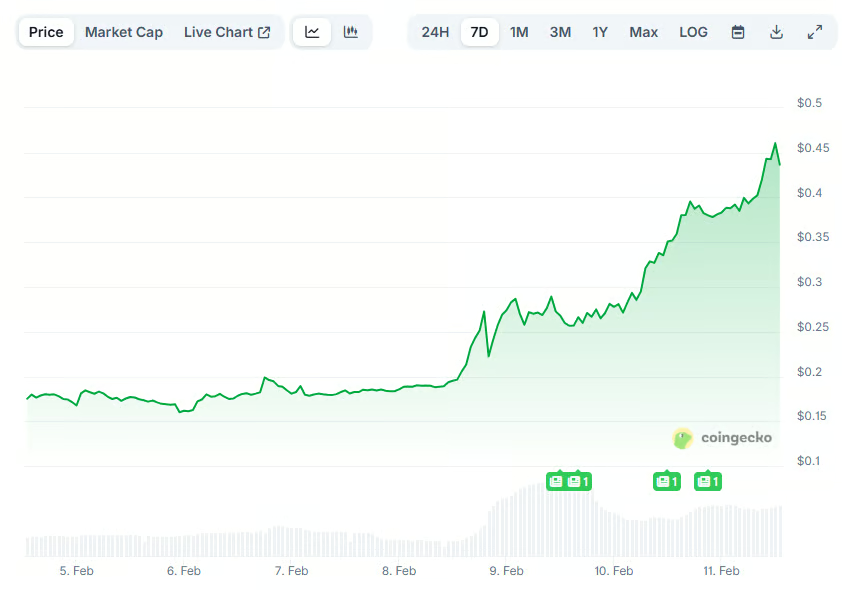
Crypto World7 days agoPippin (PIPPIN) Enters Crypto’s Top 100 Club After Soaring 30% in a Day: More Room for Growth?
-
 Video6 days ago
Video6 days agoPrepare: We Are Entering Phase 3 Of The Investing Cycle
-

 NewsBeat3 days ago
NewsBeat3 days agoThe strange Cambridgeshire cemetery that forbade church rectors from entering
-

 Business6 days ago
Business6 days agoBarbeques Galore Enters Voluntary Administration
-

 Business7 hours ago
Business7 hours agoTesla avoids California suspension after ending ‘autopilot’ marketing
-
 Crypto World6 days ago
Crypto World6 days agoEthereum Price Struggles Below $2,000 Despite Entering Buy Zone
-

 NewsBeat3 days ago
NewsBeat3 days agoMan dies after entering floodwater during police pursuit
-

 Crypto World5 days ago
Crypto World5 days agoKalshi enters $9B sports insurance market with new brokerage deal
-

 NewsBeat4 days ago
NewsBeat4 days agoUK construction company enters administration, records show